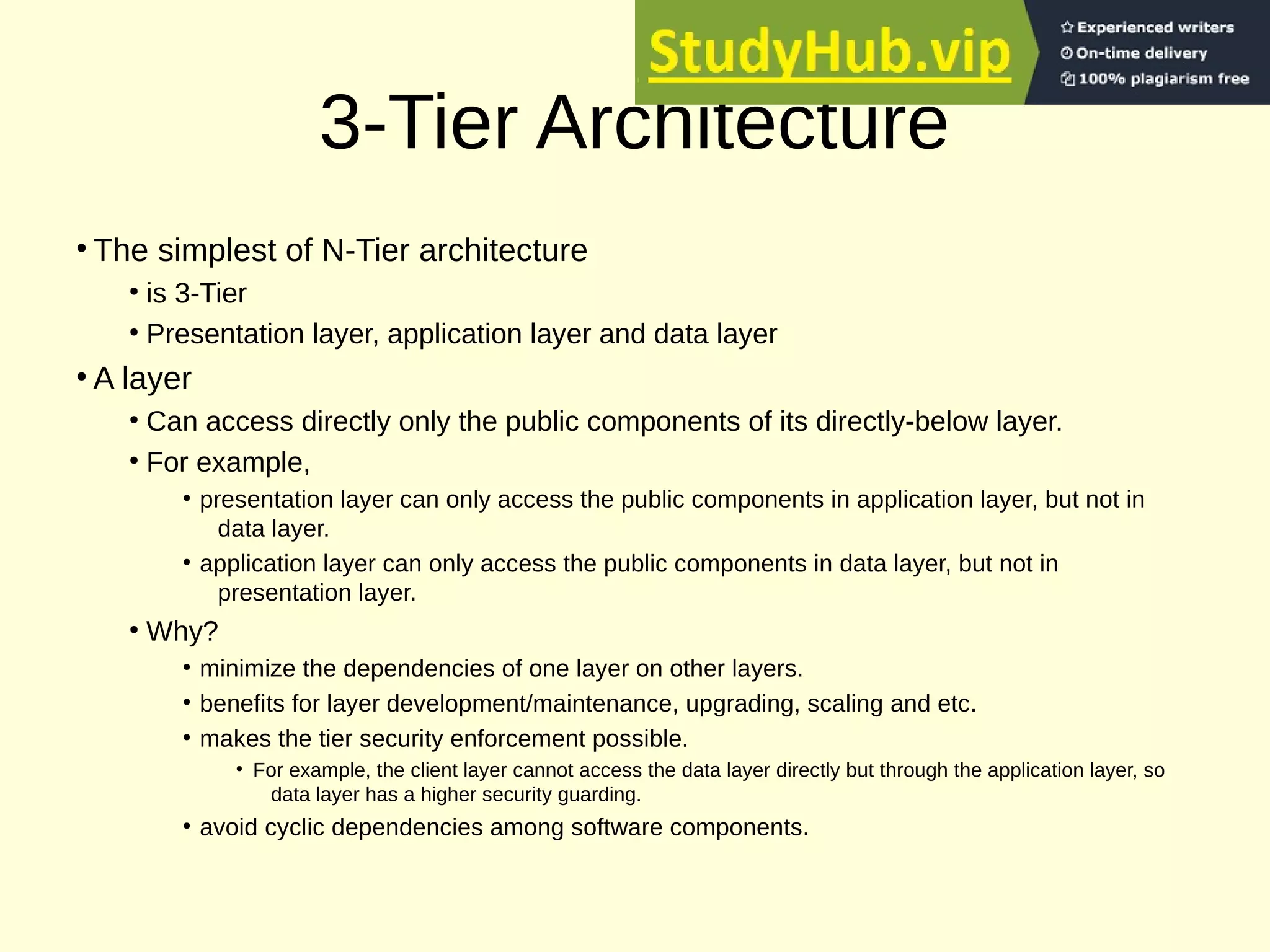
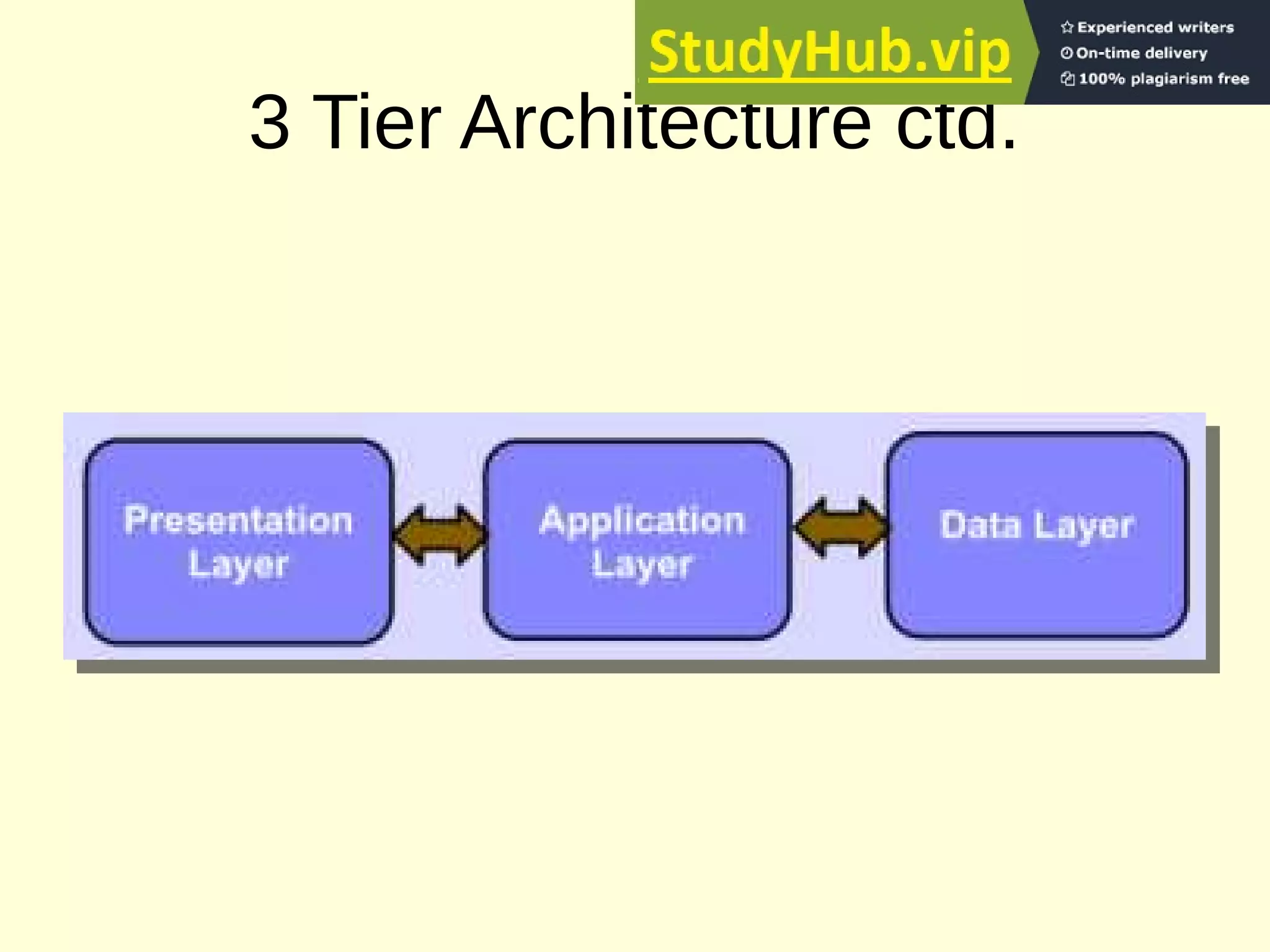
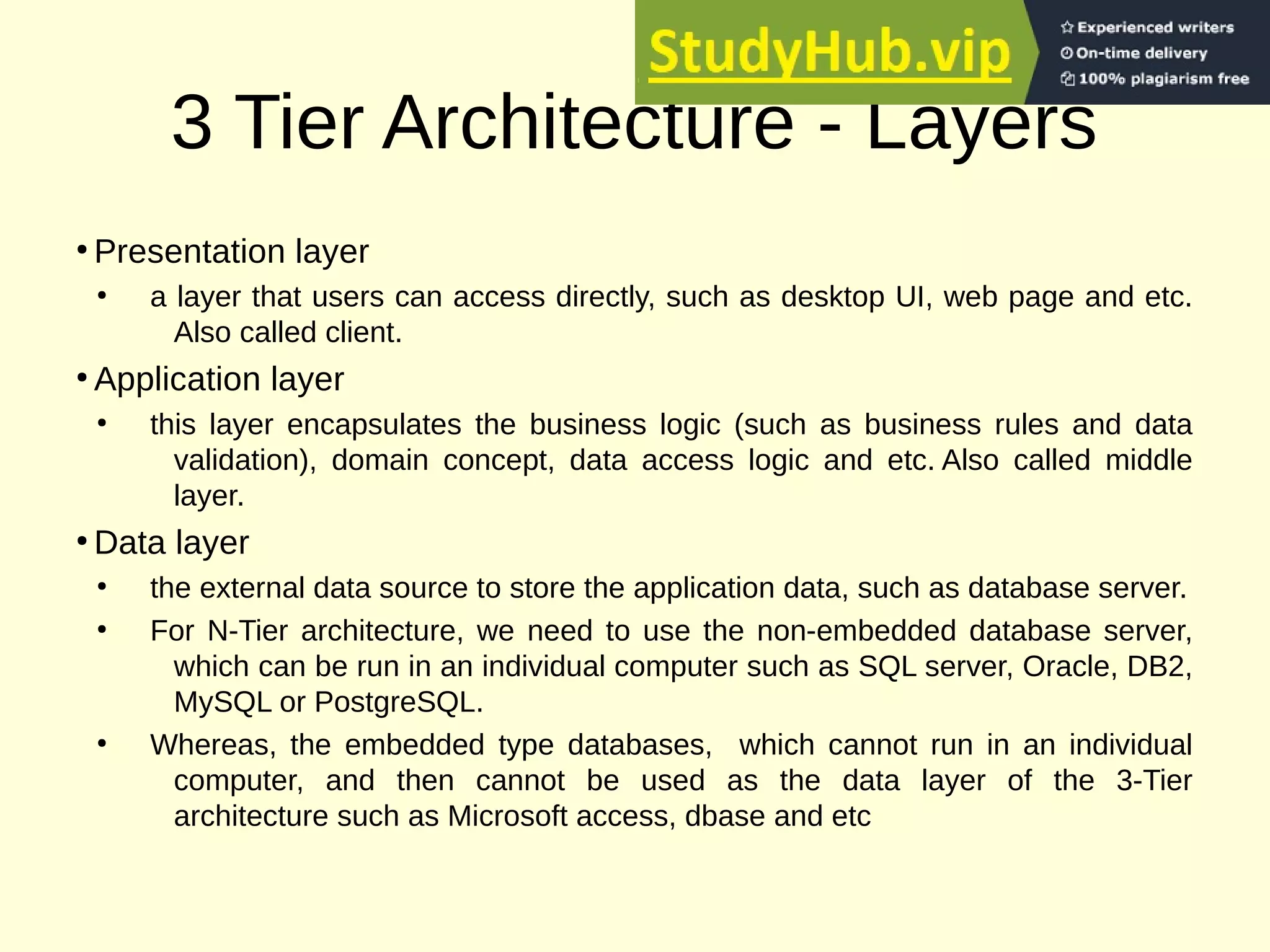
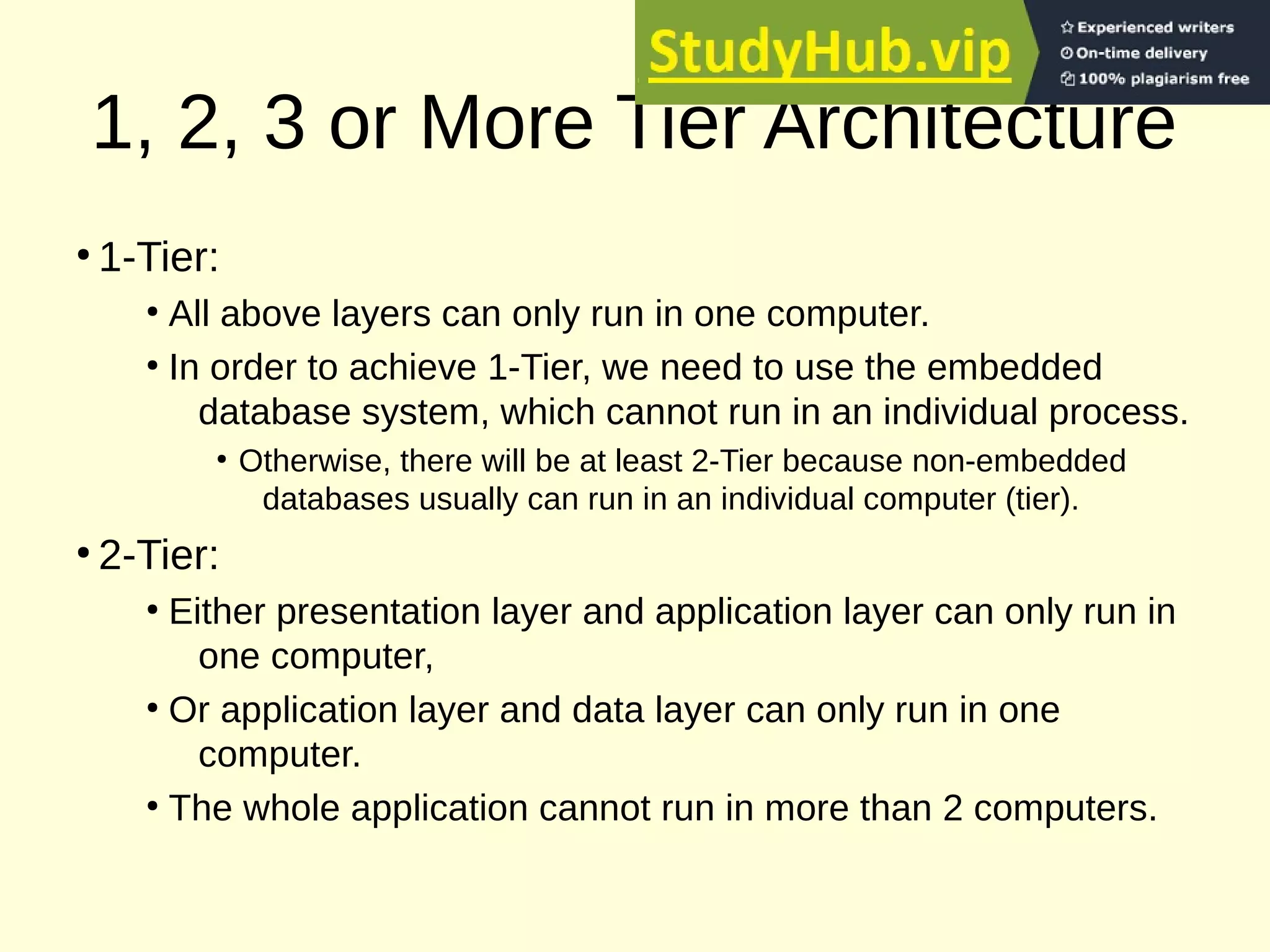
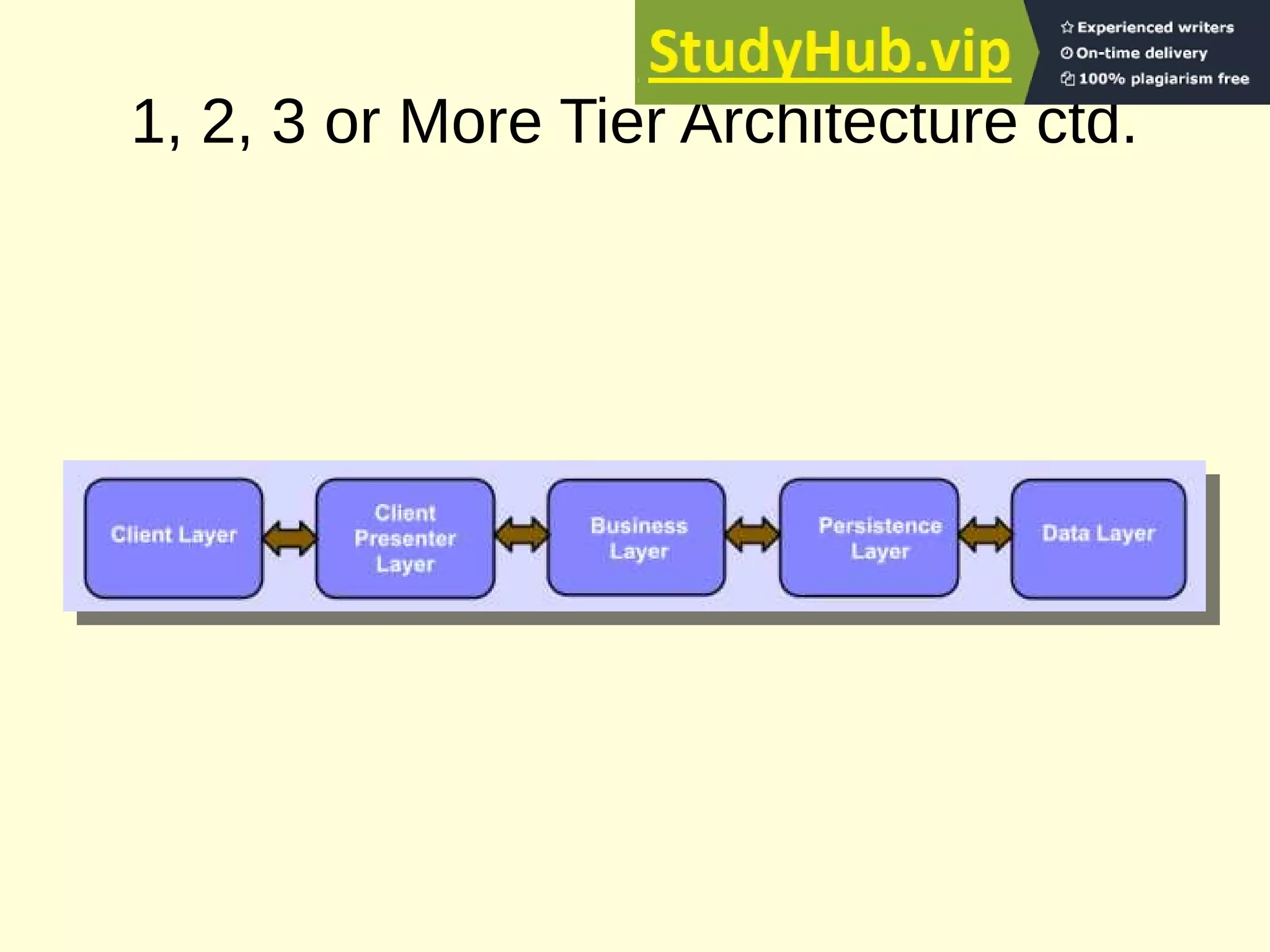
This document provides an overview of the key concepts for the Advanced Web Design and Development course (BIT 3207). It lists recommended books and motivation for learning web design. It then covers network fundamentals including IP, IP addressing, transport layer protocols, TCP connections, HTTP protocol, URLs, status codes and methods. It also discusses client-side components like browsers, HTML, HTML5, XML and JavaScript. On the server-side it covers servers, web servers, CGI, JSP, ASP/PHP and databases. It concludes with an explanation of 3-tier architecture and the layers of presentation, application and data.

![Books
• Rabbit and Dynamic C ® - An Introduction
to TCP/IP
• W3C - RFC2616 [Hypertext Transfer
Protocol]
• Responsive Web Design with HTML5 and
CSS3
• Beginning PHP5, Apache, and MySQL ®
Web Development](https://image.slidesharecdn.com/advancedwebdesignanddevelopmentbit3207-230806151943-9df61c42/75/Advanced-Web-Design-And-Development-BIT-3207-2-2048.jpg)

![Network fundamentals HTTP - URL
• The “http” scheme is used to locate network resources
via the HTTP protocol.
http_URL = "http:" "//" host [ ":" port ] [ abs_path [ "?" query ]]
• If the port is empty or not given, port 80 is assumed.
The semantics are that the identified resource is
located at the server listening for TCP connections on
that port of that host, and the Request-URI for the
resource is abs_path. The use of IP addresses in URLs
SHOULD be avoided whenever possible. If the
abs_path is not present in the URL, it MUST be given
as “/” when used as a Request-URI for a resource.](https://image.slidesharecdn.com/advancedwebdesignanddevelopmentbit3207-230806151943-9df61c42/75/Advanced-Web-Design-And-Development-BIT-3207-9-2048.jpg)



![DATABASE COMPONENTS – SQL
• Structured query language is a standardized
query language for requesting information from a
database. The original version called SEQUEL
(structured English query language) was designed
by an IBM research center in 1974 and 1975. SQL
was first introduced as a commercial database
systemin 1979 by Oracle Corporation.
• Eg.:
SELECT [fields] FROM [table|view] WHERE [true
condition]](https://image.slidesharecdn.com/advancedwebdesignanddevelopmentbit3207-230806151943-9df61c42/75/Advanced-Web-Design-And-Development-BIT-3207-23-2048.jpg)