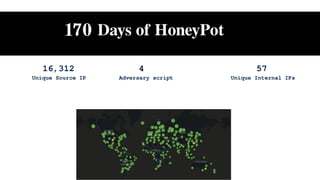
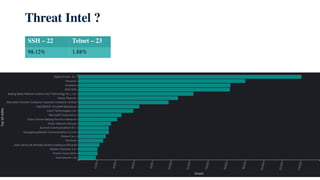
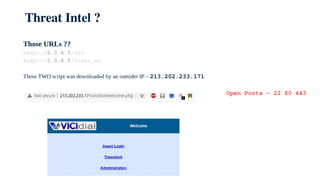
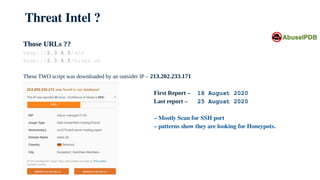
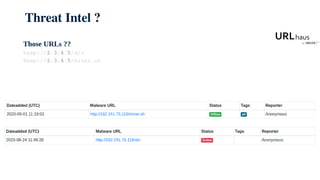
The document discusses using honeypots for network security analysis. It begins with background on honeypots, explaining that they are decoy systems meant to attract cyber attacks. The document then discusses threat intelligence gathered from a honeypot including unique source IPs, attacked ports, downloaded scripts and their origins, and affected internal IPs. It notes the top devices targeted were outdated routers and IP cameras. The document concludes with discussing internal analysis and challenges convincing a client they have an issue after honeypot alerts.
















![What about the internals !!! one CCIE got it covered?
– Slack gives me an alert, and I let my CS team knew to work on that particular client.
– 2 days later I got alert for the same IP, me again knock my CS team to work on it.
– 1 day later, I got the alert again; and then I asked our CS team whether they have worked on it or not ?
– they replied, on second day client IT concern replied “i am a CCIE, I know what is happening
in my network, you guys dont have to bother me again & again”
So the challenge begins for me → → →
[192.168.0.133 ← Faked the User’s IP for demonstration purpose]](https://image.slidesharecdn.com/havinghoneypotforbetternetworksecurityanalysis-new-201014024203/85/Having-Honeypot-for-Better-Network-Security-Analysis-23-320.jpg)








