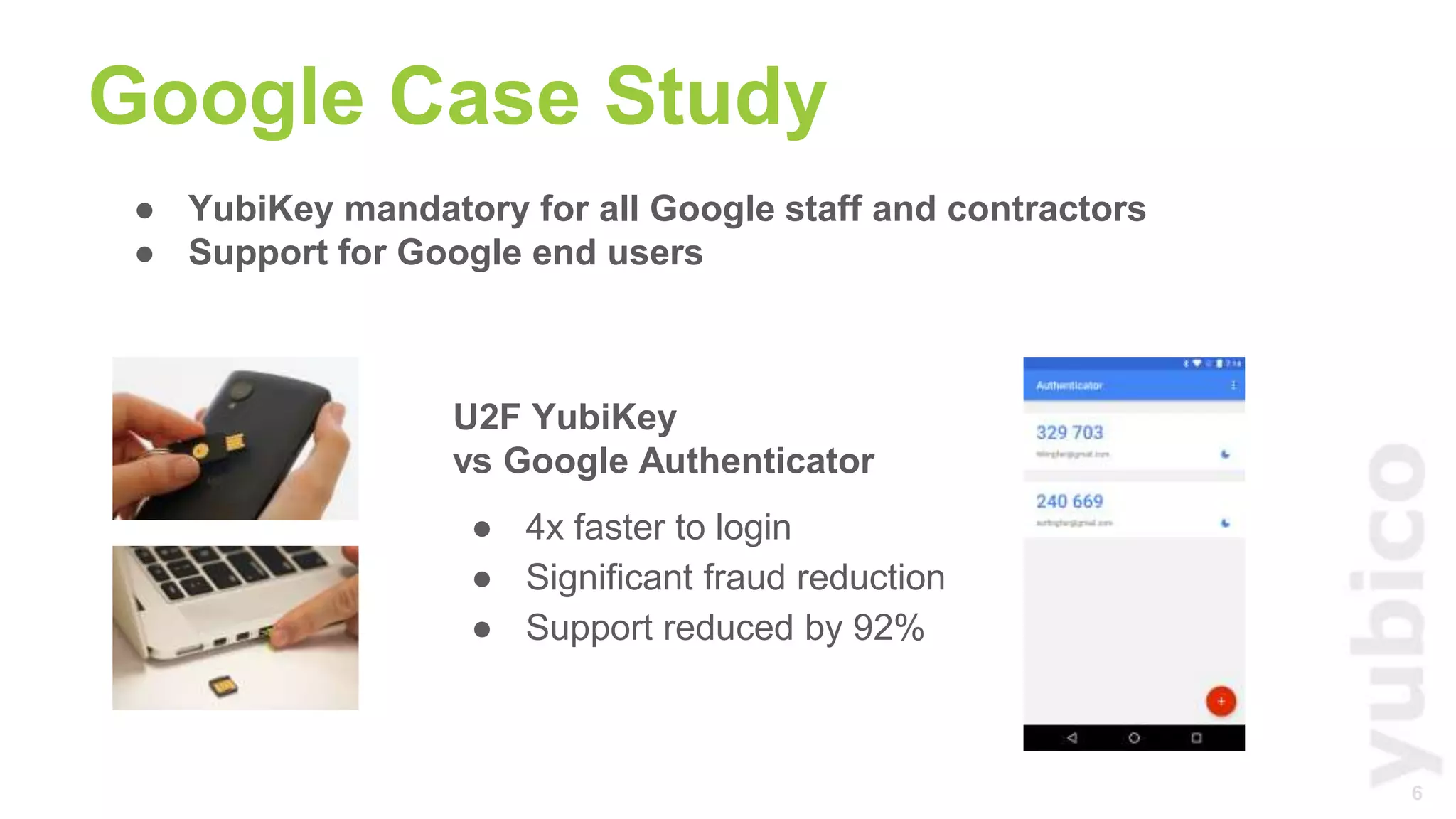
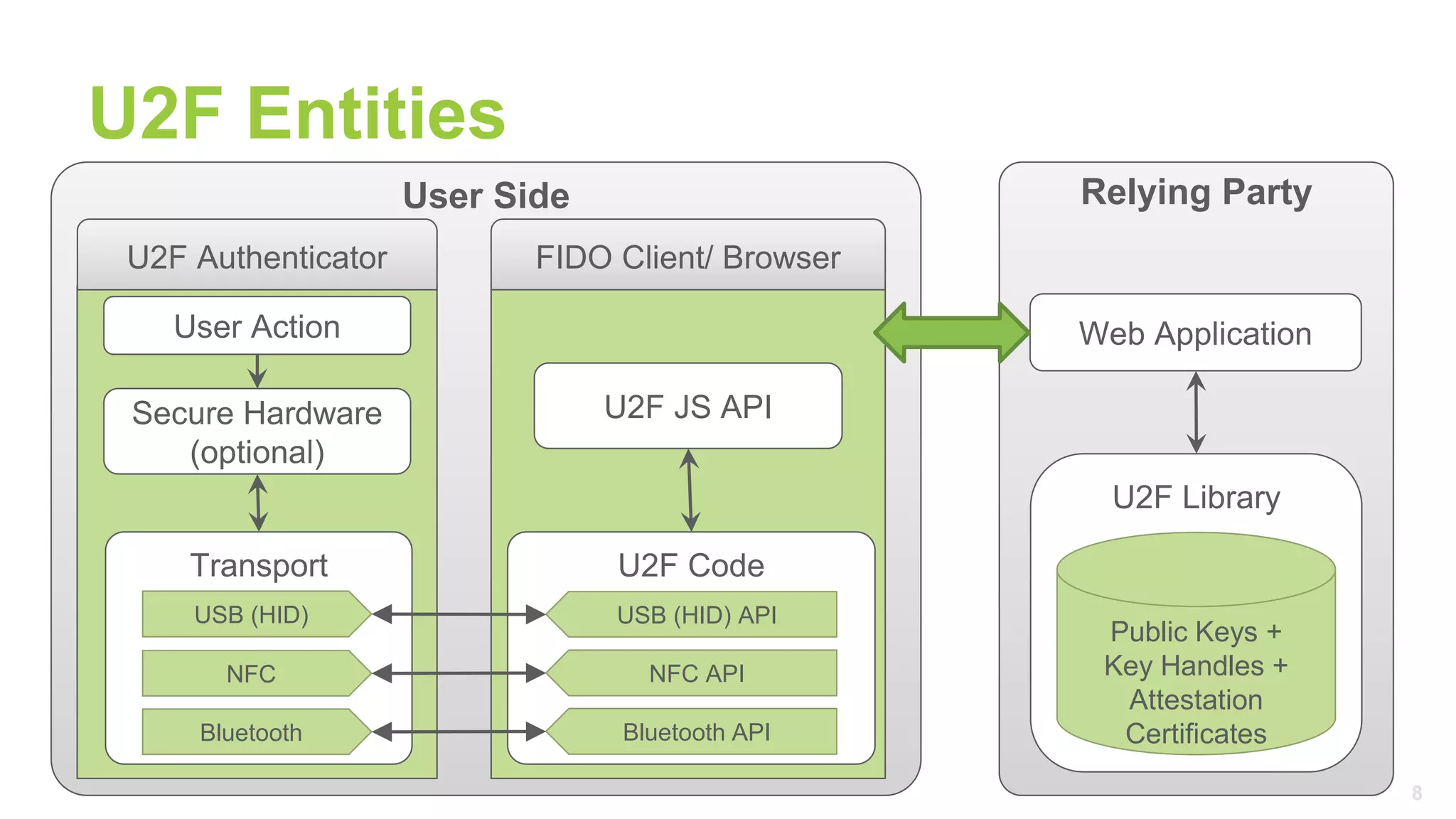
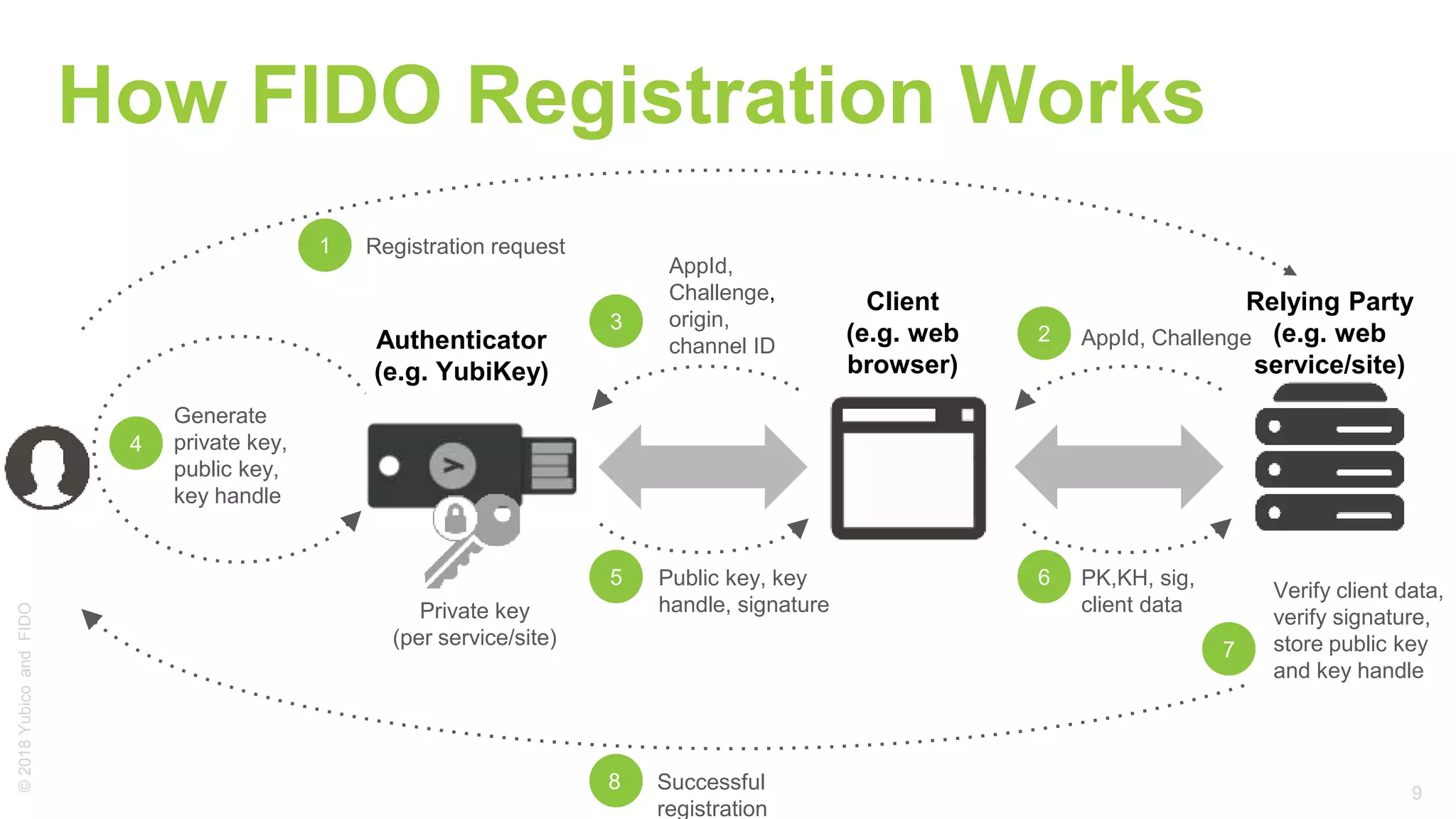
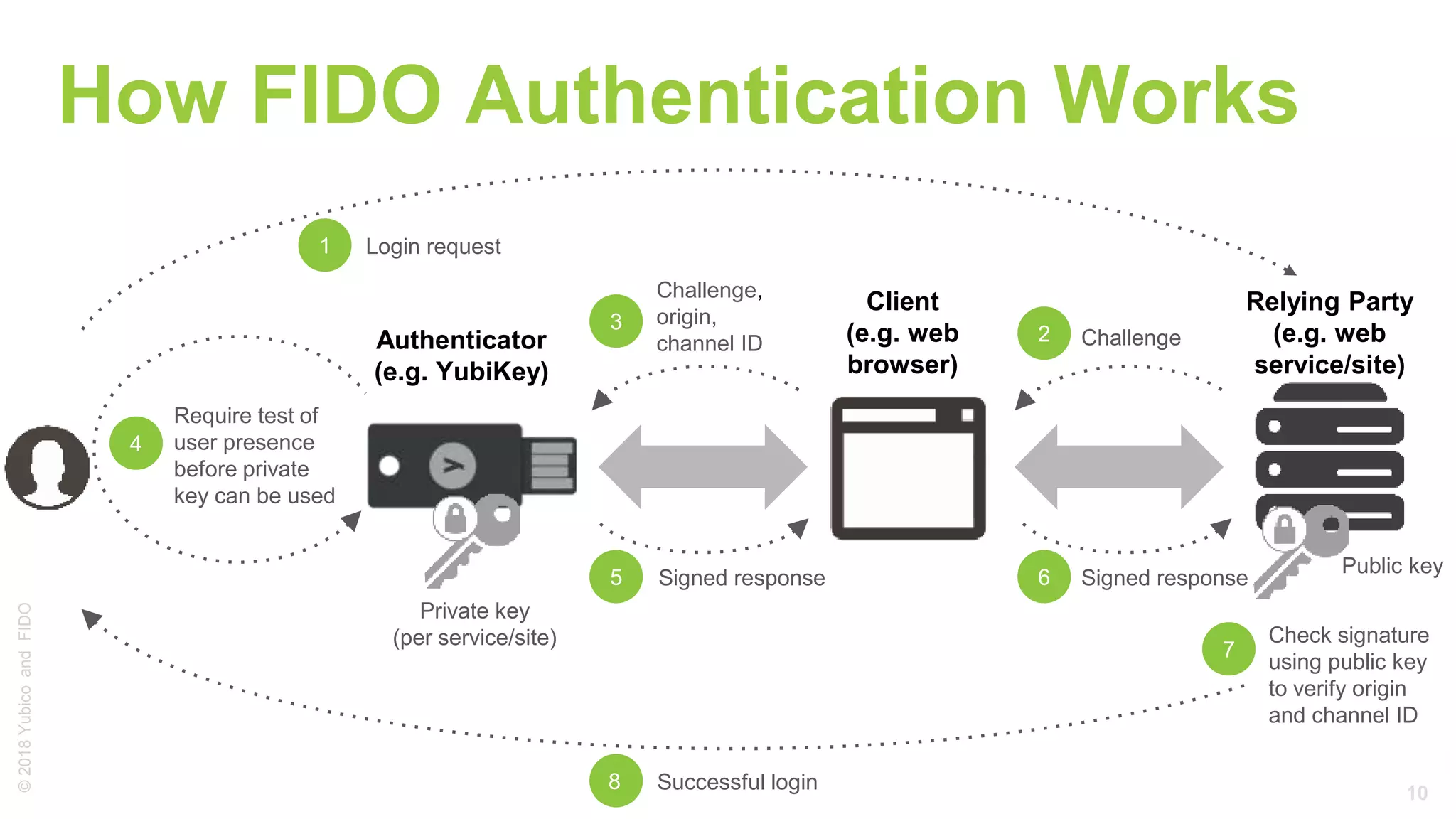
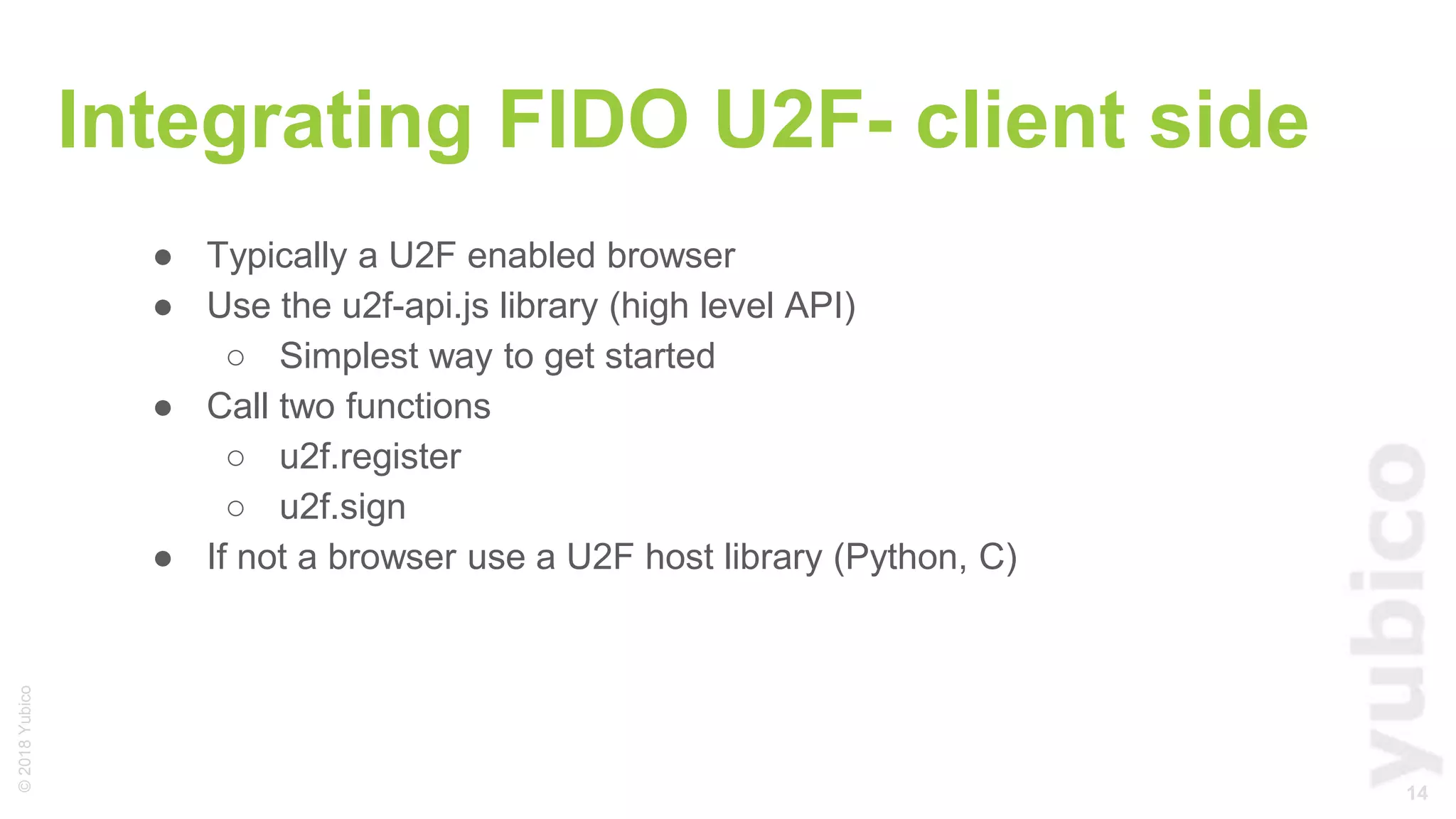
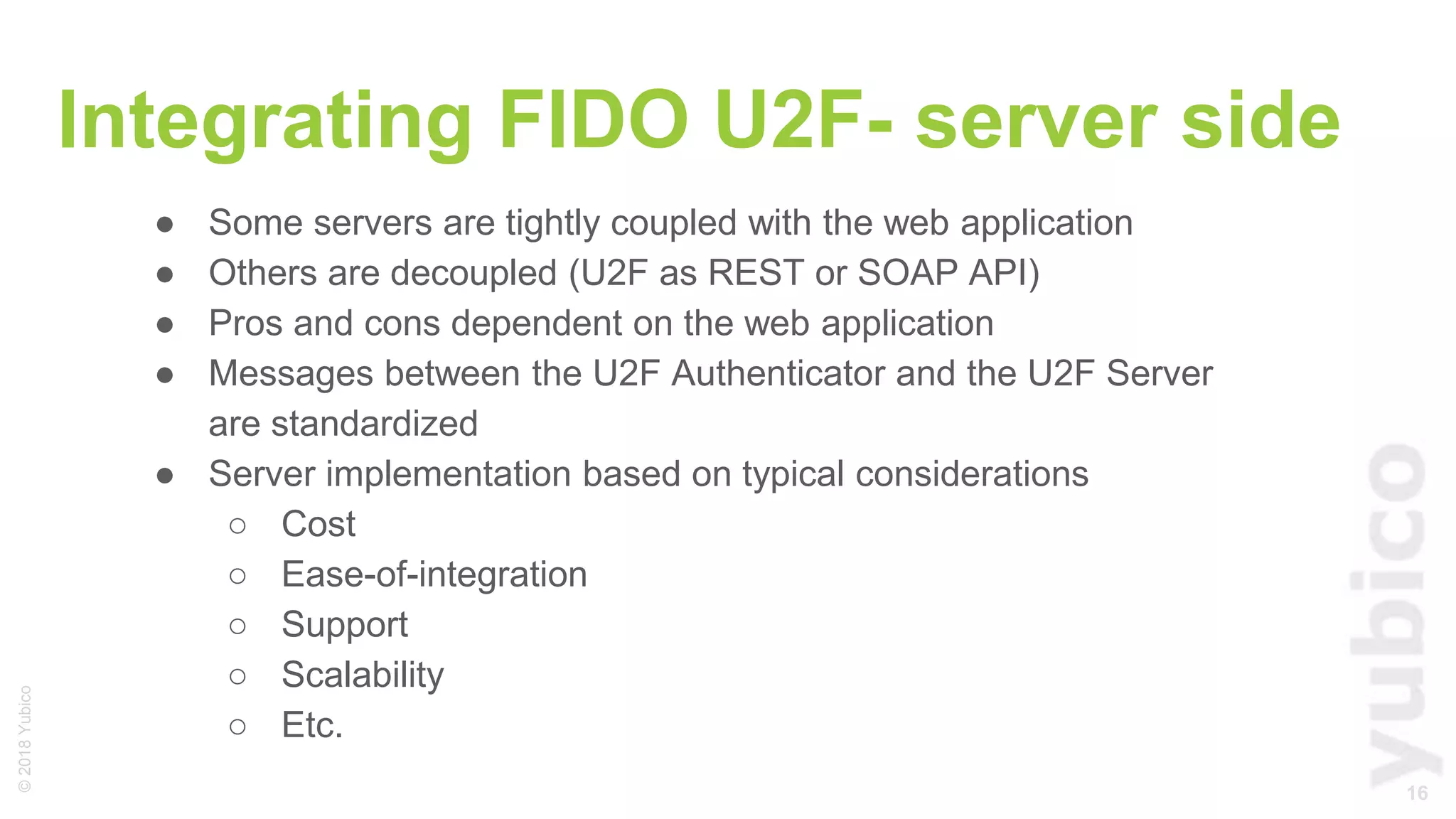
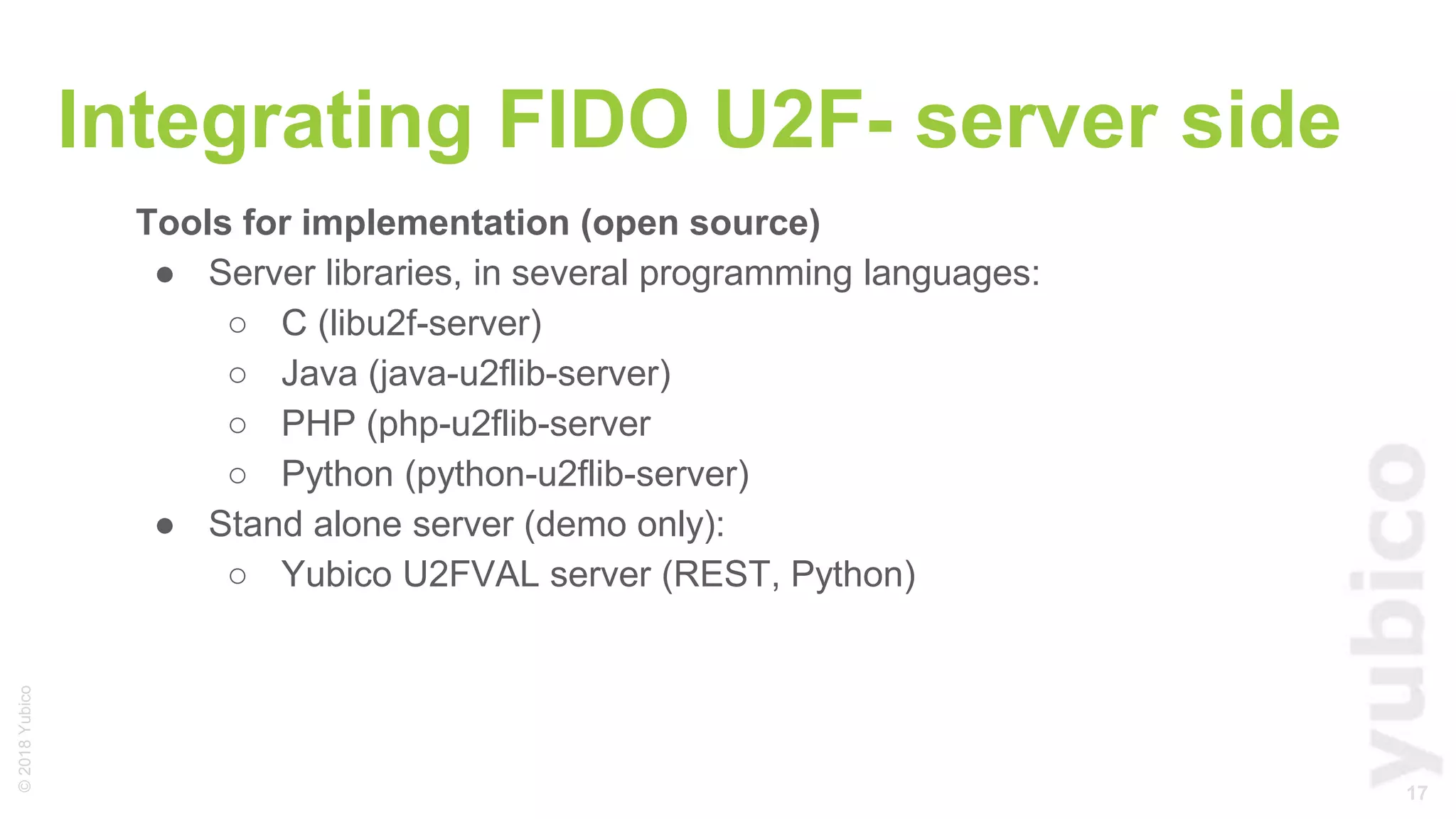
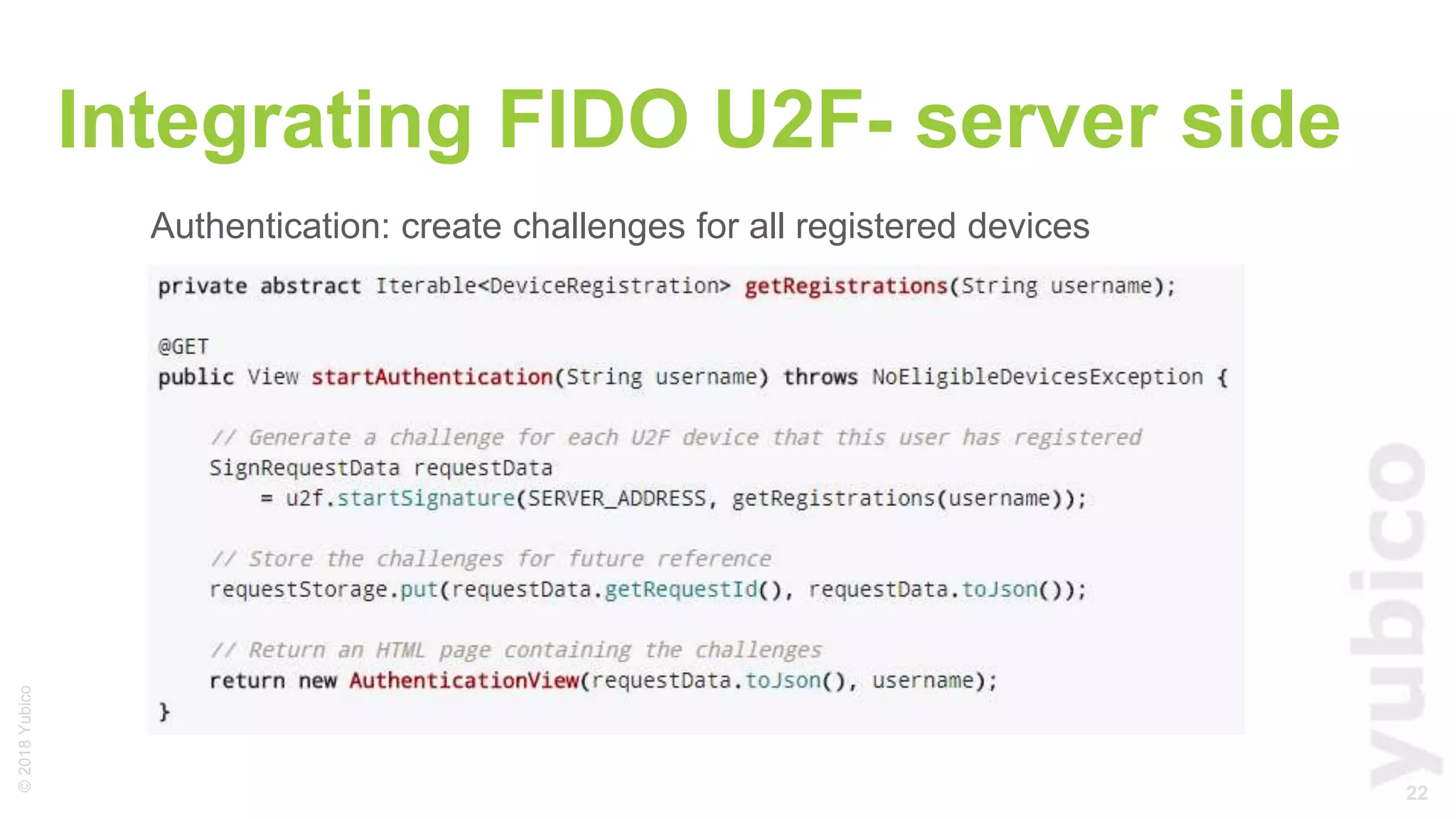
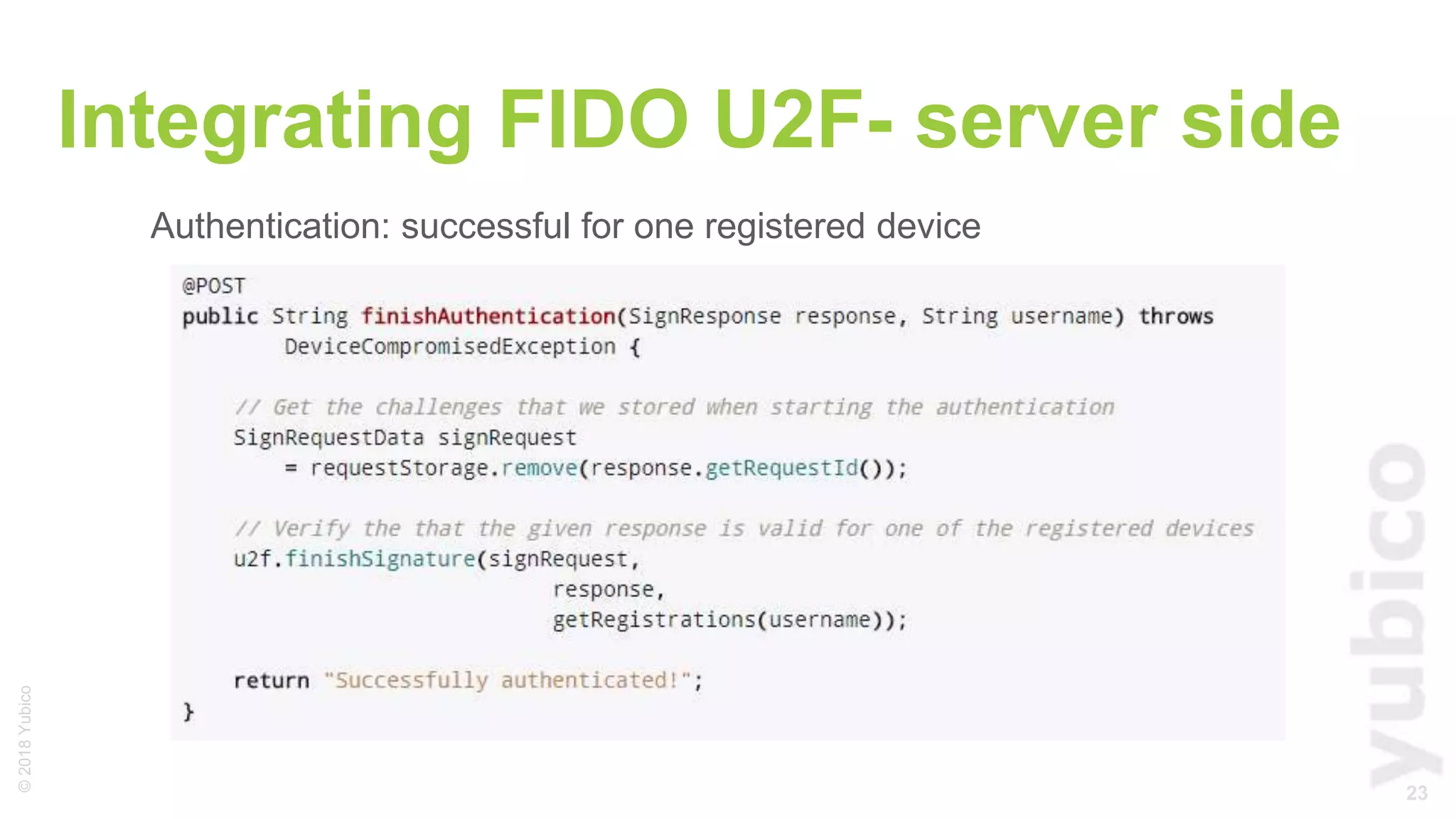
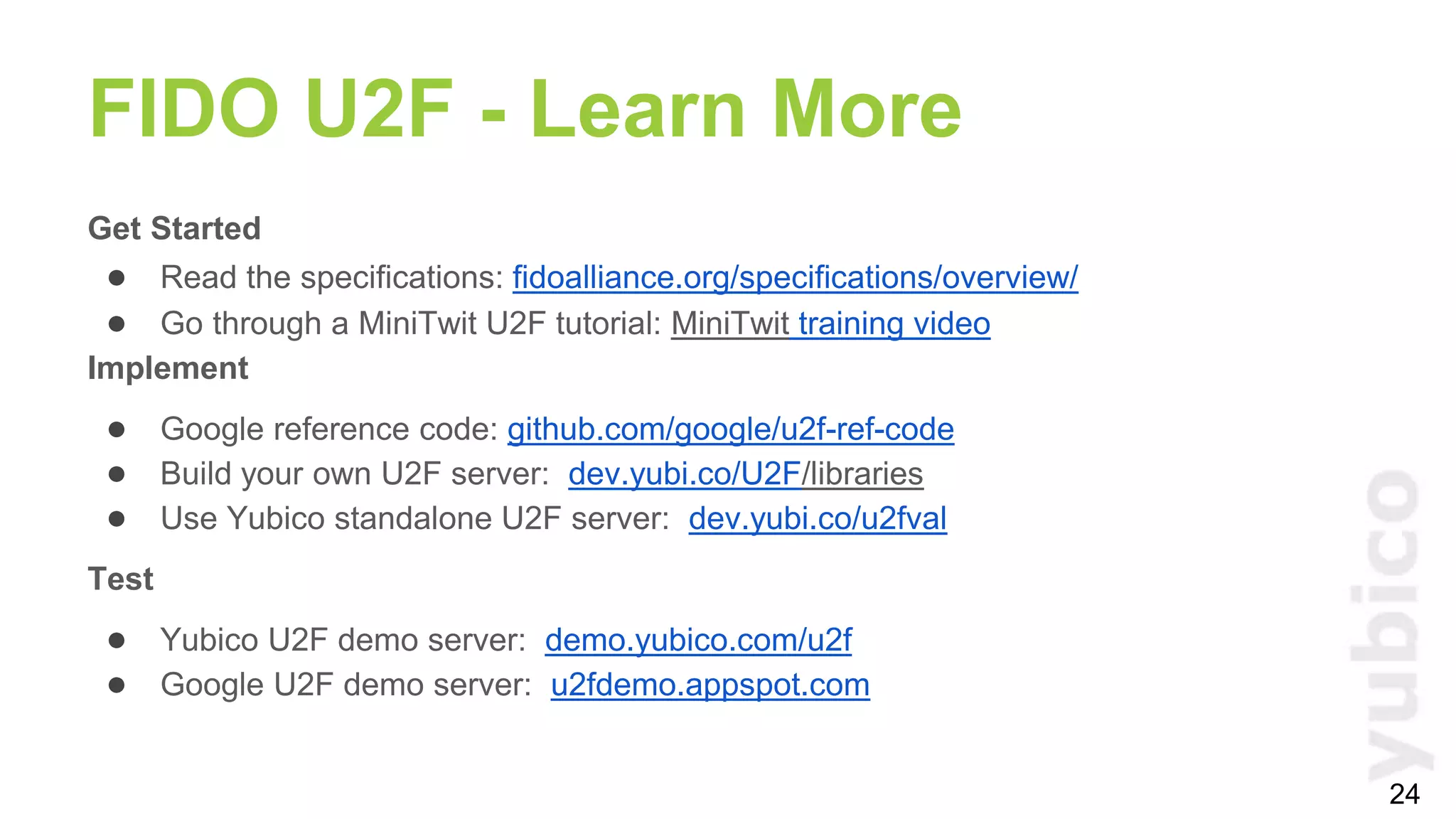
The document provides a comprehensive tutorial on FIDO U2F, a standard for secure authentication using hardware tokens like YubiKey. It covers the protocol's principles, integration methods for both client and server sides, and highlights the benefits of U2F, such as enhanced security and user convenience. Additionally, it includes demo instructions and links for further exploration and implementation resources.