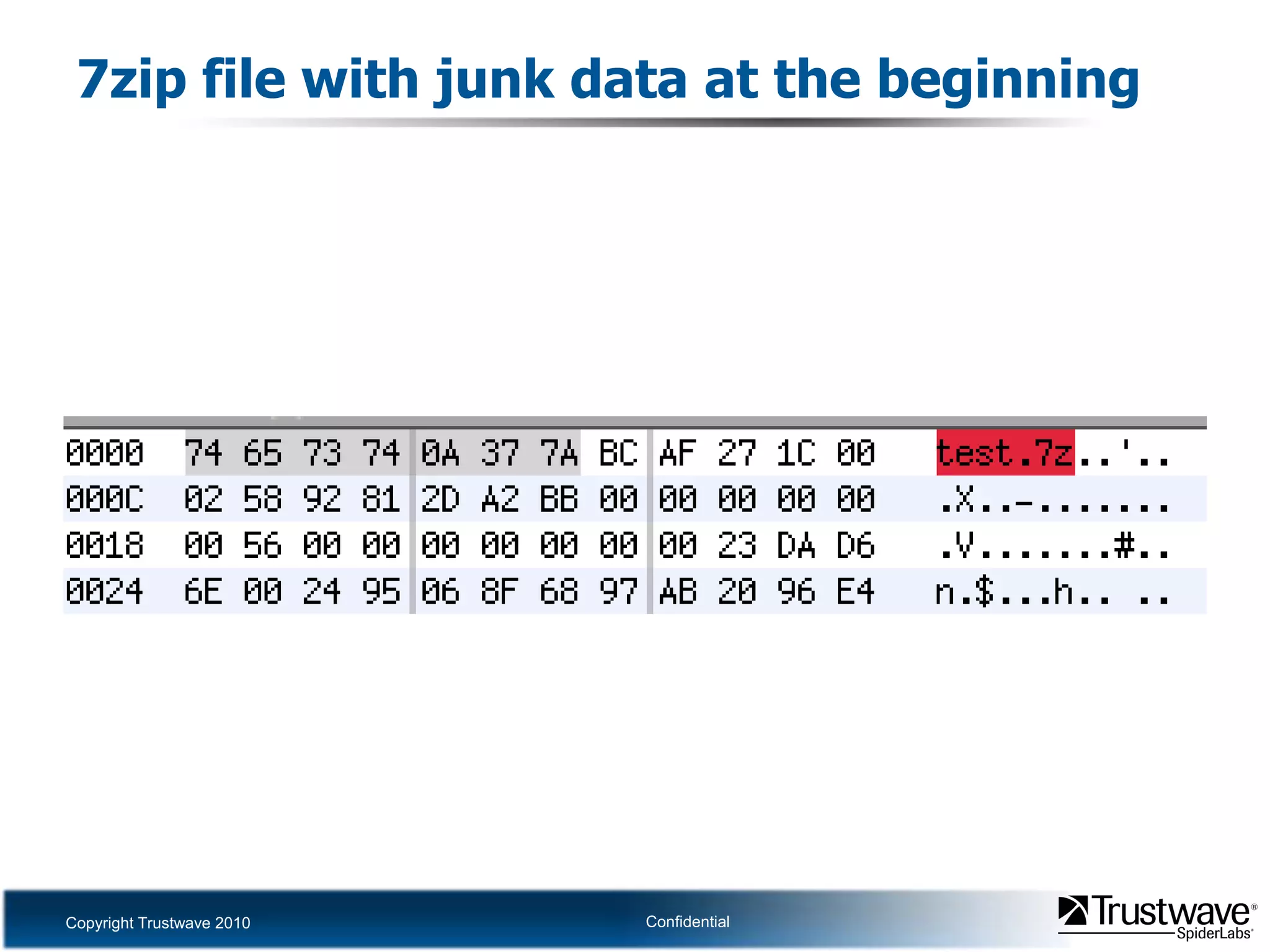
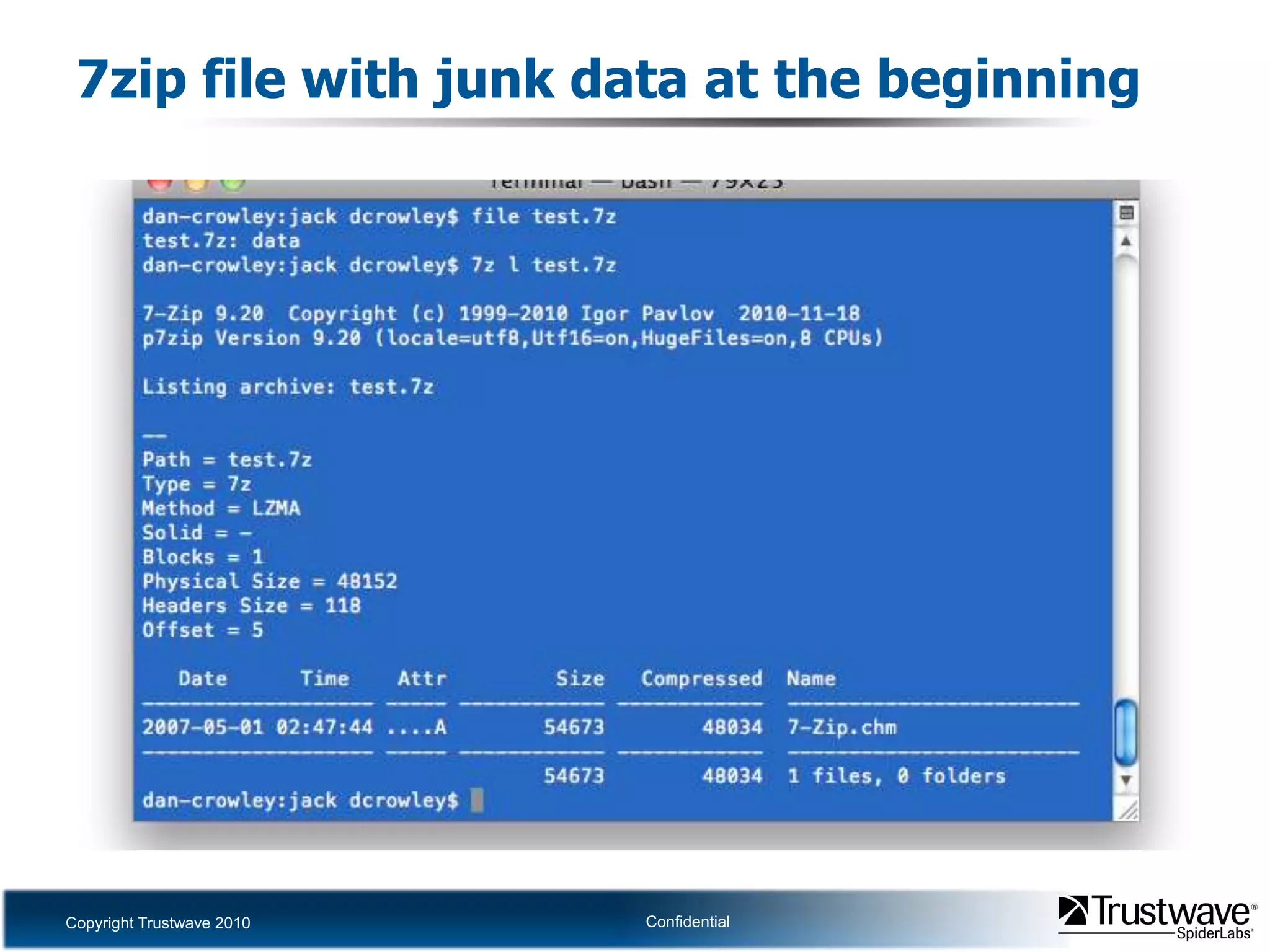
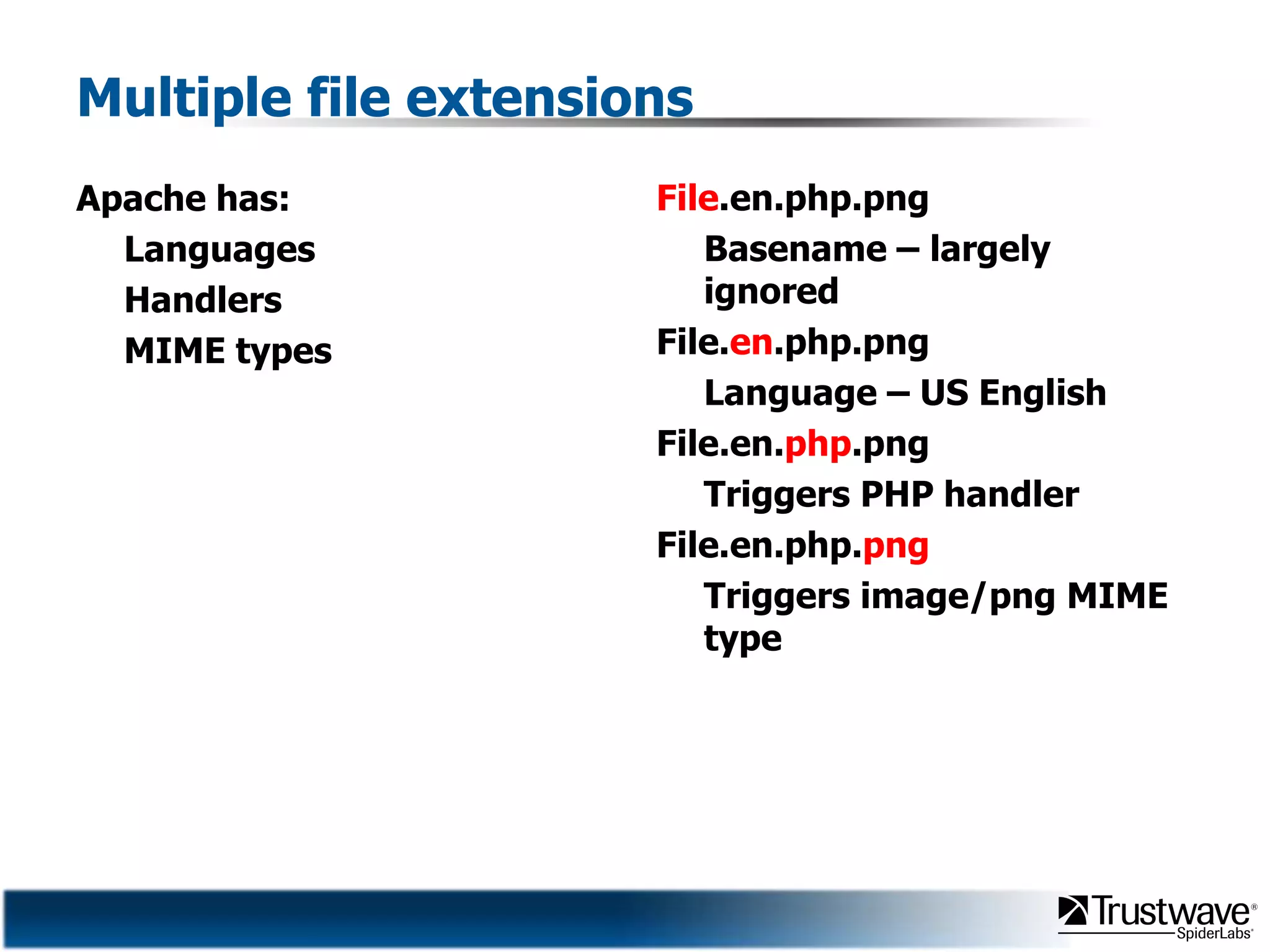
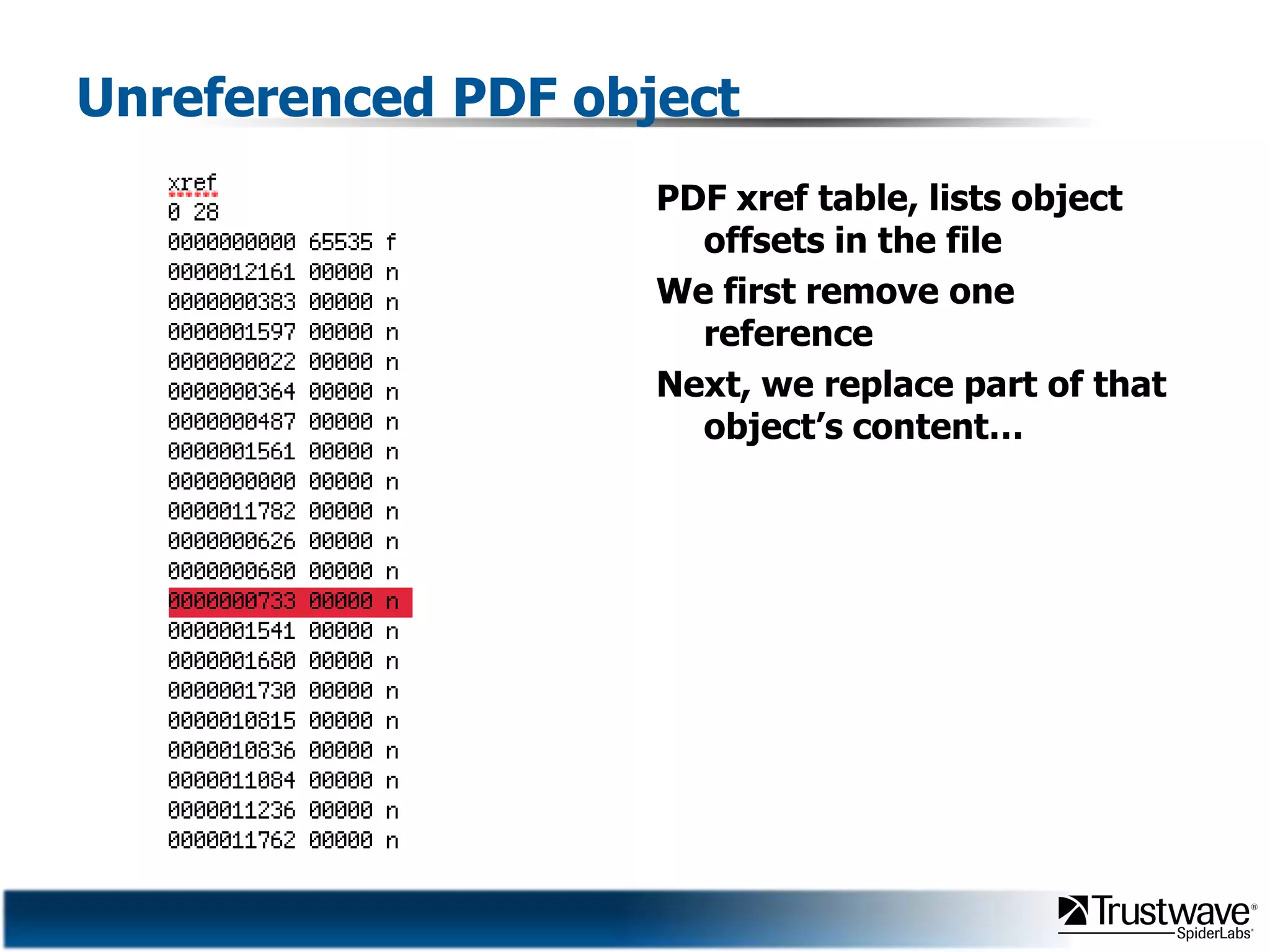
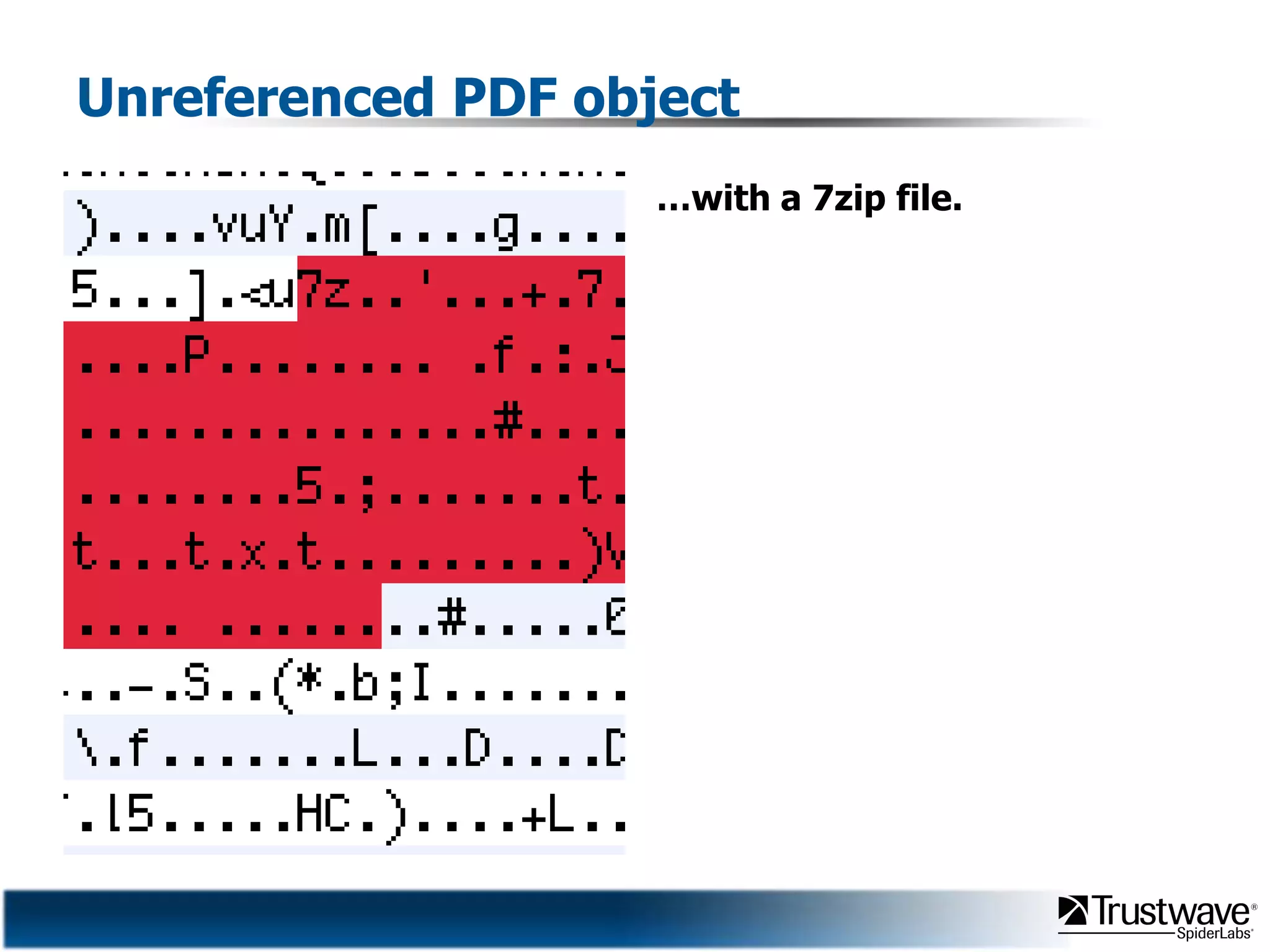
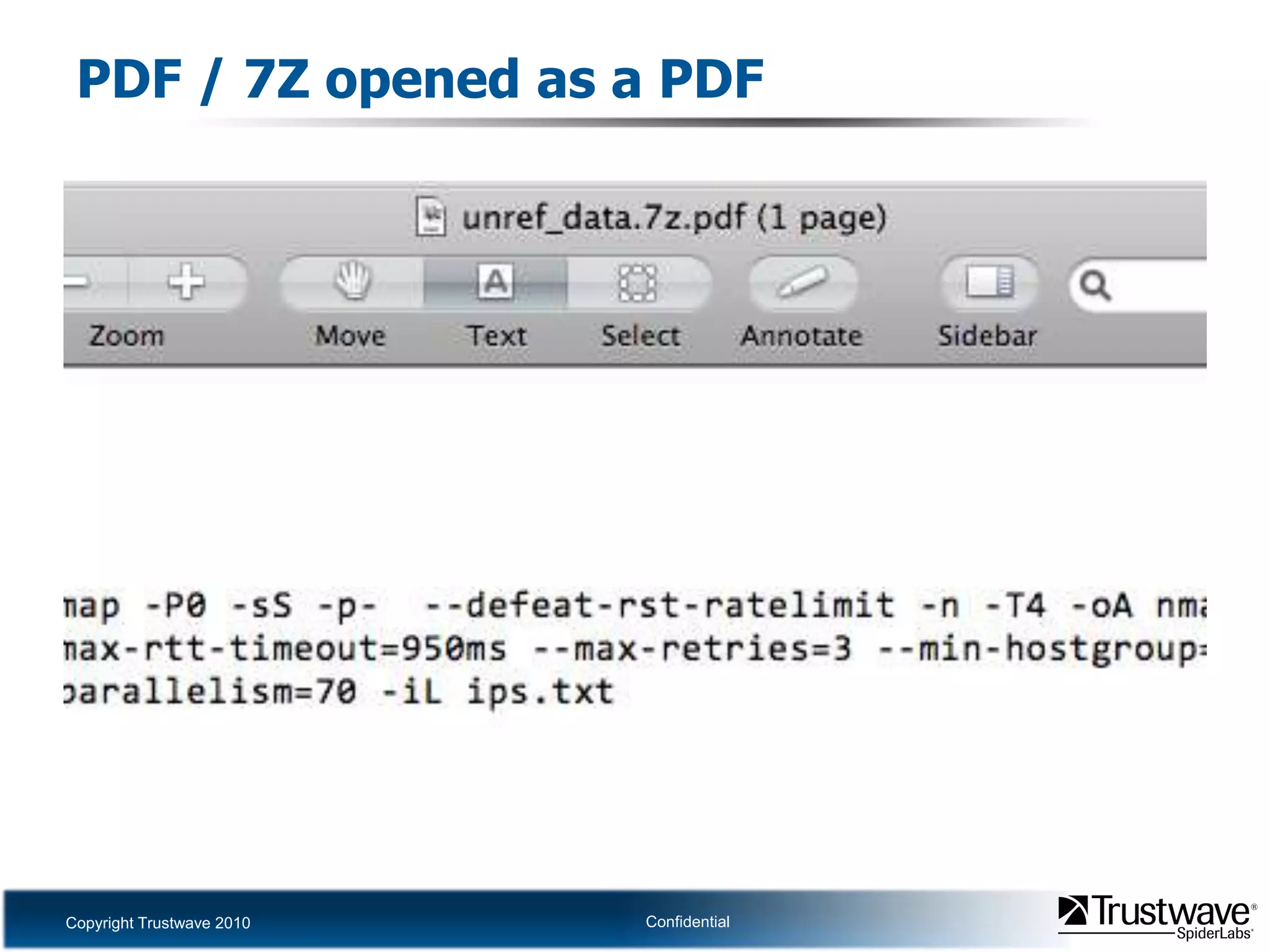
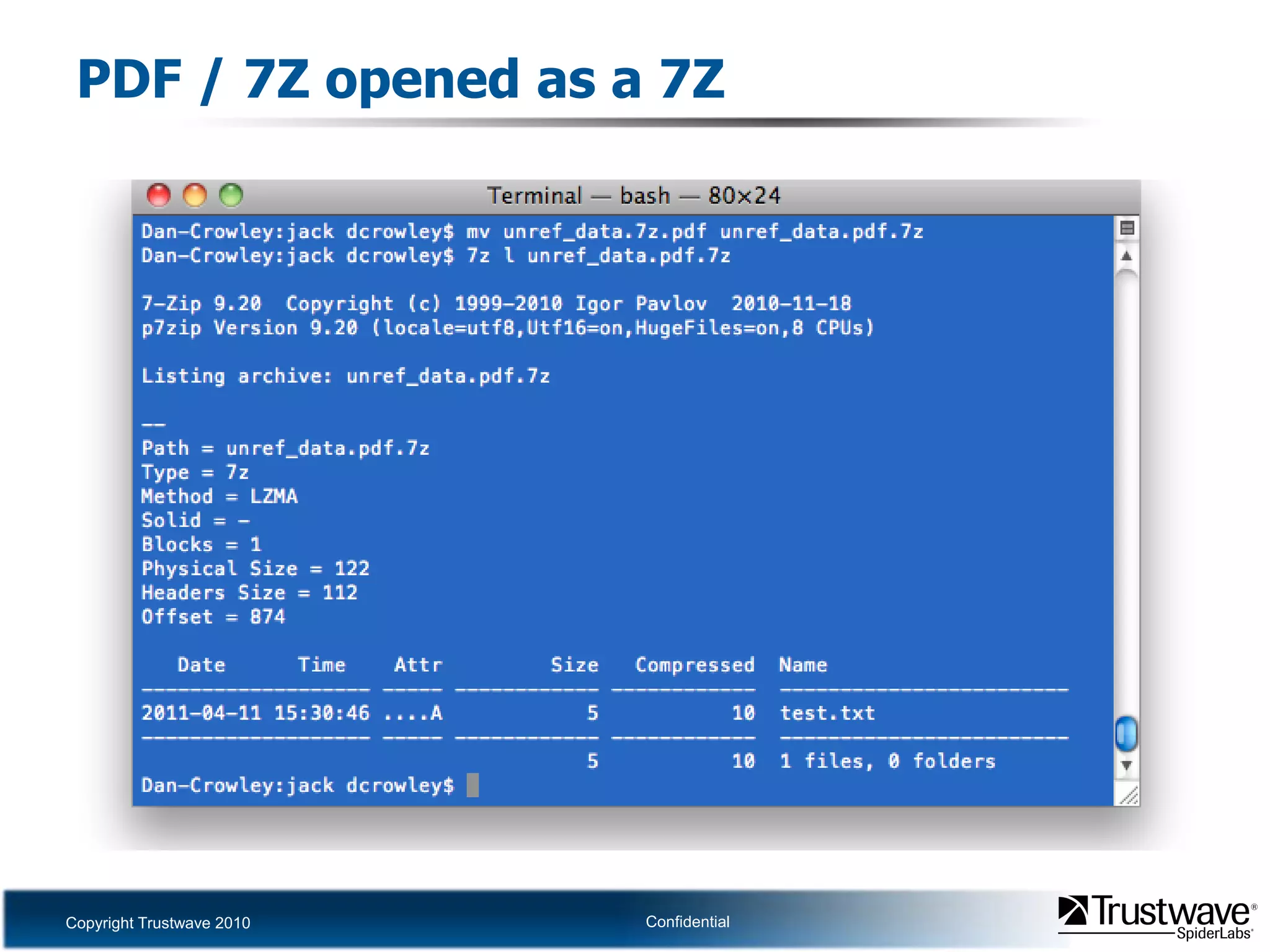
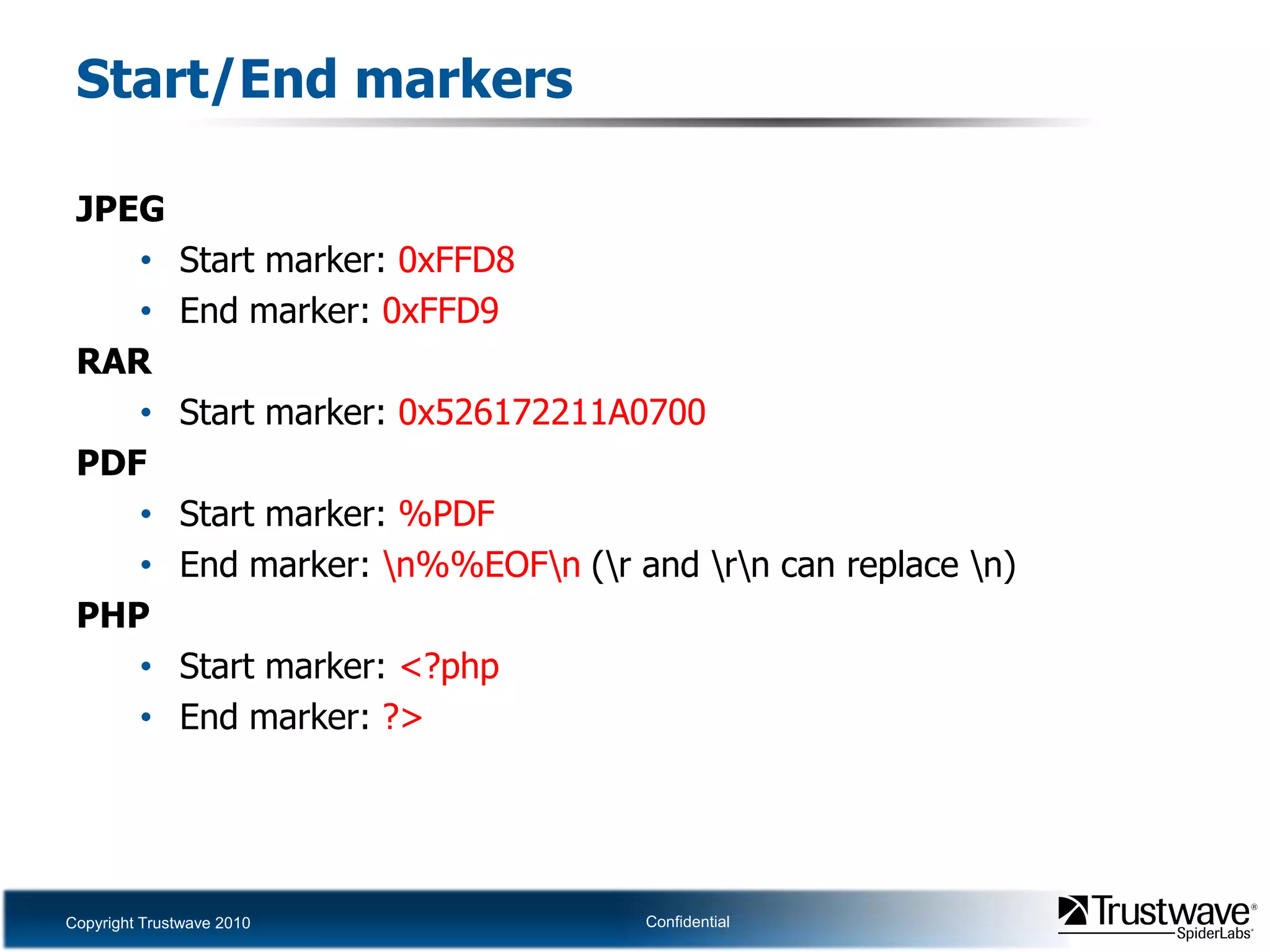
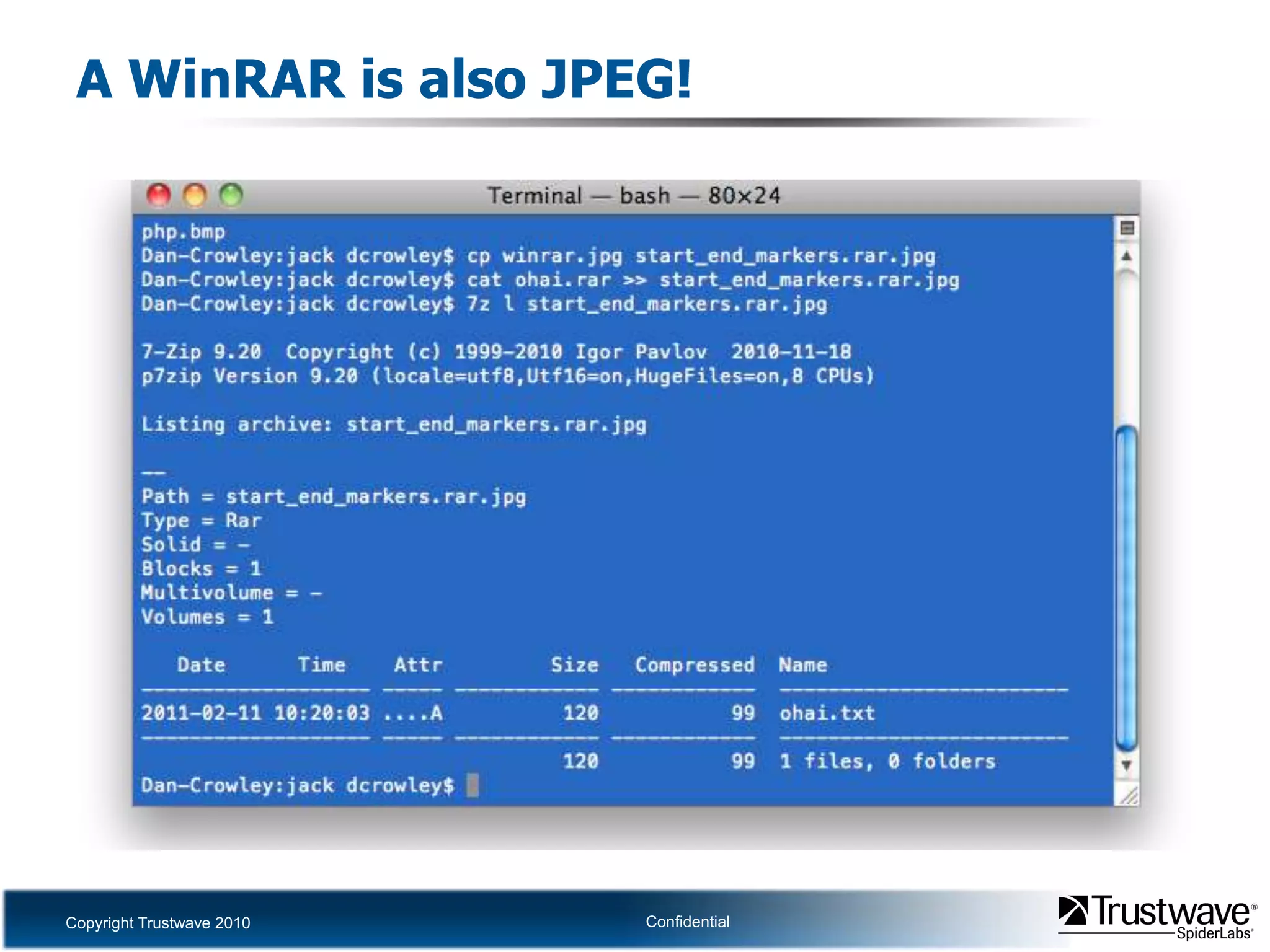
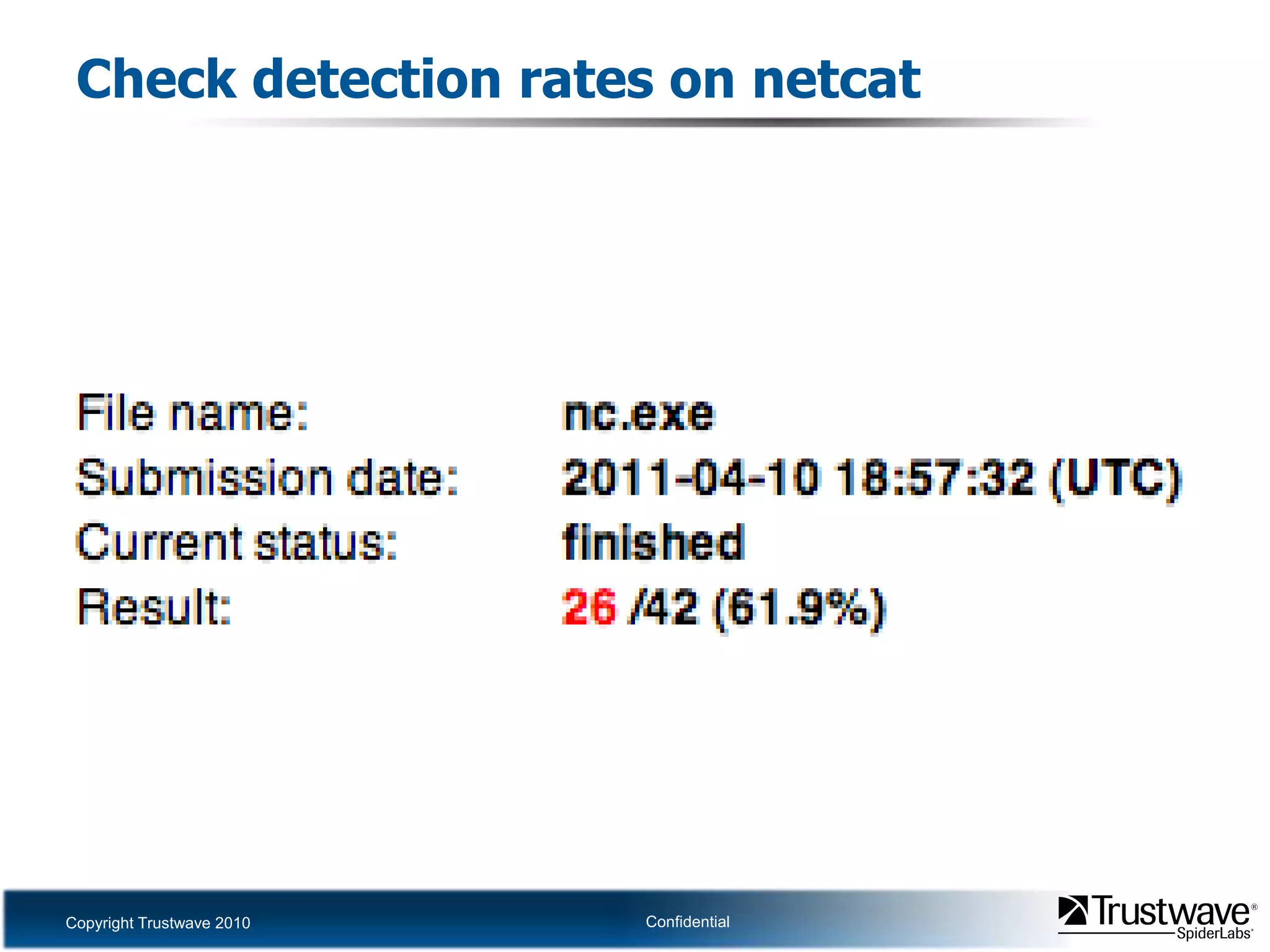
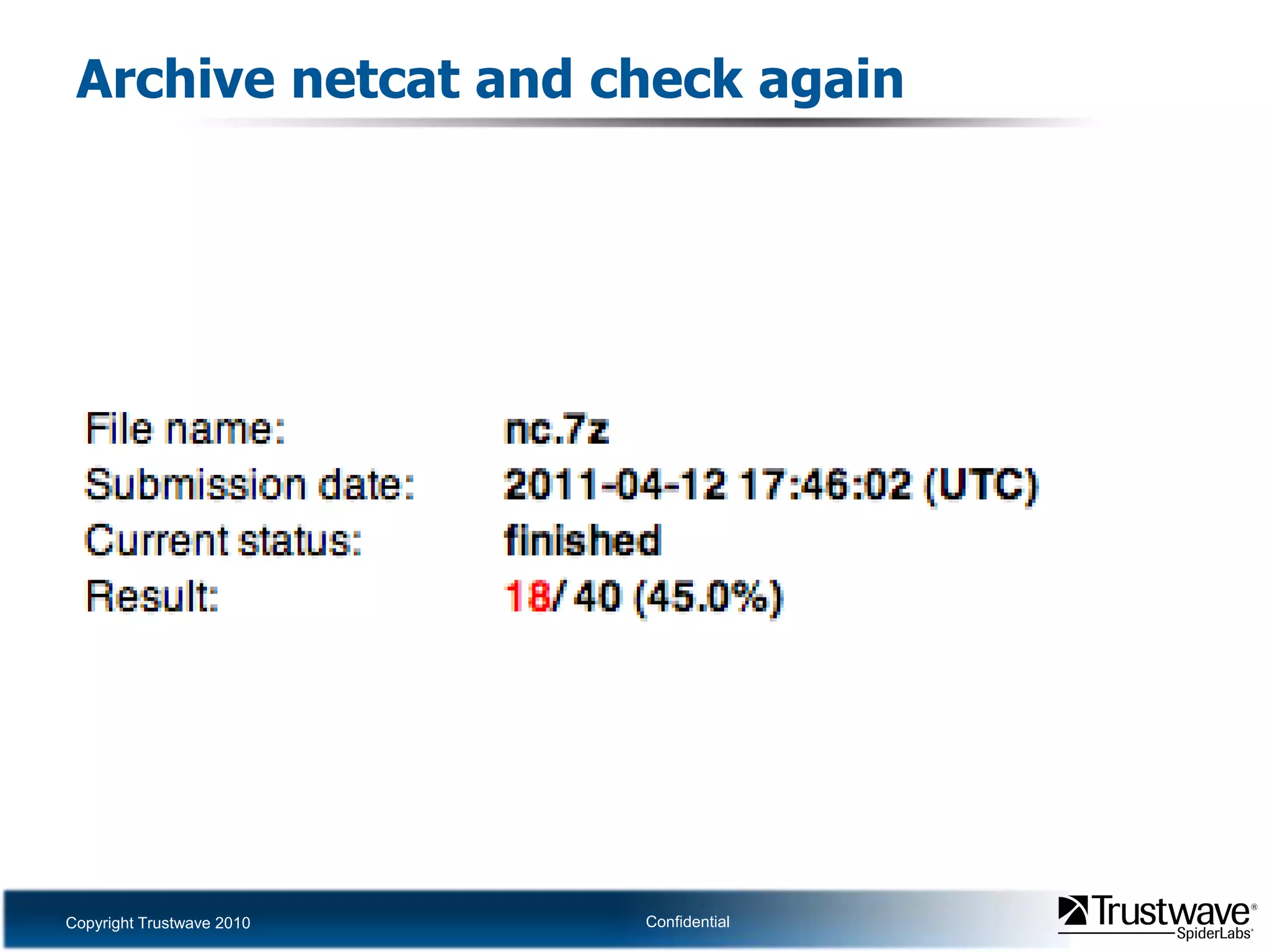
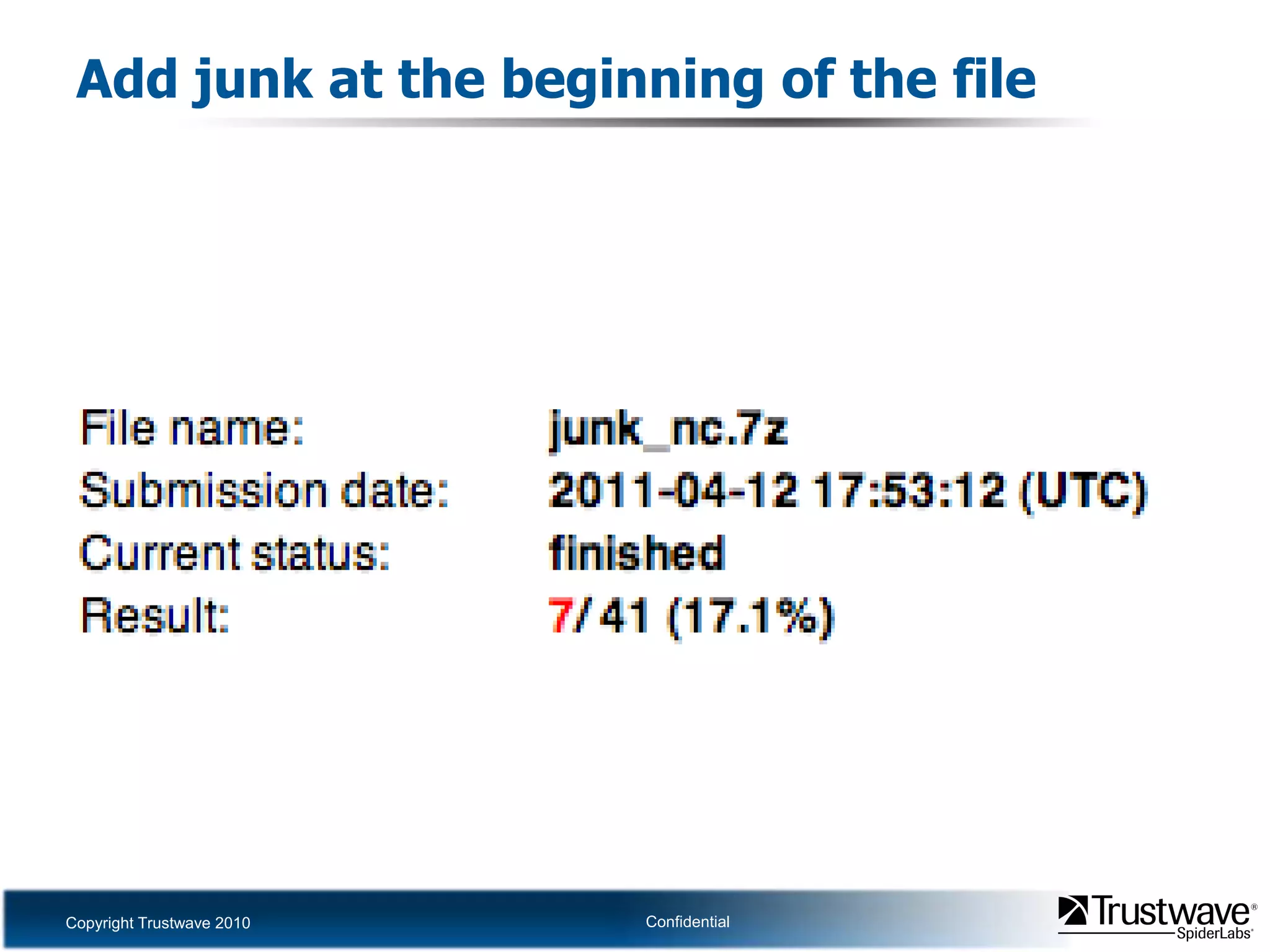
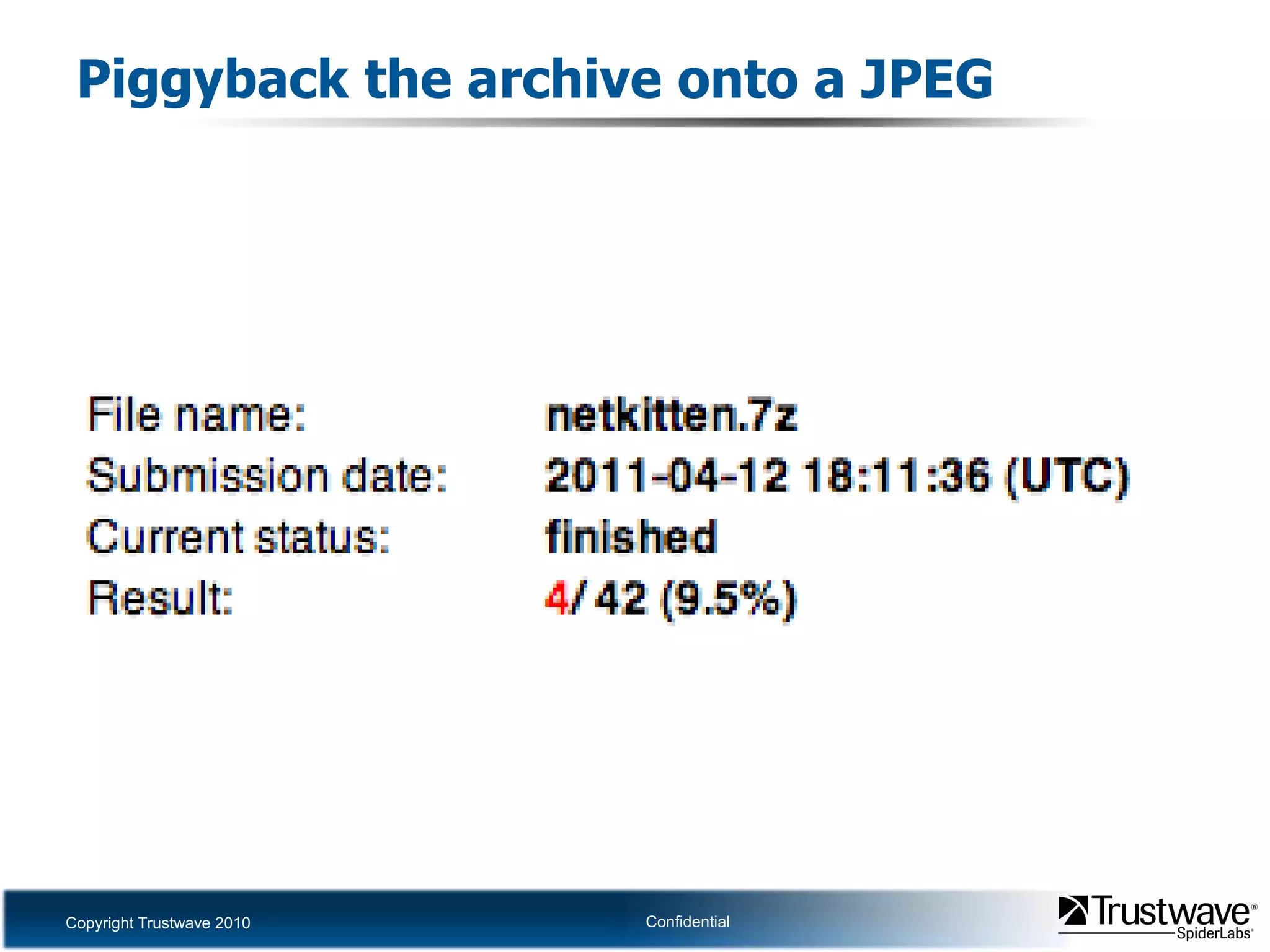
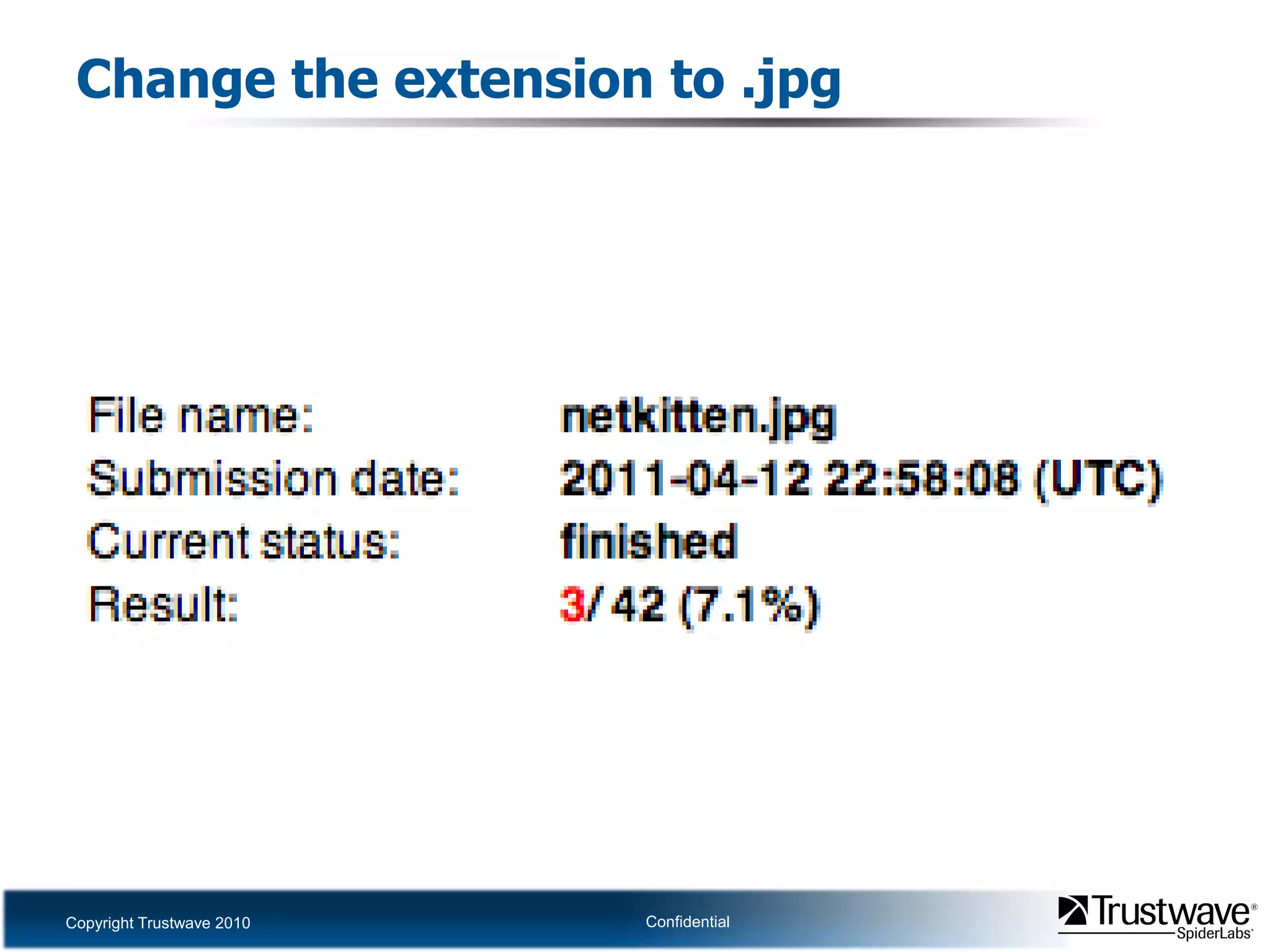
This document discusses how files can contain data in multiple formats by piggybacking one file type into another. It provides examples of how files like JPEGs, PDFs, and GIFs can sometimes contain additional hidden data like archives, scripts, or documents. This technique could allow for covert channels, bypass of security tools like antivirus, and denial of service attacks if file size limits are not properly enforced. The document recommends defenses like validating the full file contents and allowed extensions for file uploads to prevent abuse of this flexibility in file formats.