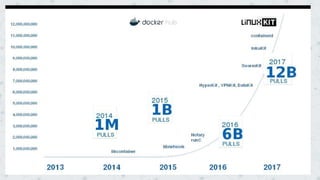
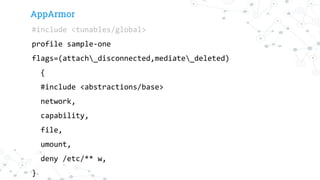
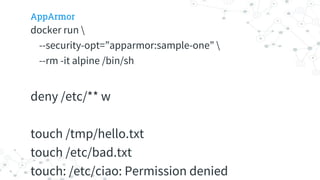
The document introduces a free ebook by Gianluca Arbezzano on Docker and container security, drawing from his experience in deploying and securing containers. It covers various topics including security practices like AppArmor and SELinux, image scanning with CoreOS Clair, and using BPF for efficient kernel operations. Additionally, it discusses concepts such as Docker Content Trust and Notary for secure image management and offers insights on maintaining secure container environments.

















![cilium policy allowed -s cilium:io.cilium.service.client
-d cilium:io.cilium.service.server
Resolving policy for context &{Trace:1
Logging:0xc42177b590
From:[cilium:io.cilium.service.client]
To:[cilium:io.cilium.service.server]}
Root rules decision: undecided
No matching children in io.cilium
Root children decision: undecided
Final tree decision: deny
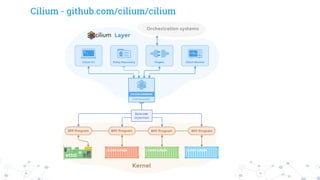
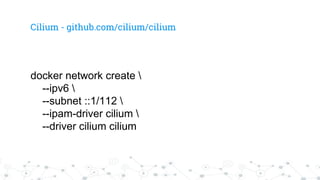
Cilium - github.com/cilium/cilium](https://image.slidesharecdn.com/dockersecurity-devopscon-170613201114/85/Security-Tips-to-run-Docker-in-Production-23-320.jpg)