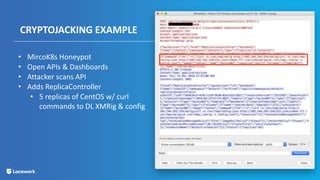
James Condon presented the top 10 threats to cloud security. These included cryptojacking, data leaks from misconfigurations, SSH brute force attacks, data exfiltration by advanced persistent threats, malware like ransomware and coin miners, remote code execution from vulnerabilities, container escapes, server compromises, and malicious insiders. Mitigations involved visibility, access controls, patching, monitoring, and security best practices.