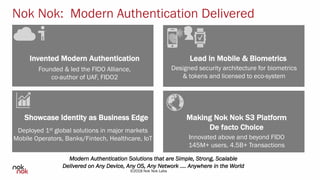
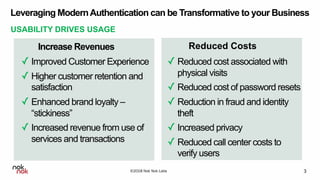
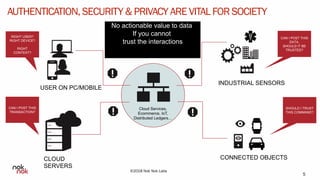
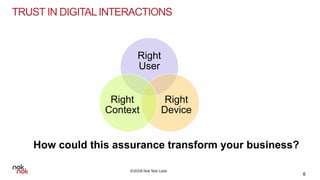
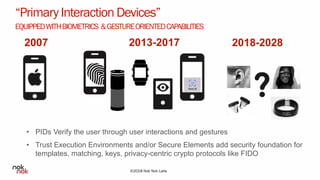
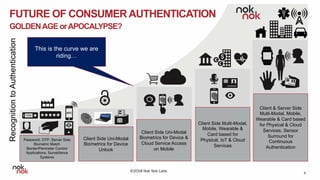
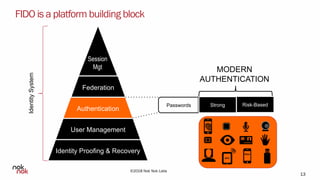
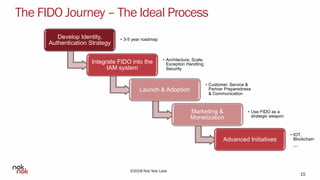
The document discusses modern authentication and Nok Nok Labs' role in pioneering this area. It notes that Nok Nok Labs invented modern authentication, founded and led the FIDO Alliance, and has deployed authentication solutions for major markets. The document promotes the benefits of leveraging modern authentication, such as improved customer experience, higher retention and satisfaction, and reduced fraud and costs. It argues that authentication, security, and privacy will be vital for society with the rise of cloud services, IoT, and other technologies.







![©2018 Nok Nok Labs
BENEFIT of a FIDO FRAMEWORK
Enabling MultifactorAuthentication
Easy for developer,IT& END-USER
RIGHTLEVELOFABSTRACTION
18
Something I
Know
Something
I Have
Something I Have
+
Something I
Know
Or
Something I
Have, Who I am
…
Or
[Something I
Have, Who I am]
x2
…
TapTouch
SAME DEVELOPER API, SAME BACKEND, DIFFERENT POLICY](https://image.slidesharecdn.com/deployingfidoauthentication-businessconsiderations-181005200956/85/Deploying-FIDO-Authentication-Business-Considerations-18-320.jpg)
