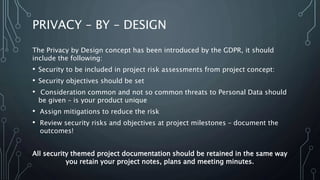
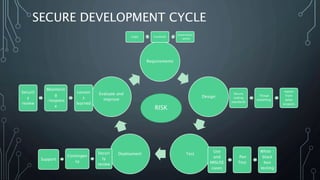
The Data Protection Act (DPA) 2018 establishes regulations governing personal data protection, emphasizing consent, security, and the rights of data subjects. It defines roles for data controllers and processors, introduces significant data rights, and mandates privacy by design in projects to ensure security and risk mitigation. Organizations must comply with incident reporting requirements and maintain contracts with third parties handling personal data, with substantial penalties for non-compliance.