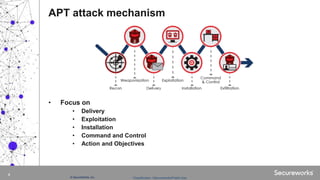
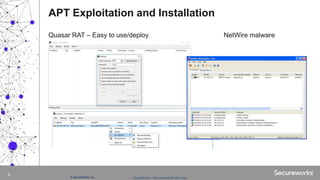
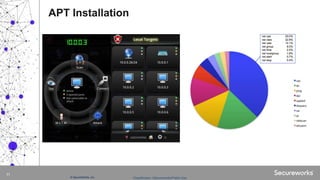
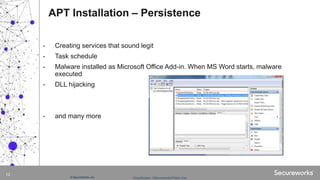
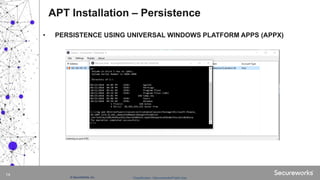
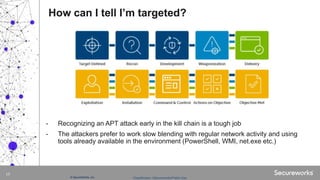
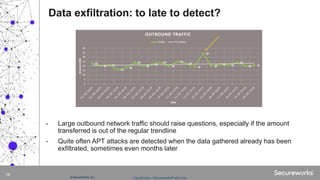
The document discusses advanced persistent threats (APTs), which are targeted cyberattacks that remain undetected for extended periods, often employing techniques initially associated with nation-state actors but now also used by cybercriminals. It outlines the mechanisms of an APT attack, including delivery, exploitation, installation, and lateral movement within networks, emphasizing the importance of identifying and detecting early signs of such attacks. To mitigate risks, organizations are advised to understand their assets, vulnerabilities, and adversaries while implementing robust multi-layered security measures.