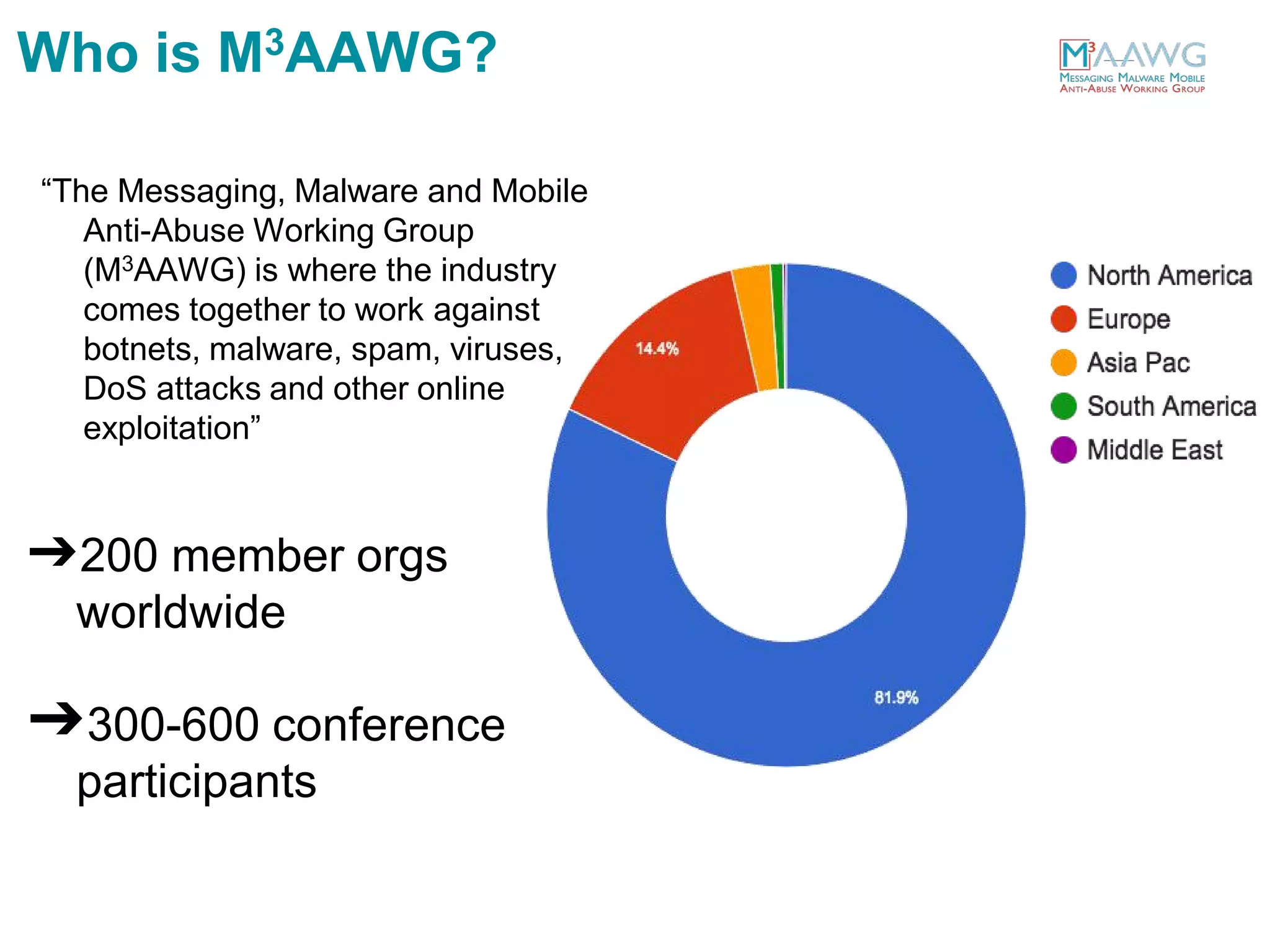
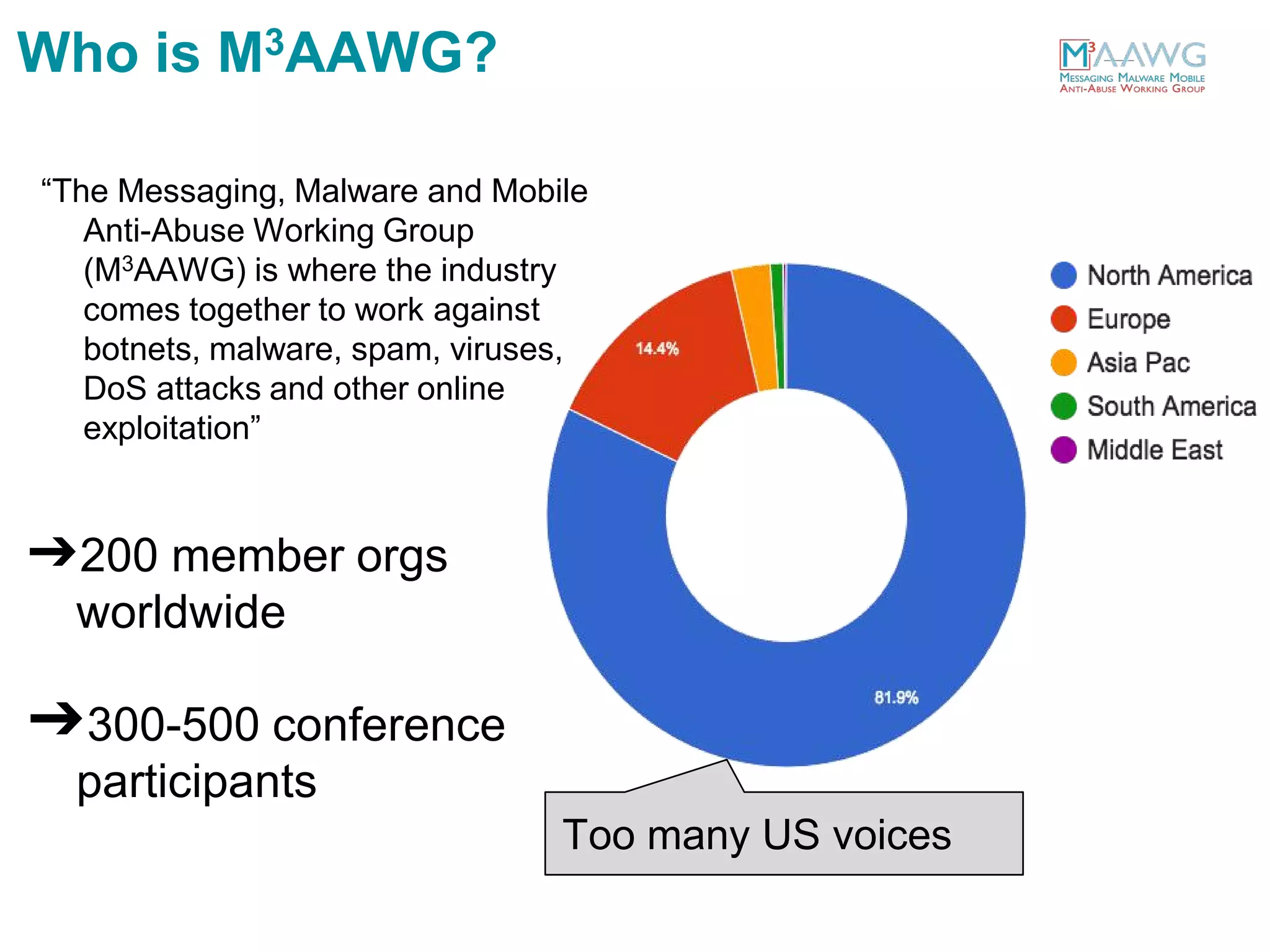
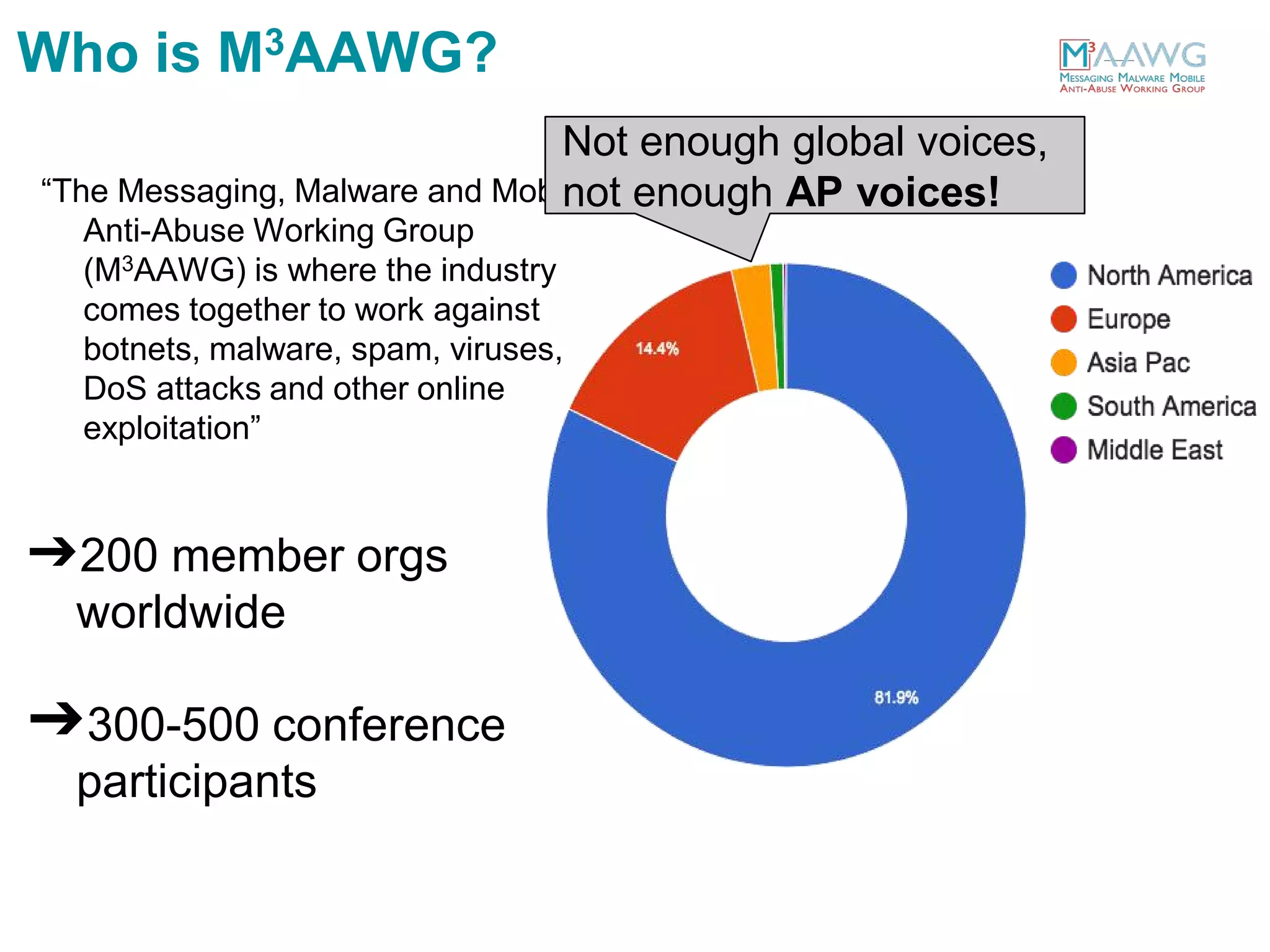
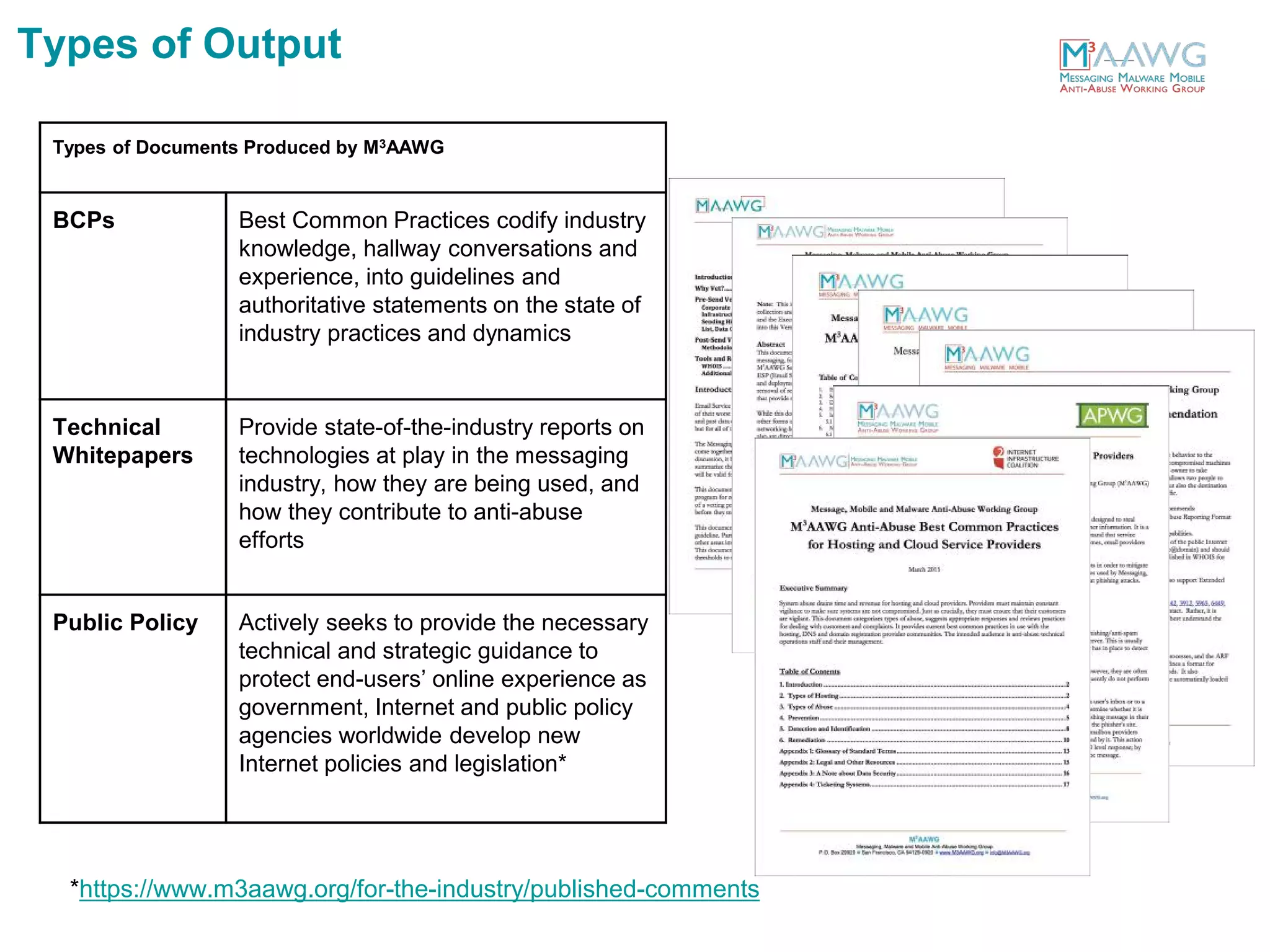
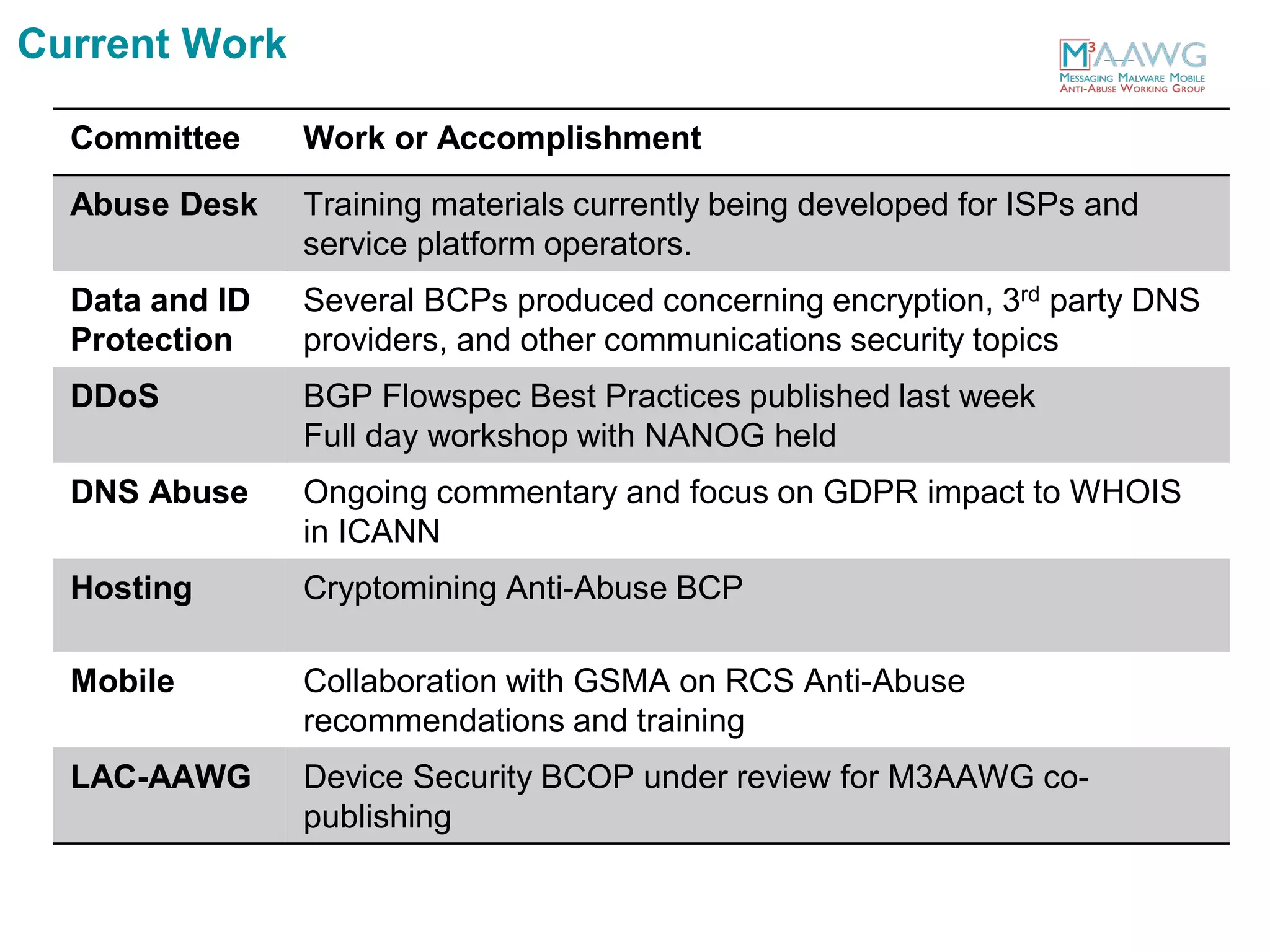
The document discusses the Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG). M3AAWG is an industry group with over 200 member organizations worldwide that works to address issues like botnets, malware, spam, and denial of service attacks. The group produces best practices documents, publishes technical reports, and provides guidance to policymakers. It also facilitates collaboration and information sharing between members through working groups and annual conferences to more effectively combat online abuse and threats.