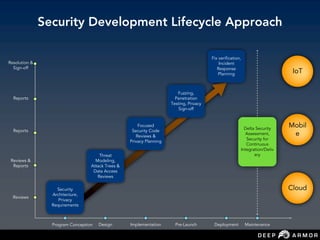
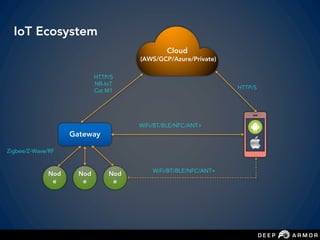
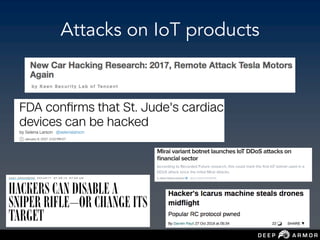
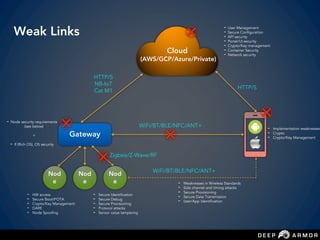
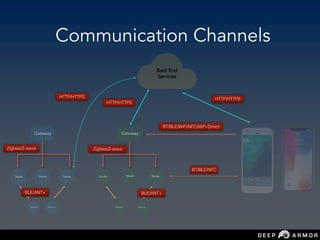
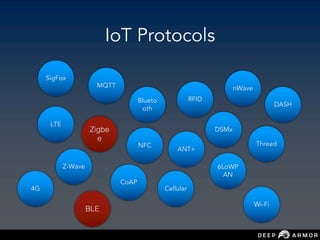
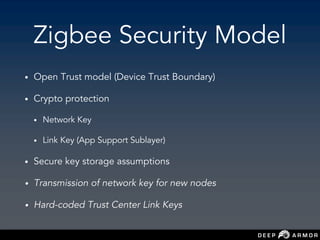
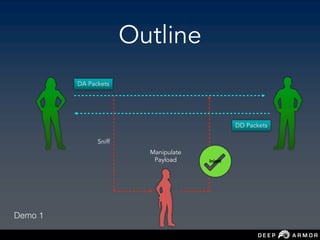
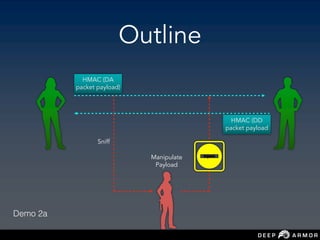
The document discusses security challenges and approaches for IoT networks and ecosystems. It provides an overview of common IoT communication protocols like Zigbee, Bluetooth Low Energy, and IEEE 802.15.4. It then demonstrates hands-on exercises attacking these protocols by sniffing and manipulating packets. It also discusses securing the AWS IoT platform and introduces the security development lifecycle approach for securing IoT products throughout the development process.





![Packet Structure
Payload
[DA/DD]
[DATA]
SRC
SEQ NUM
PAN ID
DST](https://image.slidesharecdn.com/saconsumanthnaropanth-iotnetworkecosystemsecurityattackssecuredesign-190227124903/85/Sacon-Sumanth-Naropanth-IoT-network-ecosystem-security-attacks-secure-design-15-320.jpg)







![Packet Structure
Payload
[DA/DD]
[DATA]
SRC
SEQ NUM
PAN ID
DST](https://image.slidesharecdn.com/saconsumanthnaropanth-iotnetworkecosystemsecurityattackssecuredesign-190227124903/85/Sacon-Sumanth-Naropanth-IoT-network-ecosystem-security-attacks-secure-design-25-320.jpg)




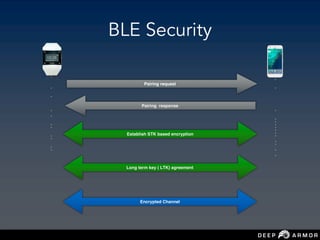








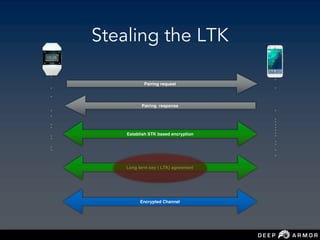
![Understanding BLE
pcaps
• Protocol Data Unit
• PDU length determines —> advertising packet
or not
•pdu_type == 5 [connection request by
bluetooth device ]](https://image.slidesharecdn.com/saconsumanthnaropanth-iotnetworkecosystemsecurityattackssecuredesign-190227124903/85/Sacon-Sumanth-Naropanth-IoT-network-ecosystem-security-attacks-secure-design-43-320.jpg)



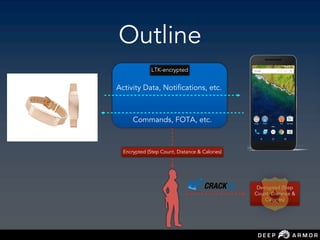
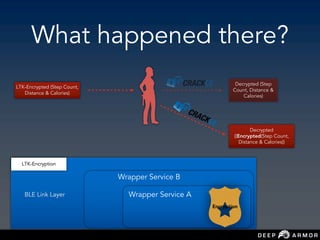
![Hacking
[Wearable - Mobile]
Channels](https://image.slidesharecdn.com/saconsumanthnaropanth-iotnetworkecosystemsecurityattackssecuredesign-190227124903/85/Sacon-Sumanth-Naropanth-IoT-network-ecosystem-security-attacks-secure-design-48-320.jpg)






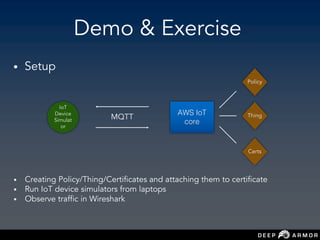
![Topics of Interest
• Review of overly permissive policies
• Wild card should be avoided [iot : *]
• iot:Publish/UpdateJobExecution/GetThingShadow
• Must specify ARN of resource [wildcard * should not be used]](https://image.slidesharecdn.com/saconsumanthnaropanth-iotnetworkecosystemsecurityattackssecuredesign-190227124903/85/Sacon-Sumanth-Naropanth-IoT-network-ecosystem-security-attacks-secure-design-59-320.jpg)