Research Issues
•Download as DOCX, PDF•
0 likes•28 views
Issues of Paper
Report
Share
Report
Share
Recommended
Recommended
Embedded computing is everywhere. It is in our car engines, refrigerators, and even in the singing greeting cards we send. With improvements in wireless technology, these systems are starting to talk with each other, and they are appearing in places like our shoes and wrists to monitor our athletic activity or health. This emerging Internet of Everything (IoE) has tremendous potential to improve our lives. But like any powerful technology, it also has a dark side: it will observe and implement many of our actions. Security in the IoE is likely to be even more critical than general Internet security. After reviewing some of the challenges in creating a secure IoE, Horowitz will describe a new research program at Stanford to address this issue.Mark Horowitz - Stanford Engineering - Securing the Internet of Things

Mark Horowitz - Stanford Engineering - Securing the Internet of ThingsStanford School of Engineering
More Related Content
What's hot
Embedded computing is everywhere. It is in our car engines, refrigerators, and even in the singing greeting cards we send. With improvements in wireless technology, these systems are starting to talk with each other, and they are appearing in places like our shoes and wrists to monitor our athletic activity or health. This emerging Internet of Everything (IoE) has tremendous potential to improve our lives. But like any powerful technology, it also has a dark side: it will observe and implement many of our actions. Security in the IoE is likely to be even more critical than general Internet security. After reviewing some of the challenges in creating a secure IoE, Horowitz will describe a new research program at Stanford to address this issue.Mark Horowitz - Stanford Engineering - Securing the Internet of Things

Mark Horowitz - Stanford Engineering - Securing the Internet of ThingsStanford School of Engineering
What's hot (19)
International Journal of Wireless Networks Systems (IJWNS)

International Journal of Wireless Networks Systems (IJWNS)
International Journal of Wireless Networks Systems (IJWNS)

International Journal of Wireless Networks Systems (IJWNS)
International Journal of Wireless Networks Systems (IJWNS)

International Journal of Wireless Networks Systems (IJWNS)
International Journal of Wireless Networks Systems (IJWNS)

International Journal of Wireless Networks Systems (IJWNS)
International Journal of Wireless Networks Systems (IJWNS)

International Journal of Wireless Networks Systems (IJWNS)
Top cited 2nd articles in 2017 - International Journal of Network Security & ...

Top cited 2nd articles in 2017 - International Journal of Network Security & ...
Mark Horowitz - Stanford Engineering - Securing the Internet of Things

Mark Horowitz - Stanford Engineering - Securing the Internet of Things
Wireless Sensor Network Nodes: Security and Deployment in the Niger-Delta Oil...

Wireless Sensor Network Nodes: Security and Deployment in the Niger-Delta Oil...
Similar to Research Issues
The security in wireless sensor networks (WSNS) is a very important issue. These networks may be exposed
it different attacks. With this in mind, researchers propose in this area variety of security techniques for
this purpose, and this article describes security in wireless sensor networks. Discussed threats and attacks
of wireless sensor networks. The article also aims to provide the basic information related to determining
essential requirements for the protection WSNs. Lastly, we mention some security mechanisms against
these threats and attacks in Wireless Sensor Network.Wireless Sensor Networks, Security Requirements, Attacks, Security Mechanisms.

Wireless Sensor Networks, Security Requirements, Attacks, Security Mechanisms.AIRCC Publishing Corporation
Similar to Research Issues (20)
SECURITY IN WIRELESS SENSOR NETWORKS: COMPARATIVE STUDY

SECURITY IN WIRELESS SENSOR NETWORKS: COMPARATIVE STUDY
Wireless Sensor Networks, Security Requirements, Attacks, Security Mechanisms.

Wireless Sensor Networks, Security Requirements, Attacks, Security Mechanisms.
A SERVEY ON WIRELESS SENSOR NETWORK SECURITY ISSUES & CHALLENGES

A SERVEY ON WIRELESS SENSOR NETWORK SECURITY ISSUES & CHALLENGES
A Security Framework for Replication Attacks in Wireless Sensor Networks

A Security Framework for Replication Attacks in Wireless Sensor Networks
Analysis of security threats in wireless sensor network

Analysis of security threats in wireless sensor network
International Journal of Engineering and Science Invention (IJESI)

International Journal of Engineering and Science Invention (IJESI)
Multi-stage secure clusterhead selection using discrete rule-set against unkn...

Multi-stage secure clusterhead selection using discrete rule-set against unkn...
Tactical approach to identify and quarantine spurious node participation requ...

Tactical approach to identify and quarantine spurious node participation requ...
Submit Your Research Articles - International Journal of Network Security & I...

Submit Your Research Articles - International Journal of Network Security & I...
A review of privacy preserving techniques in wireless sensor network

A review of privacy preserving techniques in wireless sensor network
A review of privacy preserving techniques in wireless sensor network

A review of privacy preserving techniques in wireless sensor network
International Journal of Network Security & Its Applications (IJNSA) - ERA, W...

International Journal of Network Security & Its Applications (IJNSA) - ERA, W...
SECURITY AND KEY MANAGEMENT CHALLENGES OVER WSN (A SURVEY) 

SECURITY AND KEY MANAGEMENT CHALLENGES OVER WSN (A SURVEY)
SECURITY AND KEY MANAGEMENT CHALLENGES OVER WSN (A SURVEY) 

SECURITY AND KEY MANAGEMENT CHALLENGES OVER WSN (A SURVEY)
Next Generation Network: Security and Architecture

Next Generation Network: Security and Architecture
Recently uploaded
Differences between analog and digital communicationanalog-vs-digital-communication (concept of analog and digital).pptx

analog-vs-digital-communication (concept of analog and digital).pptxKarpagam Institute of Teechnology
Recently uploaded (20)
Involute of a circle,Square, pentagon,HexagonInvolute_Engineering Drawing.pdf

Involute of a circle,Square, pentagon,HexagonInvolute_Engineering Drawing.pdf
UNIT-2 image enhancement.pdf Image Processing Unit 2 AKTU

UNIT-2 image enhancement.pdf Image Processing Unit 2 AKTU
Software Engineering Practical File Front Pages.pdf

Software Engineering Practical File Front Pages.pdf
Developing a smart system for infant incubators using the internet of things ...

Developing a smart system for infant incubators using the internet of things ...
5G and 6G refer to generations of mobile network technology, each representin...

5G and 6G refer to generations of mobile network technology, each representin...
Filters for Electromagnetic Compatibility Applications

Filters for Electromagnetic Compatibility Applications
Seizure stage detection of epileptic seizure using convolutional neural networks

Seizure stage detection of epileptic seizure using convolutional neural networks
Instruct Nirmaana 24-Smart and Lean Construction Through Technology.pdf

Instruct Nirmaana 24-Smart and Lean Construction Through Technology.pdf
Maximizing Incident Investigation Efficacy in Oil & Gas: Techniques and Tools

Maximizing Incident Investigation Efficacy in Oil & Gas: Techniques and Tools
8th International Conference on Soft Computing, Mathematics and Control (SMC ...

8th International Conference on Soft Computing, Mathematics and Control (SMC ...
NO1 Best Powerful Vashikaran Specialist Baba Vashikaran Specialist For Love V...

NO1 Best Powerful Vashikaran Specialist Baba Vashikaran Specialist For Love V...
NEWLETTER FRANCE HELICES/ SDS SURFACE DRIVES - MAY 2024

NEWLETTER FRANCE HELICES/ SDS SURFACE DRIVES - MAY 2024
analog-vs-digital-communication (concept of analog and digital).pptx

analog-vs-digital-communication (concept of analog and digital).pptx
Artificial intelligence presentation2-171219131633.pdf

Artificial intelligence presentation2-171219131633.pdf
Research Issues
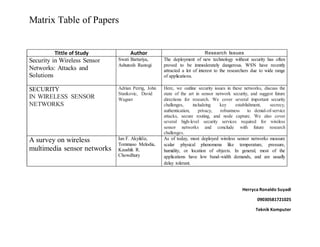
- 1. Matrix Table of Papers Herryca Ronaldo Suyadi 09030581721025 Teknik Komputer Tittle of Study Author Research Issues Security in Wireless Sensor Networks: Attacks and Solutions Swati Bartariya, Ashutosh Rastogi The deployment of new technology without security has often proved to be immoderately dangerous. WSN have recently attracted a lot of interest to the researchers due to wide range of applications. SECURITY IN WIRELESS SENSOR NETWORKS Adrian Perrig, John Stankovic, David Wagner Here, we outline security issues in these networks, discuss the state of the art in sensor network security, and suggest future directions for research. We cover several important security challenges, includeing key establishment, secrecy, authentication, privacy, robustness to denial-of-service attacks, secure routing, and node capture. We also cover several high-level security services required for wireless sensor networks and conclude with future research challenges. A survey on wireless multimedia sensor networks Ian F. Akyildiz, Tommaso Melodia, Kaushik R. Chowdhury As of today, most deployed wireless sensor networks measure scalar physical phenomena like temperature, pressure, humidity, or location of objects. In general, most of the applications have low band-width demands, and are usually delay tolerant.