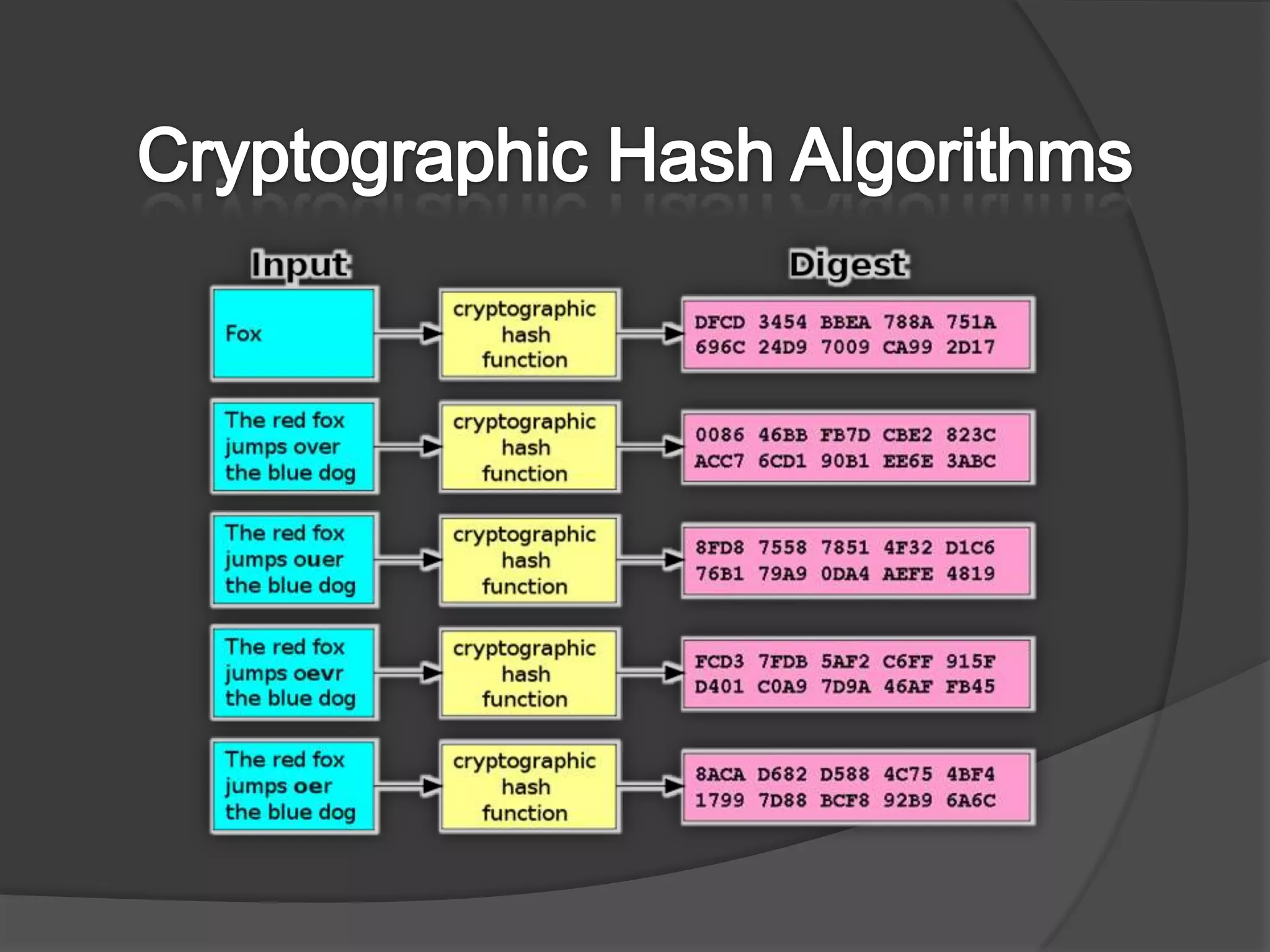
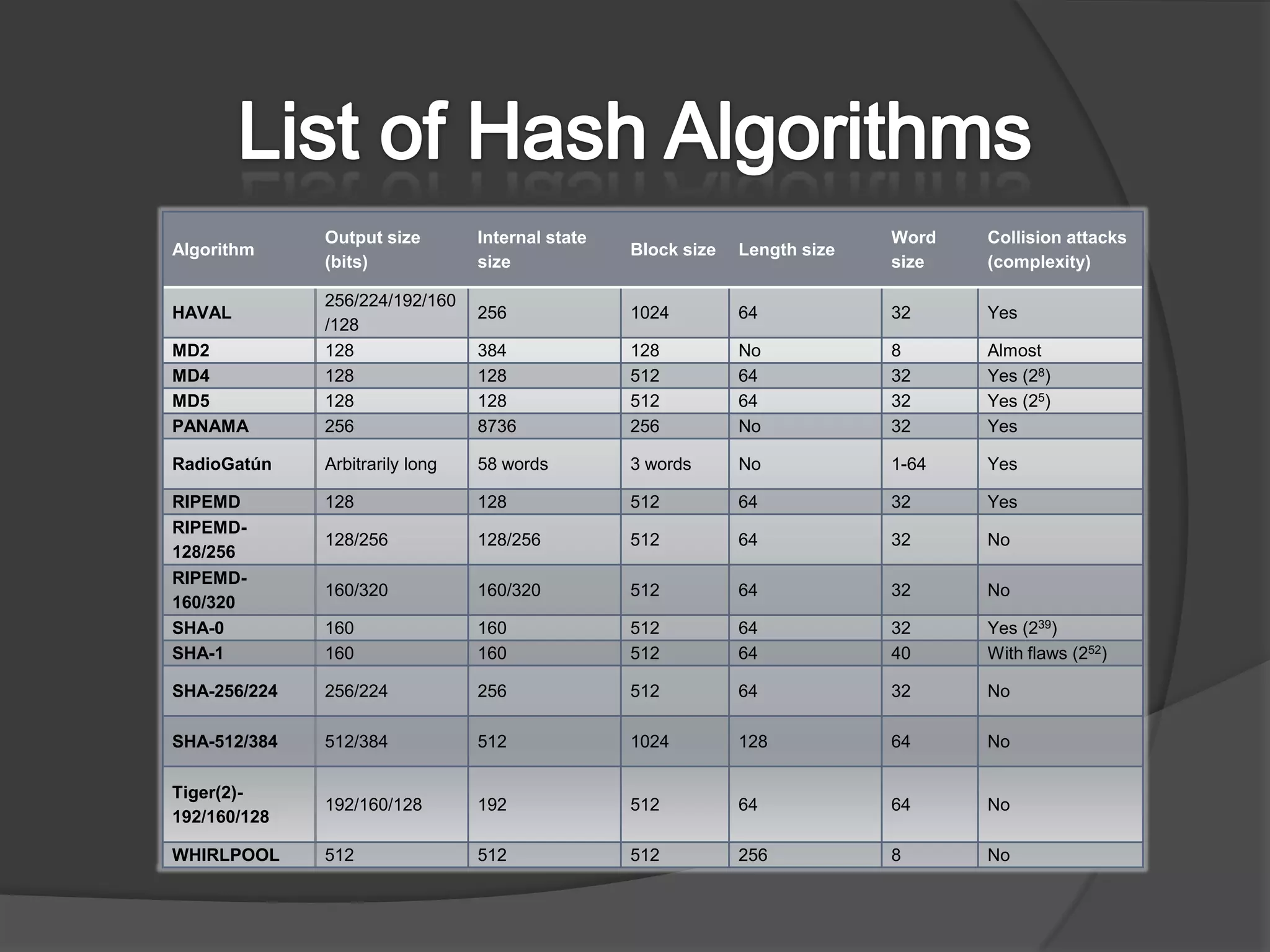
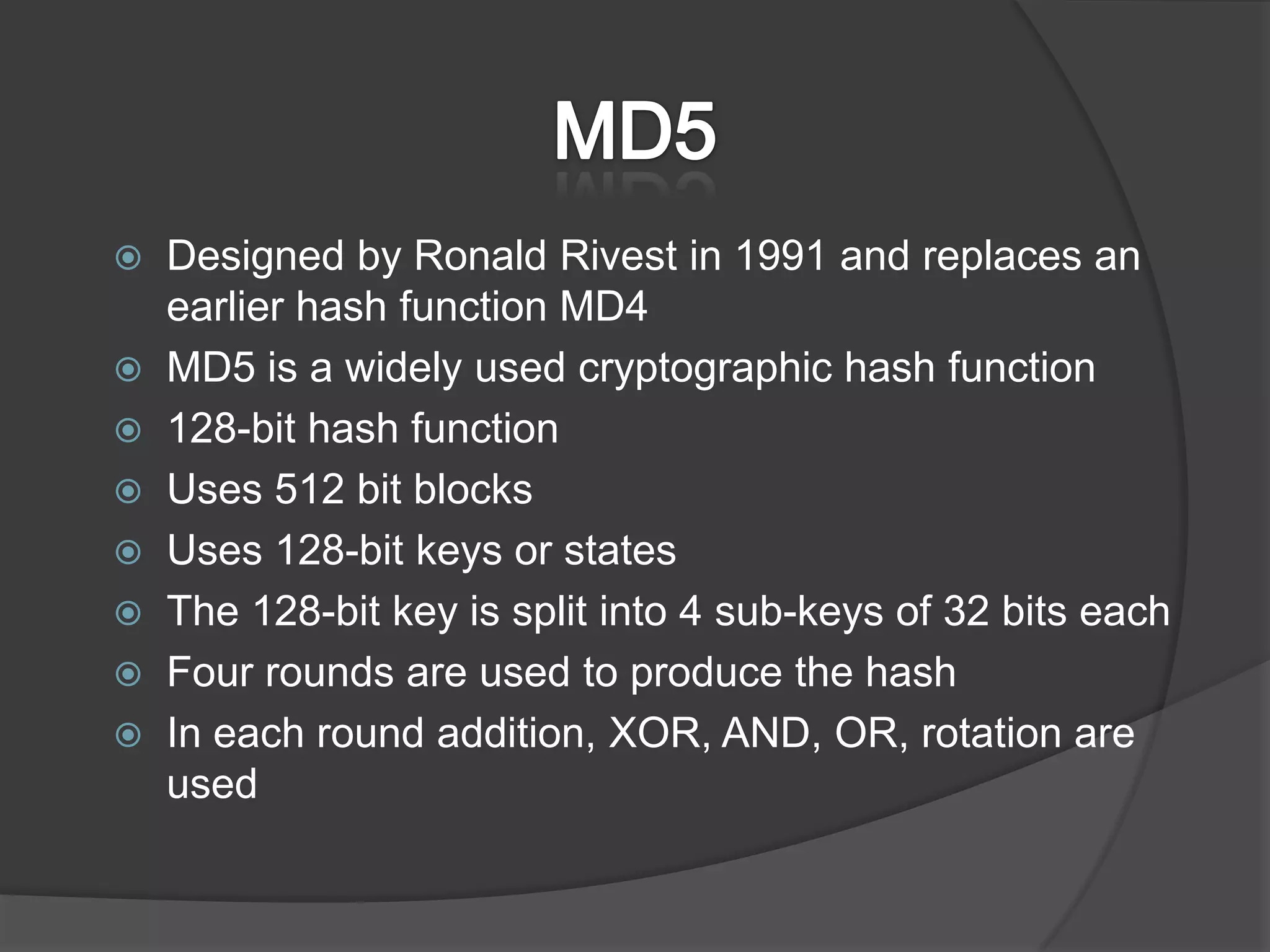
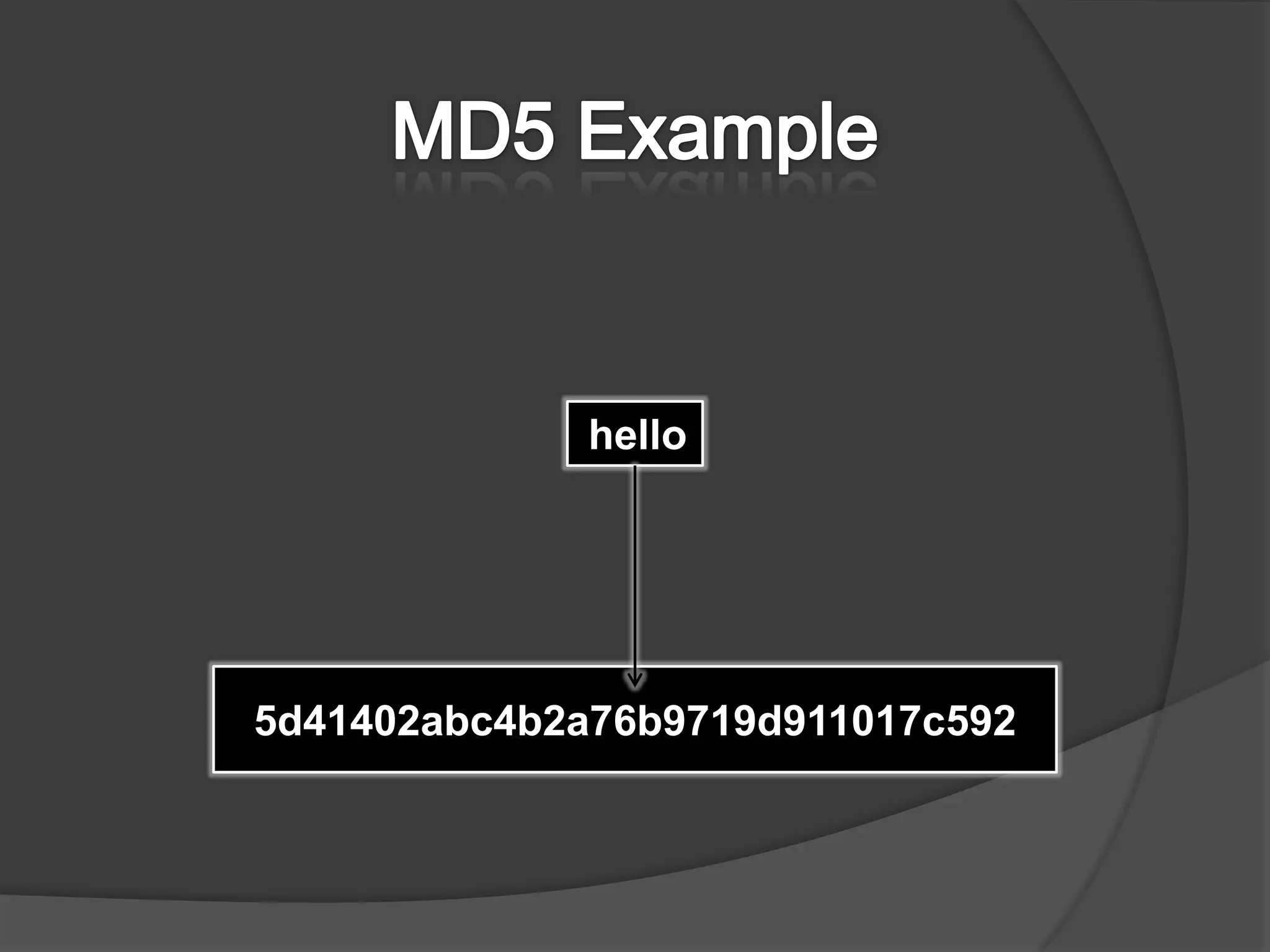
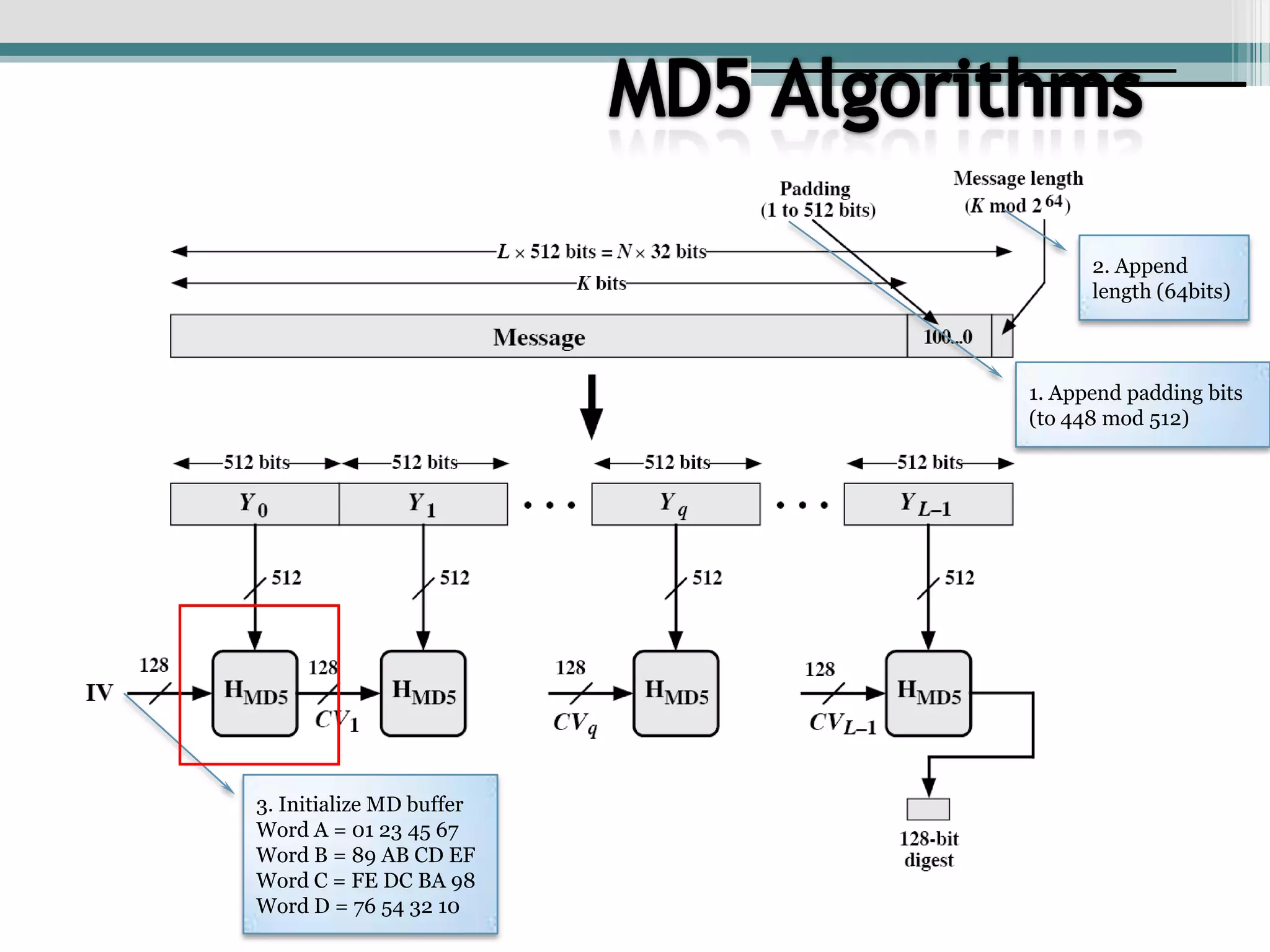
This document discusses cryptographic hash algorithms and focuses on MD5. It lists common hash algorithms and their applications such as file integrity verification and password storage. It then provides details on MD5, describing how it is a 128-bit hash function that was designed in 1991 as a replacement for MD4. The document outlines the MD5 algorithm, providing examples of how it hashes messages, and describes how it has been employed in security applications but is now considered broken due to collisions being found.


![MD5 AlgorithmsF(X,Y,Z) = (X ∧ Y) ∨ (¬X ∧ Z)G(X,Y,Z) = (X ∧ Z) ∨ (Y ∧ ¬Z)H(X,Y,Z) = X ⊕ Y ⊕ ZI(X,Y,Z) = Y ⊕ (X ∨ ¬Z)Round 0: Steps 0 to 15Round 1: Steps 16 to 31Round 2: Steps 32 to 4716 stepsRound 4: Steps 47 to 63X[k] = M [q*16+k] (32 bit)Constructed from sine function](https://image.slidesharecdn.com/criptographyashik-090808112249-phpapp02/75/Cryptography-Ashik-10-2048.jpg)