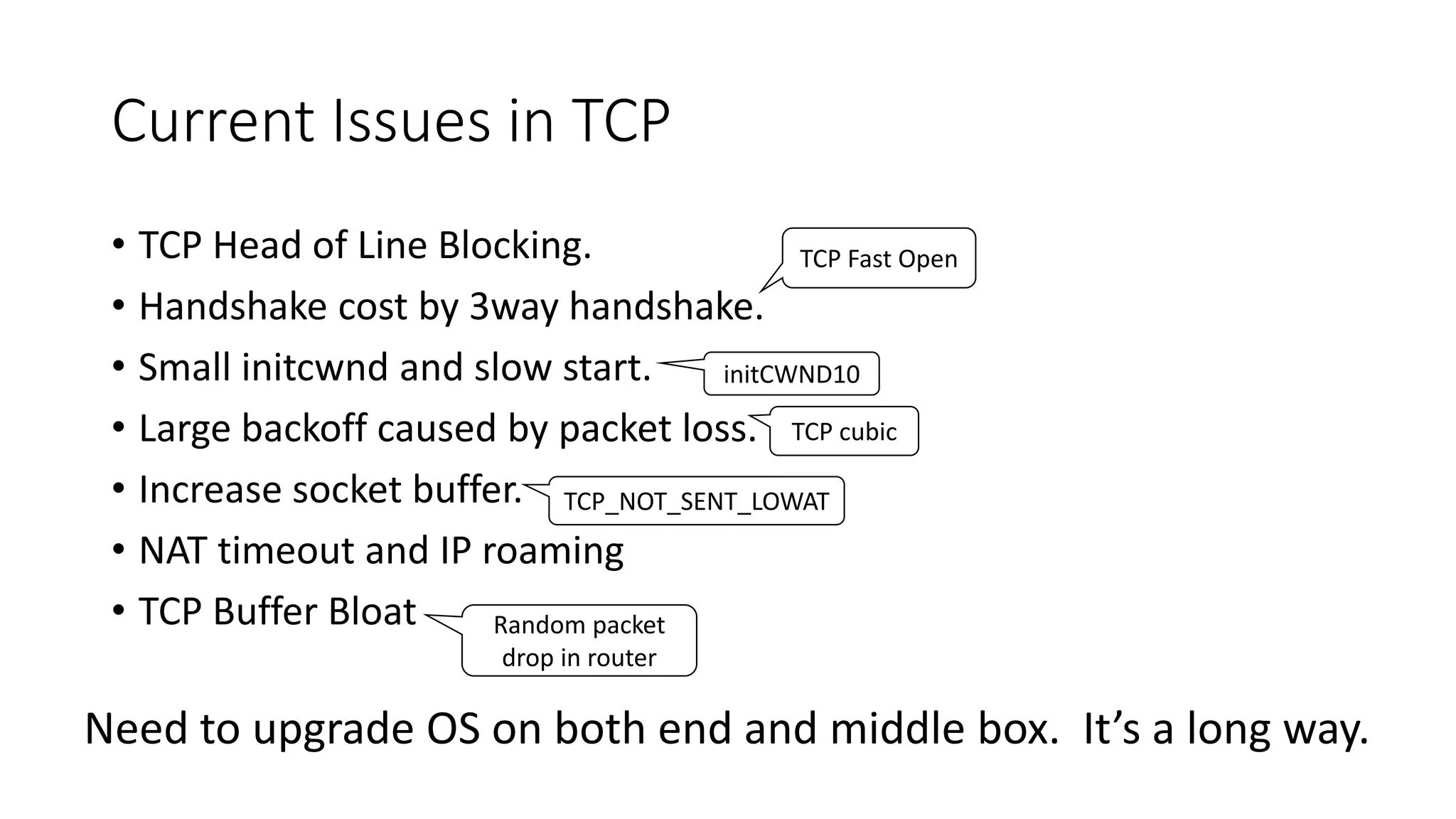
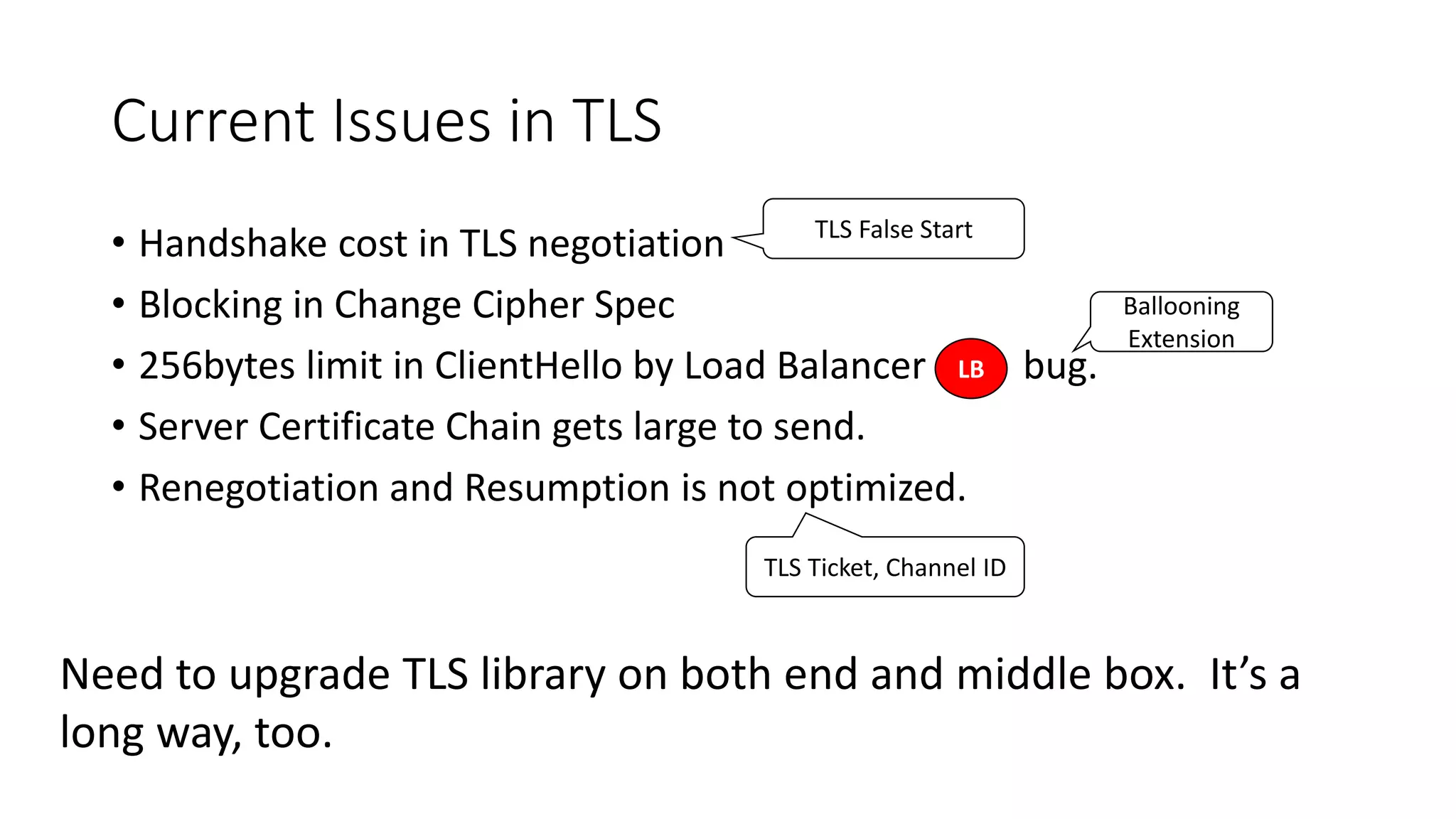
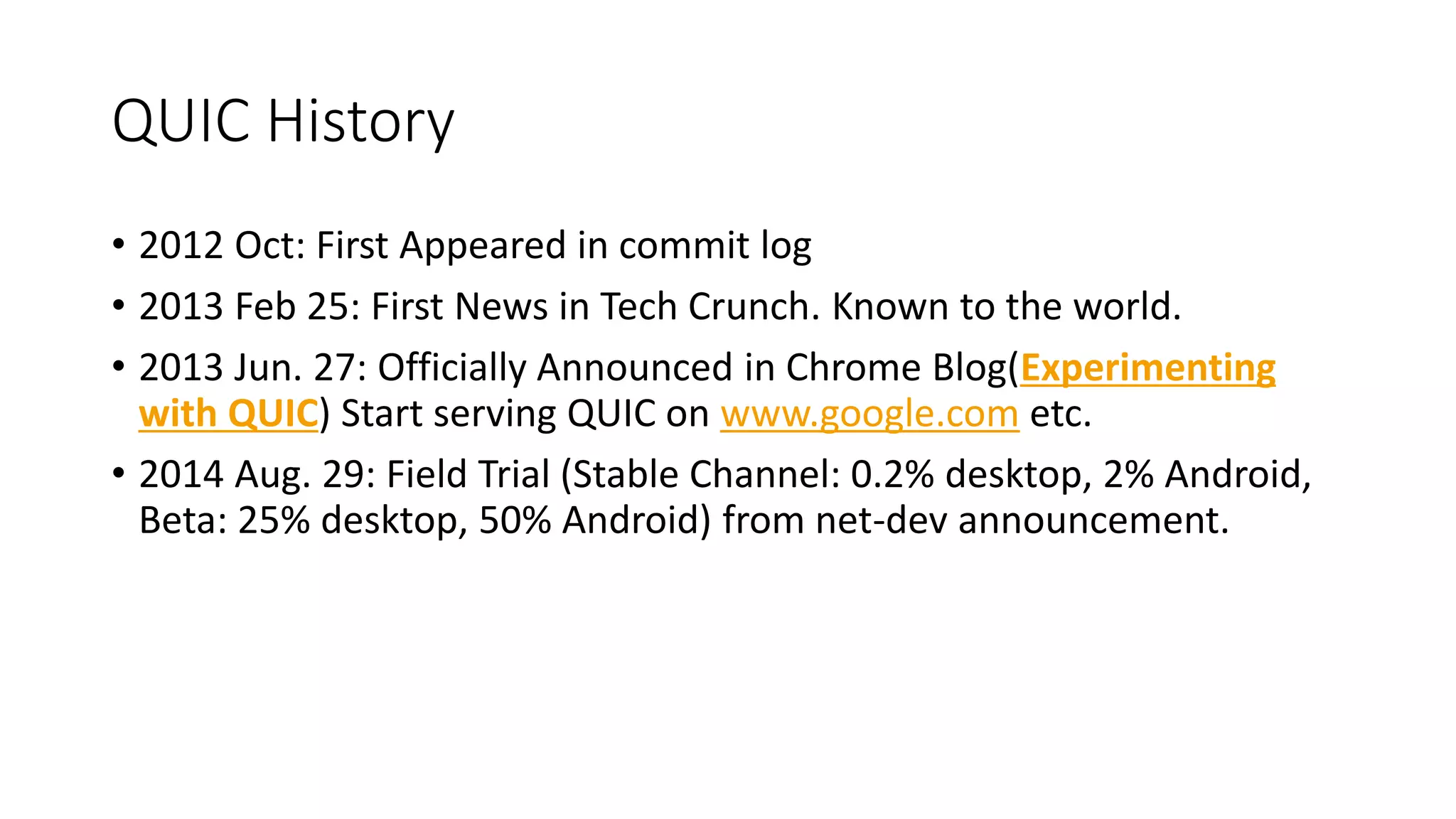
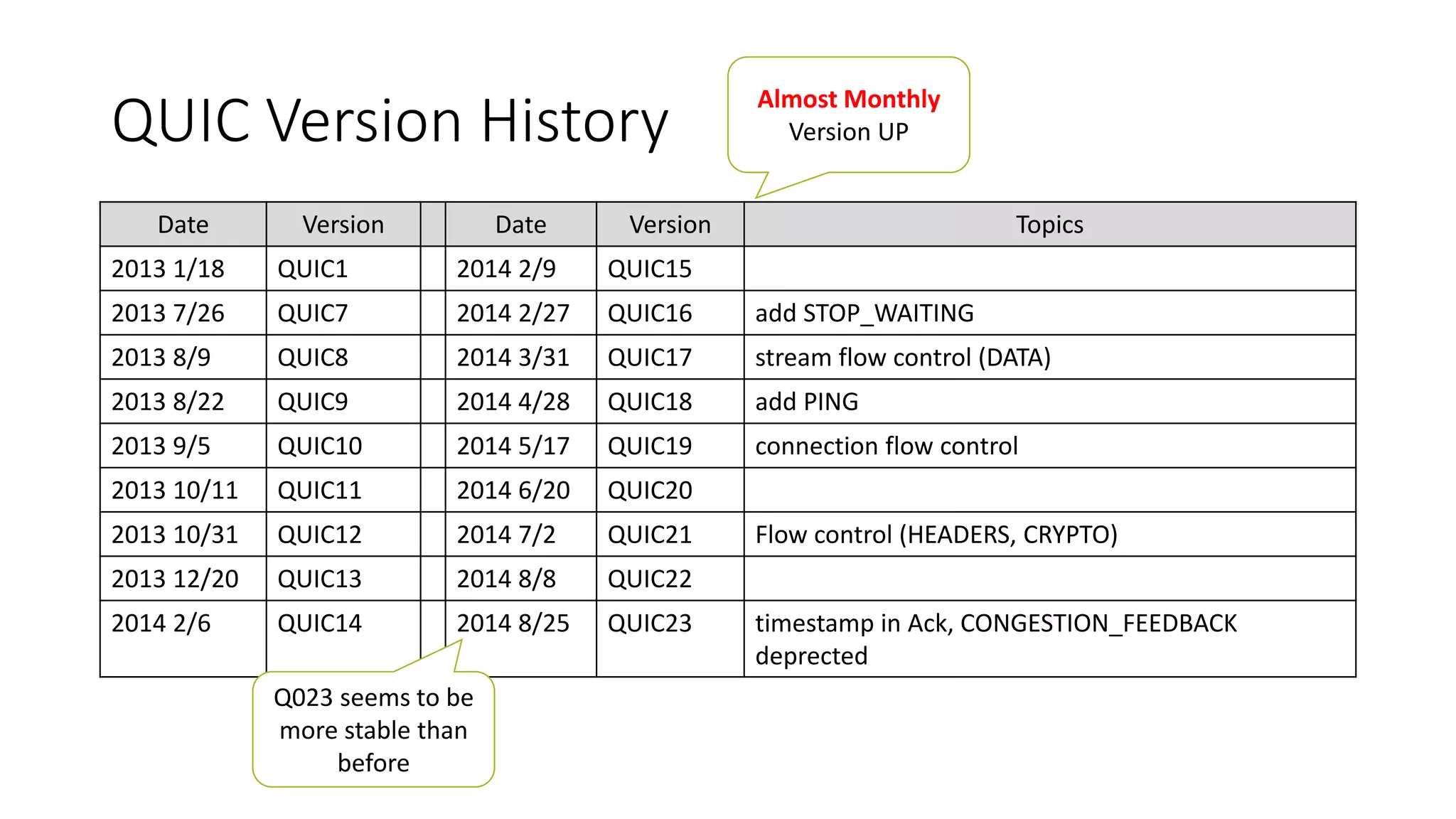
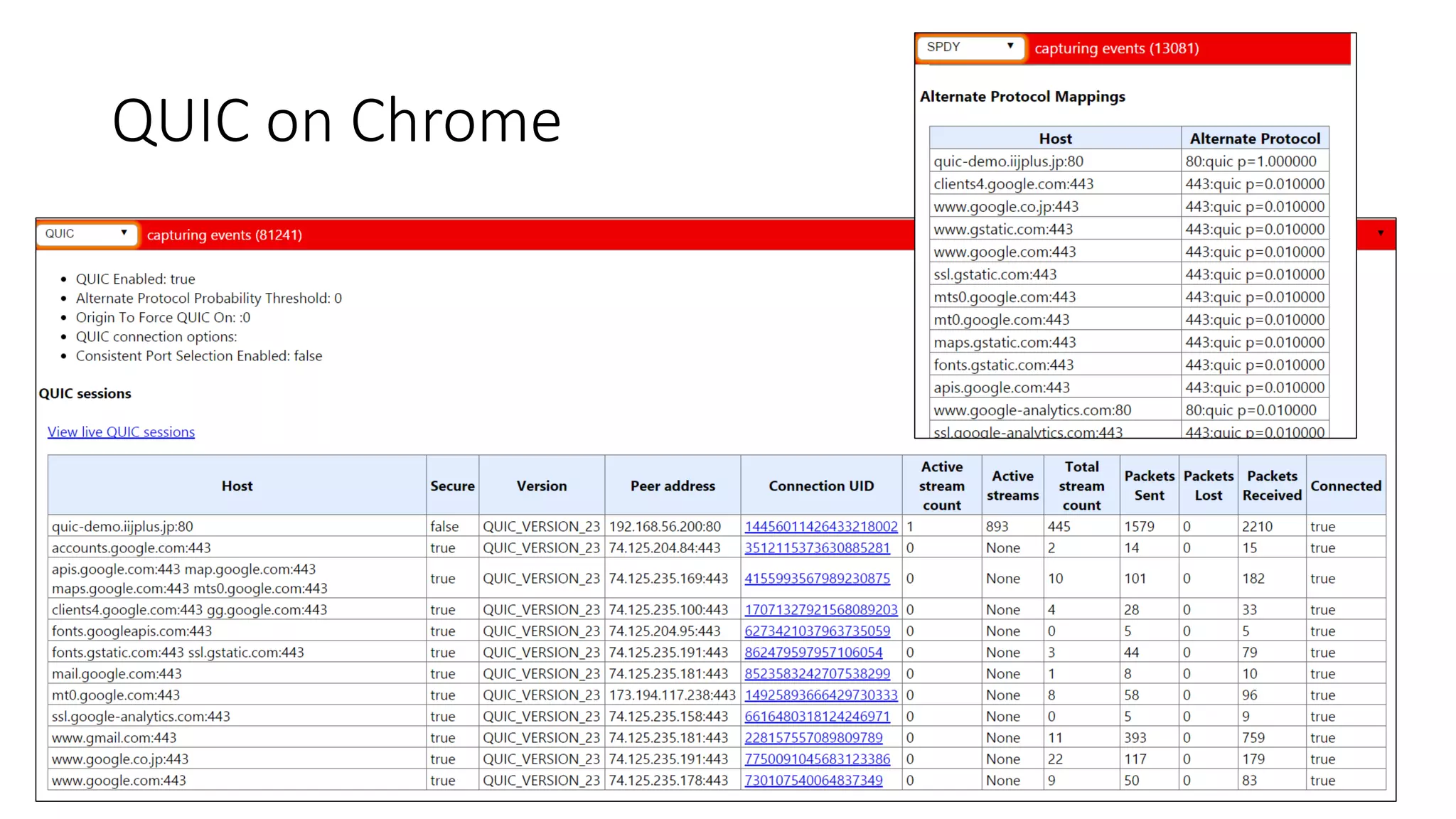
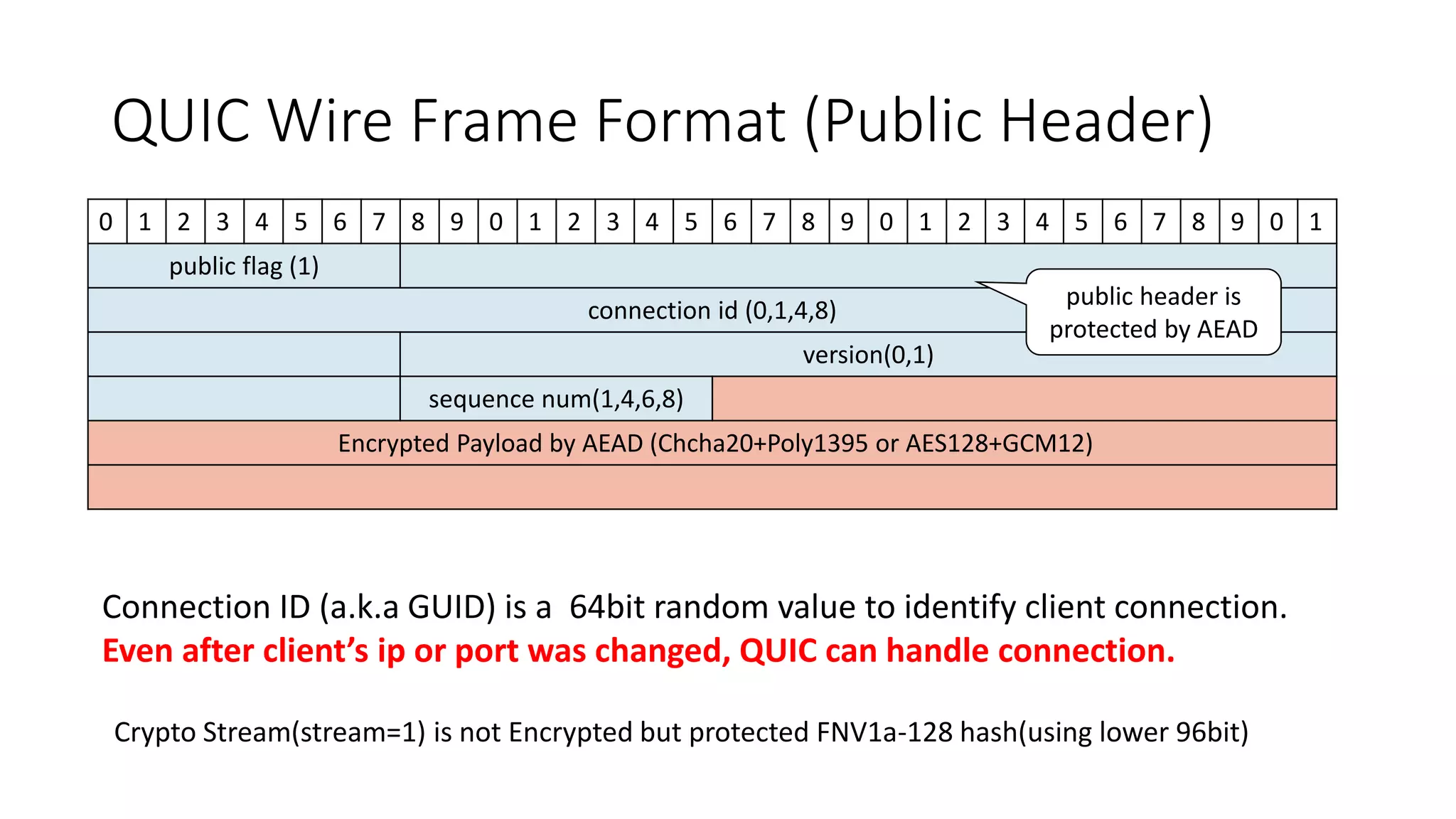
QUIC is a new transport protocol developed by Google that aims to solve issues with TCP and TLS by multiplexing streams over UDP. It includes features like stream multiplexing, connection migration, 0-RTT connection establishment, and forward error correction. The document provides technical details on QUIC including its version history, wire format specifications, frame types, cryptographic handshake process, and examples of 0-RTT, 1-RTT, and 2-RTT connection establishment.

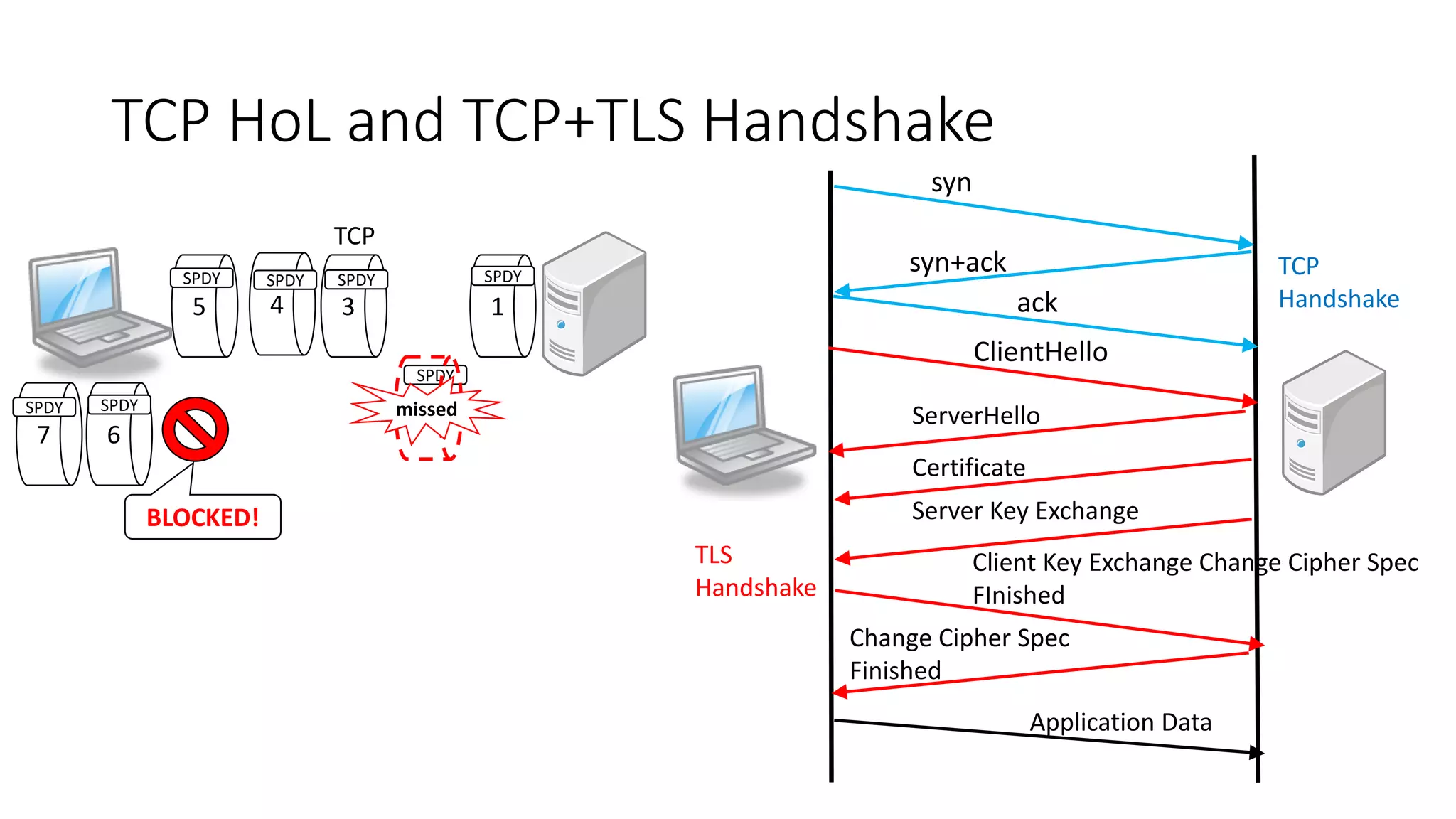
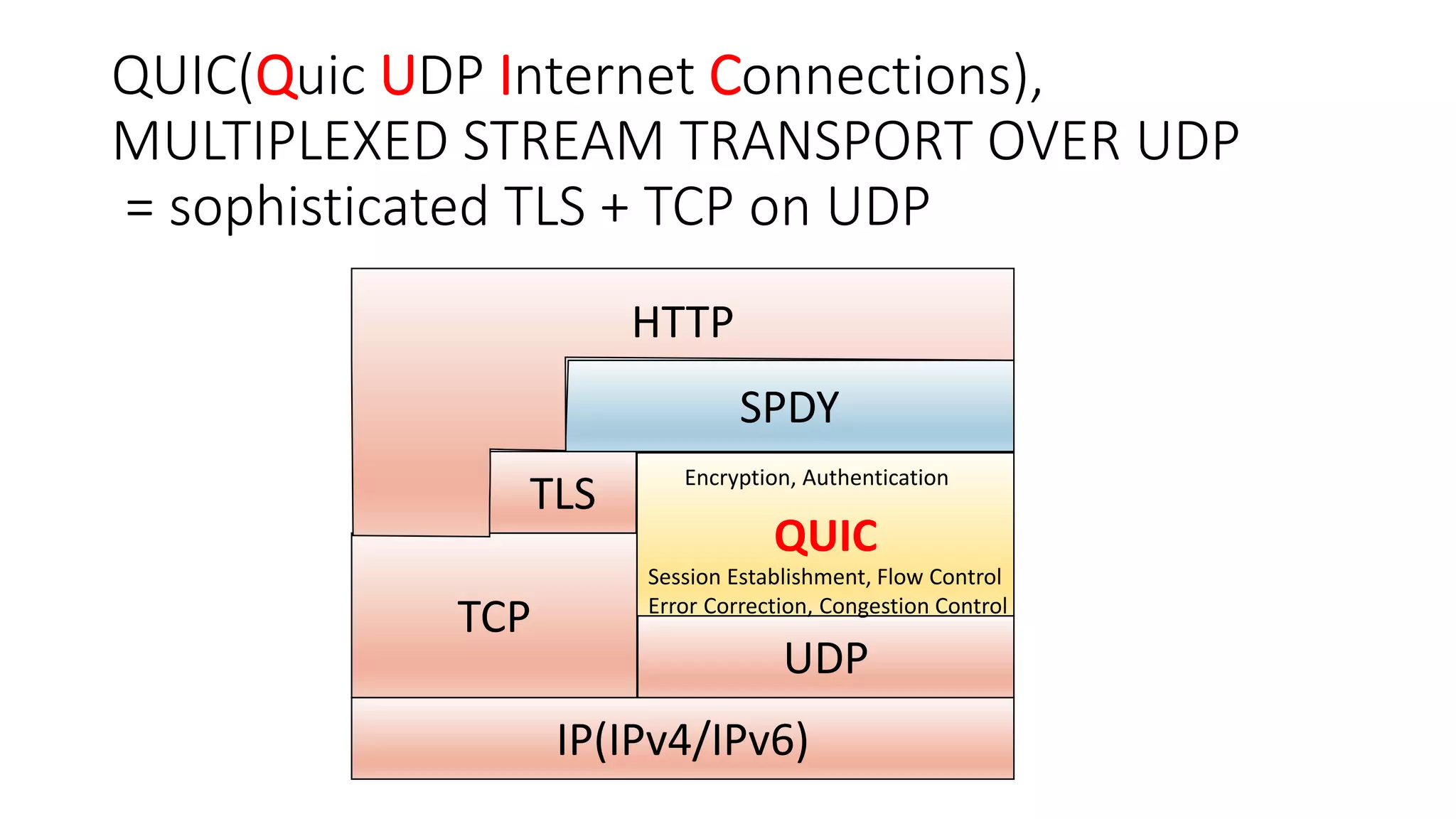
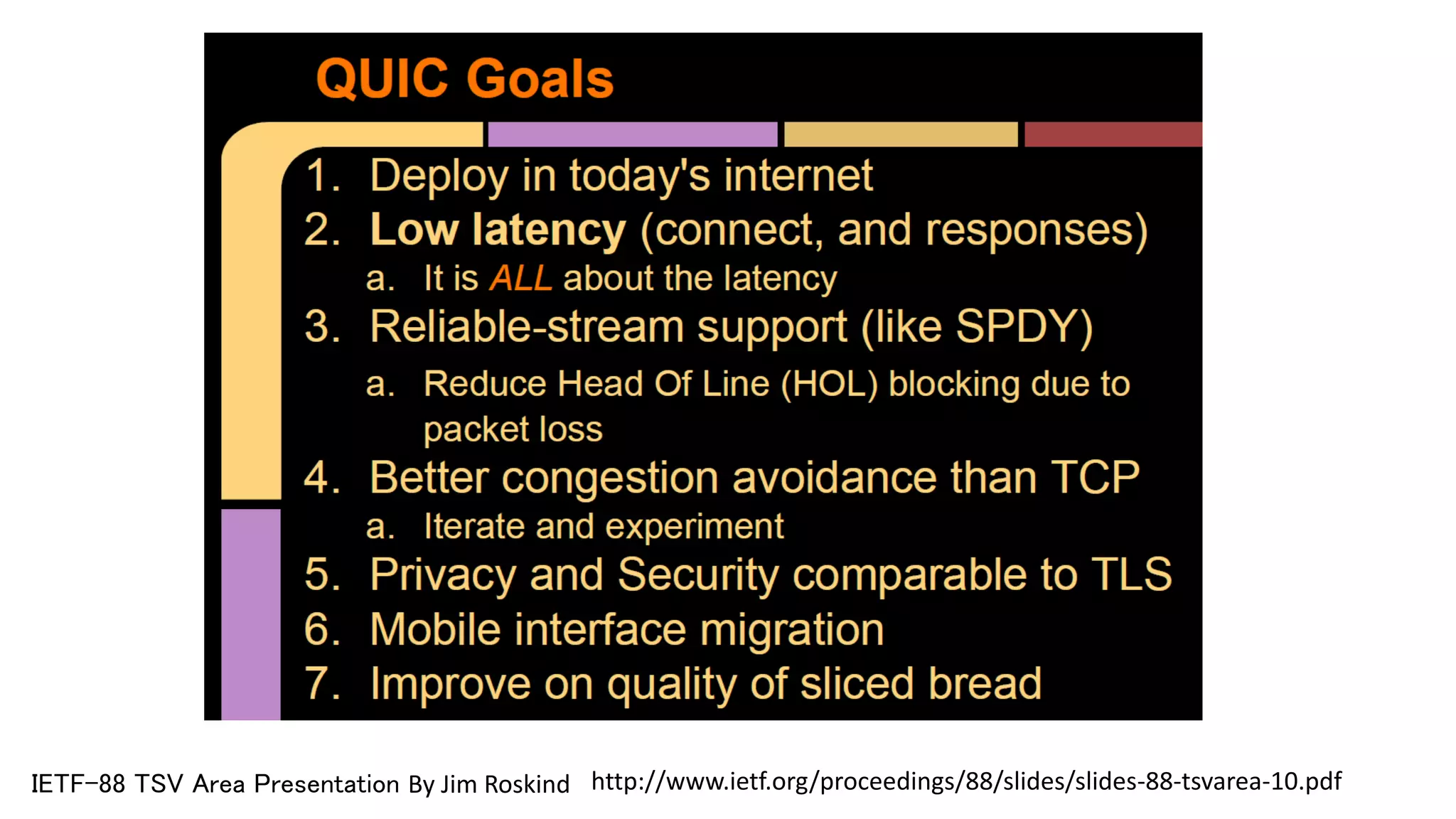
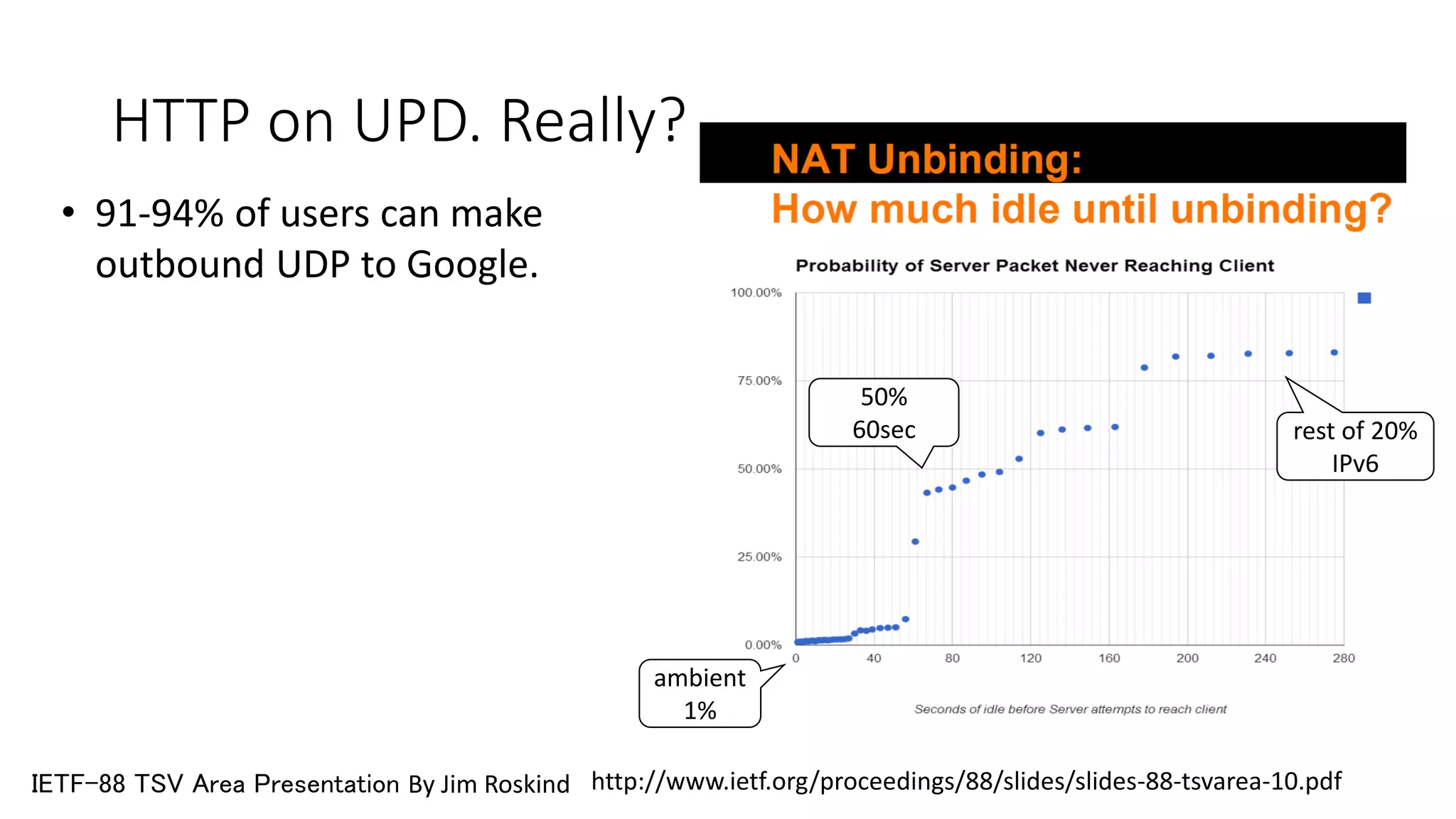


![Retransmit a lost frame as a new stream
STREAM_FRAME
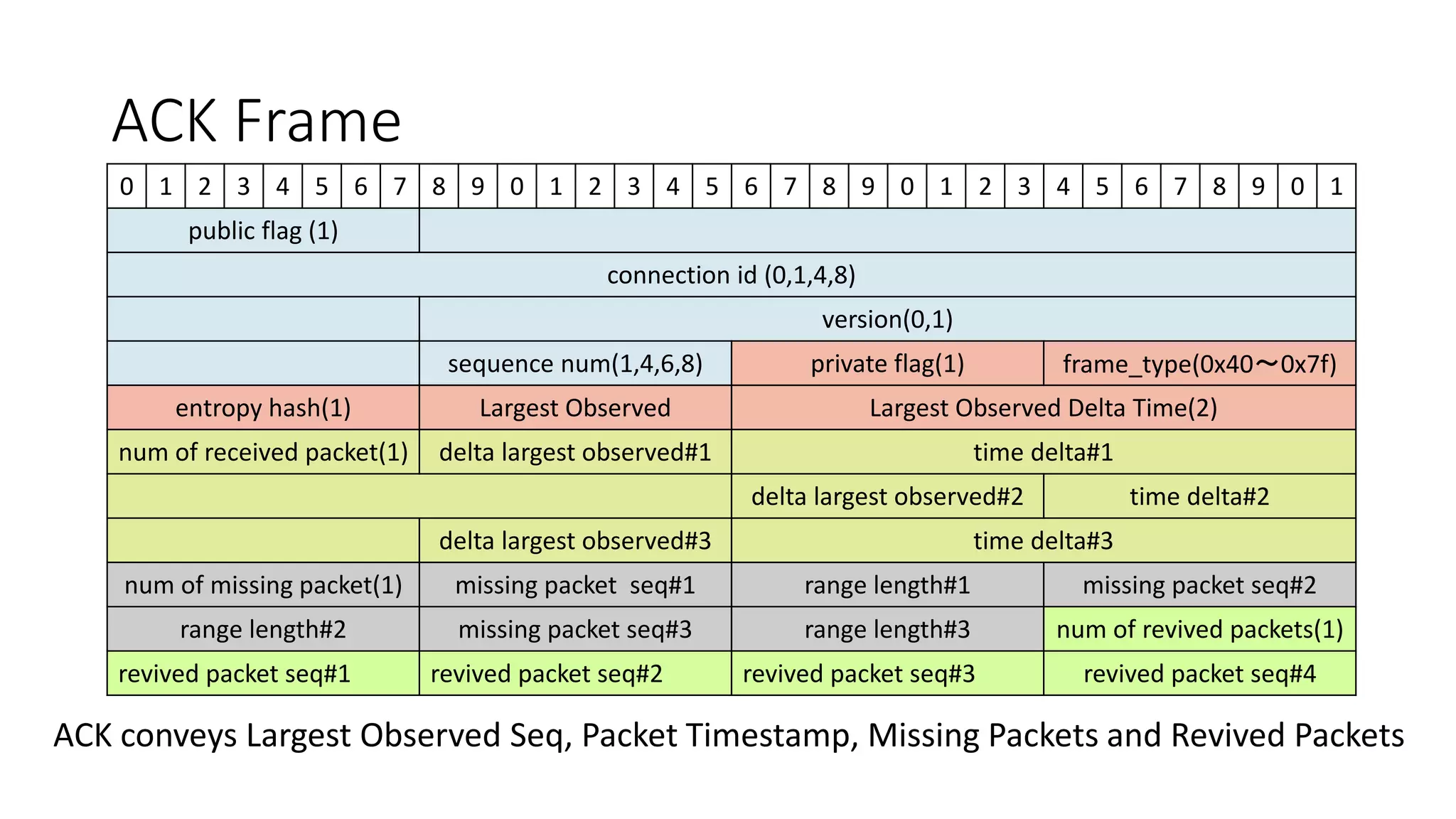
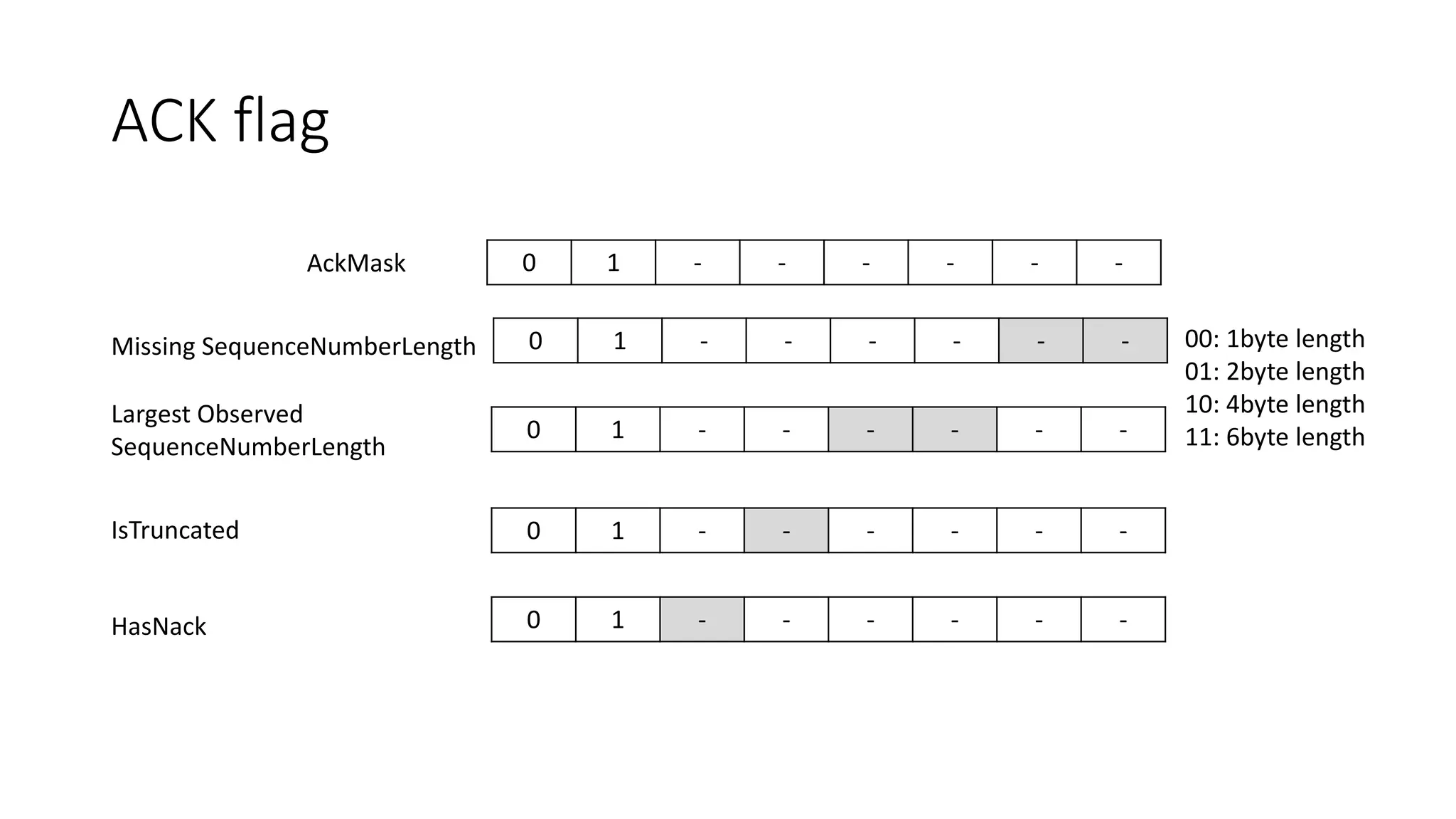
ACK(largest_observed: 11, missing: [10])
Lost
id=9
id=10
id=11
id=13 retransmit as id=10
id=12
id=10 was lost.
retransmit it as a new
stream(id=13)
Non-Blocked!
Retransmitted as a
new stream](https://image.slidesharecdn.com/quicoverview-141102192659-conversion-gate02/75/Technical-Overview-of-QUIC-32-2048.jpg)