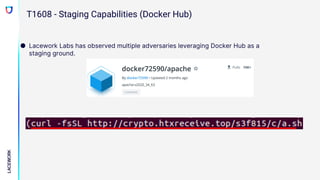
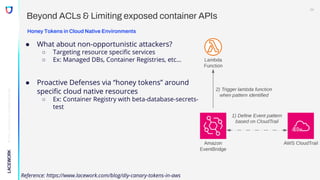
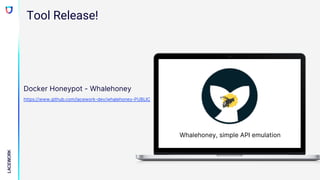
The document discusses emerging threats and attack methods targeting container workloads in cloud environments, emphasizing the shift toward such technologies and associated risks. It highlights various attack techniques, including exploitation of misconfigurations and deployment of rogue images, and describes the development and use of honeypots for gathering attack data. Recommendations for securing cloud-native environments include limiting exposure through access controls, enforcing signed container deployments, and implementing proactive defenses like honey tokens.










![echo ssh key to /root/.ssh/authorized_keys
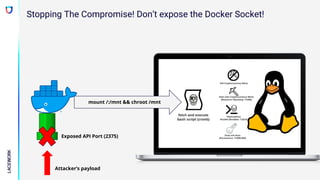
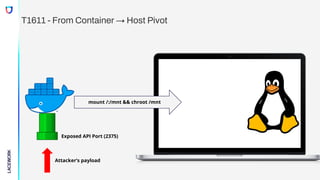
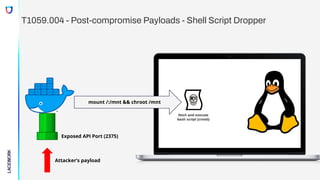
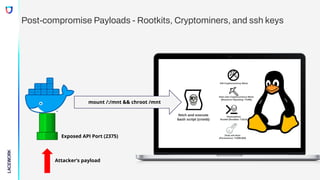
Exposed API Port (2375)
Attacker’s payload
● cmd": ["sh", "-c", "echo 'ssh-rsa
AAAAB3NzaC1yc2EAAAADAQABAAABgQDIdl8SFK8a6
VAjM6i8AAUtpl15<snippet>' >>
/opt/root/.ssh/authorized_keys]
T1189 - Drive by Compromise (SSH Key Dropping)](https://image.slidesharecdn.com/attckingcontianersinthecloud-220405233746/85/ATT-CKING-Containers-in-The-Cloud-16-320.jpg)
![…
"cmd":["--probe.docker=true","--service-token=<REDACTED>"],
"Image":"weaveworks/scope:1.13.2"
….
T1133 - External Remote Services (Weaveworks Scope)](https://image.slidesharecdn.com/attckingcontianersinthecloud-220405233746/85/ATT-CKING-Containers-in-The-Cloud-17-320.jpg)