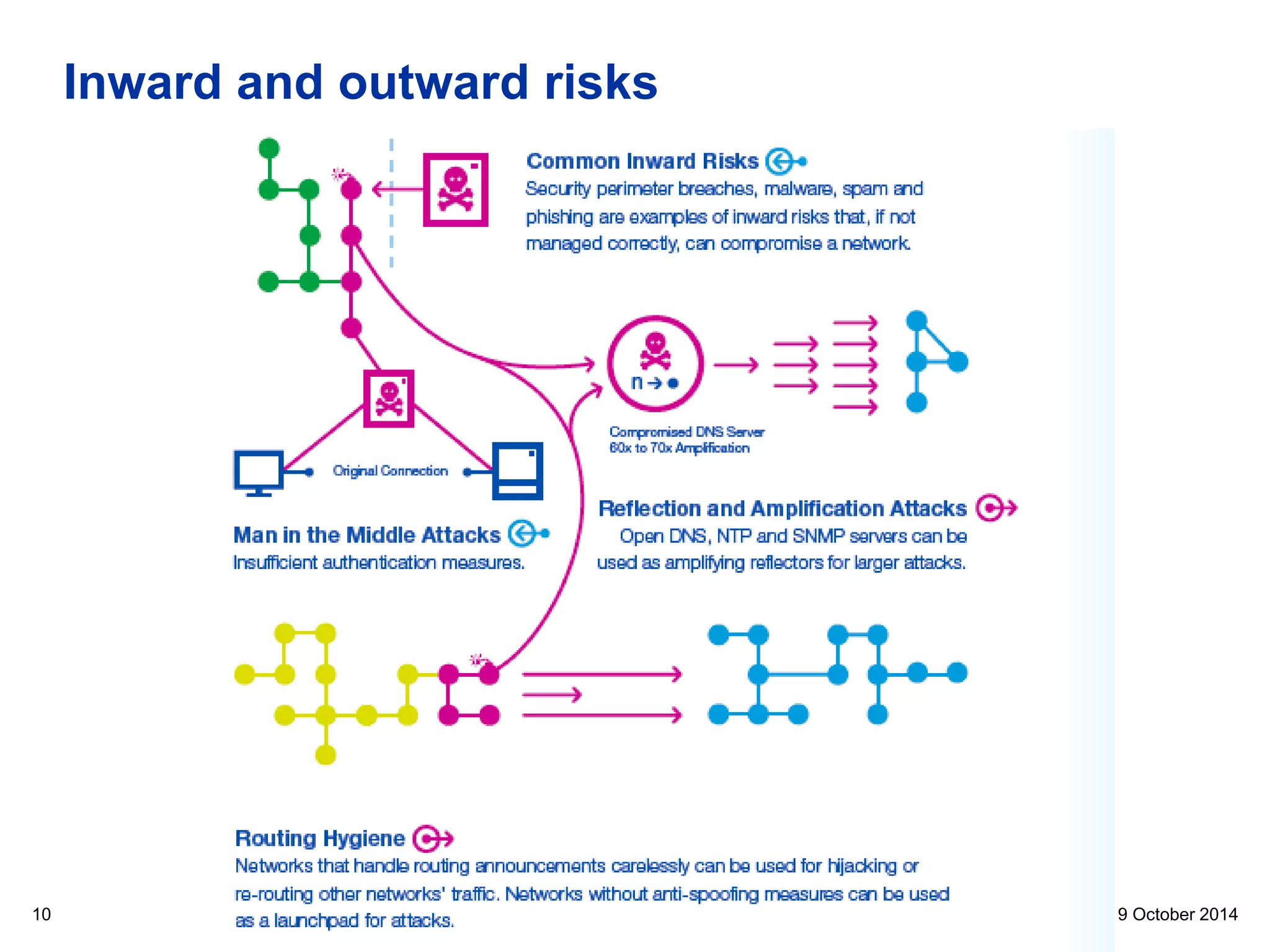
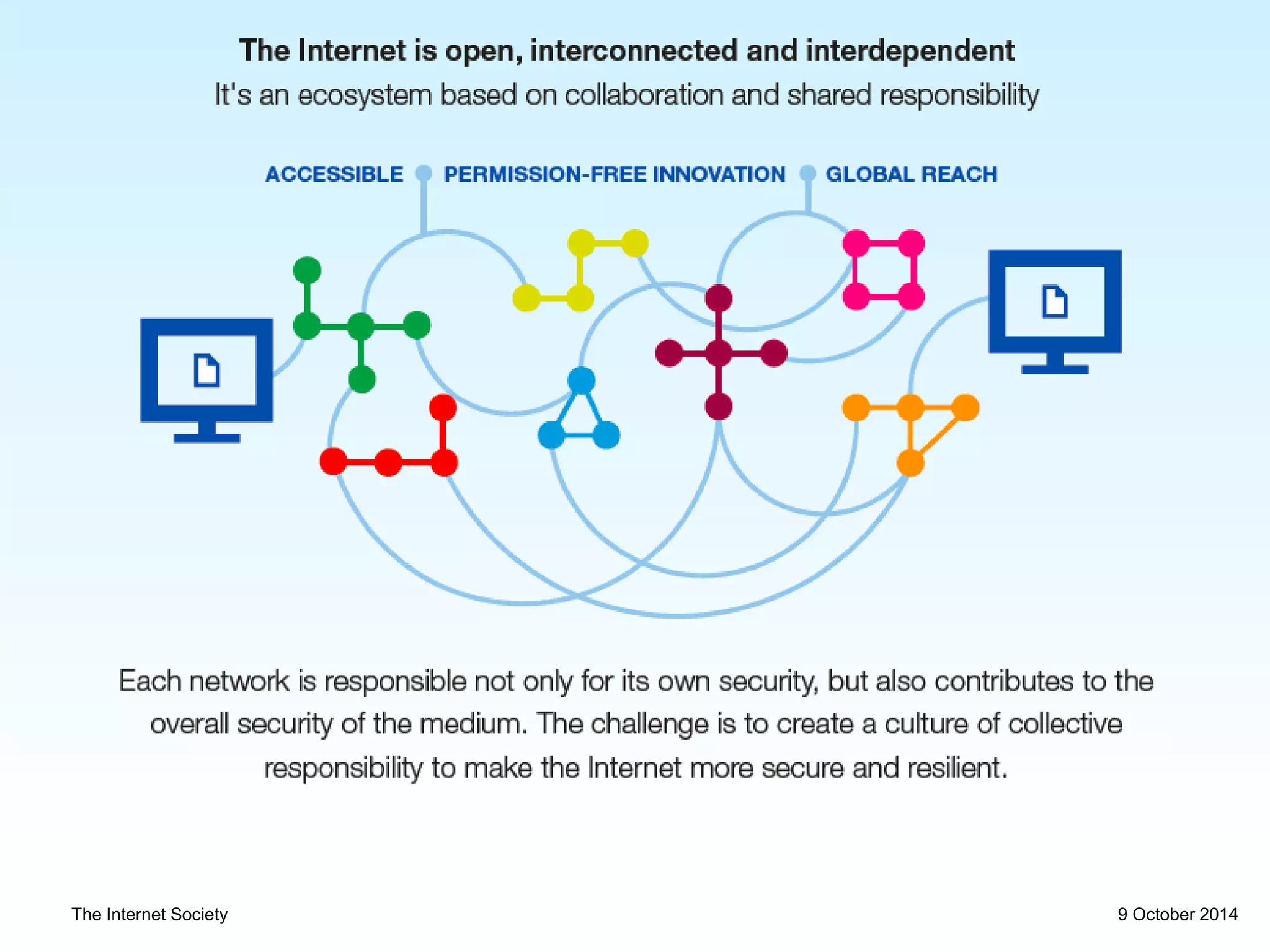
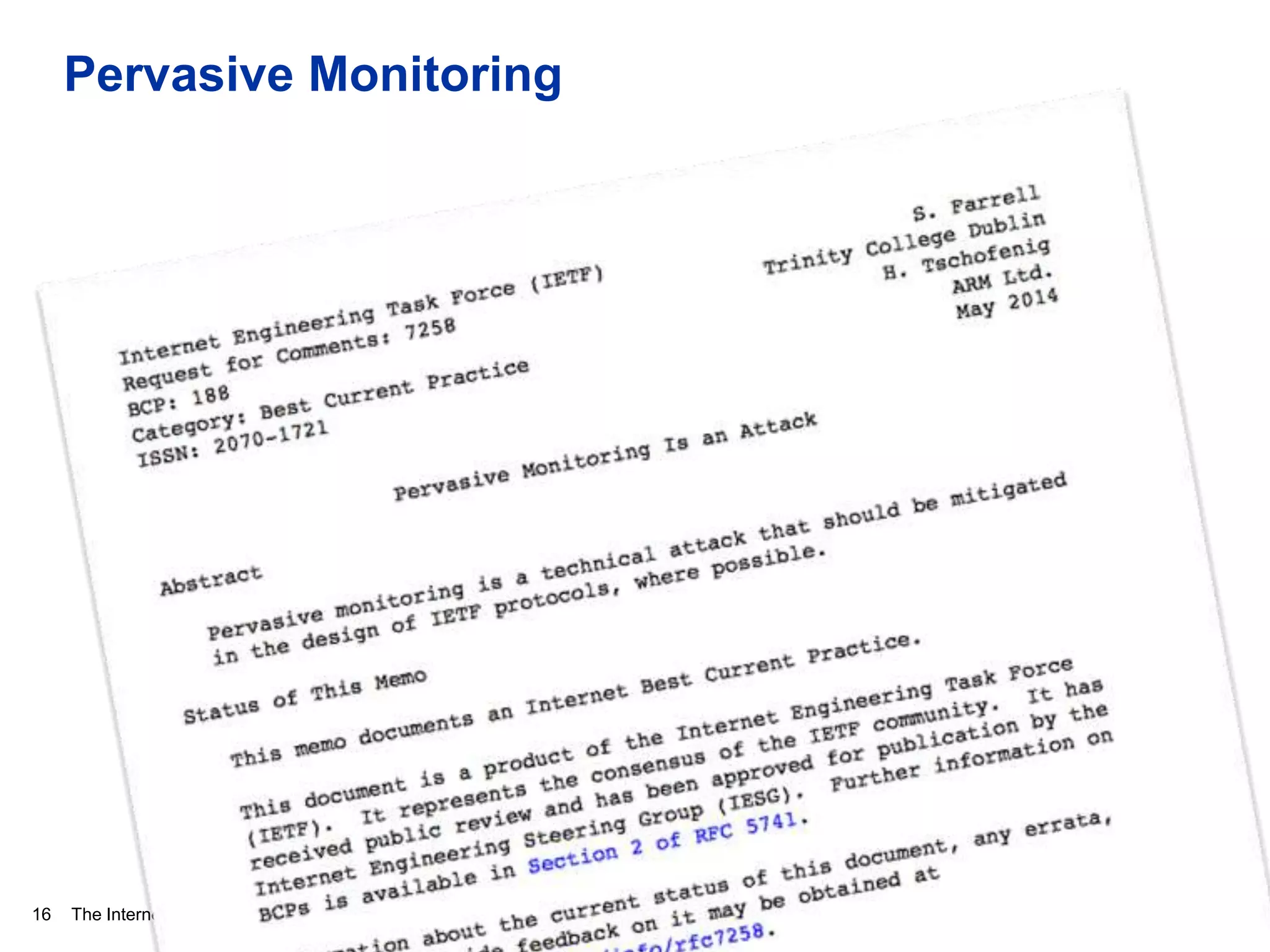
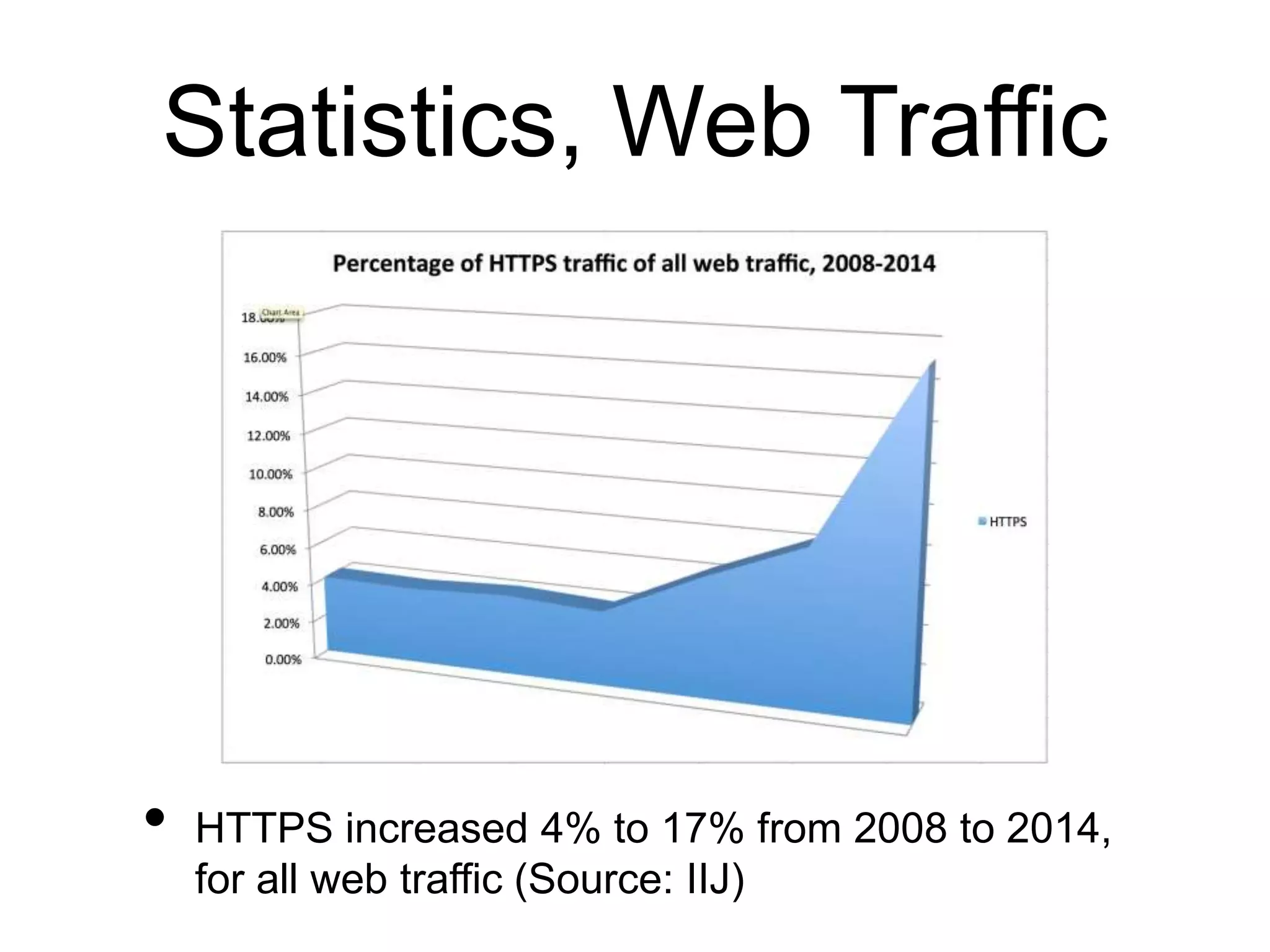
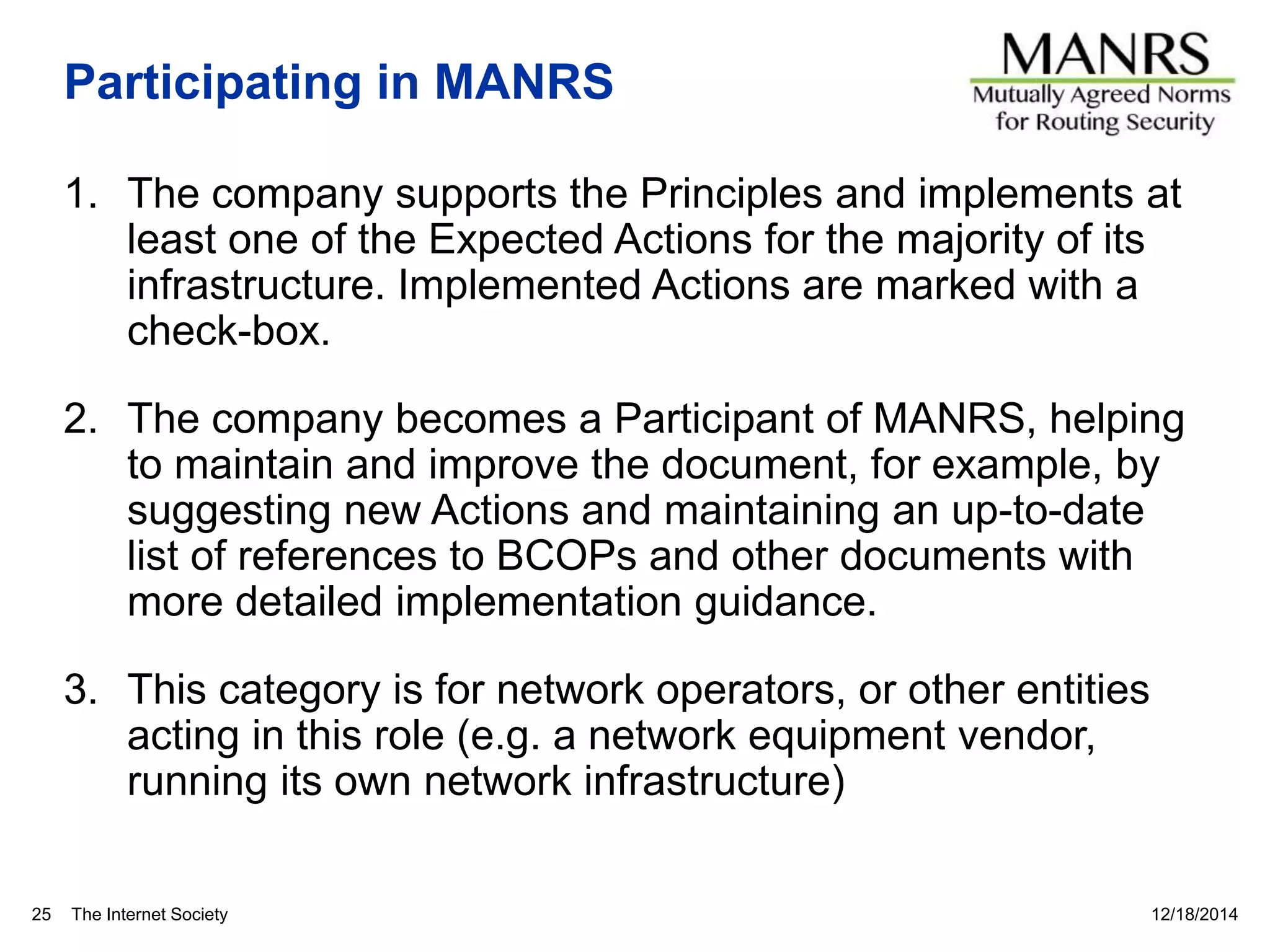
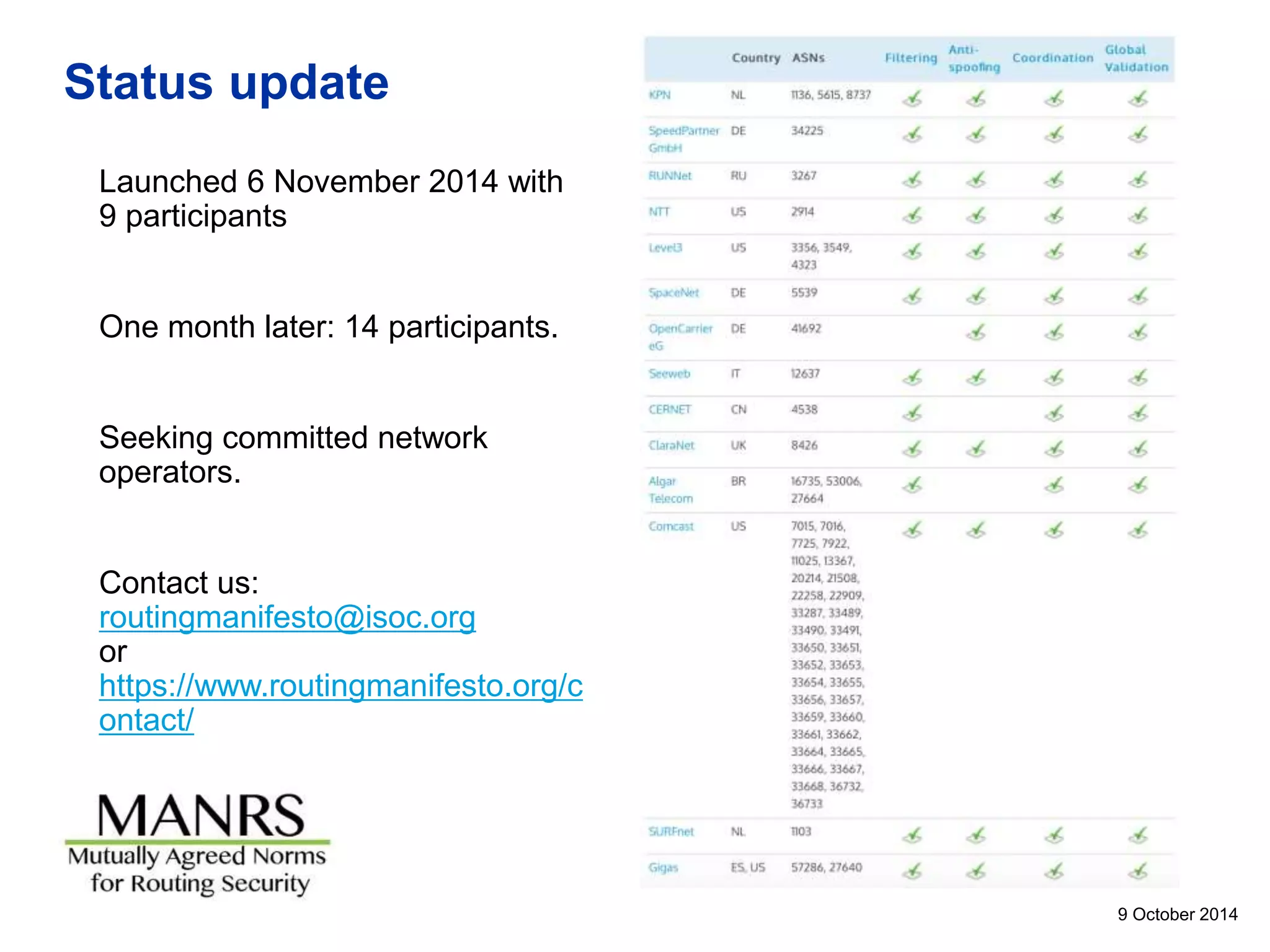
This document discusses internet security and resilience. It argues that security is about managing acceptable risks rather than stopping all threats. An open, collaborative approach based on technical standards and cooperation across borders is needed. Voluntary initiatives like MANRS that define best practices for routing security and encourage networks to implement them can help address complex issues in a way that preserves internet values. Pervasive monitoring shifts rather than eliminates surveillance and technical solutions must balance security with privacy and innovation.