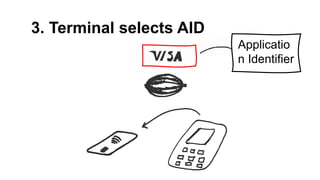
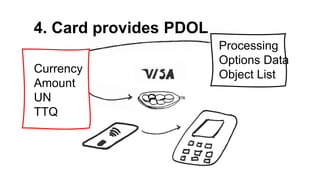
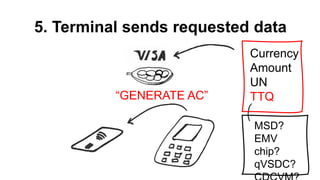
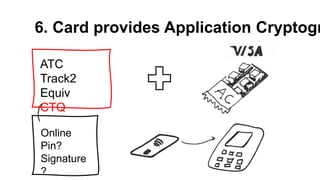
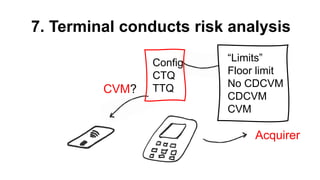
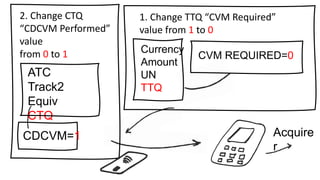
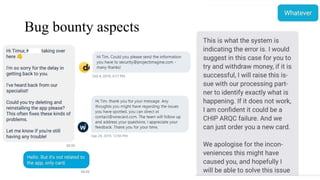
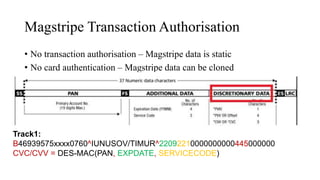
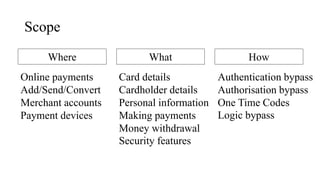
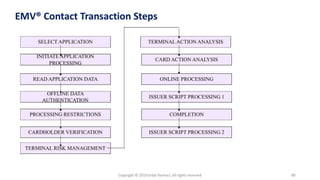
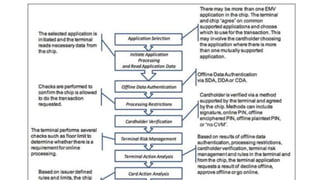
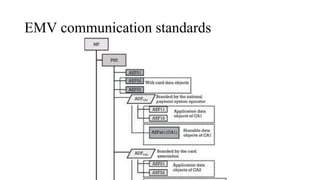
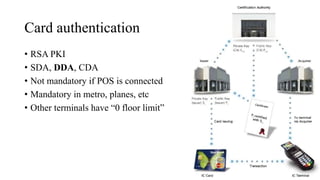
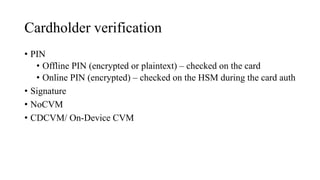
The document presents a comprehensive overview of payment security vulnerabilities, detailing the history and evolution of payment systems, including methodologies to identify and exploit weaknesses in card and NFC payments. It covers key topics such as EMV standards, cryptographic attacks, and practical recommendations for finding vulnerabilities in payment systems. Additionally, it emphasizes the importance of responsible disclosure in the context of bug bounty programs in the payment industry.




















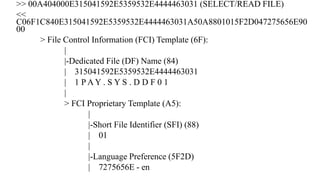
![Cardholder Verification Methods List – Tag 8E
java -jar emv-bertlv-0.1.8-shaded.jar constructed
8E160000000000000000420504054203440341031E031F02
• [4205] Encrypted PIN online, If purchase + cash, next
• [0405] Encrypted PIN by ICC, If purchase + cash, FAIL
• [4203] Encrypted PIN online, If terminal supports CVM, next
• [4403] Encrypted PIN by ICC, If terminal supports CVM, next
• [4103] Plain PIN by ICC, If terminal supports CVM, next
• [1E03] Signature, If terminal supports CVM, FAIL
• [1F02] No CVM required, If not (unattended cash, manual cash, purchase
+ cash), FAIL](https://image.slidesharecdn.com/bbinpaymentsv4-220427114937/85/Offensive-Payment-Security-30-320.jpg)
![Cardholder Verification Methods List – Tag 8E
• [4205]
• 4xxx – Transaction will not fail if not chosen
• 42xx – Encrypted PIN online
• xx05 – If purchase + cash
• [1E02]
• 1xxx – Transaction will be canceled if the verification method fails
• 1exx – Signature
• xx02 – If not unattended cash, manual cash, purchase + cash](https://image.slidesharecdn.com/bbinpaymentsv4-220427114937/85/Offensive-Payment-Security-31-320.jpg)


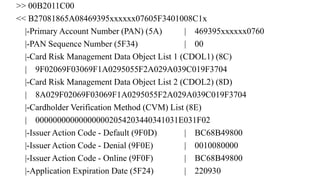



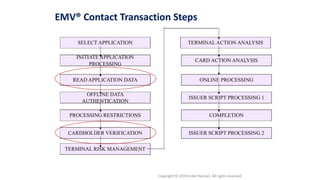

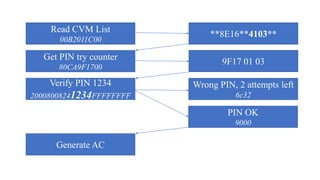



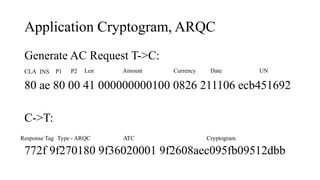
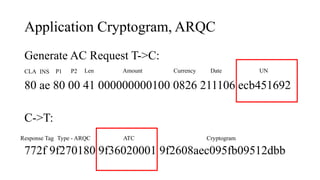
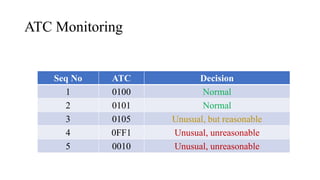
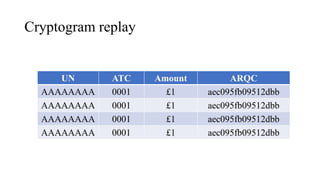




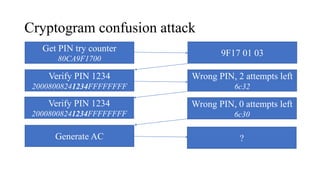
![PIN Try limit exceeded behaviour
• Disable NFC/EMV interface – optional
• Set bytes in CVR/IAD (Tag 9F10)
[Byte 3 Bit 7 = 1] Pin try limit exceeded
• Starts providing AAC cryptogram
• [Byte 1 Bit 6 = 0, Byte 1 Bit 5 = 0] AAC Returned in First Generate AC
• ARQC – Online authorisation
• TC – Offline validation
• AAC – Declined cryptogram for further analysis](https://image.slidesharecdn.com/bbinpaymentsv4-220427114937/85/Offensive-Payment-Security-58-320.jpg)
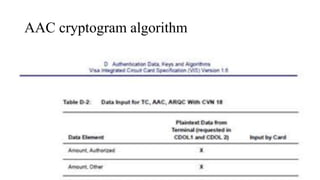
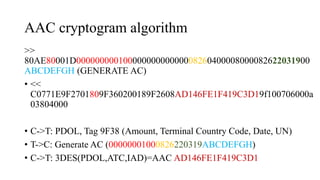
![AAC cryptogram algorithm
[9F10 (issuer application data)] 06000A03804000
[Derivation key index] 00
[Cryptogram version number] 0A
[Card verification results] 03804000
[Byte 2 Bit 8 = 1, Byte 2 Bit 7 = 0] Second GENERATE AC not requested
[Byte 2 Bit 6 = 0, Byte 2 Bit 5 = 0] AAC Returned in GPO/first
GENERATE AC
[Byte 3 Bit 7 = 1] Pin try limit exceeded
[Byte 4 Bits 8-5] Issuer Script Commands processed on last transaction = 0](https://image.slidesharecdn.com/bbinpaymentsv4-220427114937/85/Offensive-Payment-Security-61-320.jpg)