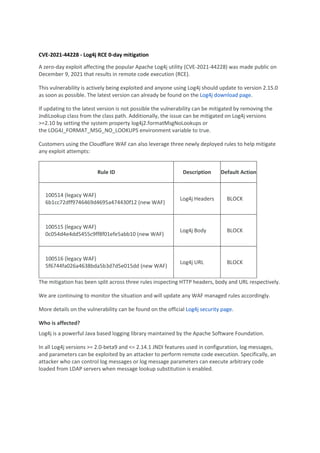
The document discusses two recent CISA advisories regarding cybersecurity threats. The first advisory outlines a serious vulnerability in the popular Log4j logging software that allows for remote code execution. The second advisory explores how ransomware attacks have increased in sophistication in 2021, becoming more "professional" with ransomware-as-a-service and cybercriminal services. The advisory provides recommendations to network defenders to reduce risks of ransomware compromise through practices like network segmentation, end-to-end encryption, and monitoring for abnormal activity.