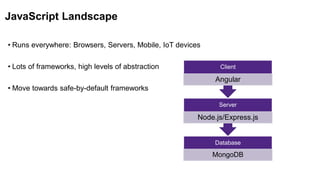
The document provides an overview of reviewing modern JavaScript applications for security. It discusses how JavaScript is used widely, common frameworks like React and Angular, and tools for analyzing JavaScript like ESLint. It also covers real-world examples of vulnerabilities like cross-site scripting and remote code execution. The talk emphasizes embracing developer tools and best practices like code reviews and linting to identify security issues in JavaScript applications.



























![DOM Clobbering
<html>
<body>
<form><input name="ownerDocument"></form>
<script>
console.log(document.forms[0].ownerDocument)
// Should return window.document
// Returns <input name="ownerDocument">
</script>
</body>
</html>](https://image.slidesharecdn.com/owaspsf-reviewingmodernjavascriptapplications-190207230816/85/OWASP-SF-Reviewing-Modern-JavaScript-Applications-29-320.jpg)


![DOM Clobbering
function lp_url_is_lastpass(e) {
if (null == e)
return !1;
var t = /^https://([a-z0-9-]+.)?lastpass.(eu|com)//i
, n = "https://lastpass.com/";
if ("undefined" != typeof base_url && (n = base_url),
0 == e.indexOf(n) || 0 == e.indexOf("https://lastpass.com/") || 0 == e.indexOf("https://lastpass.eu/"))
return !0;
if ("undefined" != typeof g_loosebasematching) {
var i = lp_gettld_url(e);
return new RegExp(i + "/$").test(base_url)
}
return t.test(e)
}
...
"openattach" == t.eventtype.value ? sendBG({
cmd: "openattach",
attachkey: t.eventdata1.value,
data: t.eventdata2.value,
mimetype: t.eventdata3.value
...
Exploit which achieved Remote Code Execution In LastPass Chrome Extension
https://bugs.chromium.org/p/project-zero/issues/detail?id=1225&desc=6
Can be set with:
x = document.createElement("a");
x.setAttribute("id", "base_url");
Can be set defined with
<value id="g_loosebasematching" />
Used to send Remote Procedure Calls (RPC)
leading to RCE](https://image.slidesharecdn.com/owaspsf-reviewingmodernjavascriptapplications-190207230816/85/OWASP-SF-Reviewing-Modern-JavaScript-Applications-32-320.jpg)


![Insecure Object Comparisons
• Similar to DOM Clobbering, there are many other ways insecure comparisons can happen
const SESSIONS = {}
const mustBeAuthenticated = (req, res, next) => {
if(req.cookies) {
const token = req.cookies.token
if(token && SESSIONS[token]) {
//allow it
next()
}
}
res.send('not authorized!')
}](https://image.slidesharecdn.com/owaspsf-reviewingmodernjavascriptapplications-190207230816/85/OWASP-SF-Reviewing-Modern-JavaScript-Applications-35-320.jpg)
![Comparison Table
Value Return
SESSIONS['invalidString'] False
SESSIONS[''] False
SESSIONS['constructor'] True
SESSIONS['hasOwnPropery'] True](https://image.slidesharecdn.com/owaspsf-reviewingmodernjavascriptapplications-190207230816/85/OWASP-SF-Reviewing-Modern-JavaScript-Applications-36-320.jpg)
![What Happens When You Create an Object in Javascript?
const test = {}
__proto__:
constructor: ƒ Object()
hasOwnProperty: ƒ hasOwnProperty()
isPrototypeOf: ƒ isProrotypeOf()
[...]
test['constructor'] === test.constructor //returns true](https://image.slidesharecdn.com/owaspsf-reviewingmodernjavascriptapplications-190207230816/85/OWASP-SF-Reviewing-Modern-JavaScript-Applications-37-320.jpg)


![How Do We Correctly Check?
• Or you can use a Map instead of an Object
SESSIONS.hasOwnProperty['__proto__']
// false
SESSIONS.hasOwnProperty['validString']
// true
SESSIONS.has(‘__proto__');
// false
SESSIONS.has(‘validString');
// true](https://image.slidesharecdn.com/owaspsf-reviewingmodernjavascriptapplications-190207230816/85/OWASP-SF-Reviewing-Modern-JavaScript-Applications-40-320.jpg)



