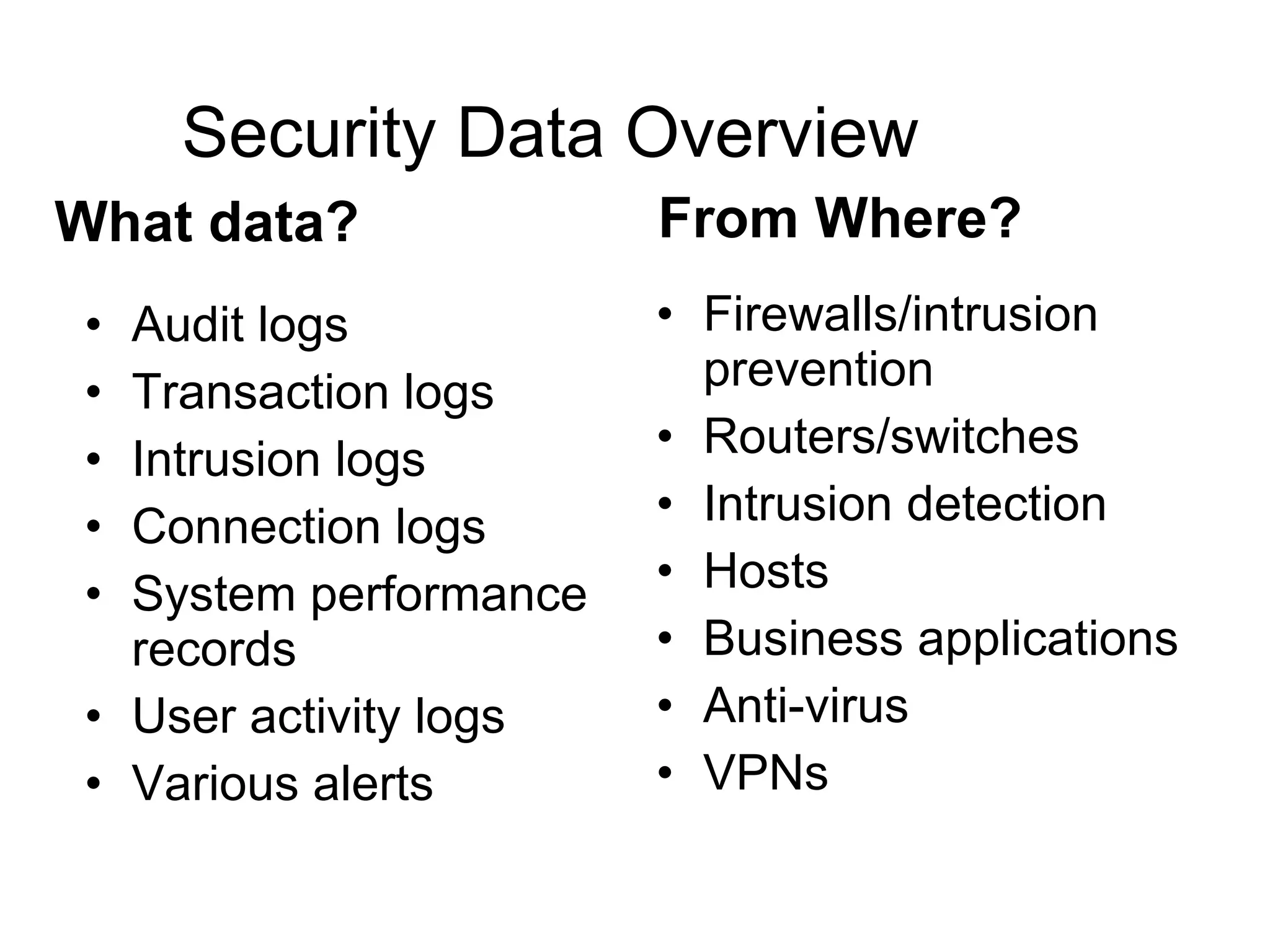
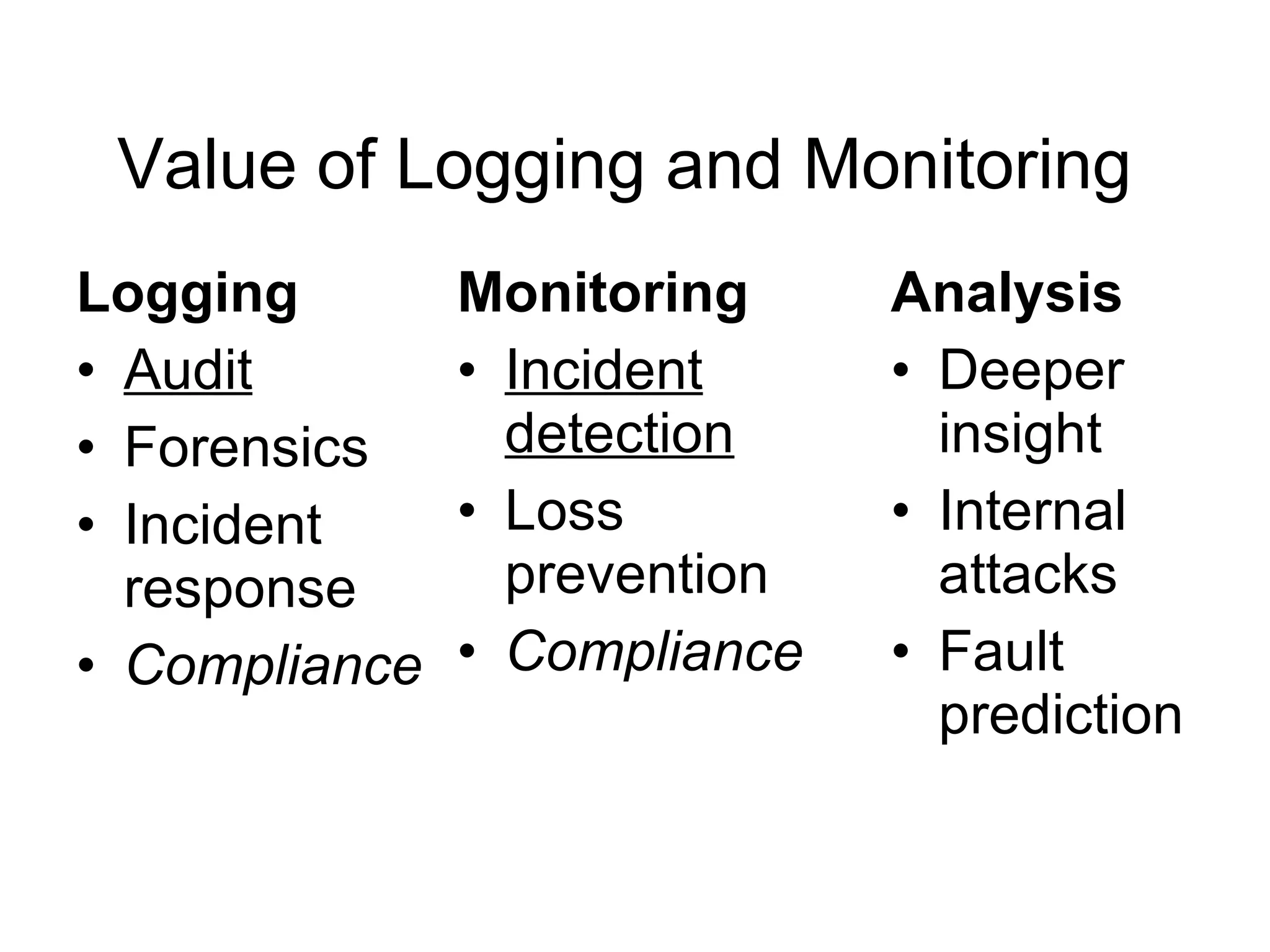
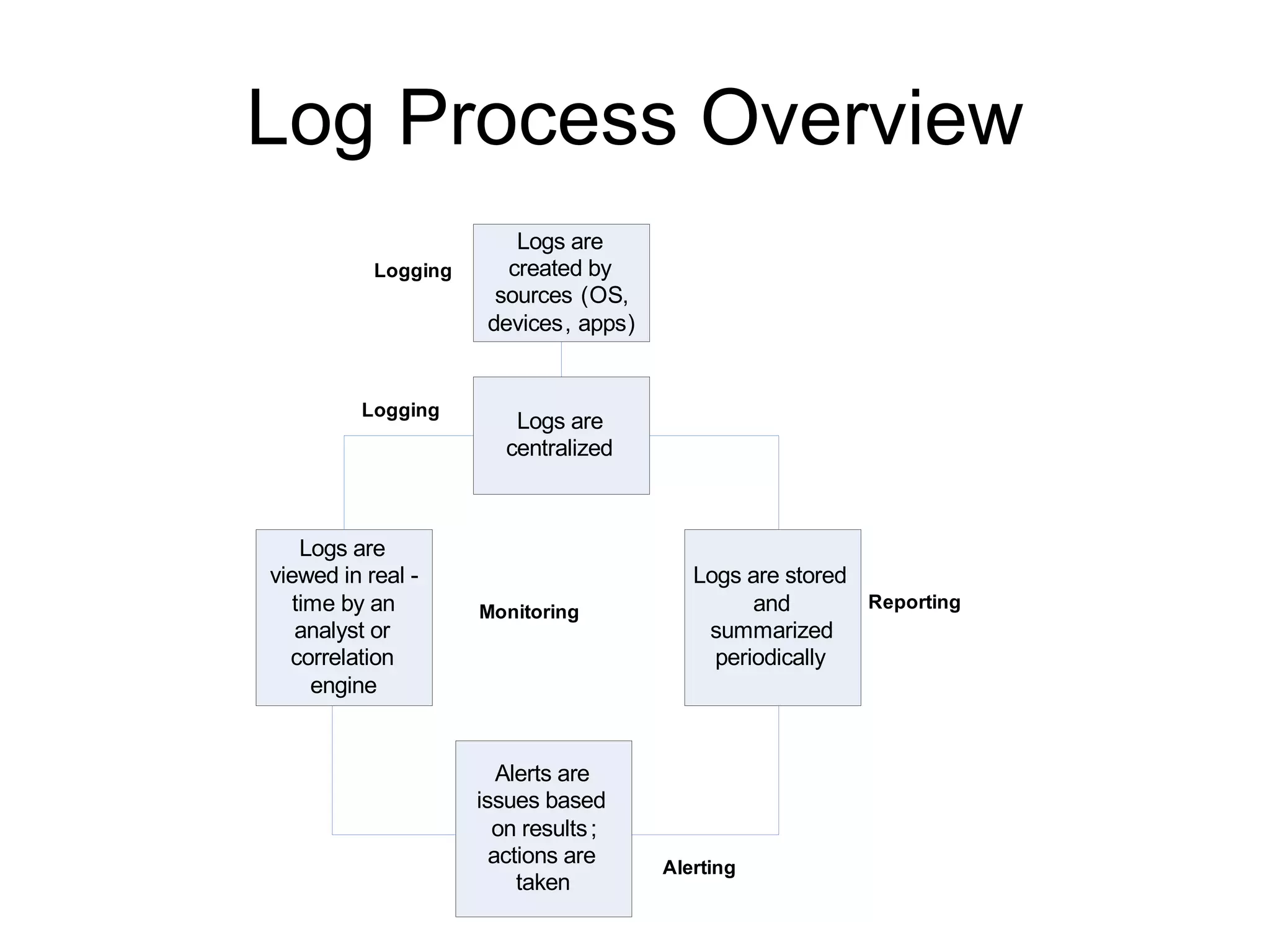
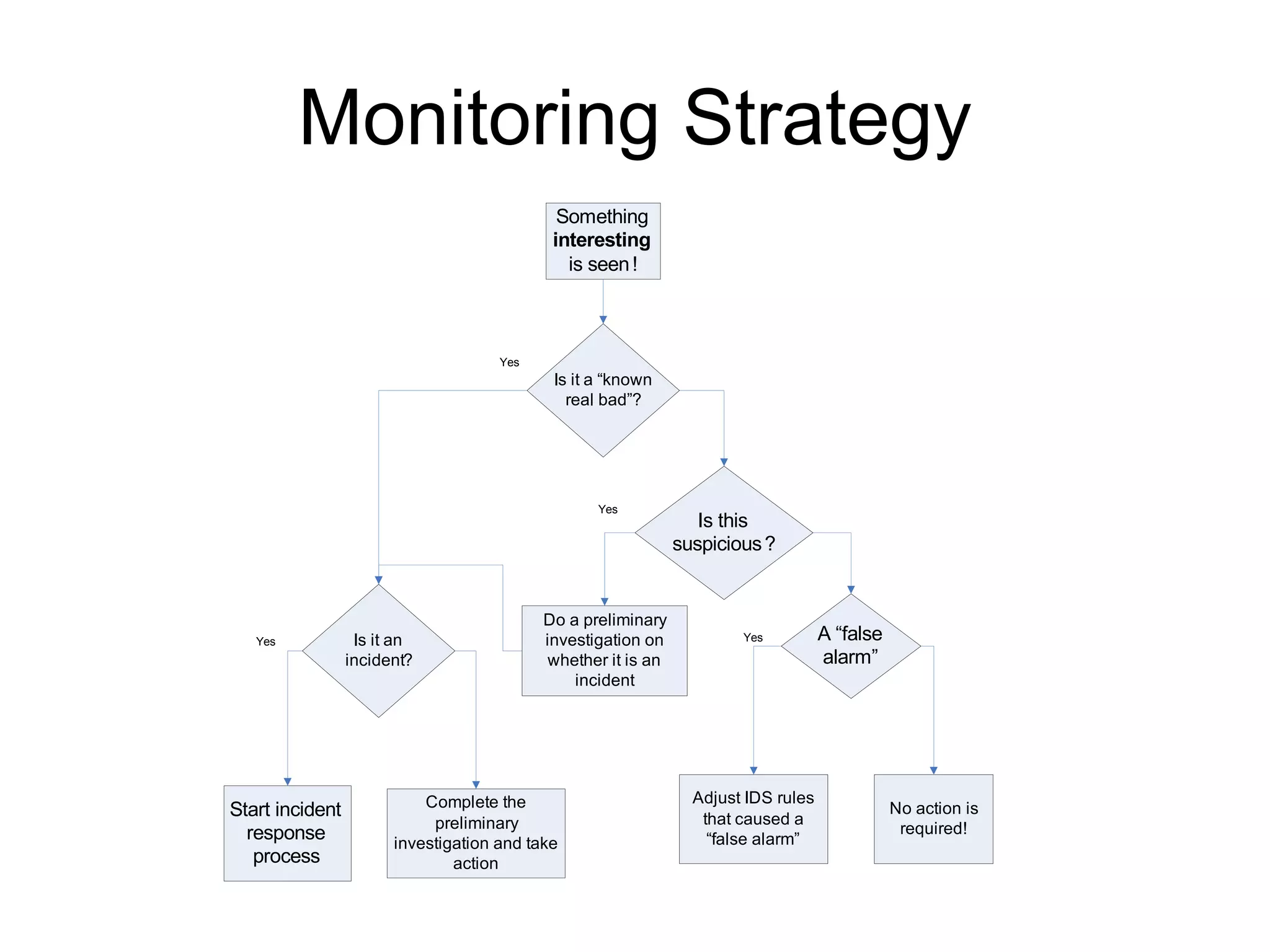
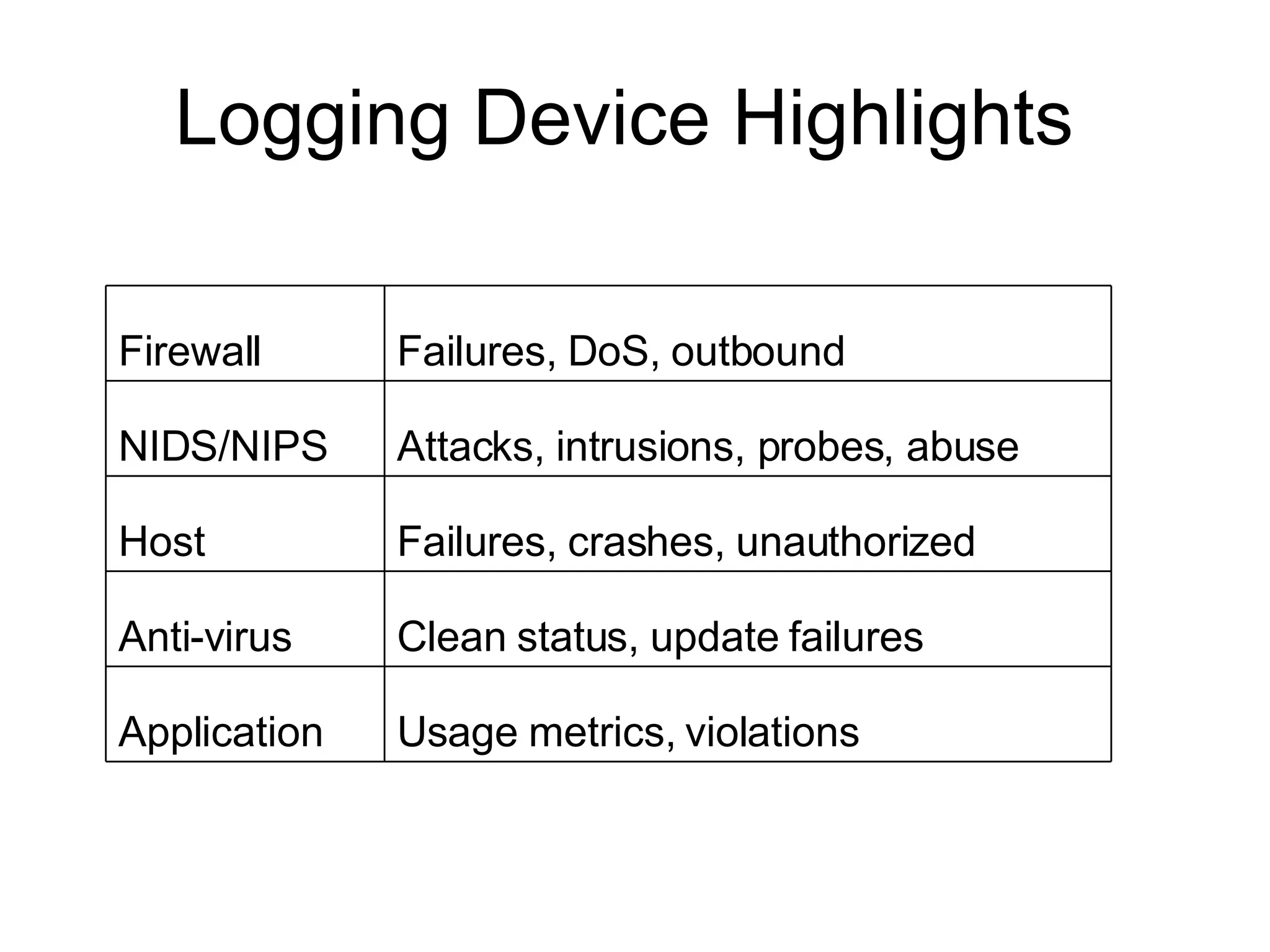
The document outlines essential logging and monitoring practices for organizations, emphasizing the importance of log management strategies, incident response, and compliance with regulations. It covers types of logs to collect, the process of centralizing logs, and the need for a phased approach in setting up a log monitoring program. Additionally, it highlights challenges in deployment, the significance of real-time analysis, and the importance of logs in forensic investigations and regulatory compliance.