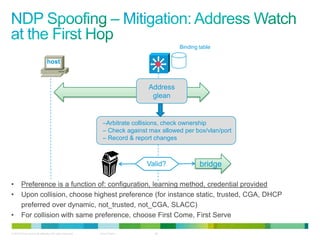
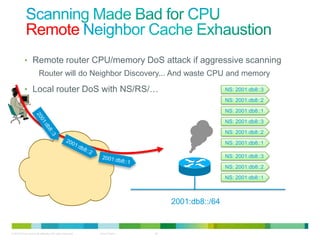
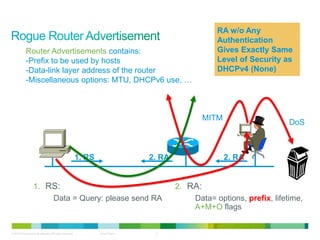
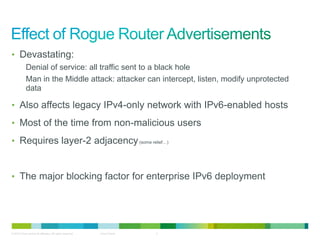
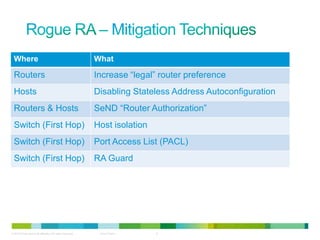
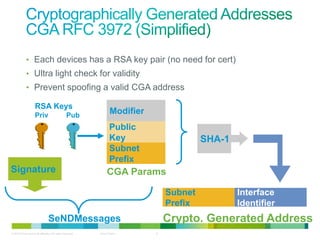
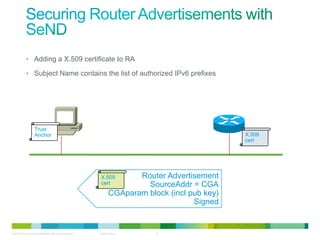
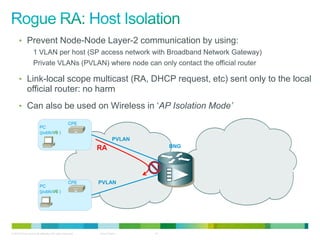
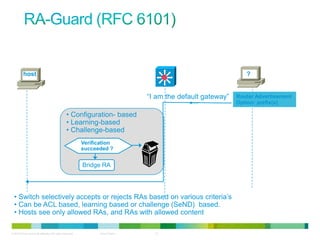
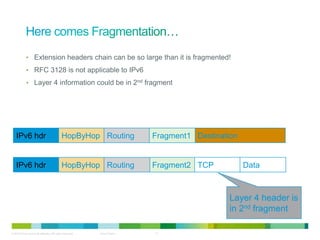
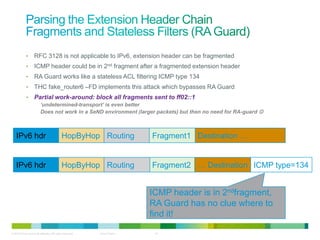
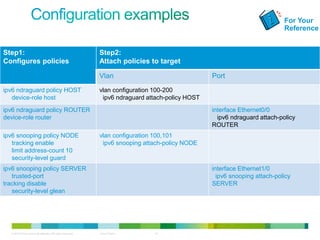
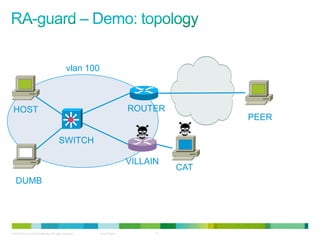
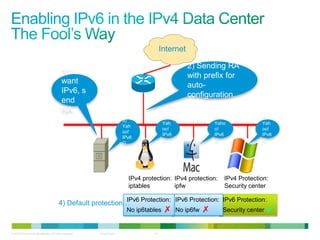
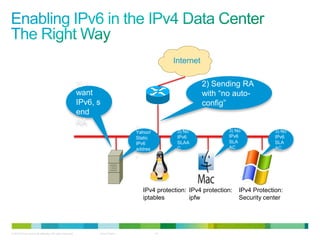
The document discusses IPv6 first hop security features like DHCP snooping and dynamic ARP inspection for IPv6. It provides an overview of the security issues with IPv6 neighbor discovery such as router advertisements being sent without authentication, allowing for man-in-the-middle attacks and denial of service. It then describes various IPv6 first hop security features that can help mitigate these issues, such as RA guard, DHCP guard, and IPv6 neighbor discovery inspection.











![Binding table
DHCP-
ADR MAC VLAN IF
server
H1 H2 H3 A1 MACH1 100 P1
A21 MACH2 100 P2
A22 MACH2 100 P2
NS [IP source=A1, LLA=MACH1] A3 MACH3 100 P3
REQUEST [XID, SMAC = MACH2]
REPLY[XID, IP=A21, IP=A22]
data [IP source=A3, SMAC=MACH3]
DAD NS [IP source=UNSPEC, target = A3] DHCP LEASEQUERY
NA [IP source=A3, LLA=MACH3] DHCP LEASEQUERY_REPLY
© 2012 Cisco and/or its affiliates. All rights reserved. Cisco Public 25](https://image.slidesharecdn.com/vyncke-layer-2securityipv6norway-120426074955-phpapp01/85/Eric-Vyncke-Layer-2-security-ipv6-norway-25-320.jpg)