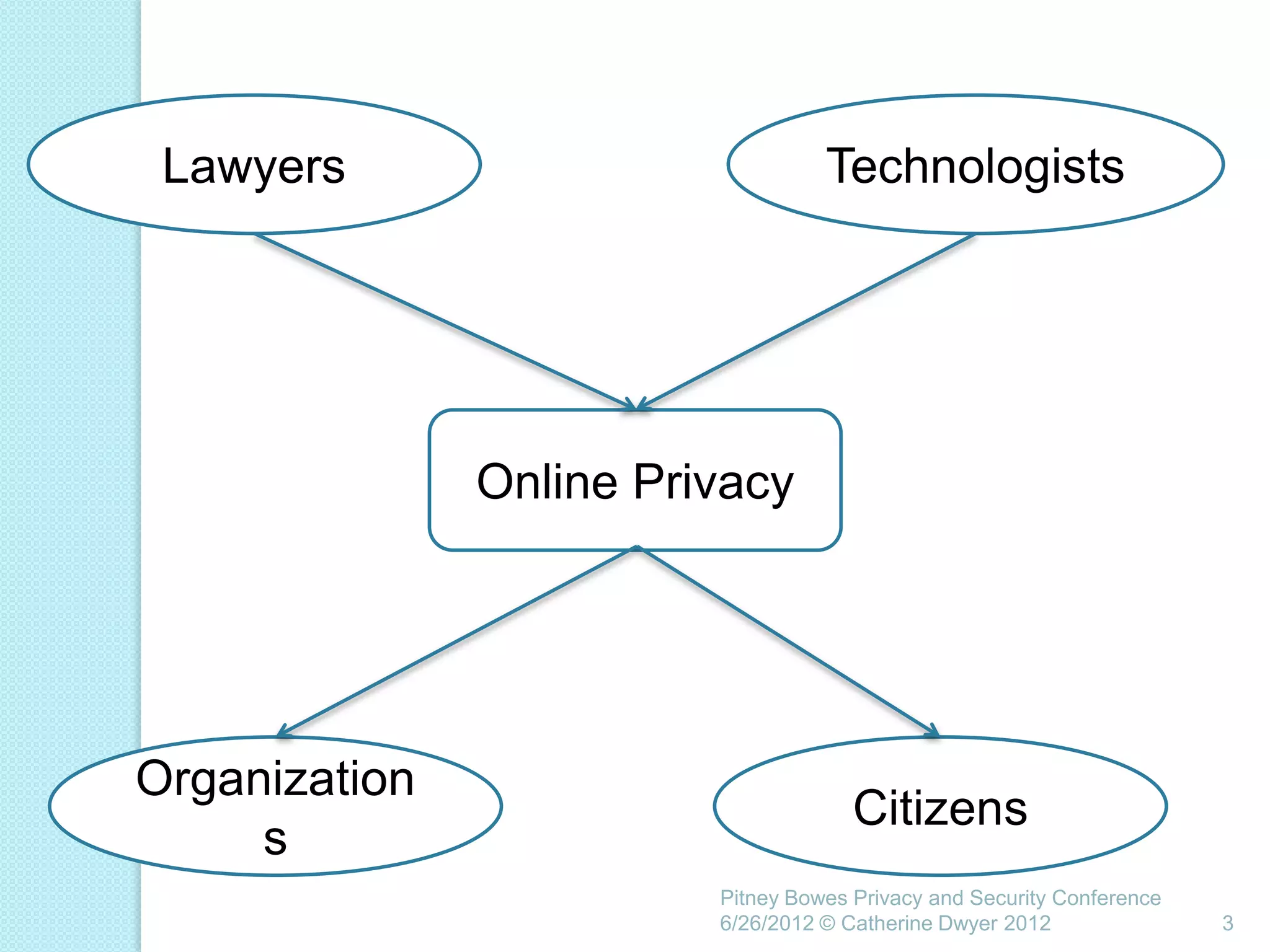
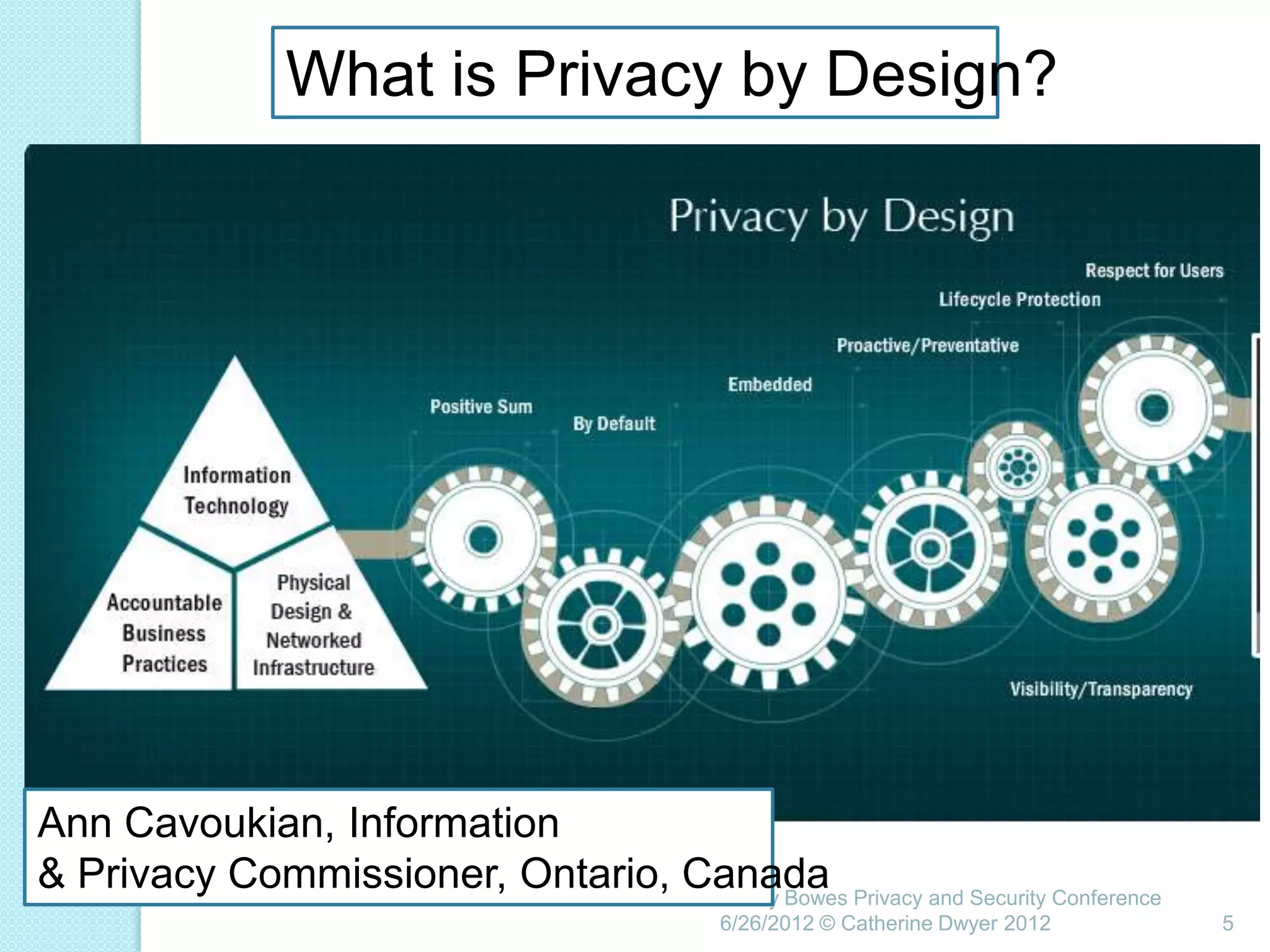
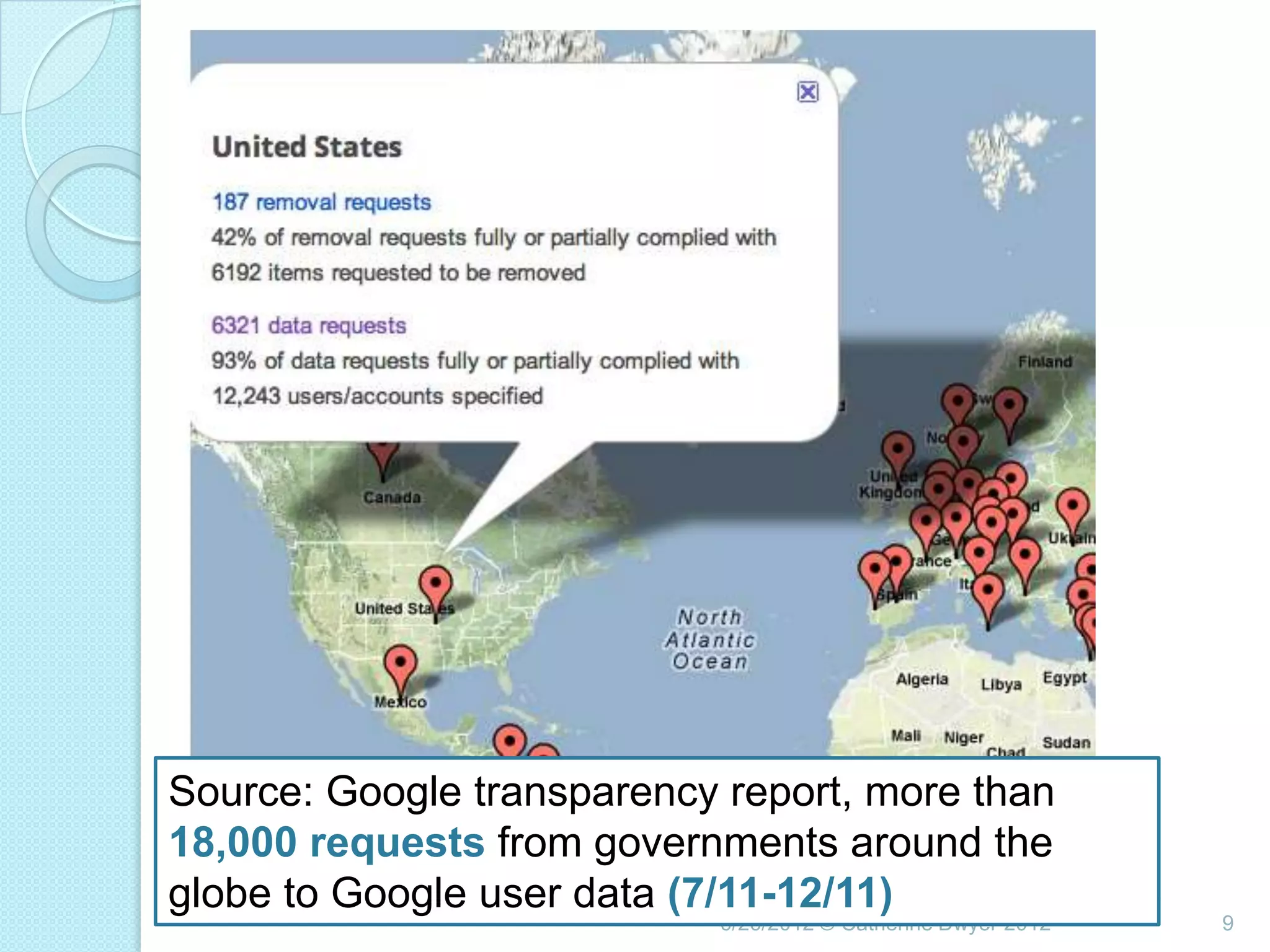
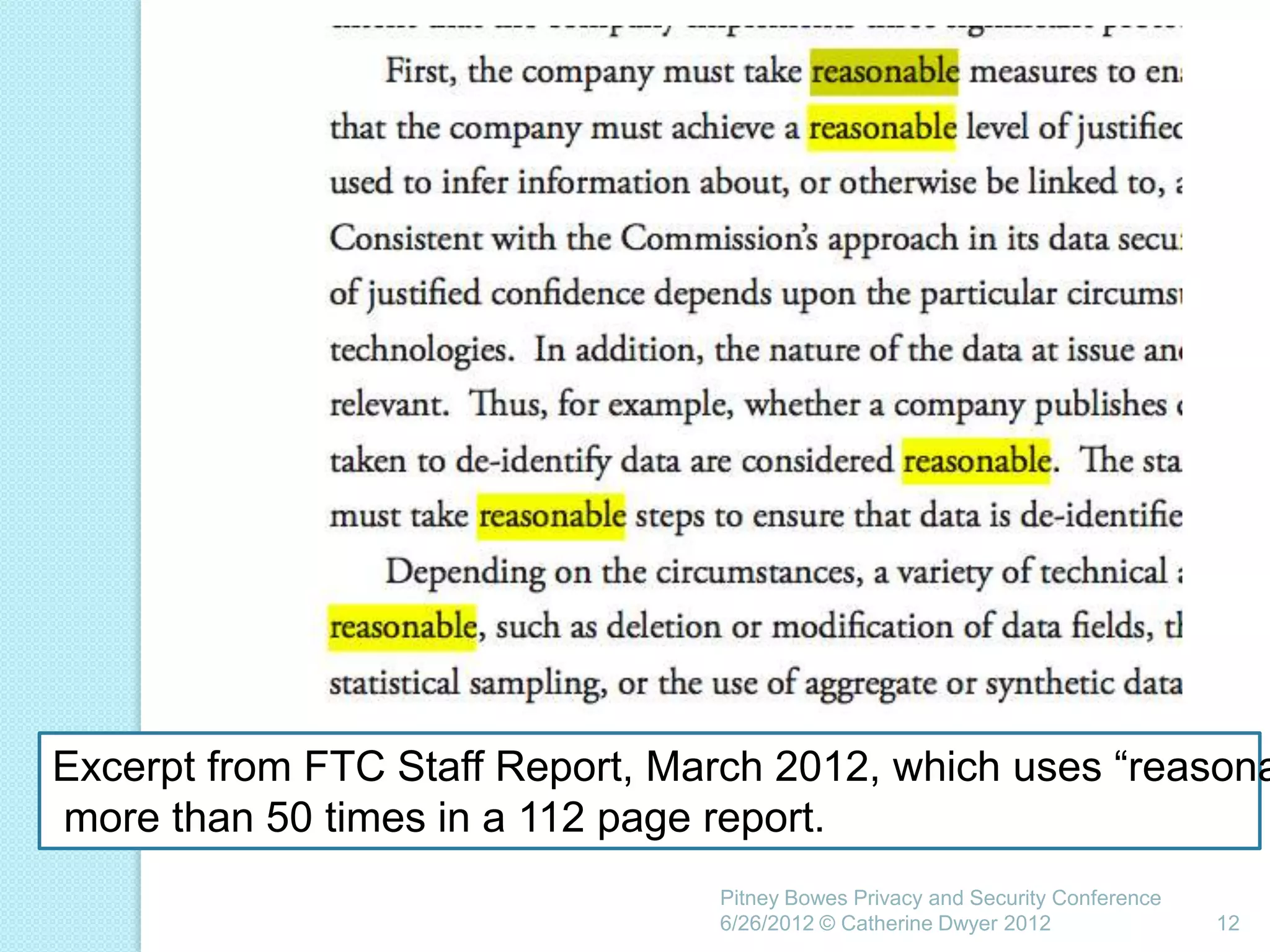
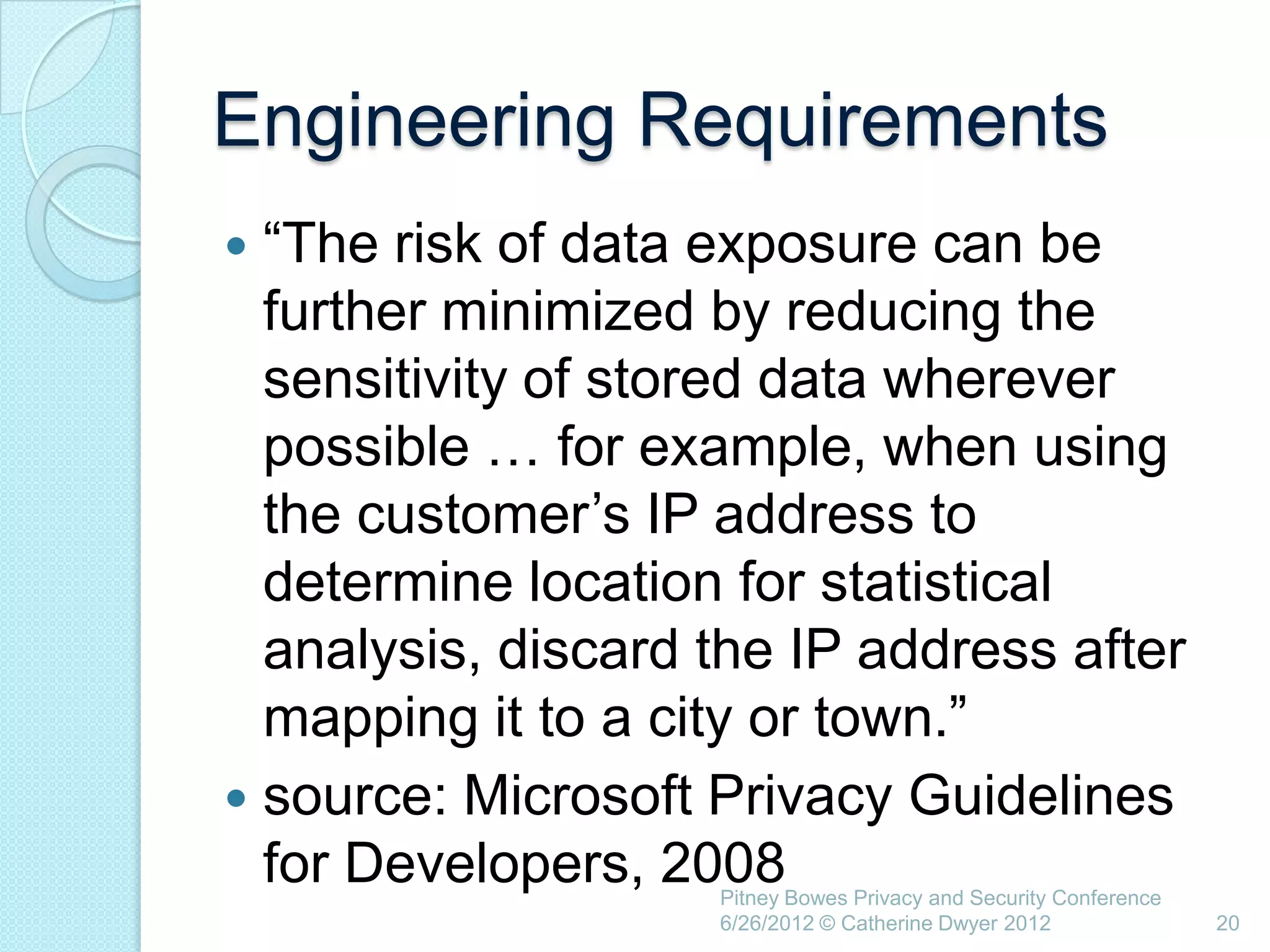
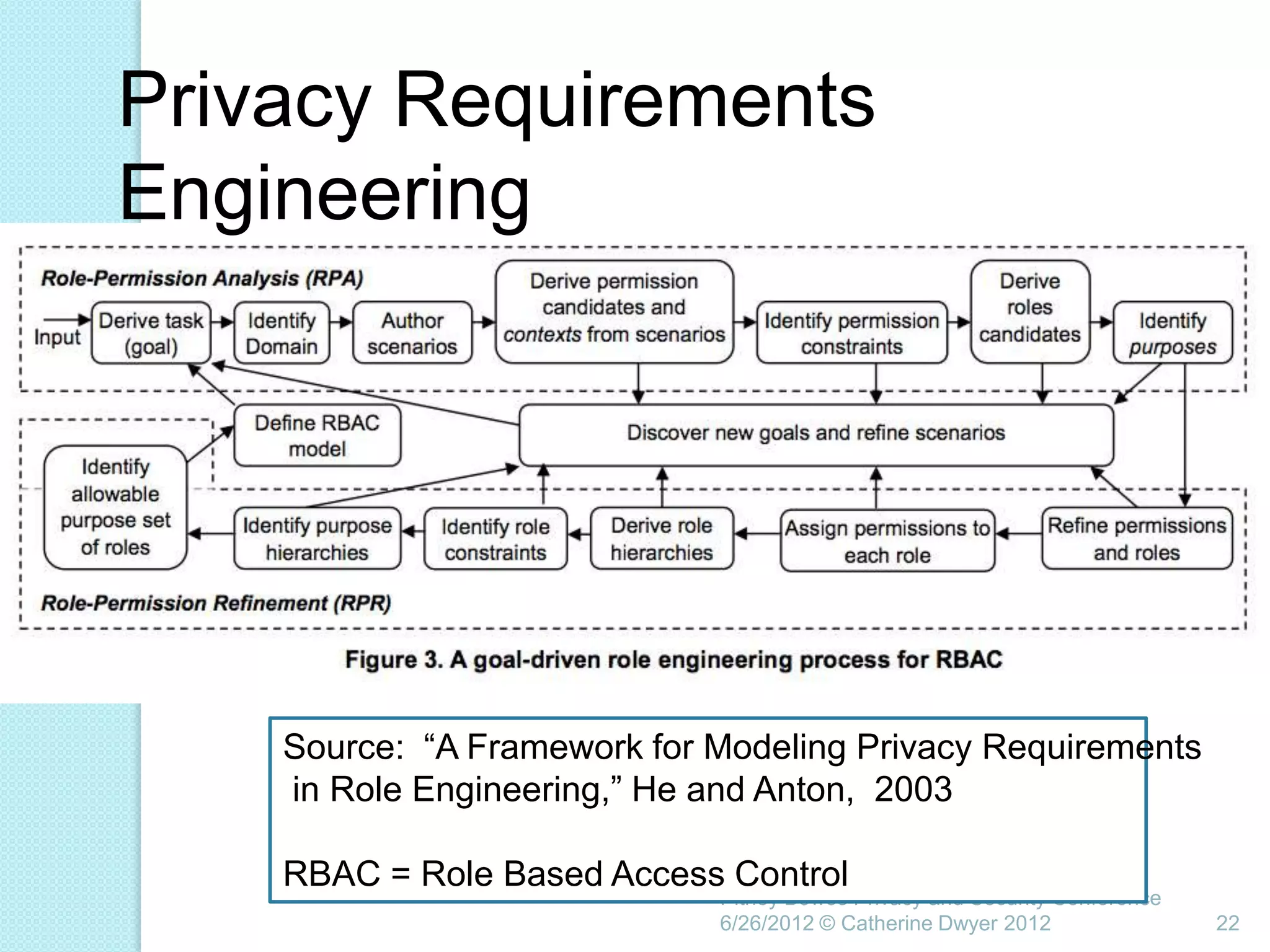
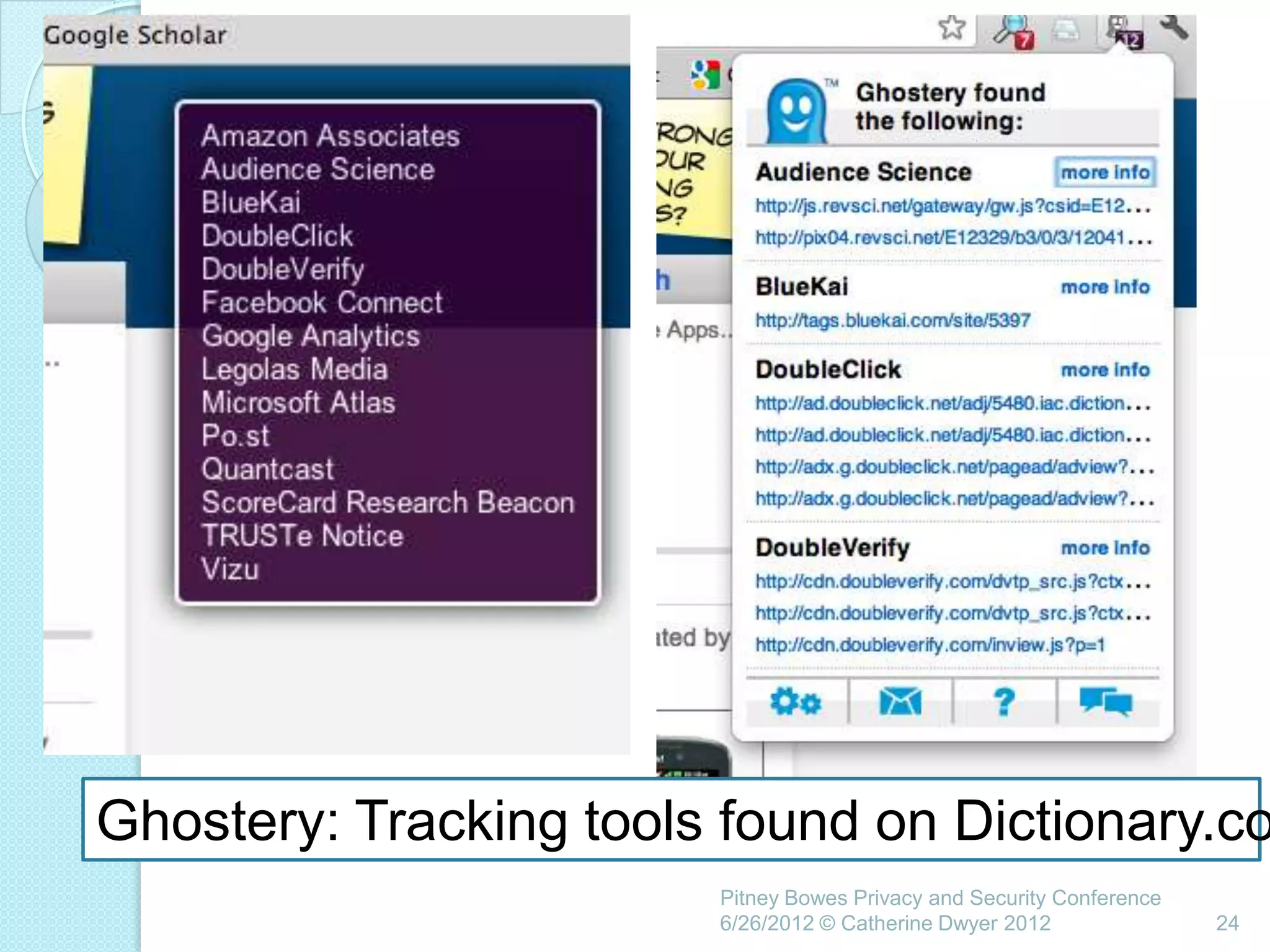
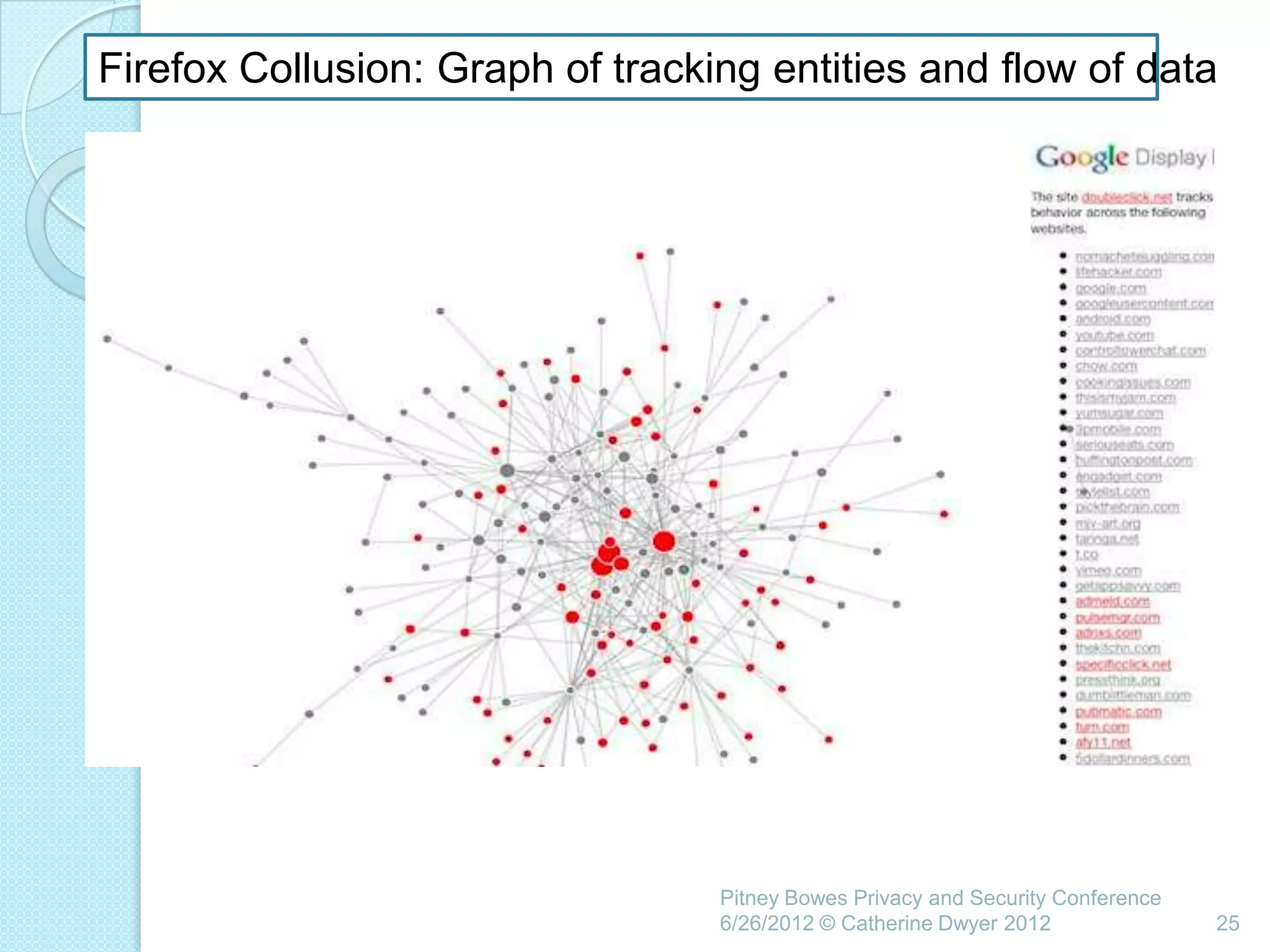
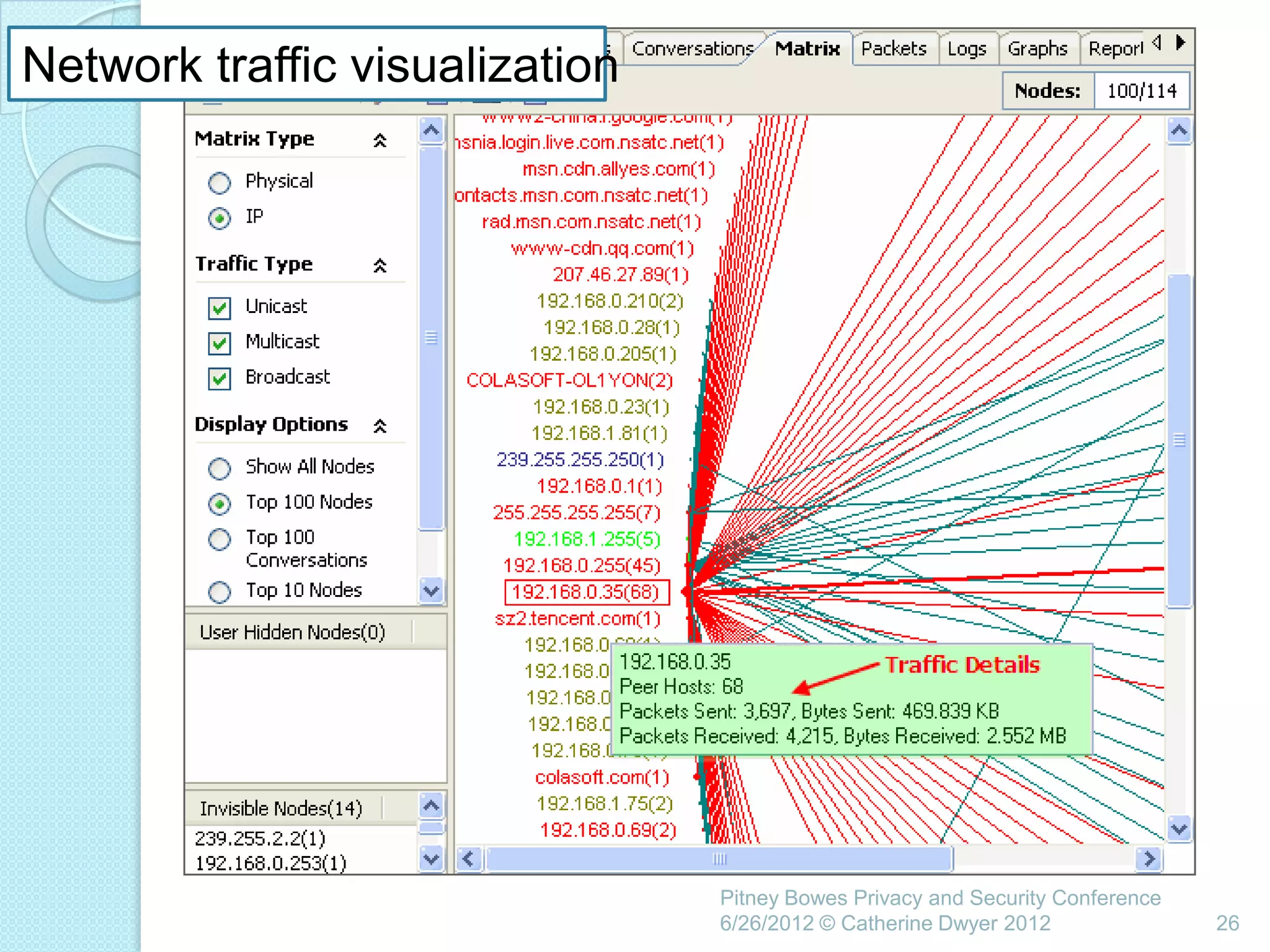
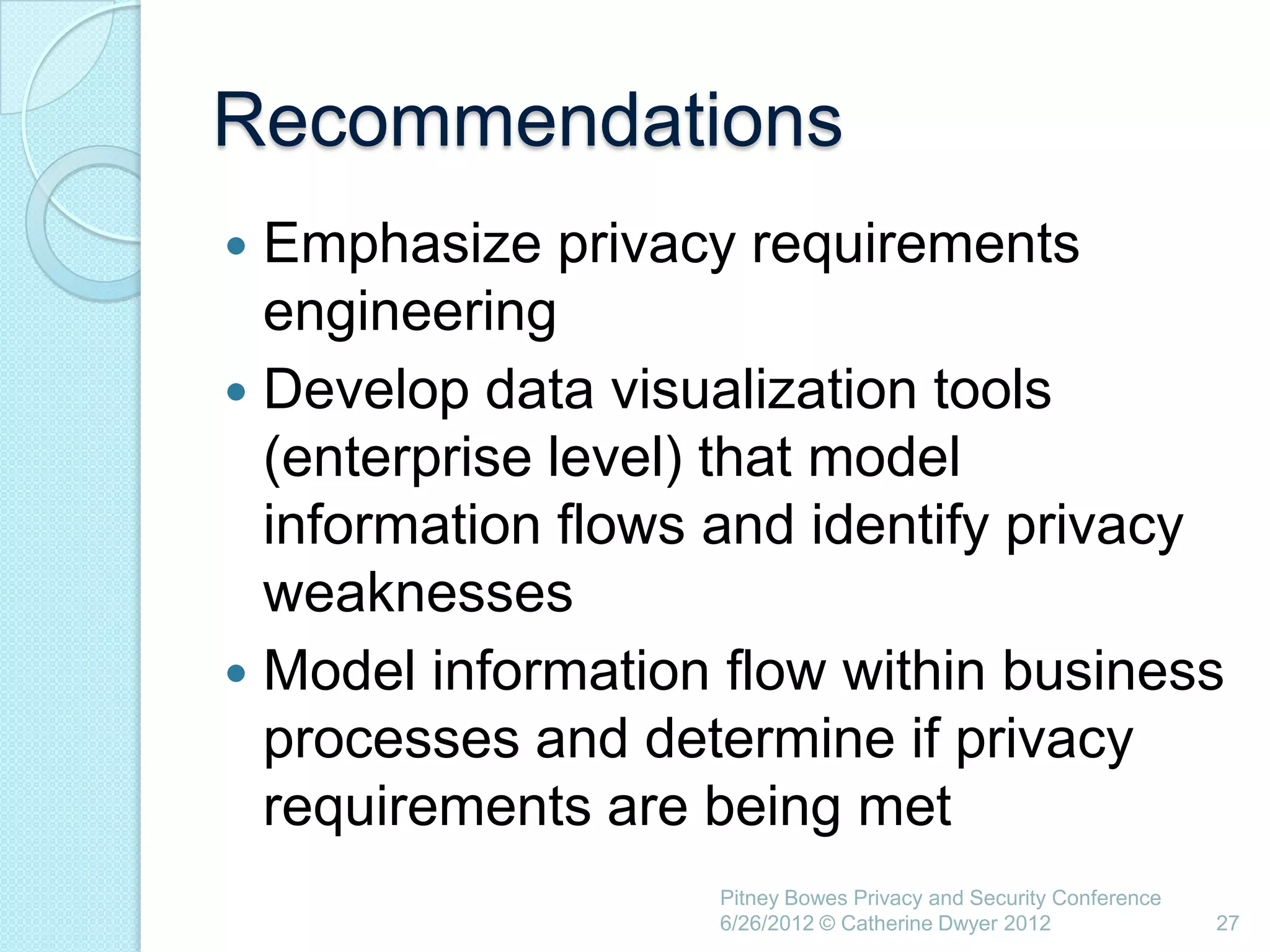
This document summarizes a presentation given by Catherine Dwyer at the Pitney Bowes Privacy and Security Conference on June 26, 2012. The presentation discusses the concept of "Privacy by Design" and argues that it needs to evolve into "Privacy Requirements Engineering" in order to make privacy objectives more tangible and measurable. Specifically, Dwyer recommends emphasizing privacy requirements engineering, developing data visualization tools to model information flows, and determining if privacy requirements are being met within business processes.