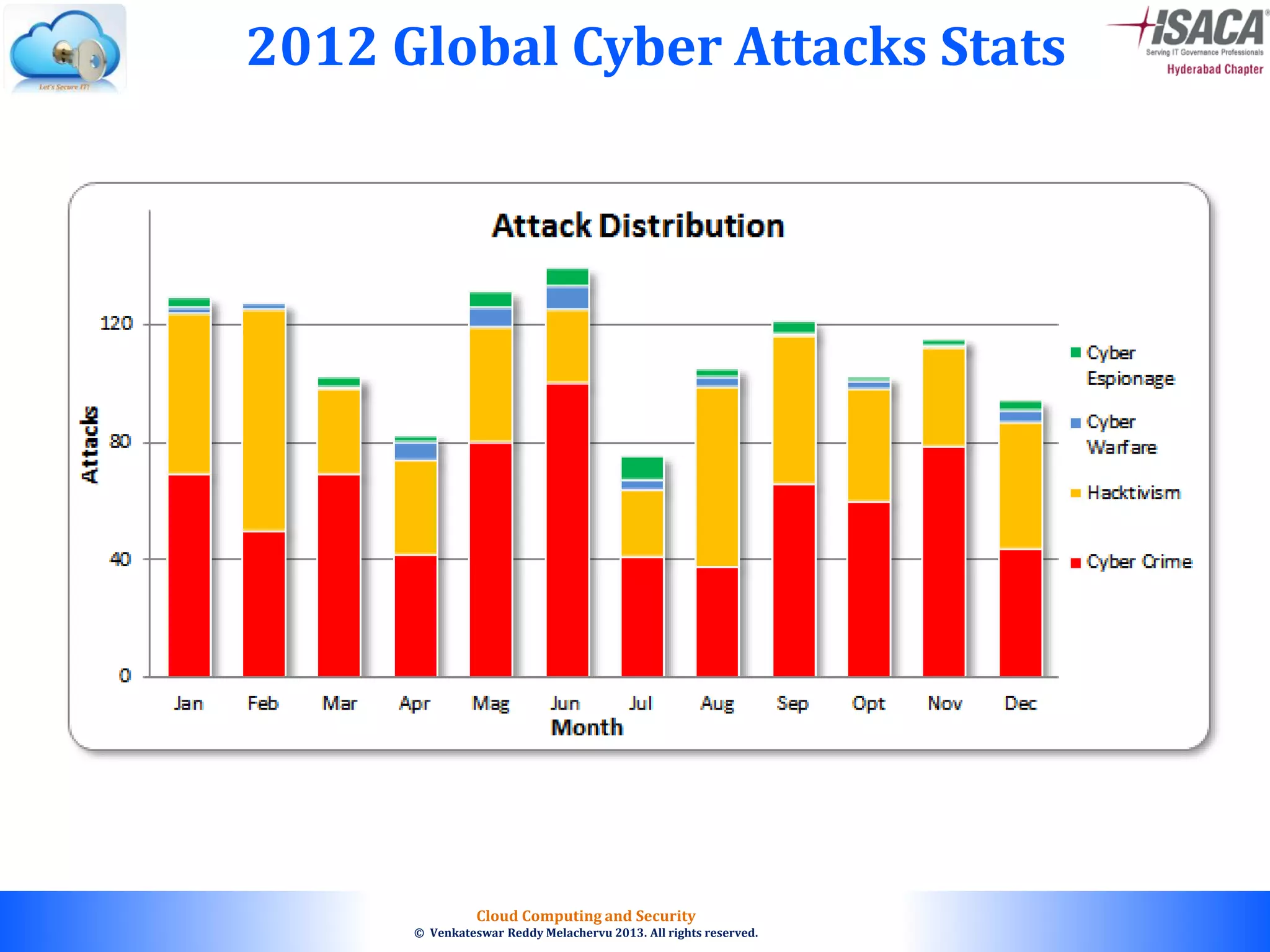
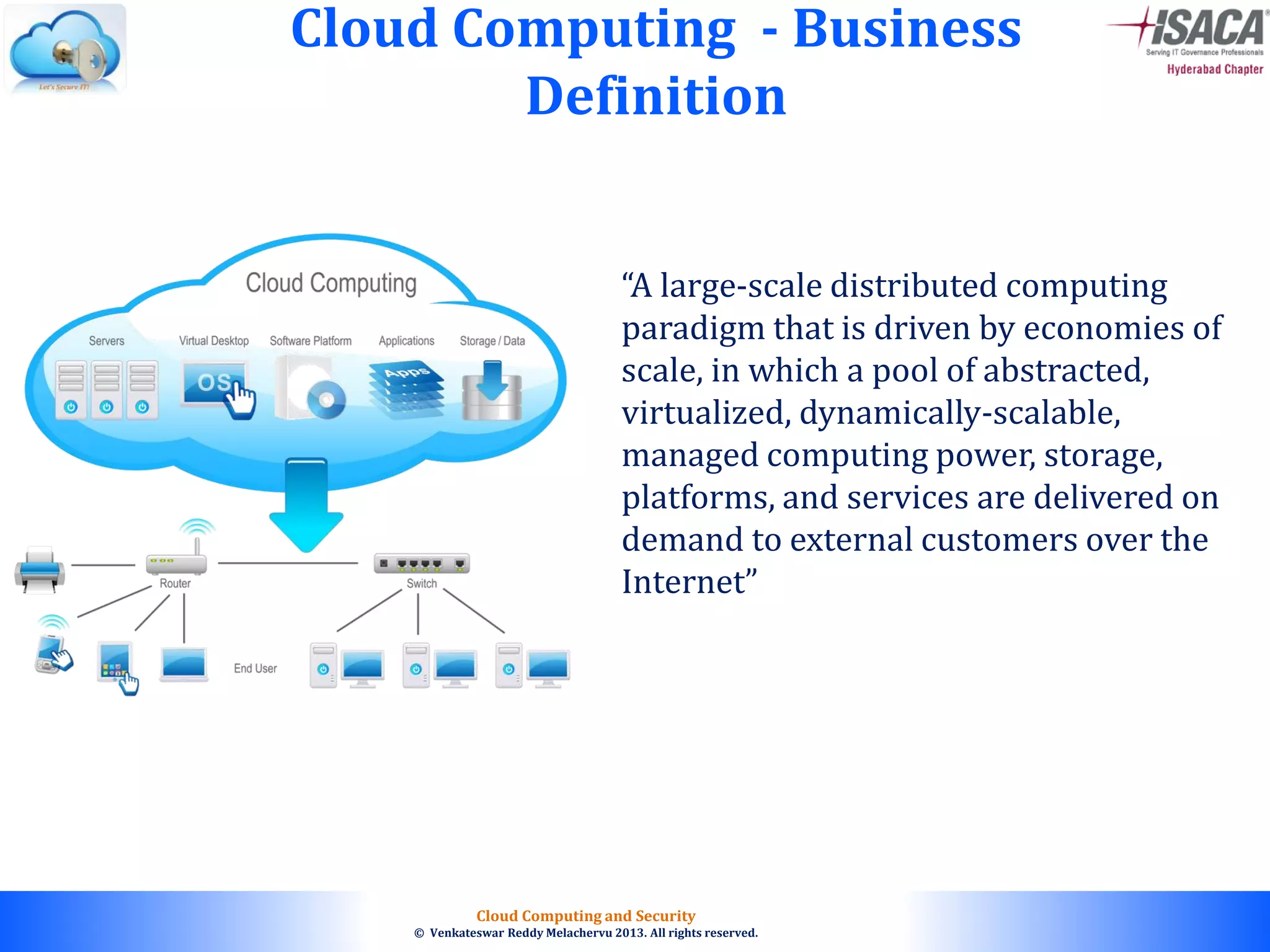
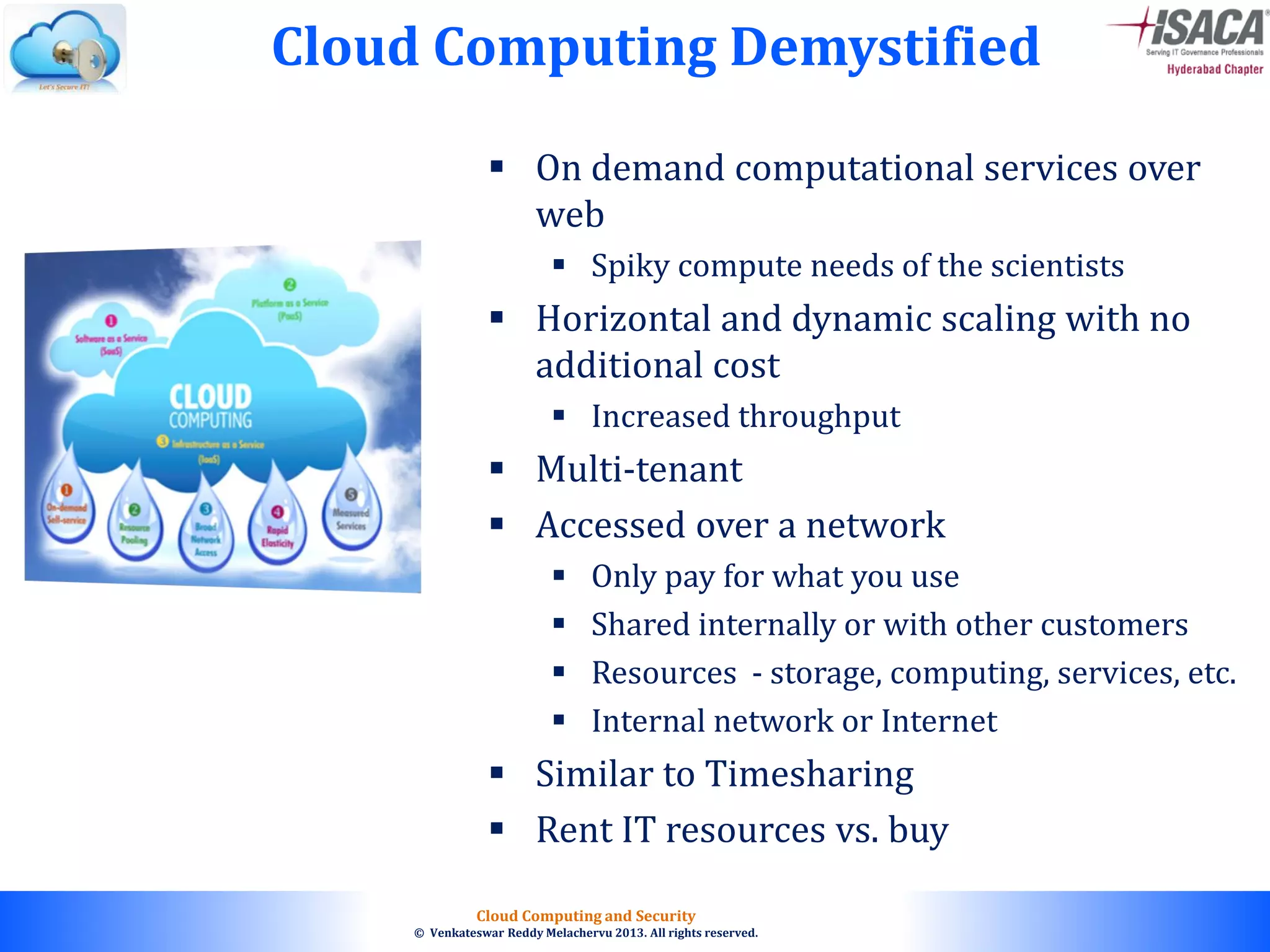
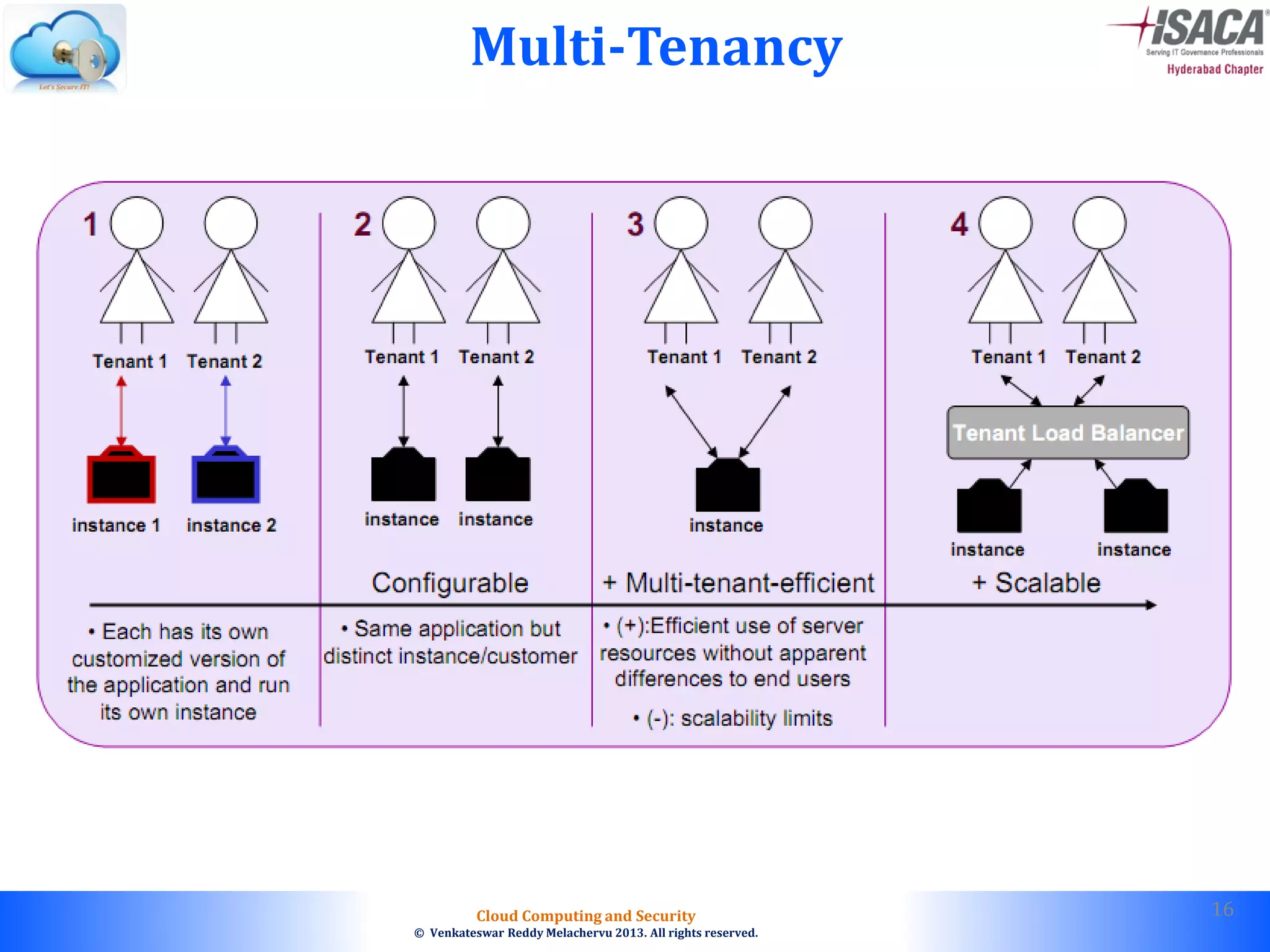
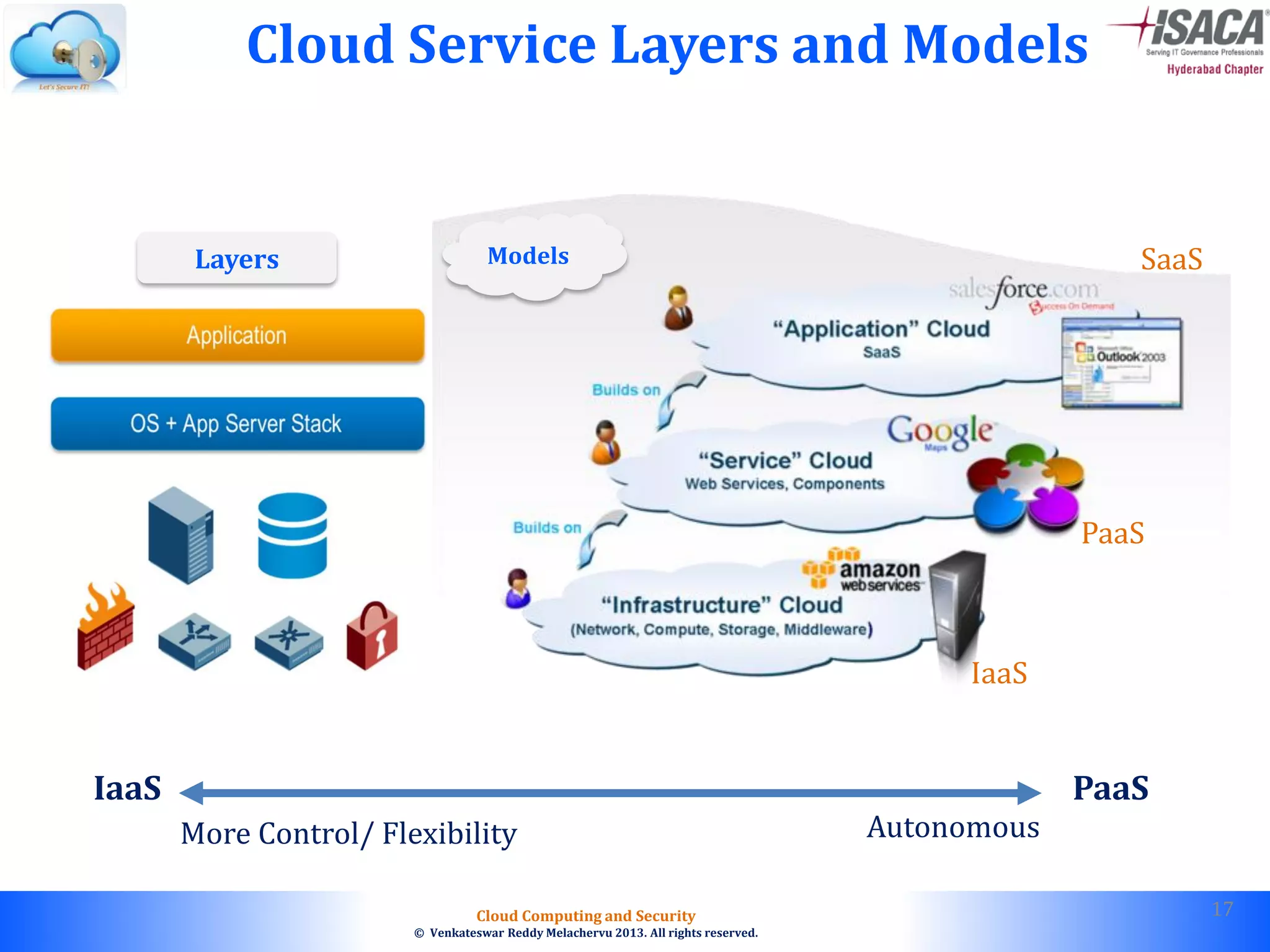
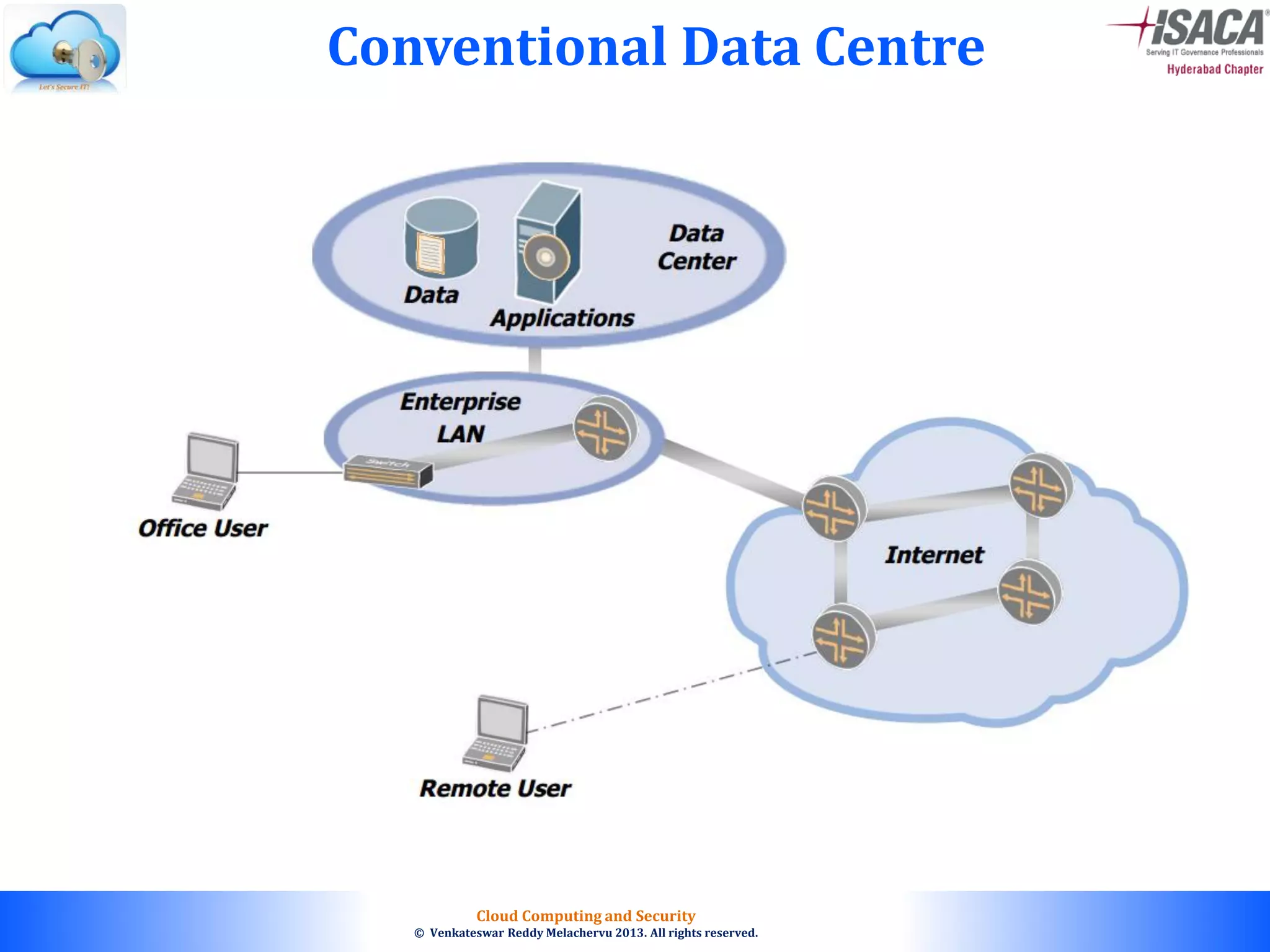
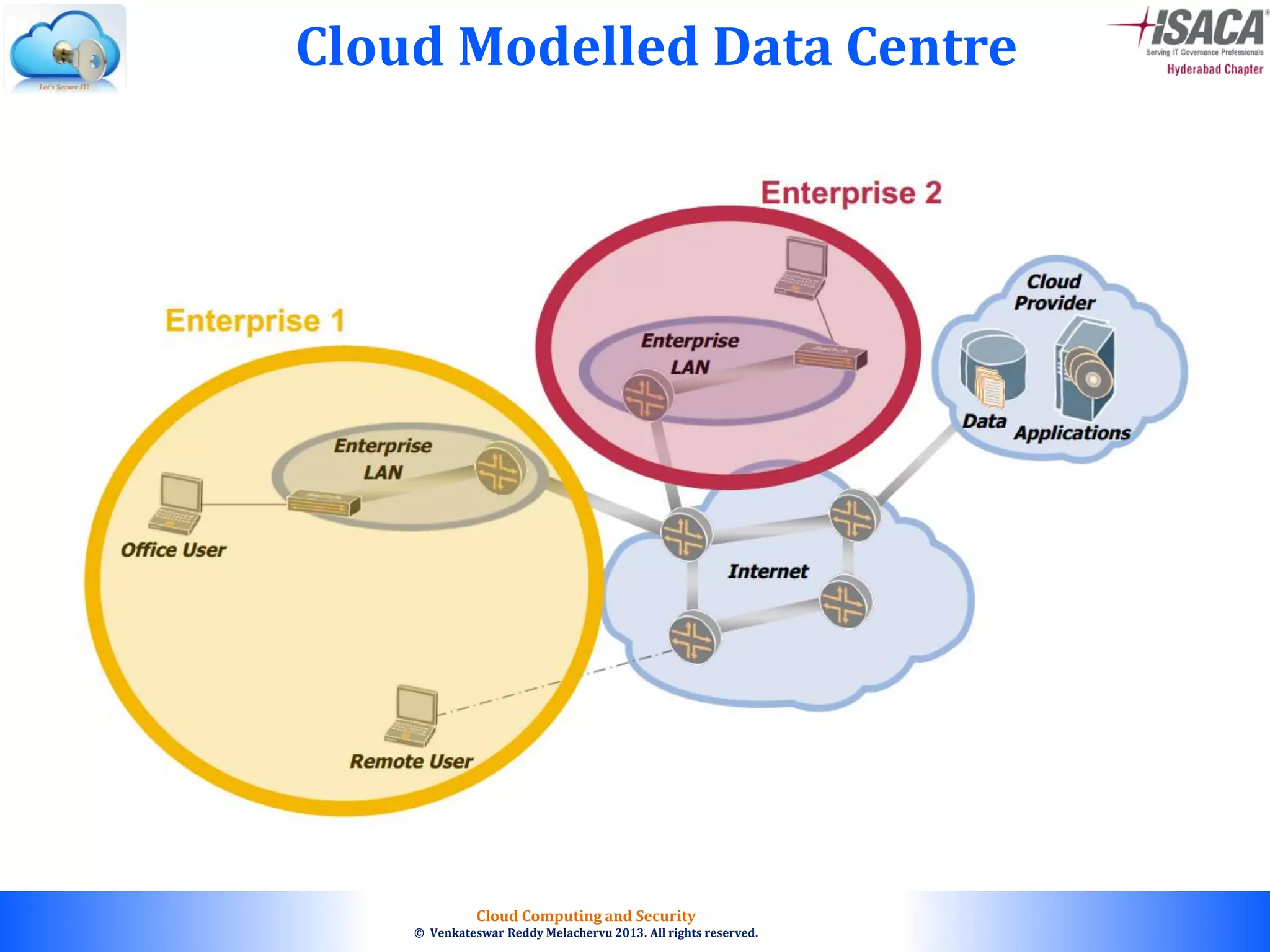
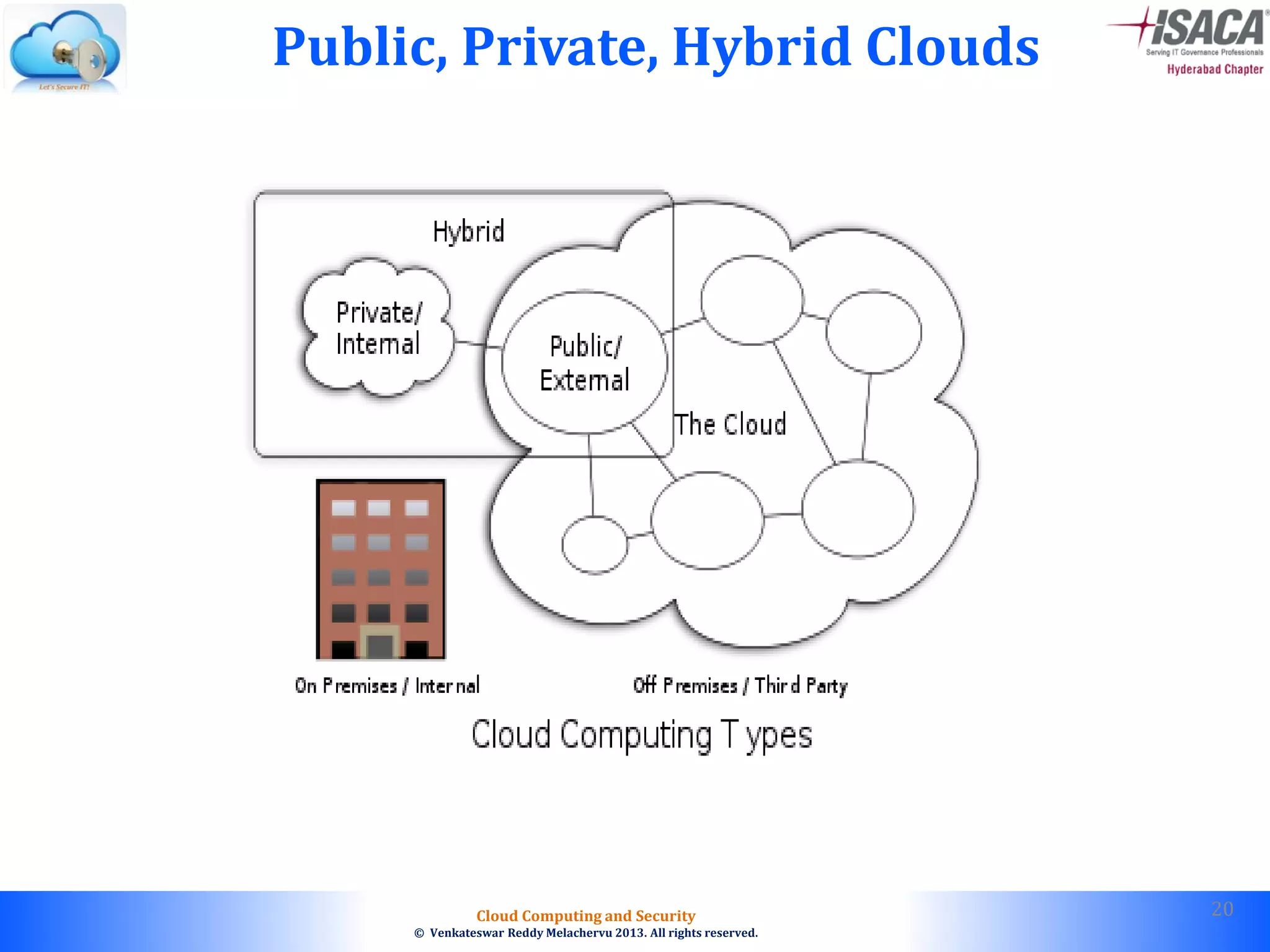
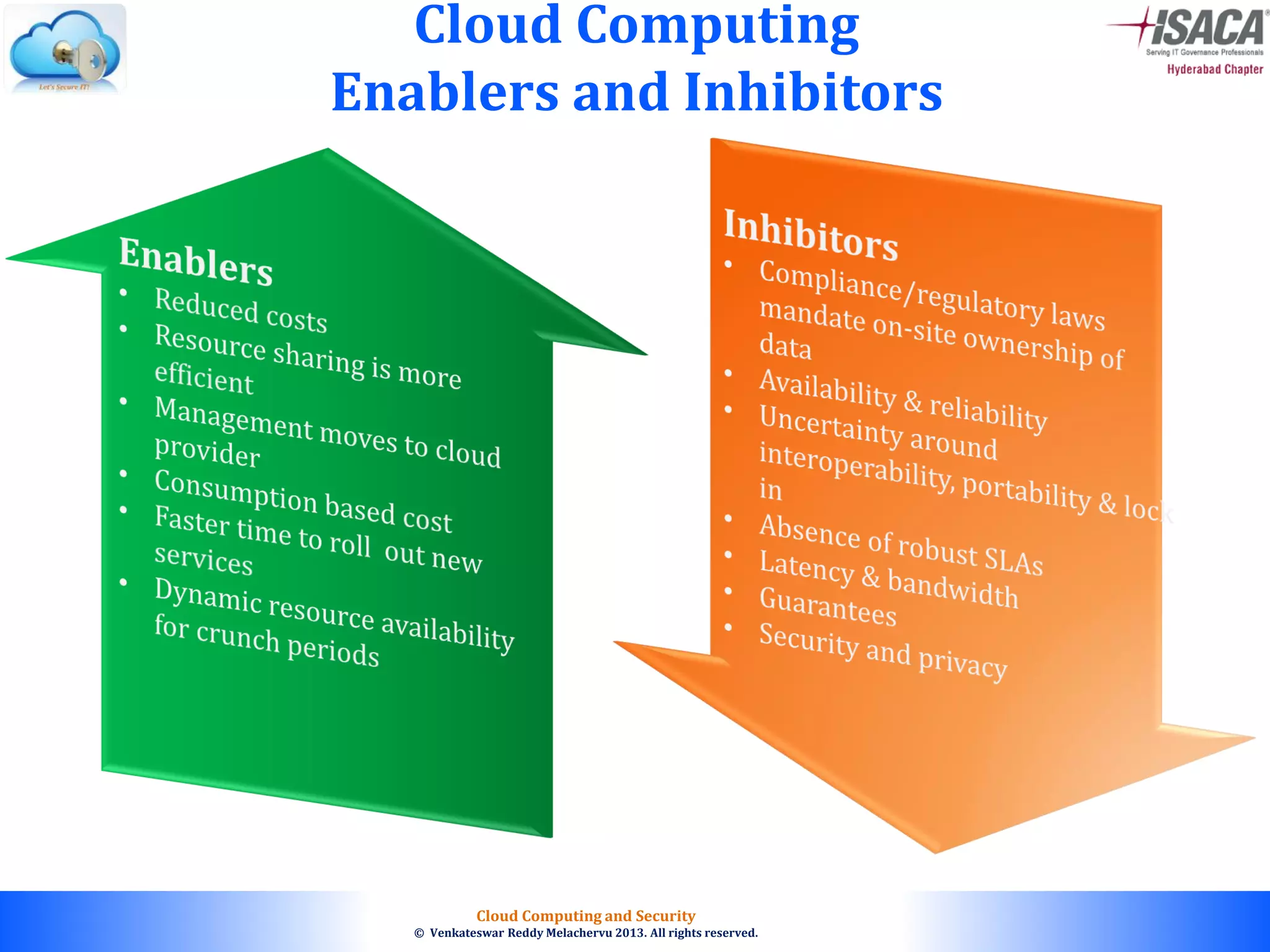
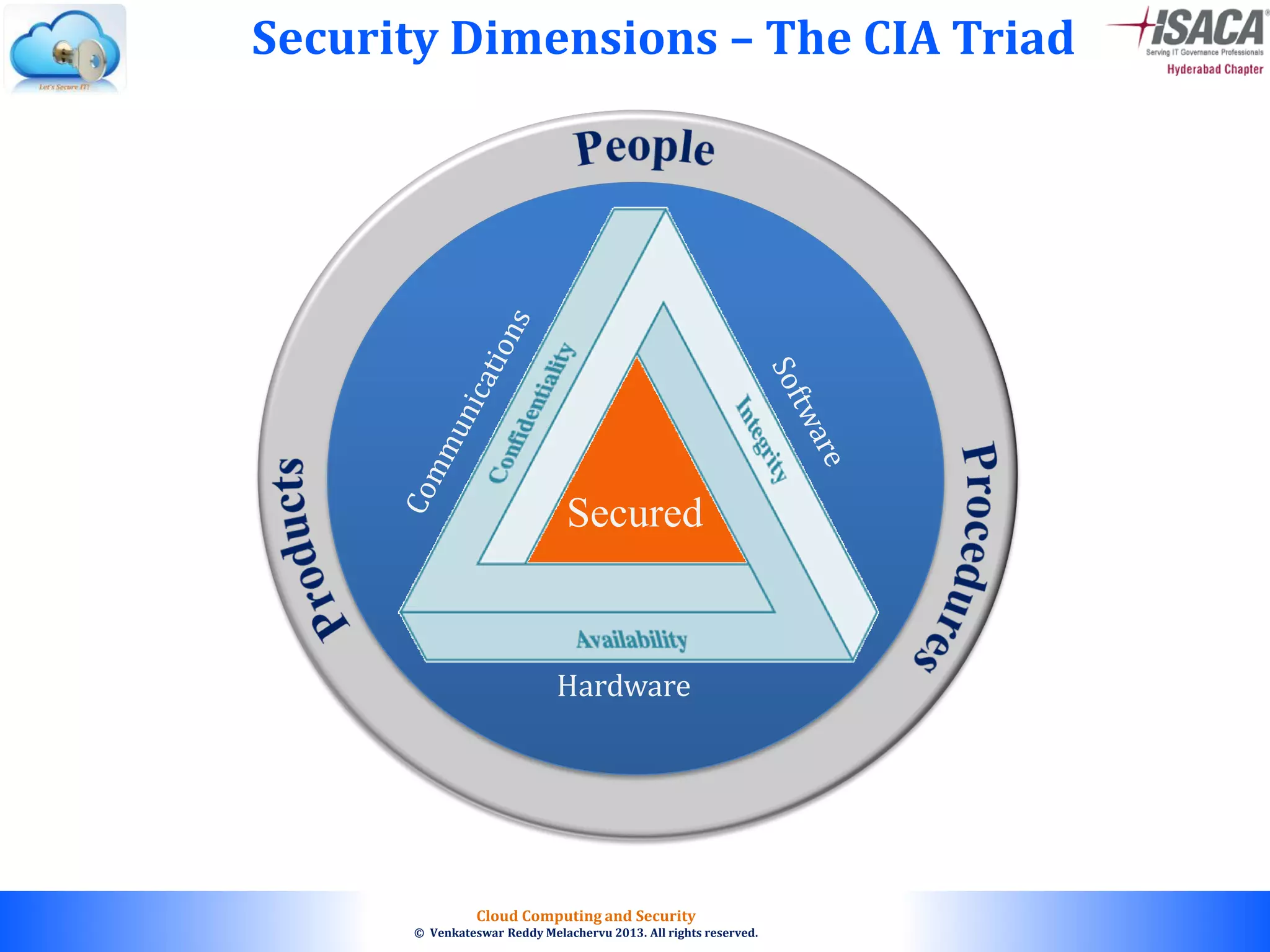
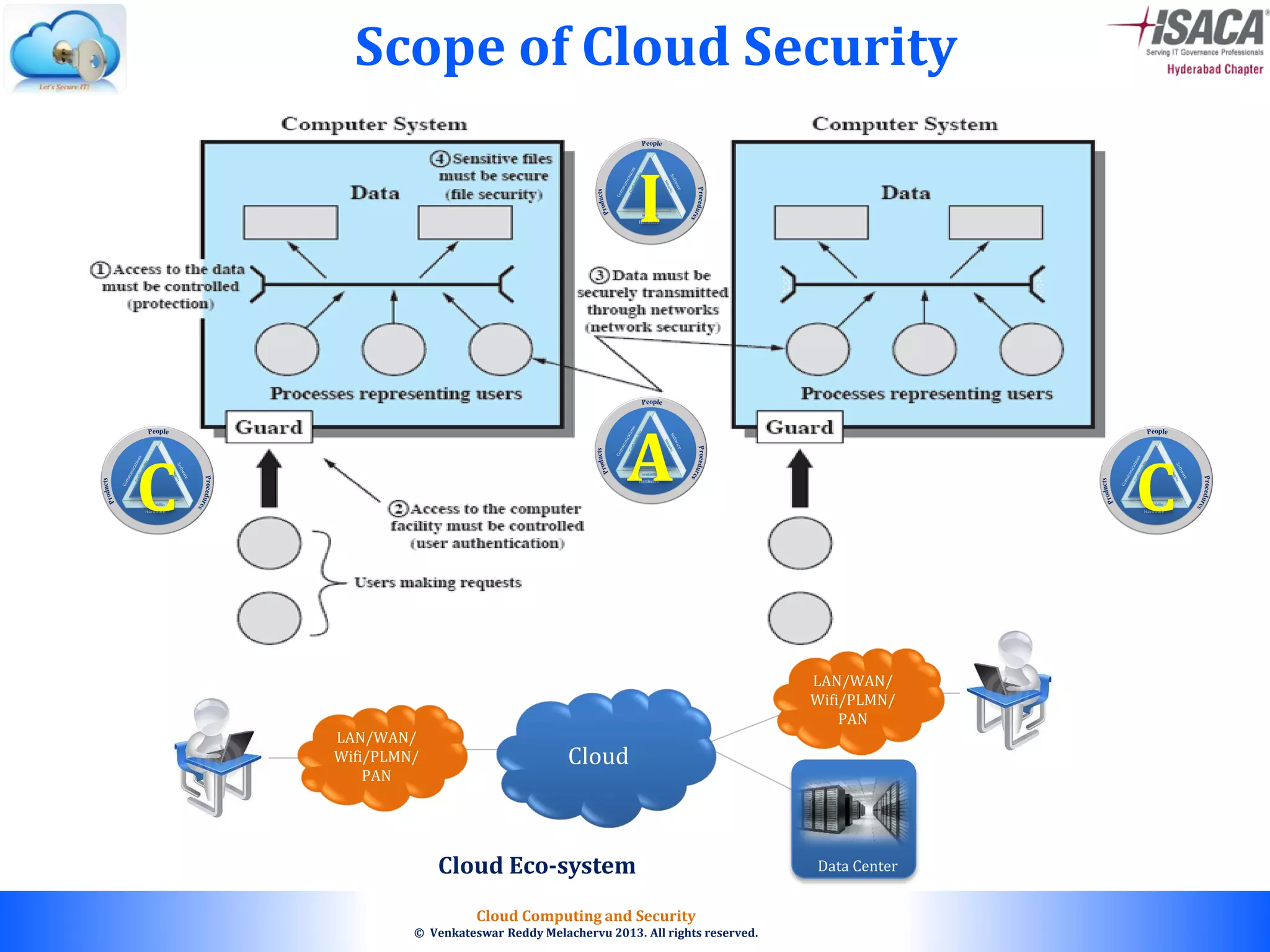
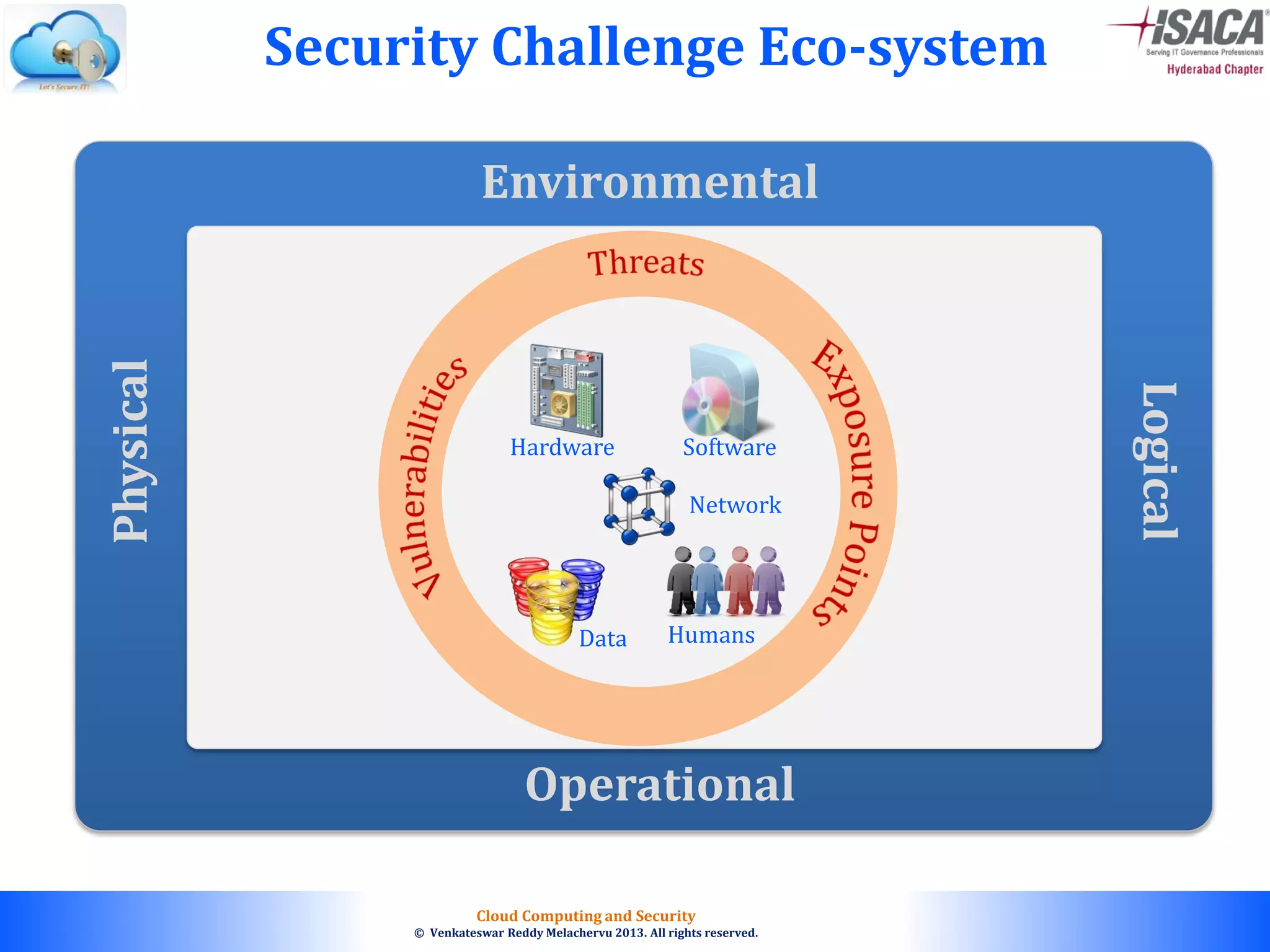
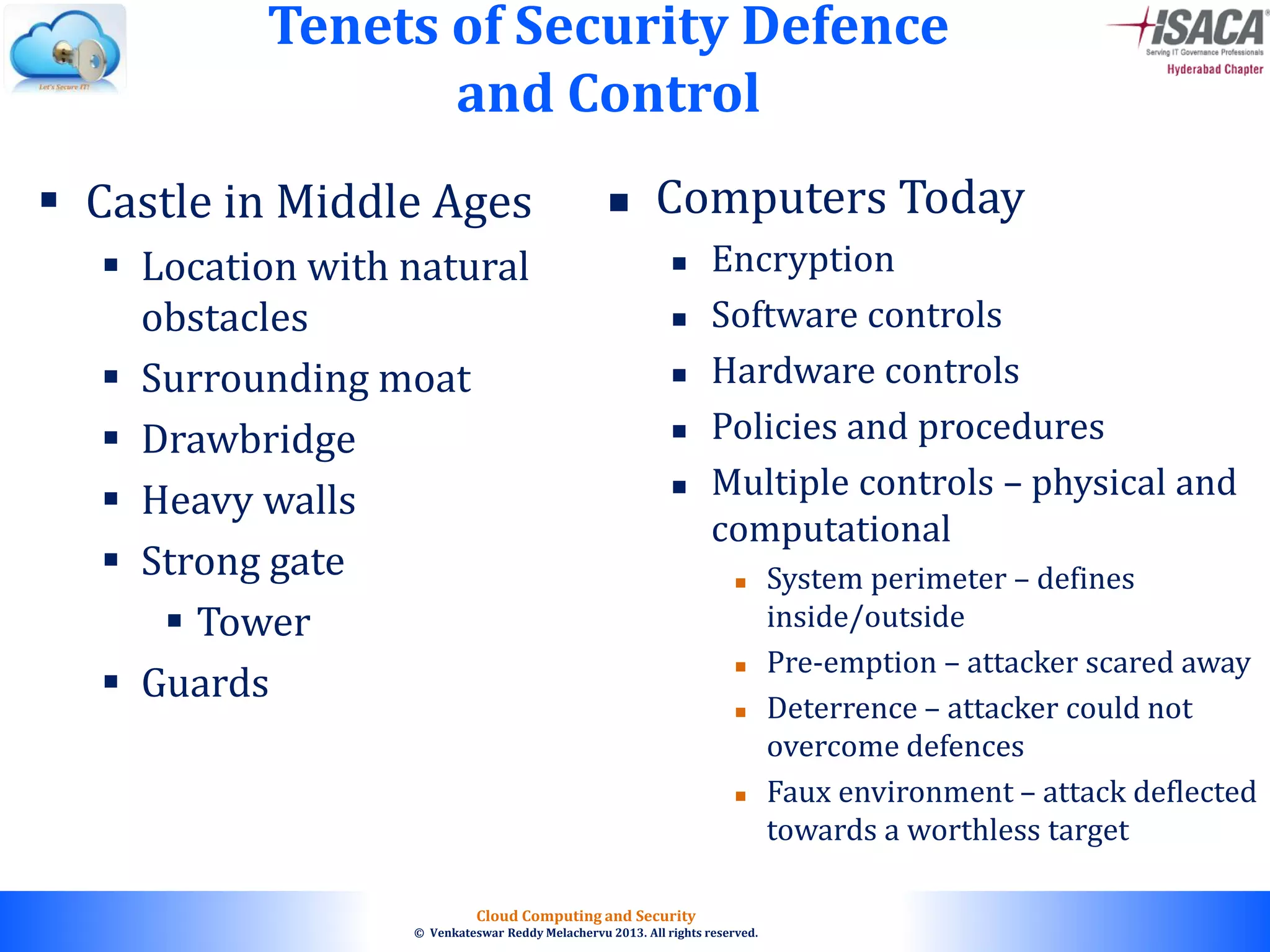
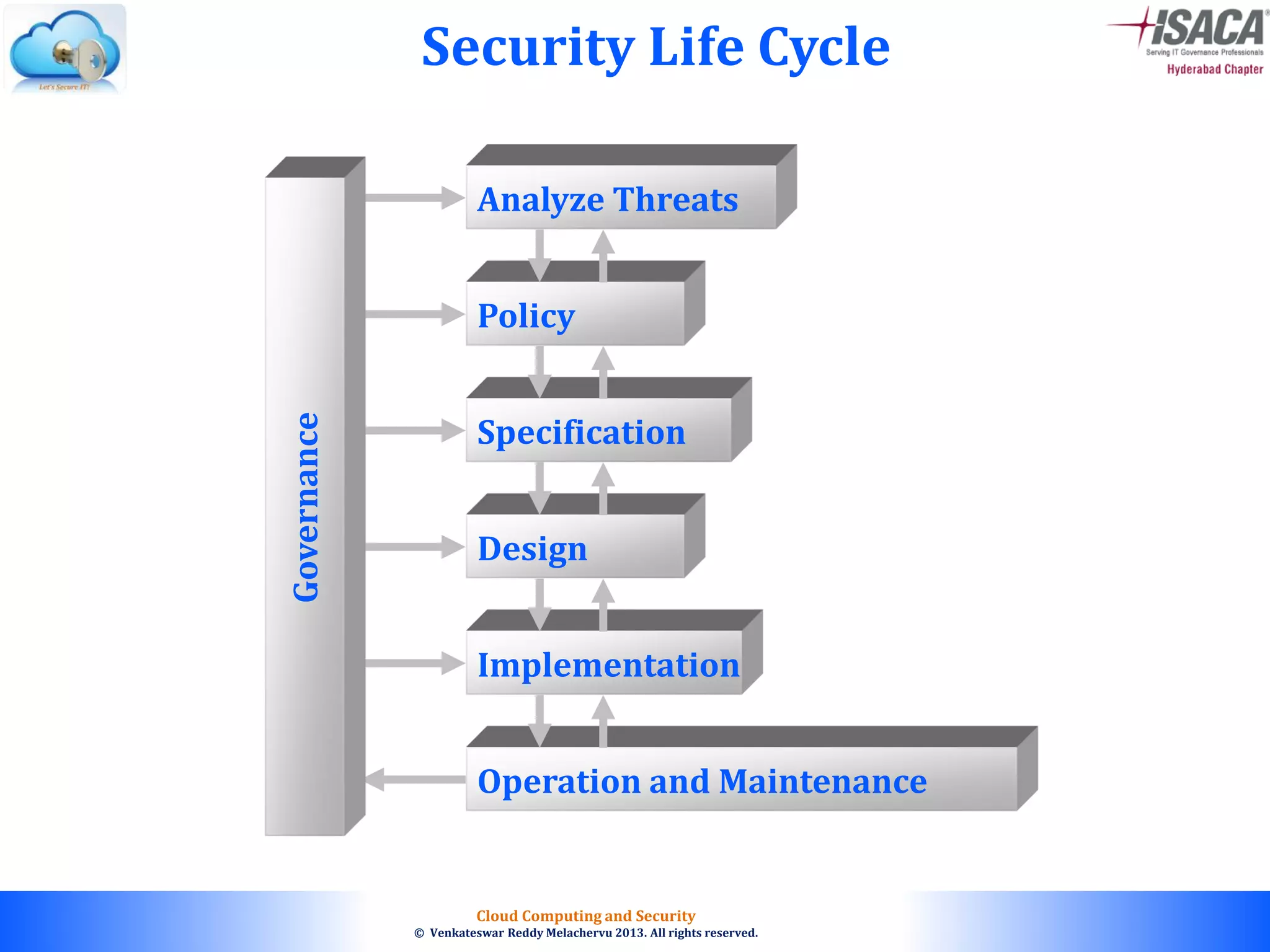
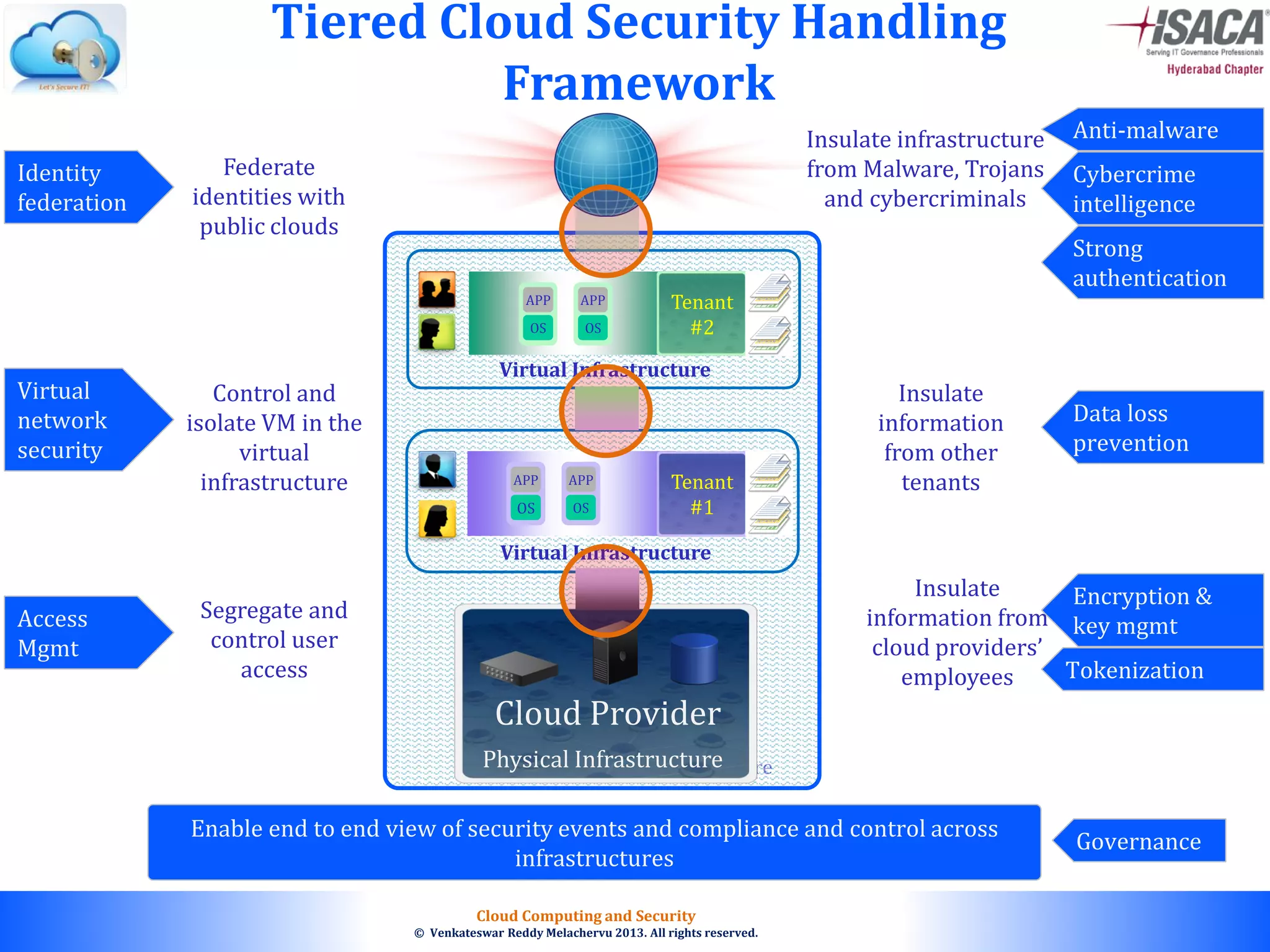
The document discusses cloud computing security, outlining the evolution of cyber attacks, various security challenges, and the importance of protecting computing systems and data. It highlights the CIA triad (confidentiality, integrity, availability), the notorious threats facing cloud services, and emphasizes the need for robust security measures and policies. Additionally, it provides insights into different types of attacks, vulnerabilities, and the necessity for constant vigilance in IT security.