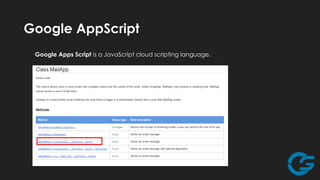
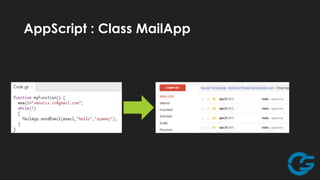
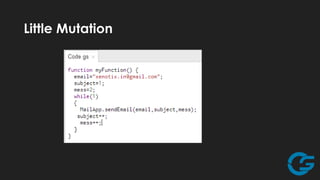
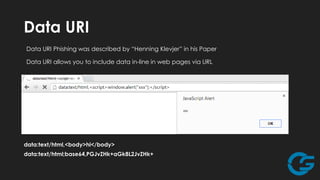
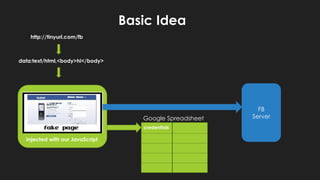
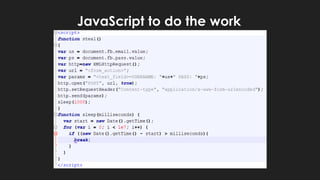
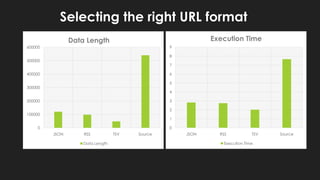
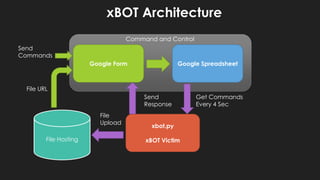
The document discusses potential abuses of Google Apps and Data API, with various methods for email bombing, phishing, and botnet communication using Google technologies. It highlights the use of Google Apps Script, Data URI, and Google Spreadsheets for malicious activities, including a prototype bot named 'xbot' that utilizes these services for command and control. The conclusion emphasizes the danger of exploiting seemingly innocent services and notes the lack of security measures like CAPTCHA on Google Forms.