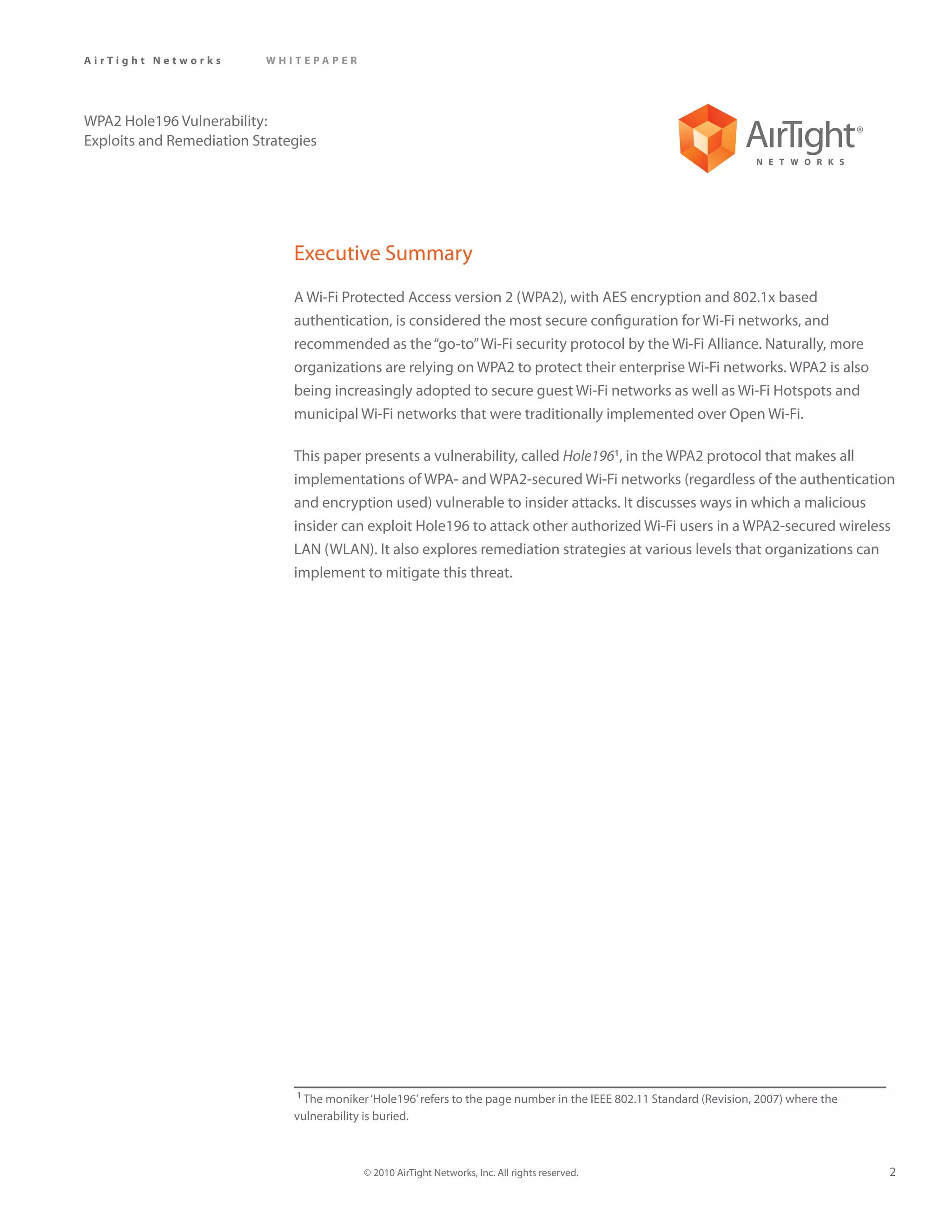
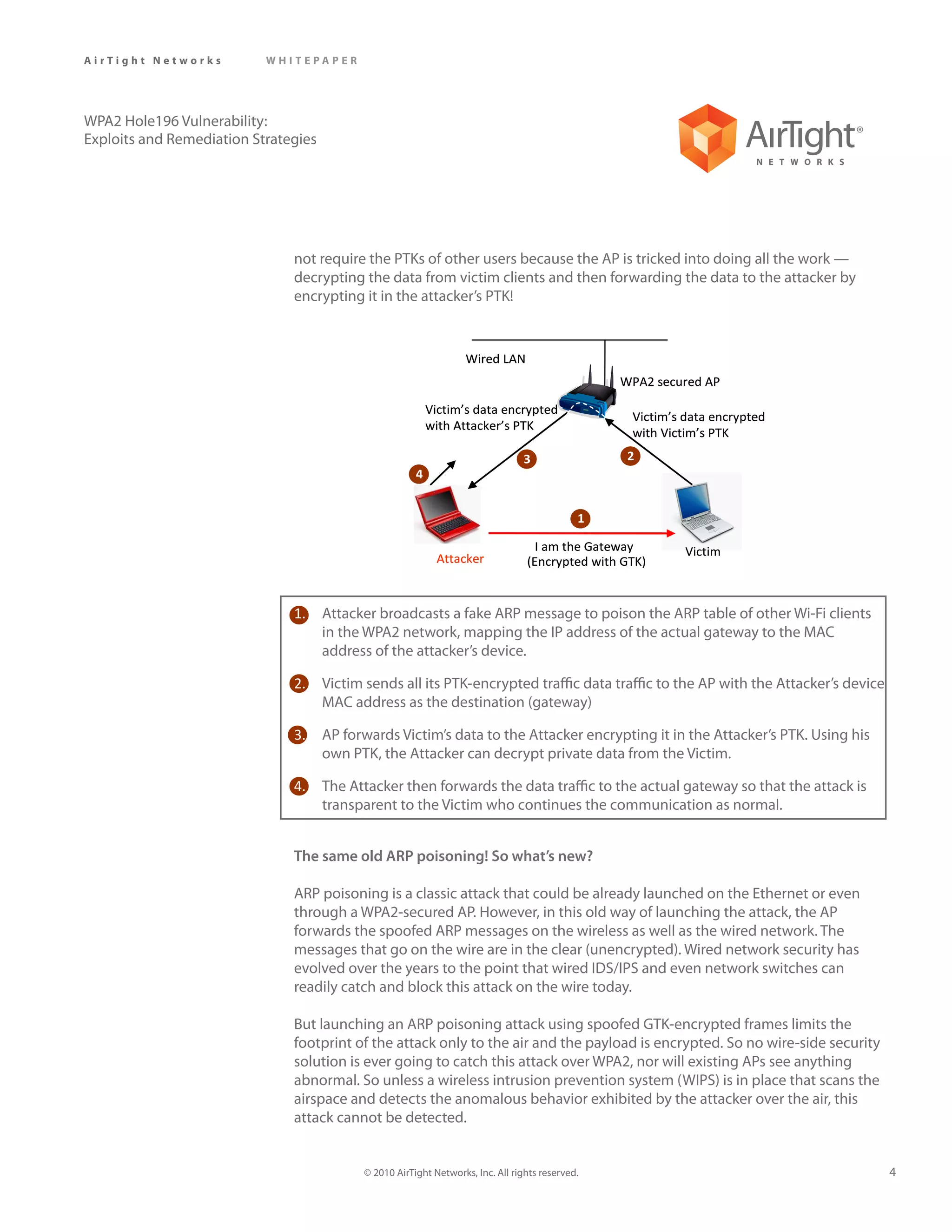
The document discusses the WPA2 Hole196 vulnerability that allows a malicious insider on a WPA2 secured wireless network to decrypt and read private data from other authorized users on the network. It describes how the vulnerability works and exploits such as ARP poisoning that can be used. It then discusses potential mitigation strategies including client isolation, fixing the vulnerability in wireless infrastructure, and using a wireless intrusion prevention system.