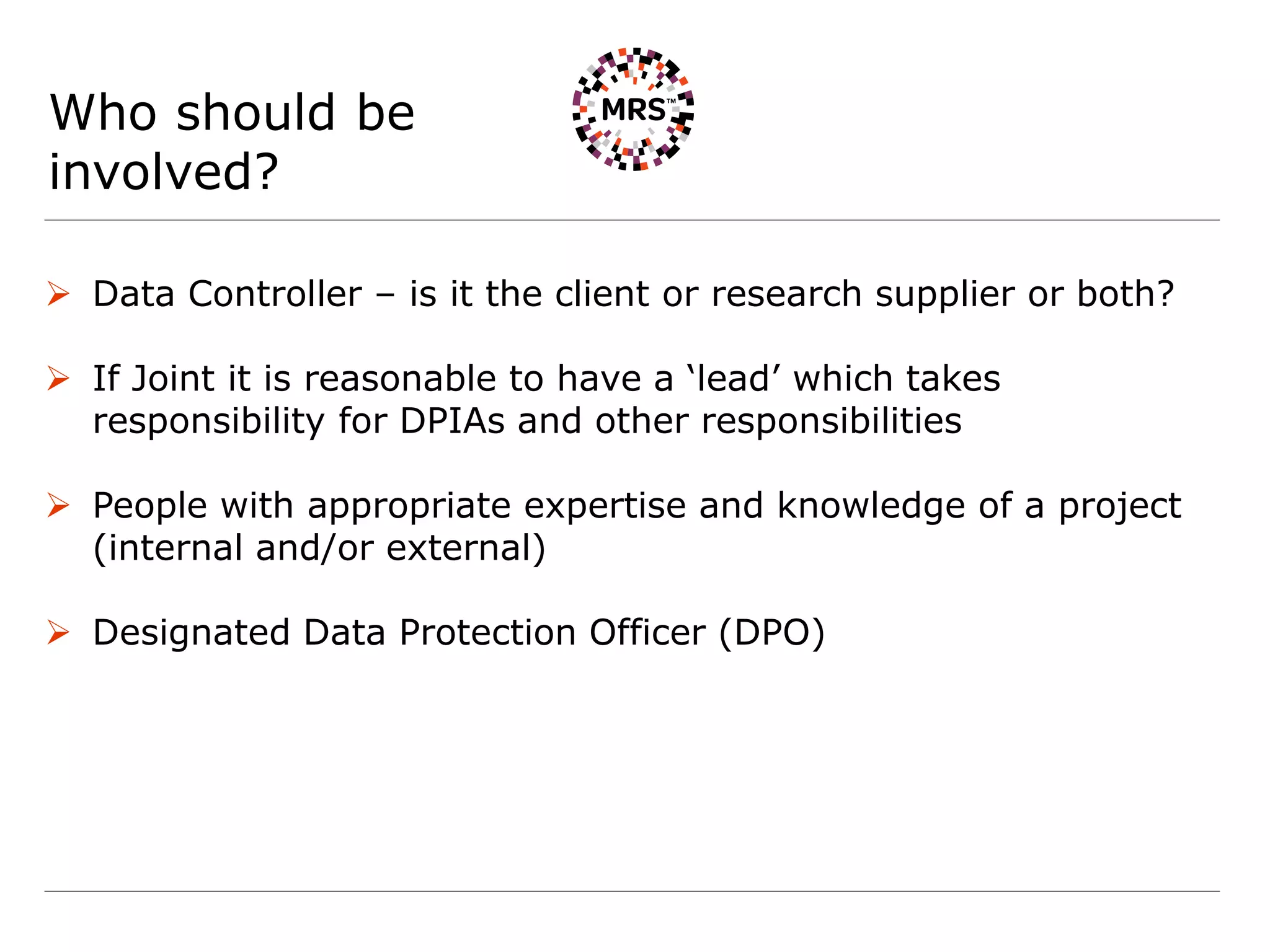
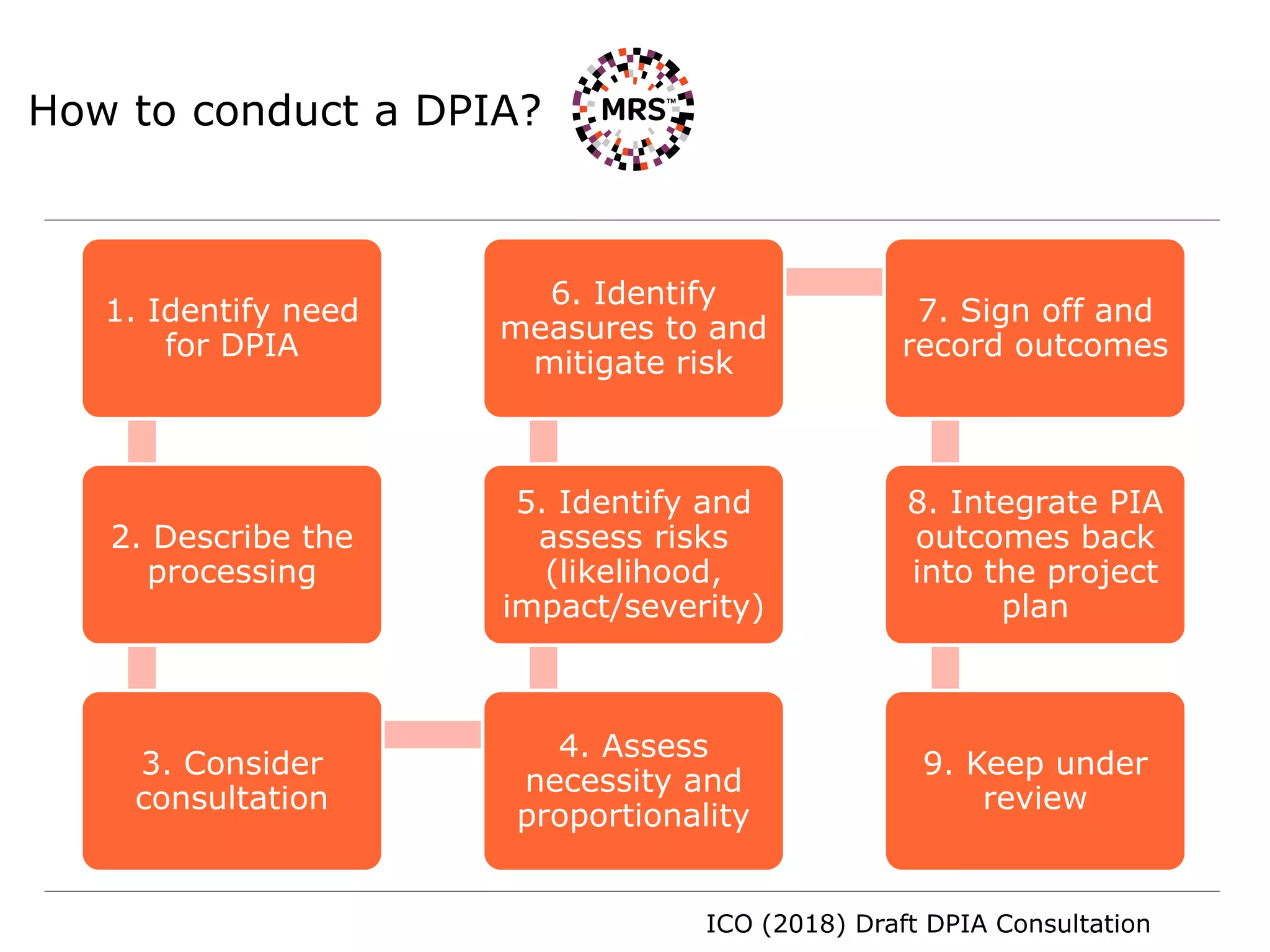
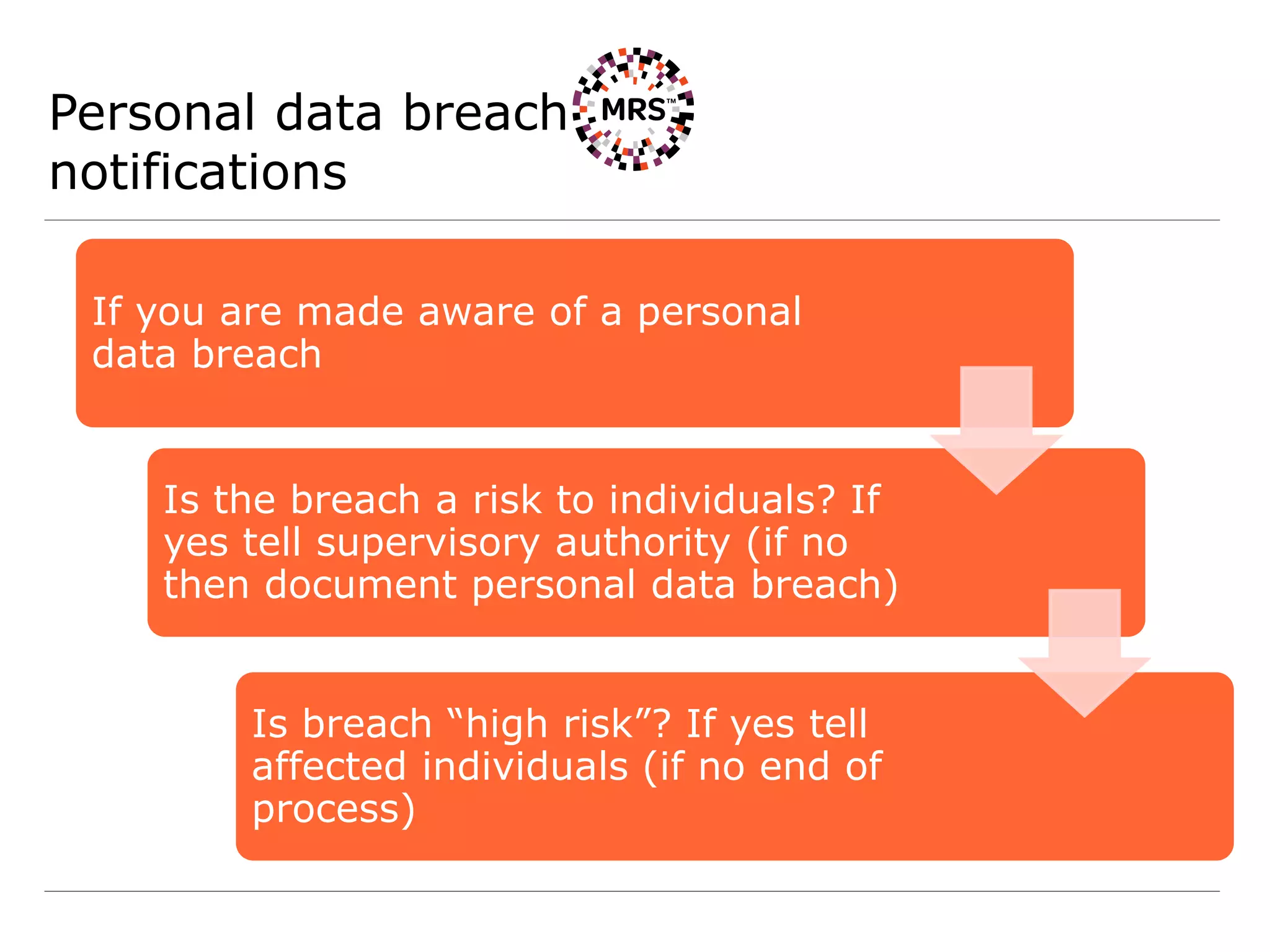
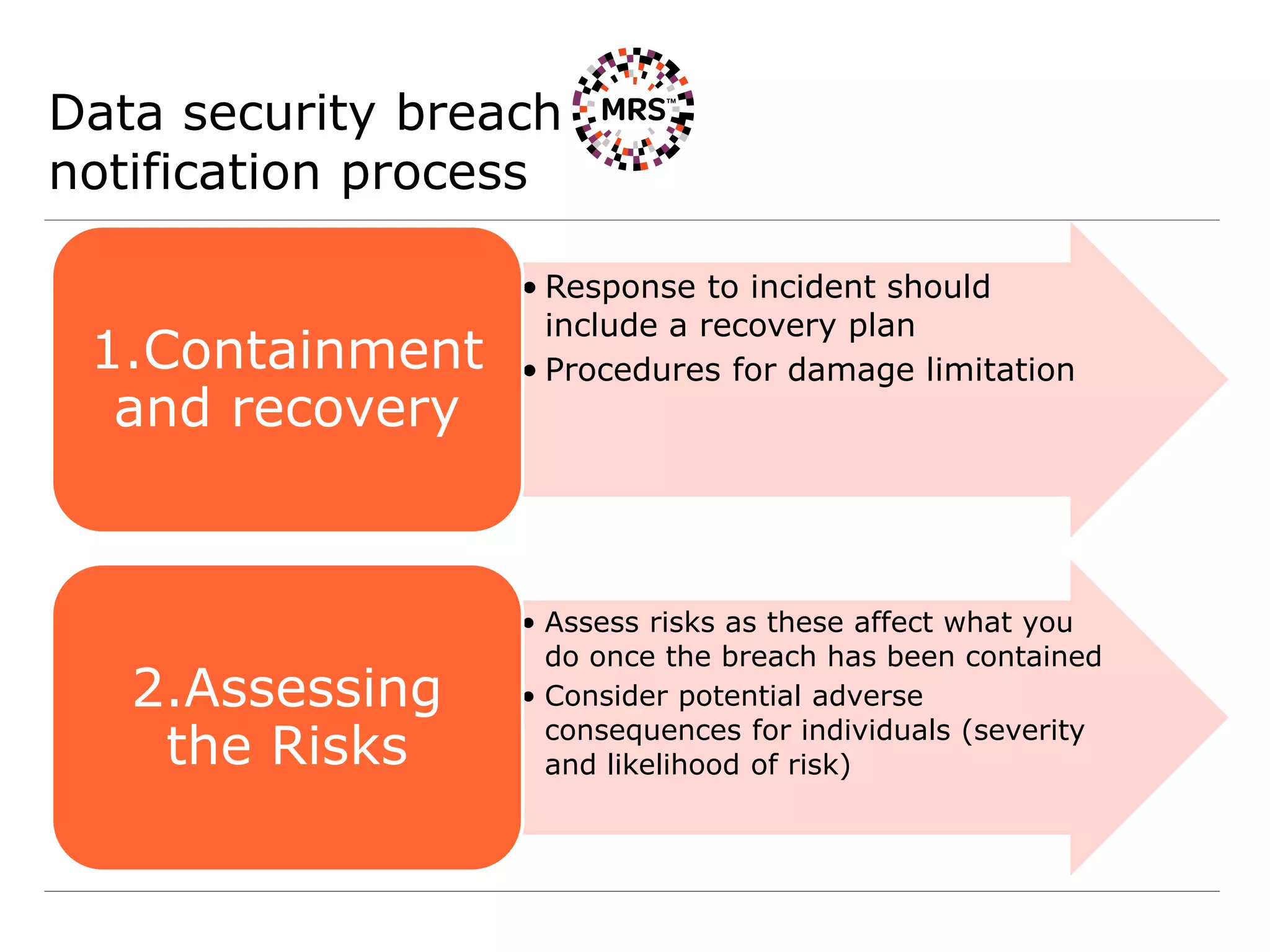
This document summarizes key organizational measures required by the General Data Protection Regulation (GDPR) for MRS Operations Network, including:
1) Reviewing existing supplier contracts and arrangements to ensure compliance, undertaking audits of suppliers as needed.
2) Including GDPR requirements in new supplier selection criteria and contracts.
3) Requiring data protection impact assessments for high-risk data processing such as large-scale or special category data.
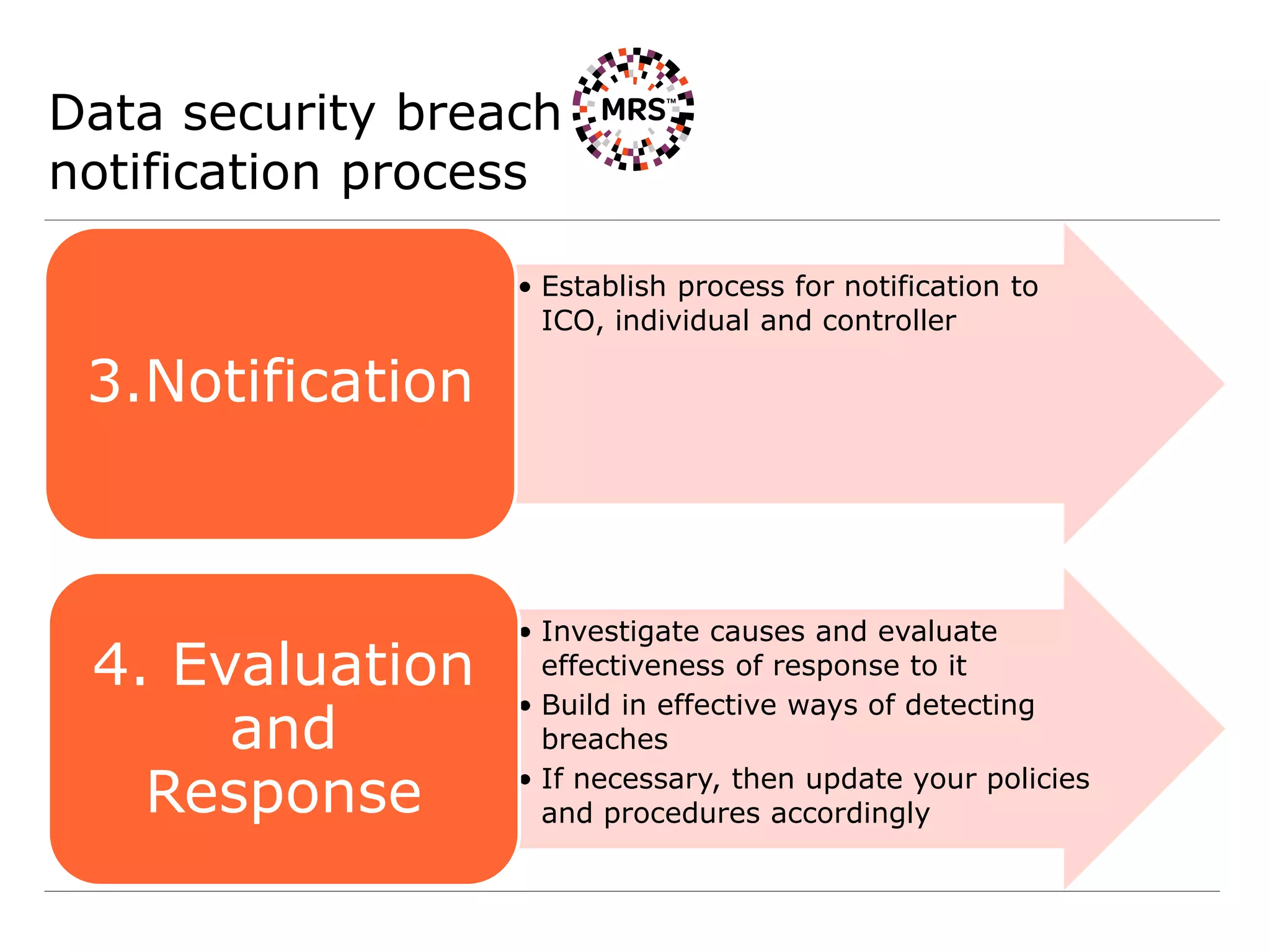
4) Establishing processes for personal data breach reporting to supervisory authorities and affected individuals as required.