The document summarizes key aspects of the upcoming EU General Data Protection Regulation (GDPR) as it relates to software development:
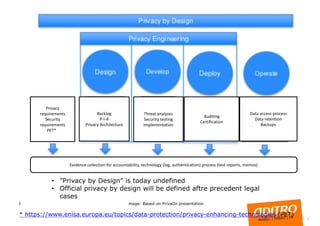
- The GDPR defines what organizations must do with personal data, but not how to implement it technically. Guidelines provide high-level principles like "privacy by design" but not specific tools or processes.
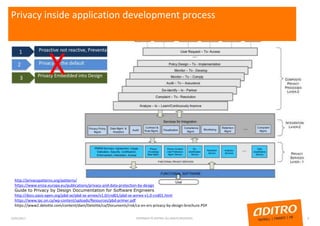
- To comply, developers must consider privacy throughout the design process using methods like data minimization, access controls, and encryption. Organizations must also be able to demonstrate and ensure ongoing compliance, such as through documentation and audits.
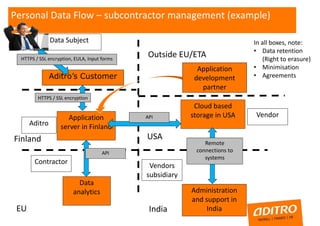
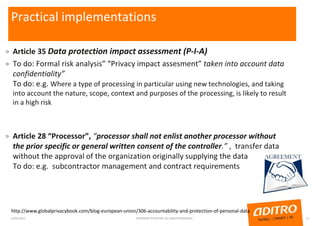
- The GDPR places new obligations on data controllers and processors around security, impact assessments, subcontractors, access requests, and accountability. While