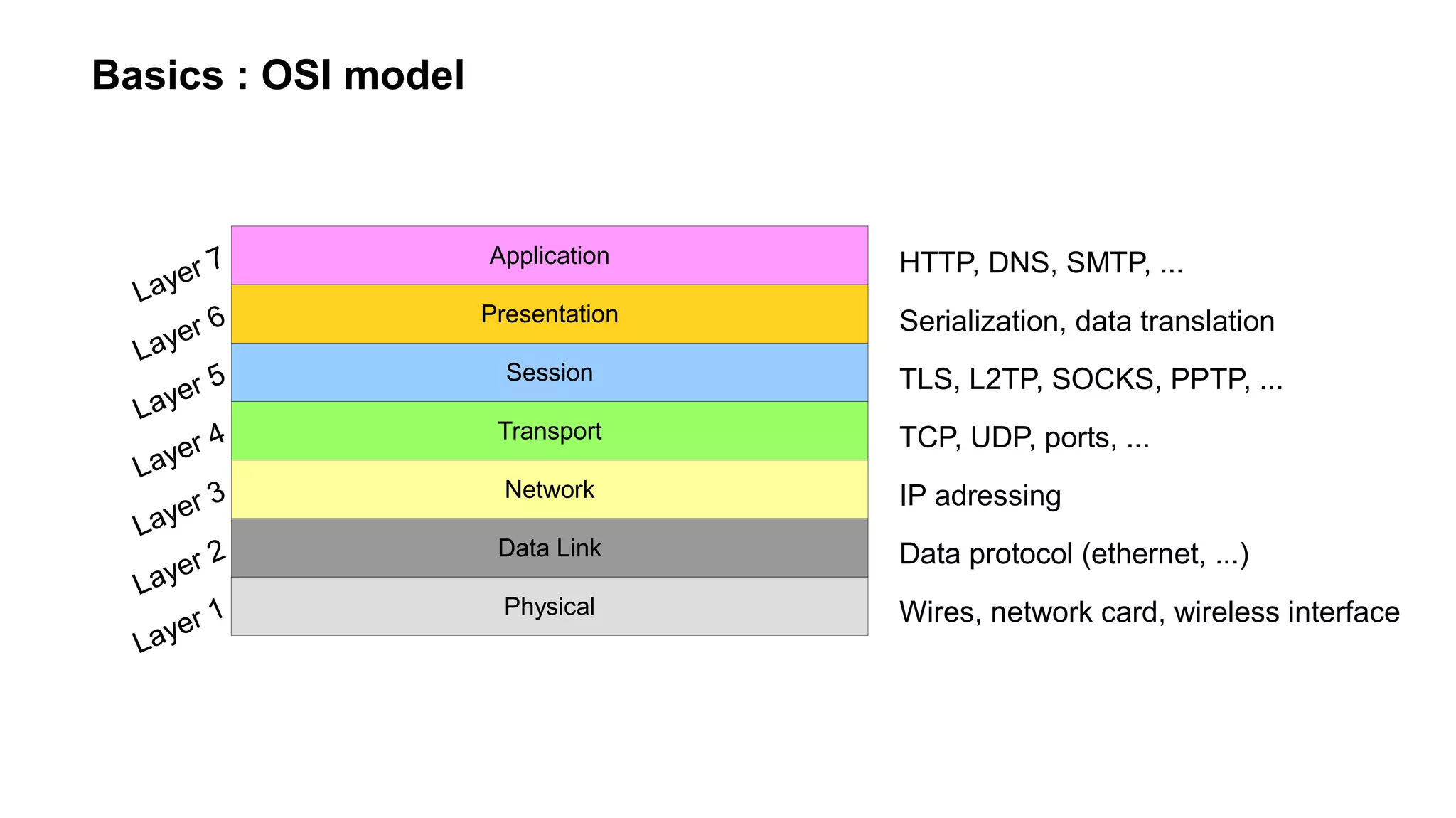
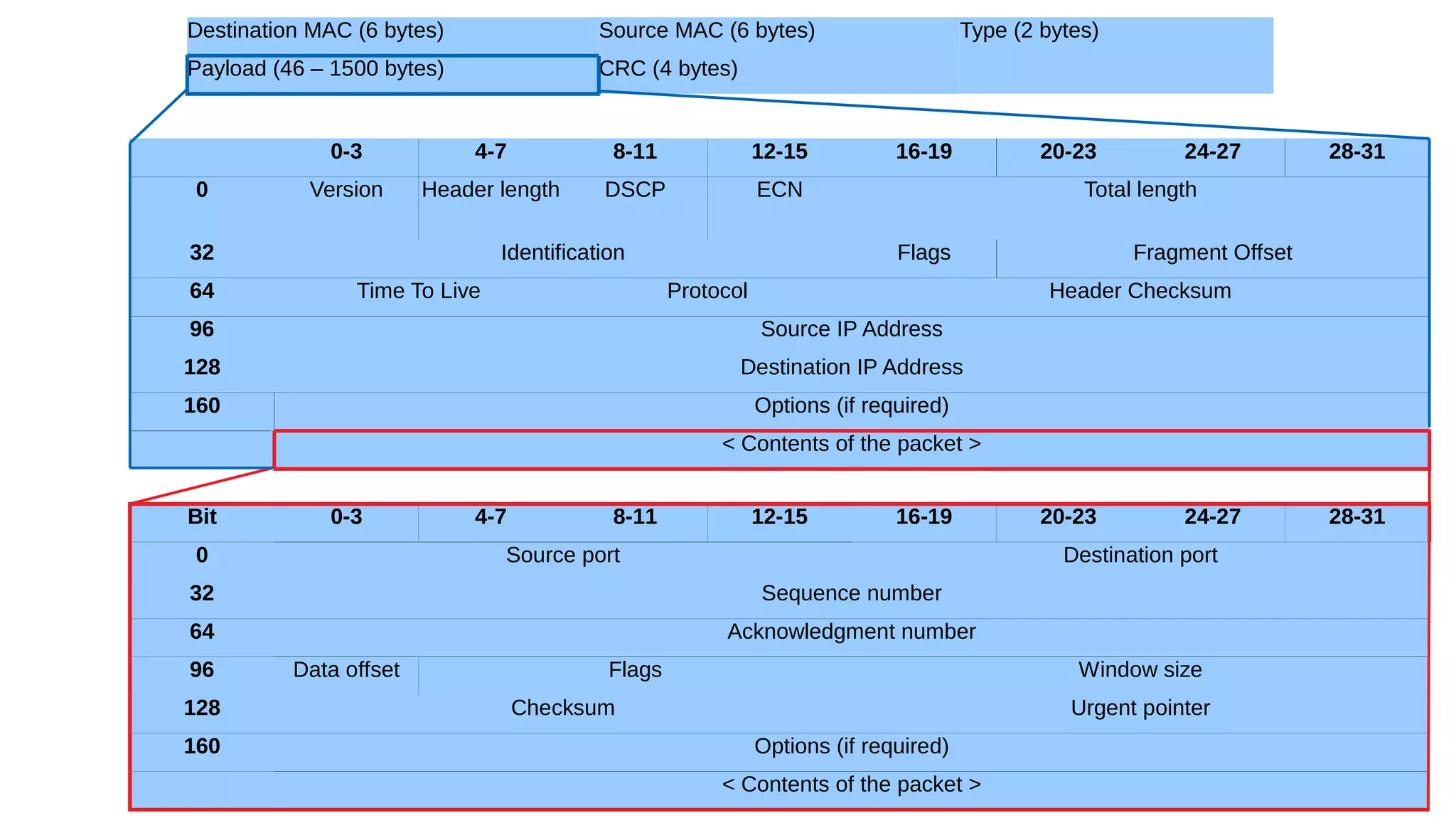
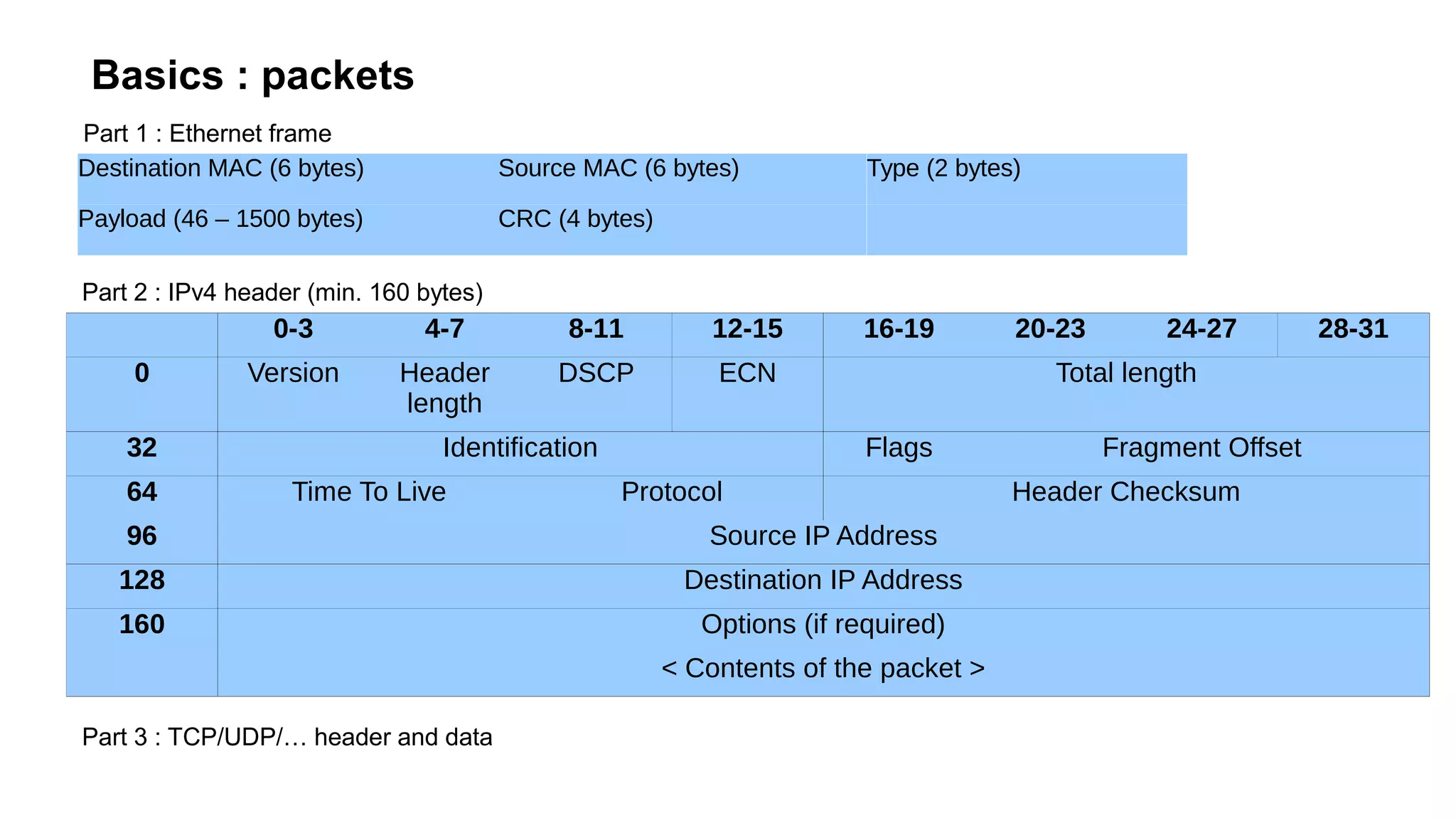
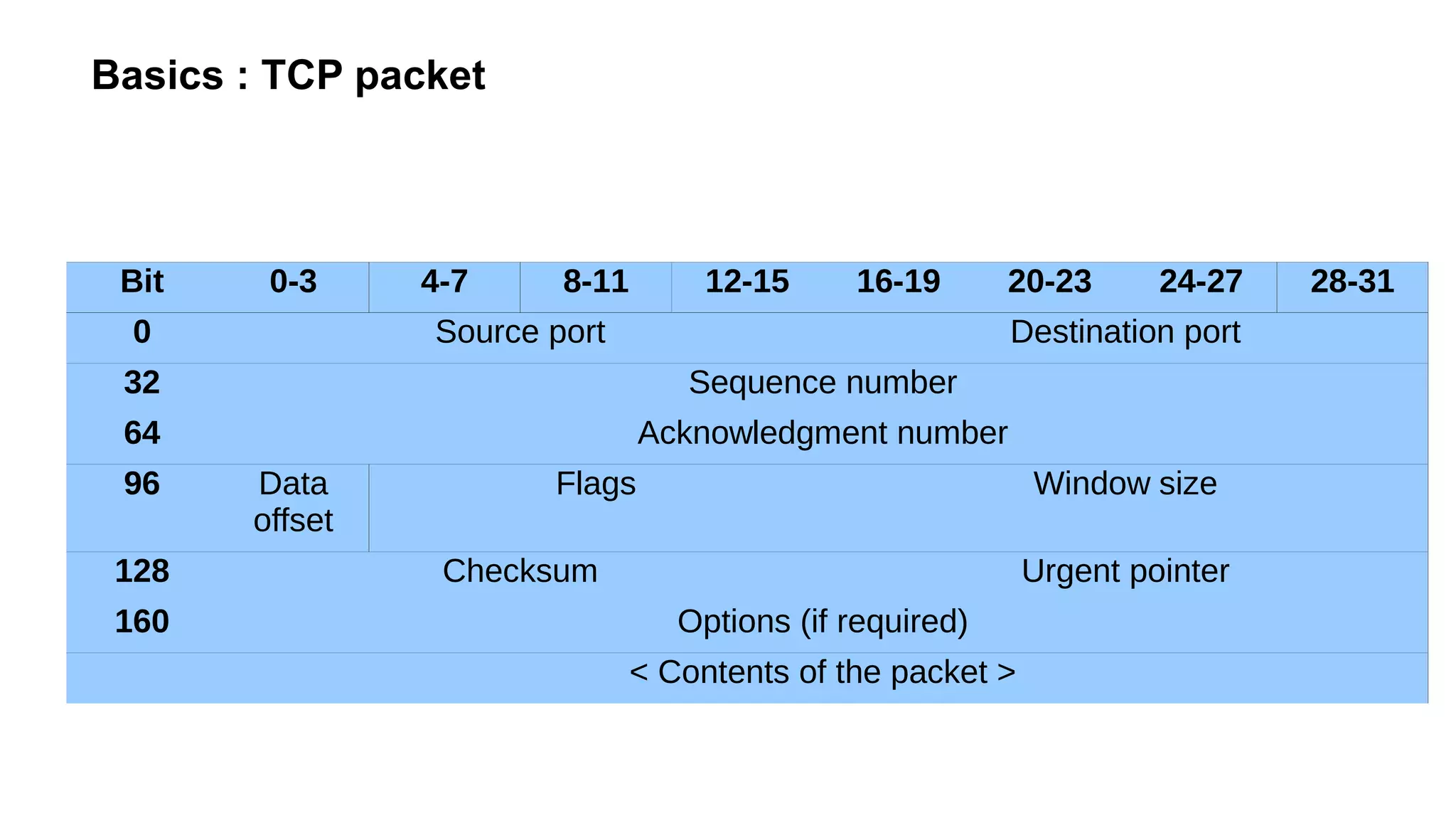
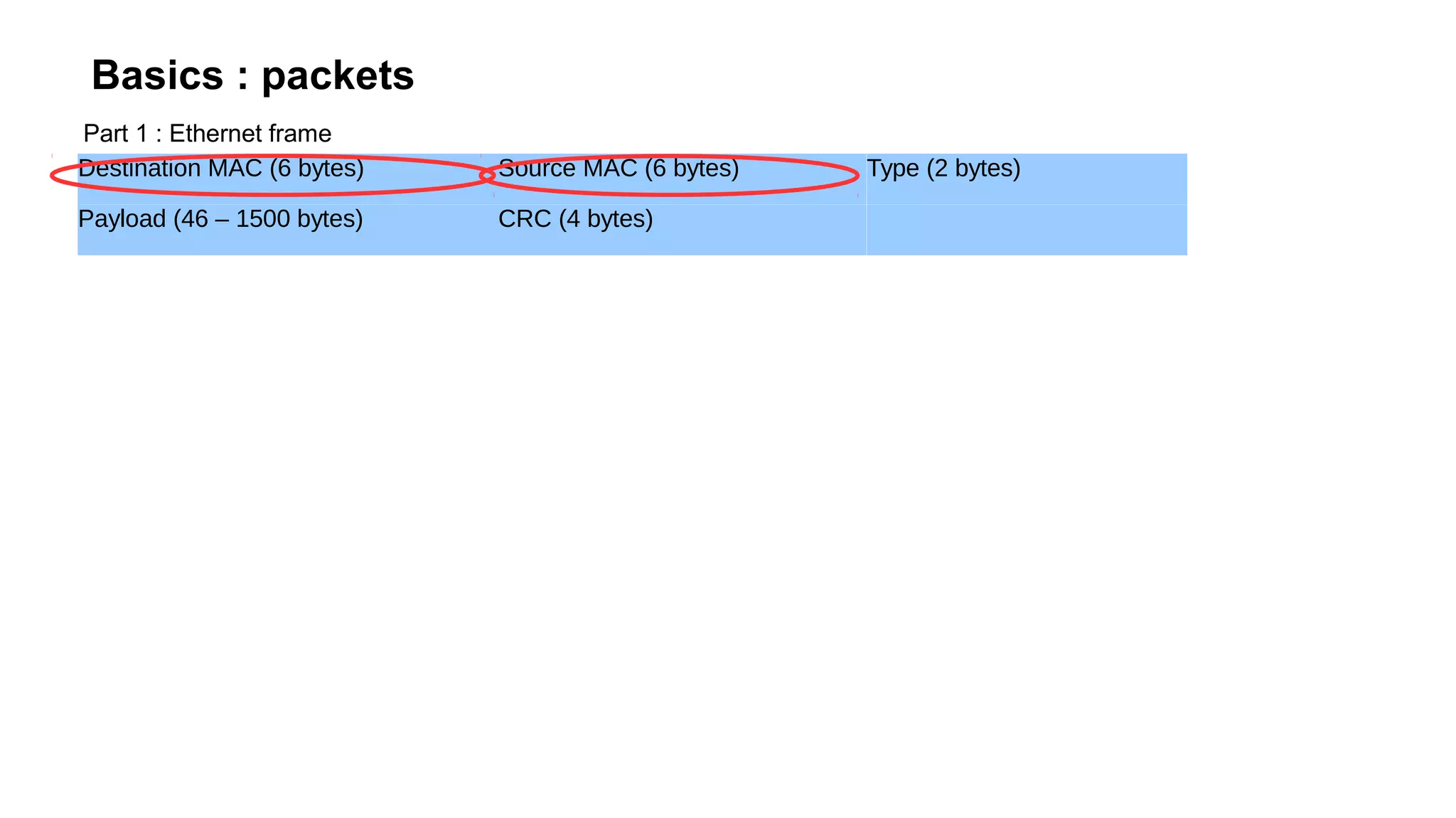
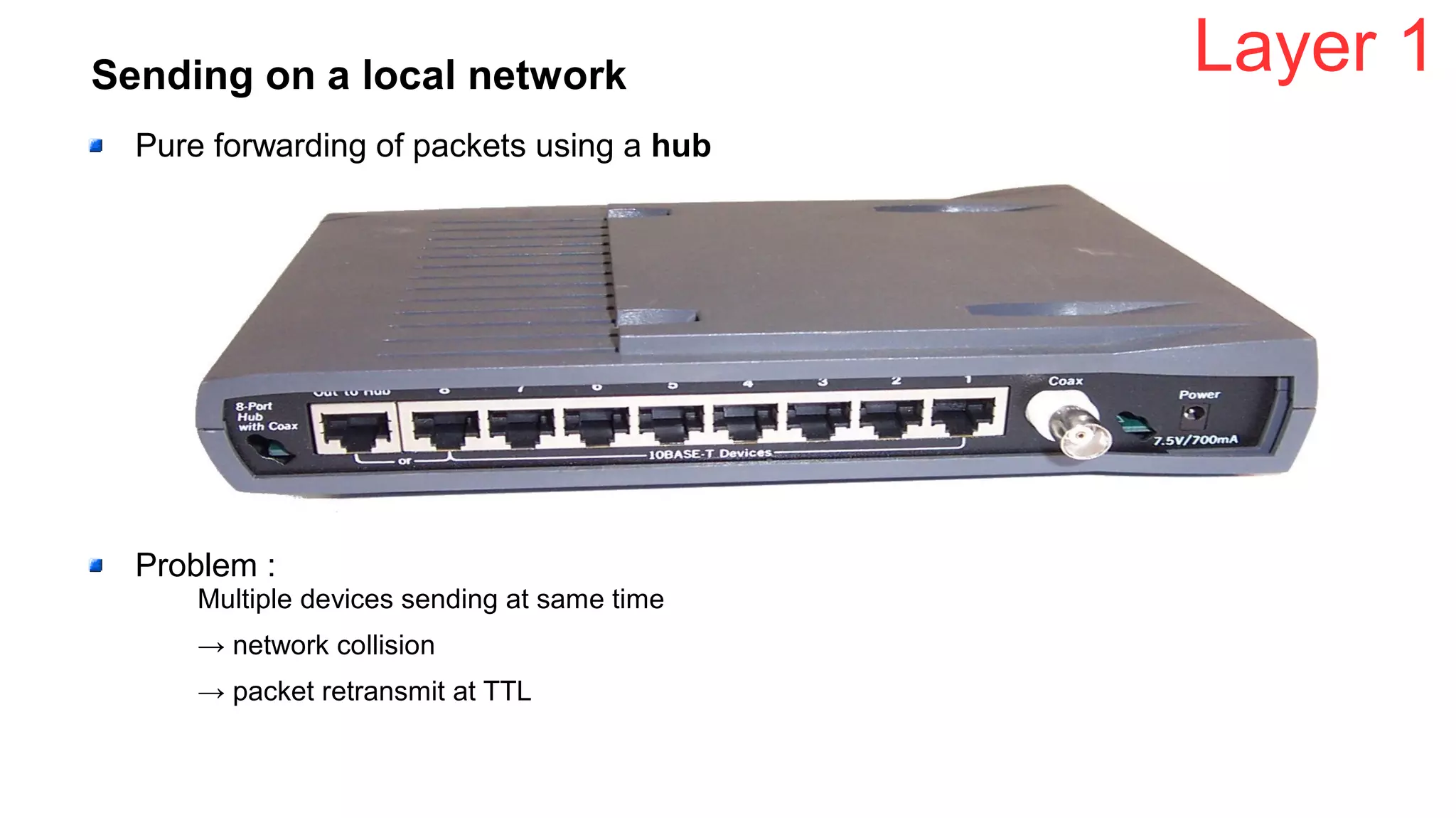
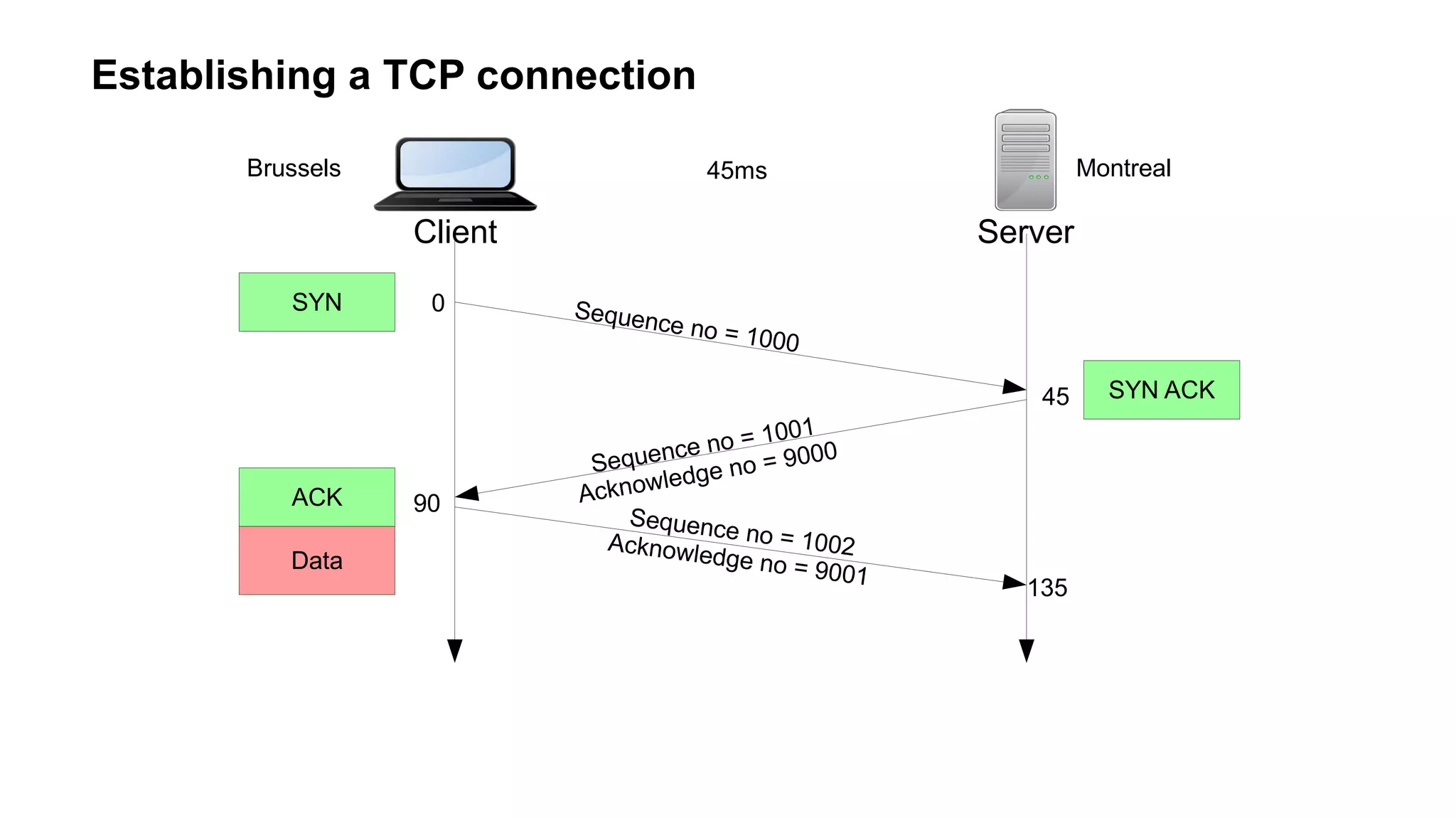
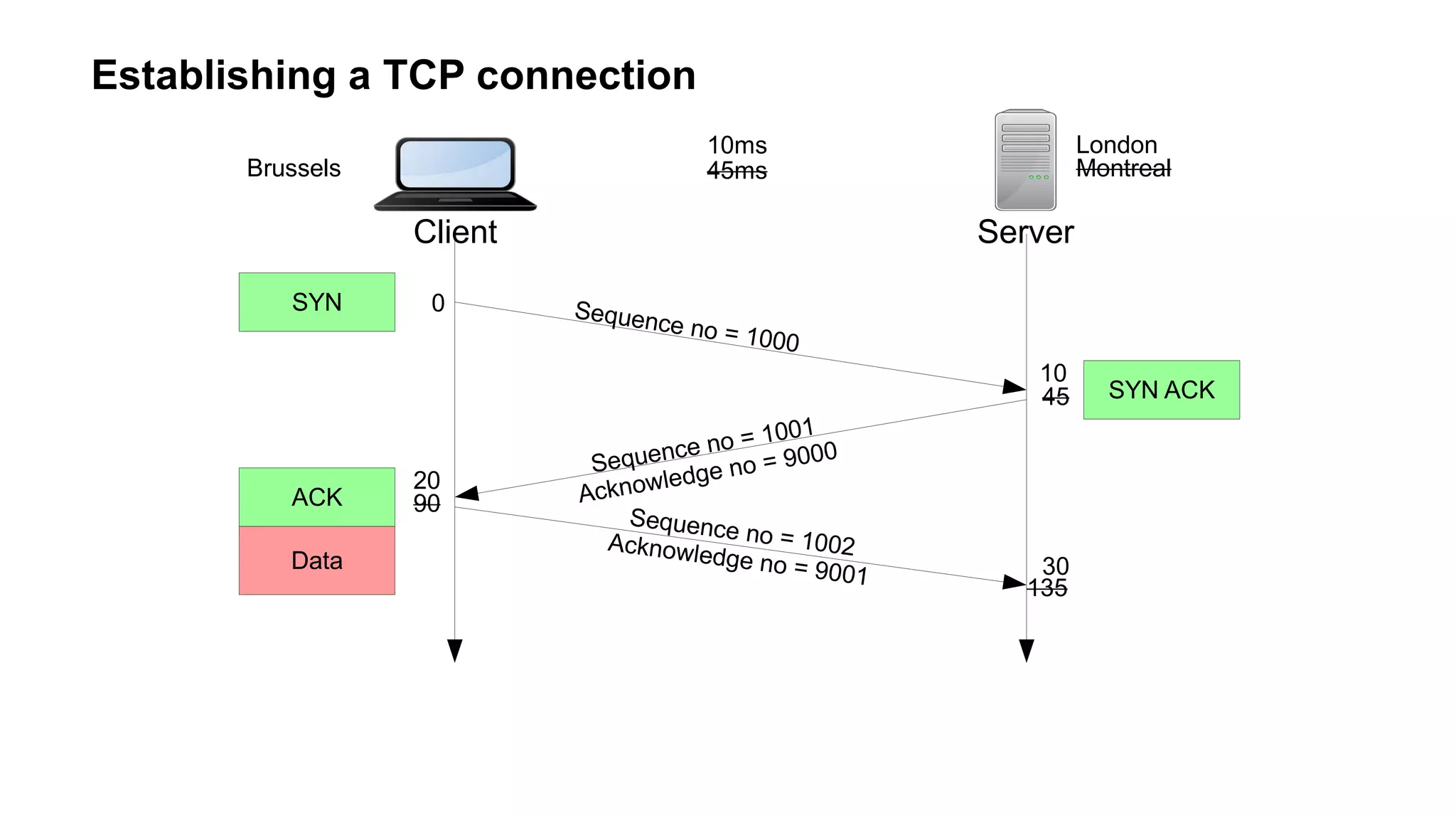
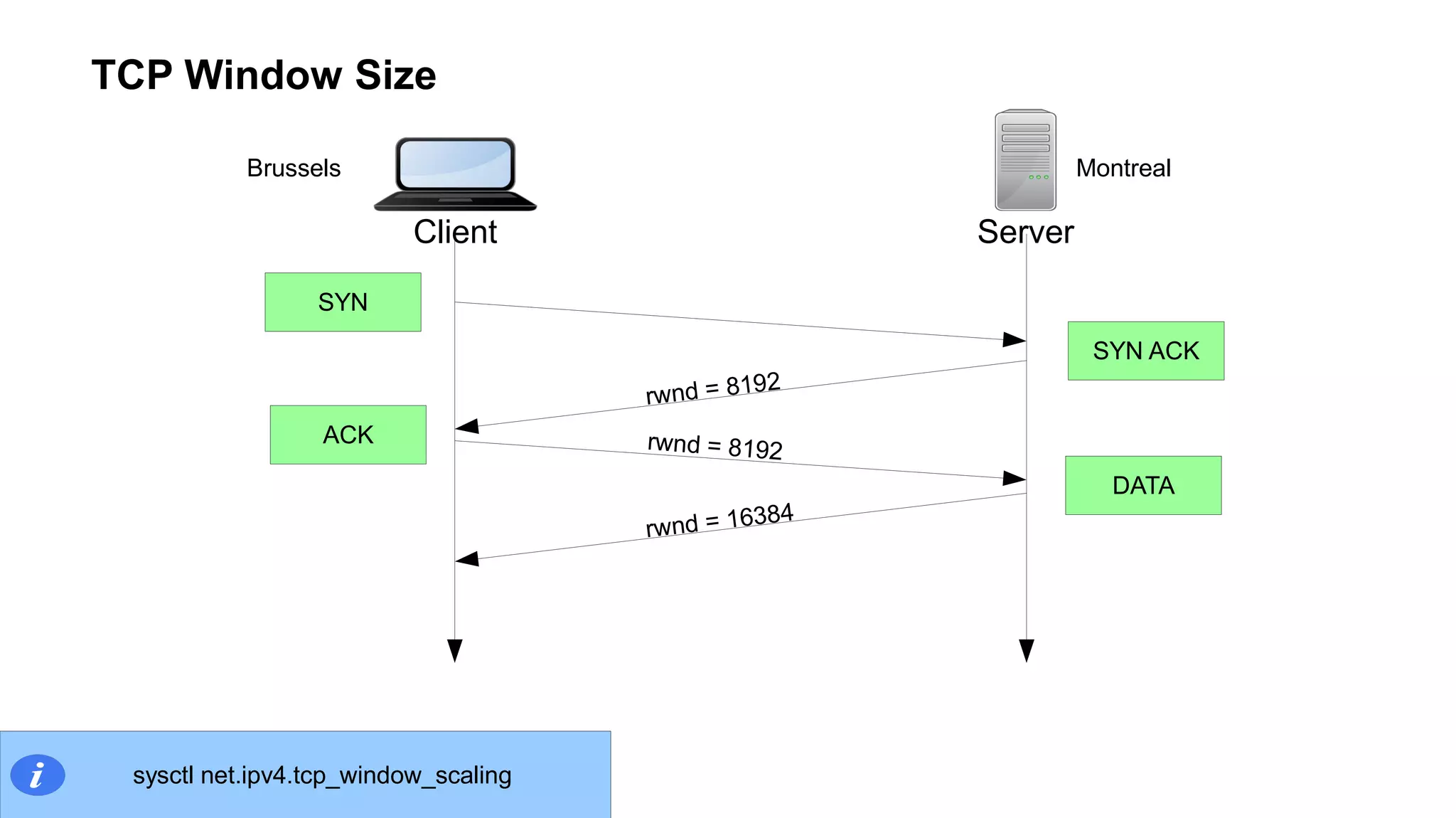
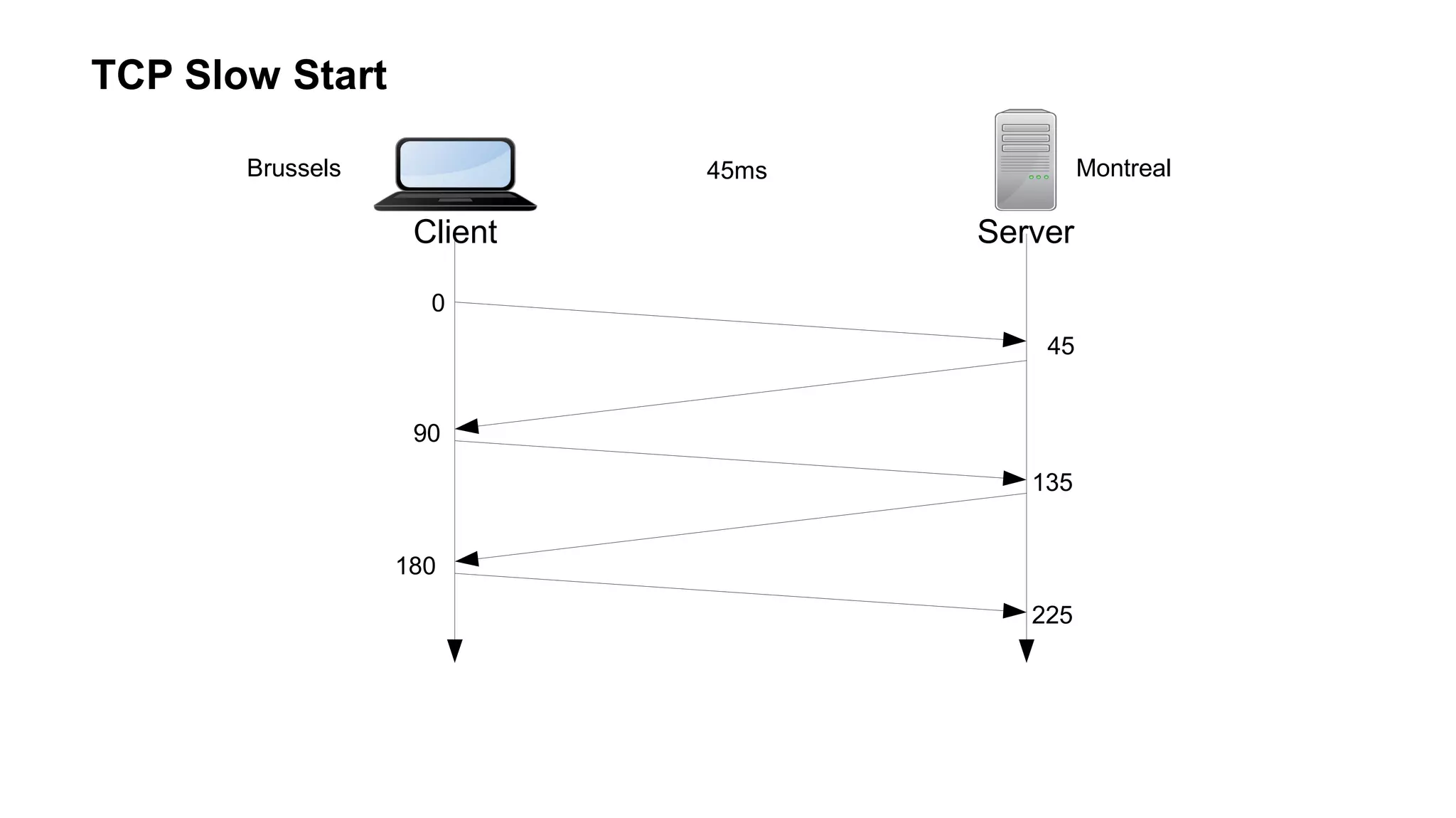
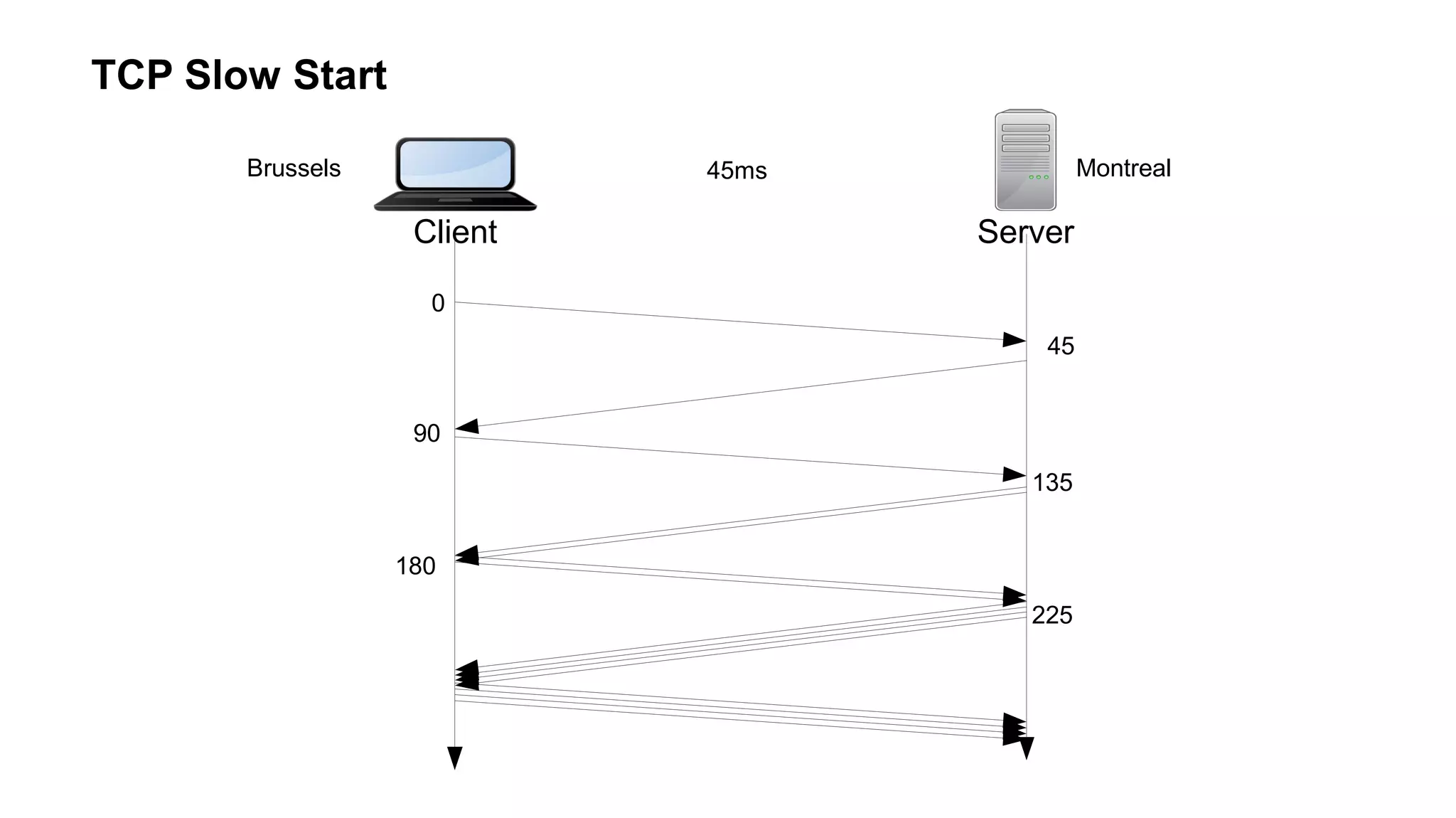
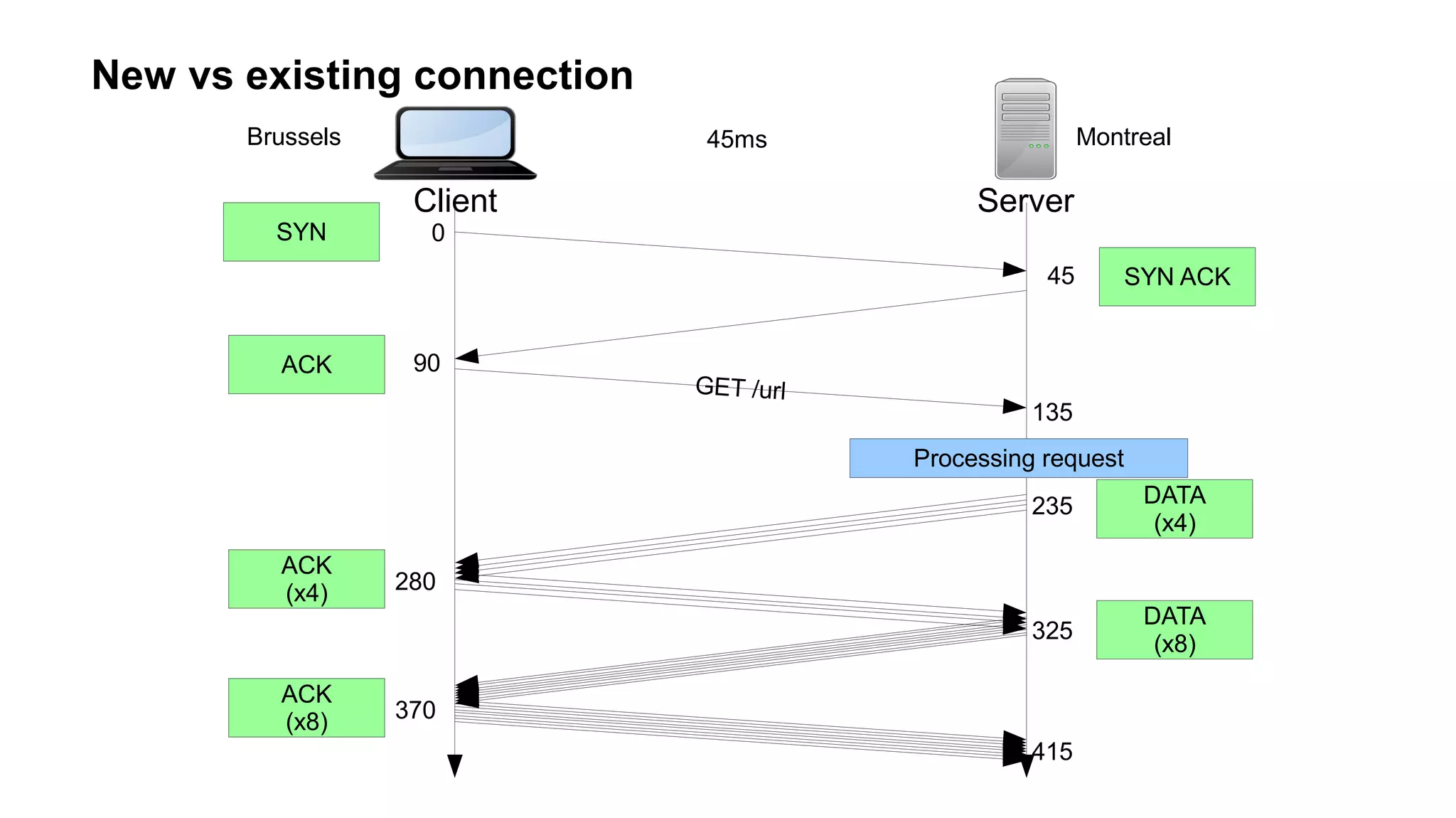
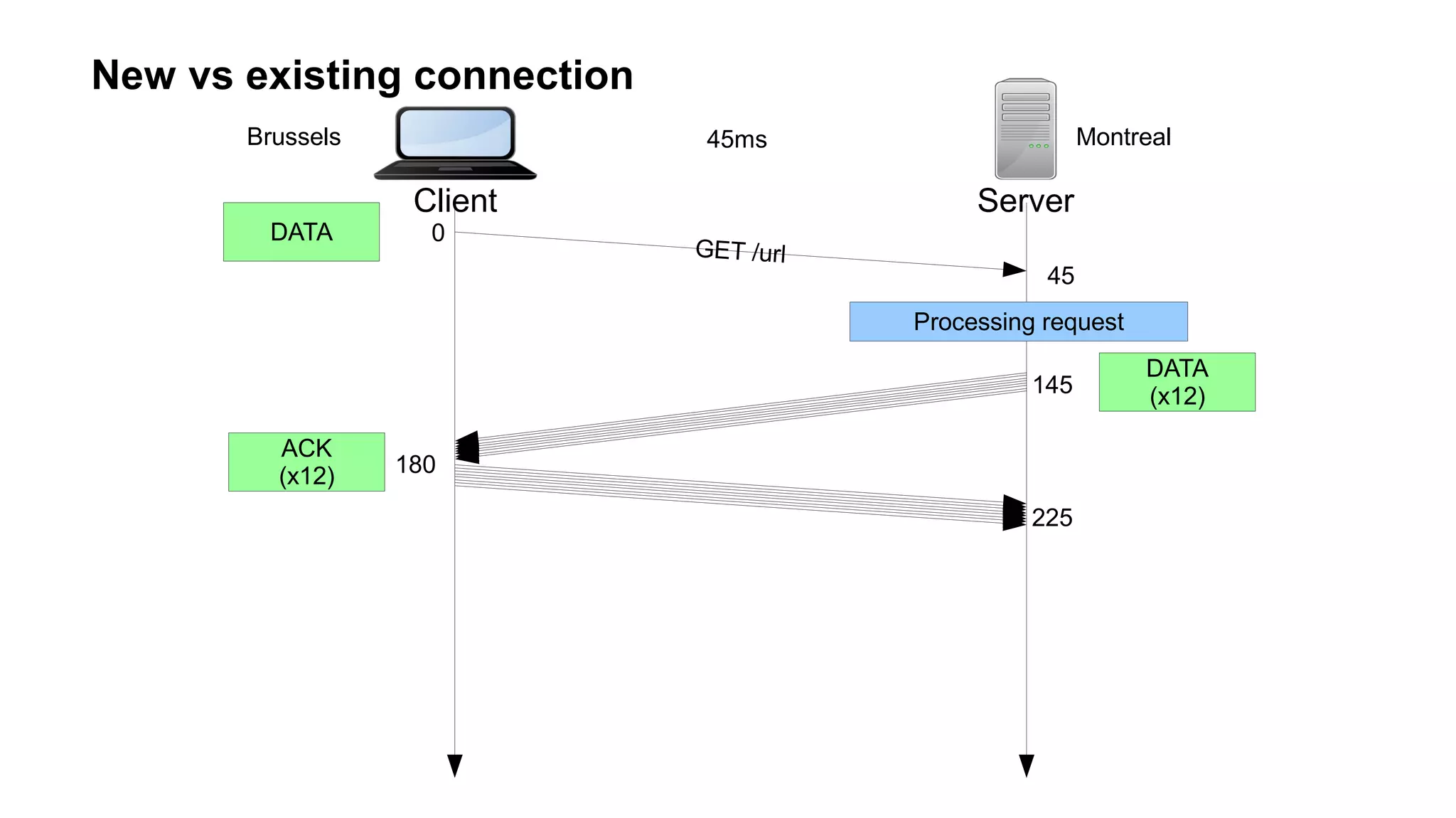
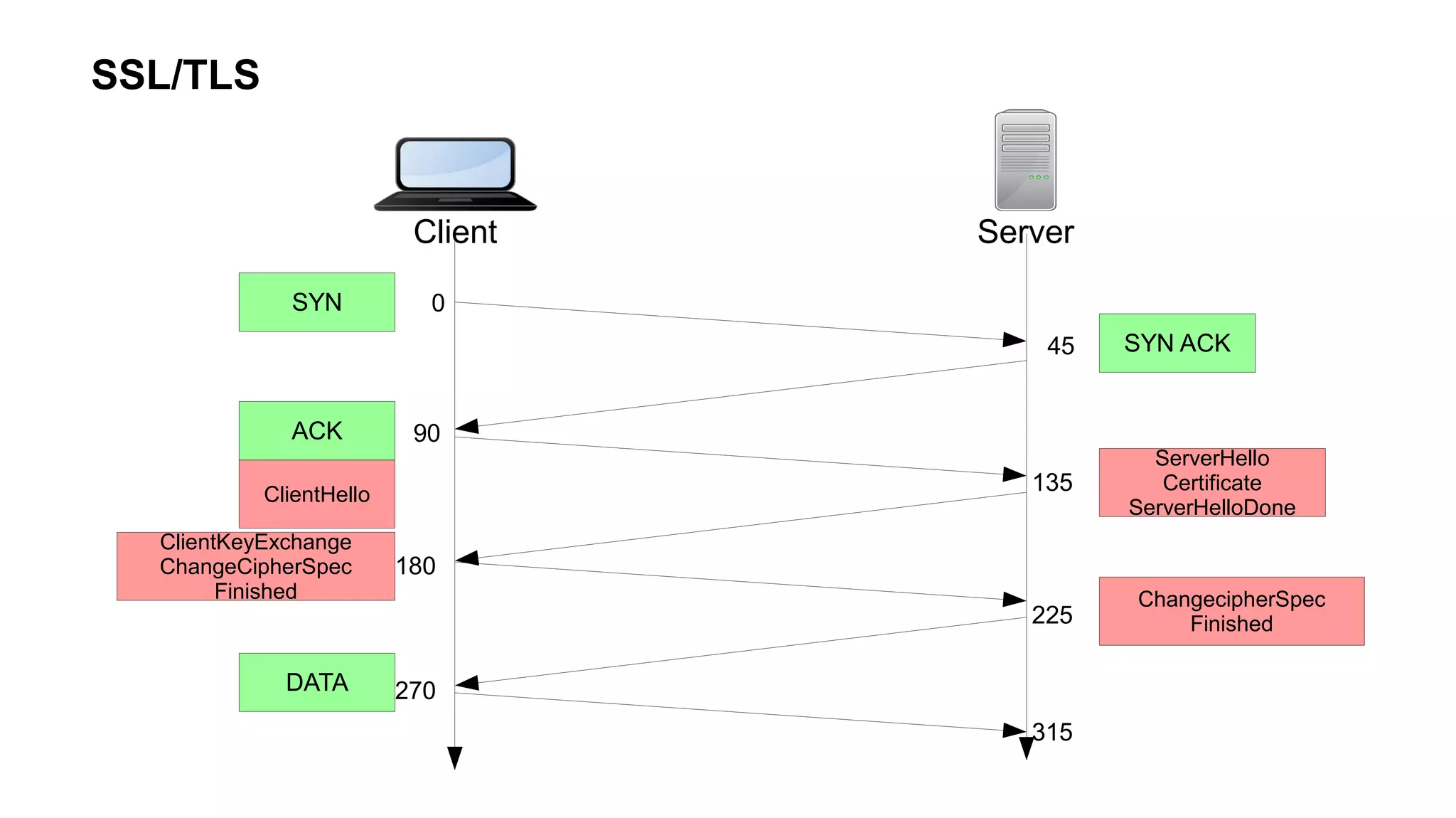
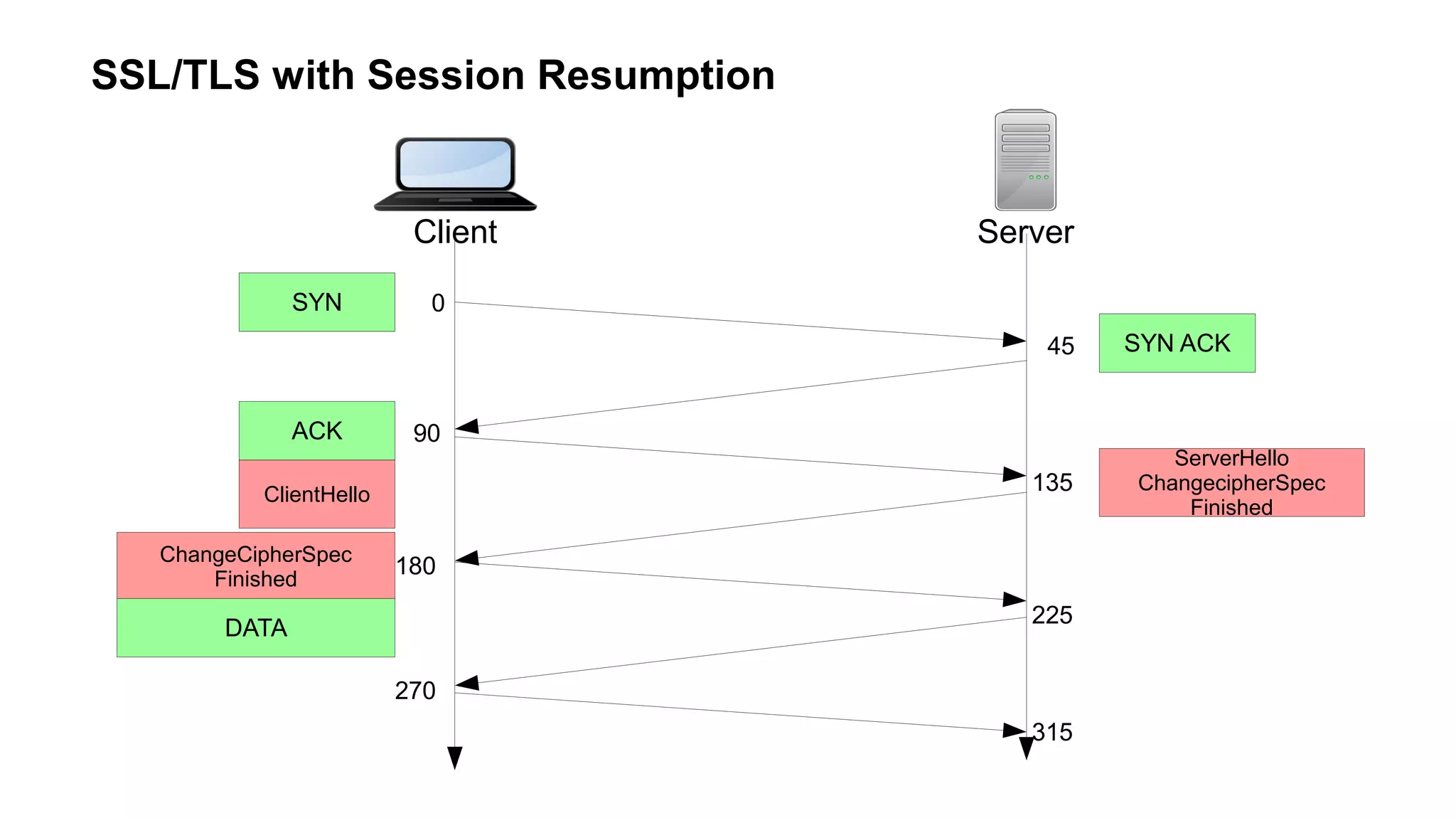
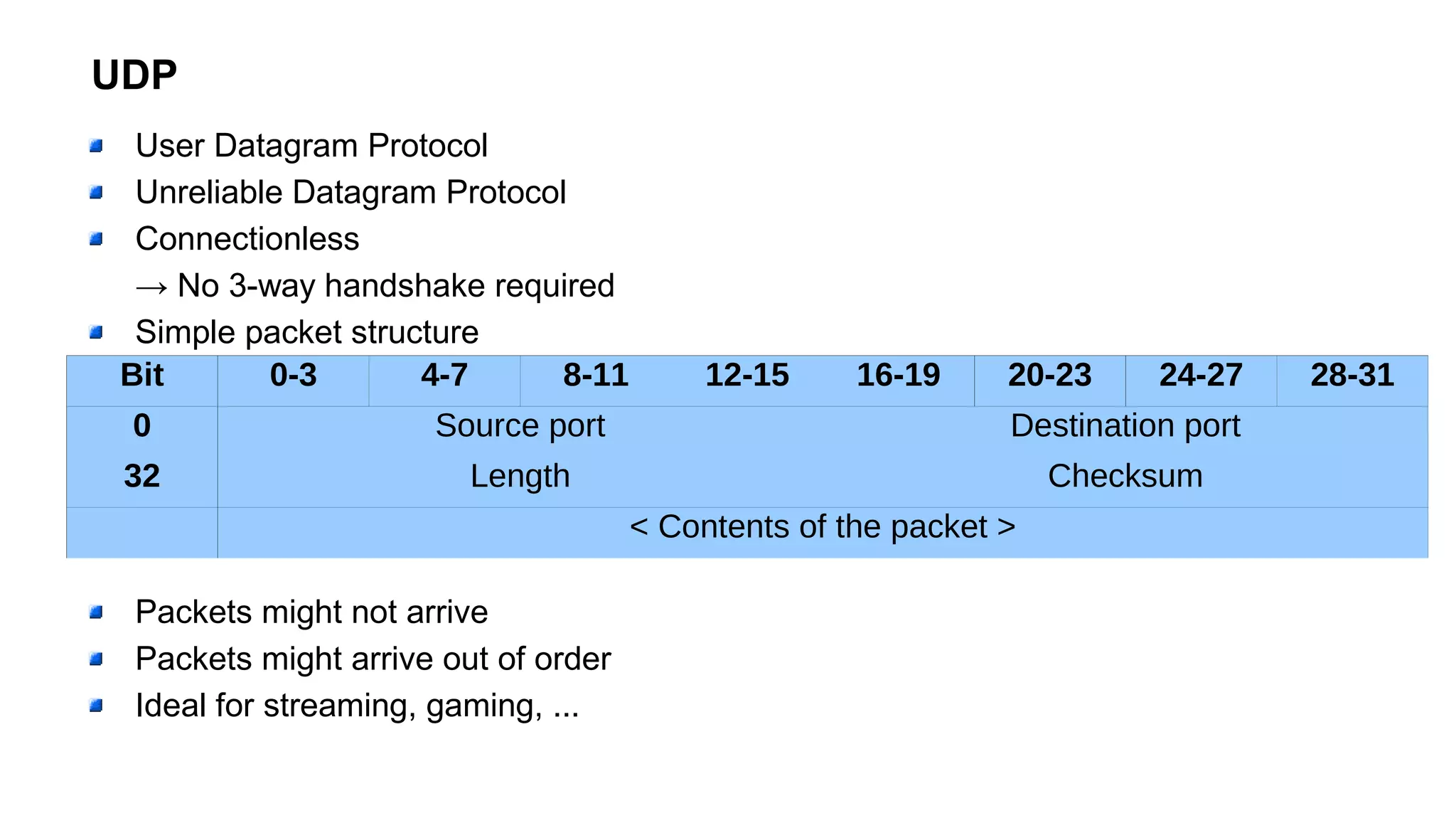
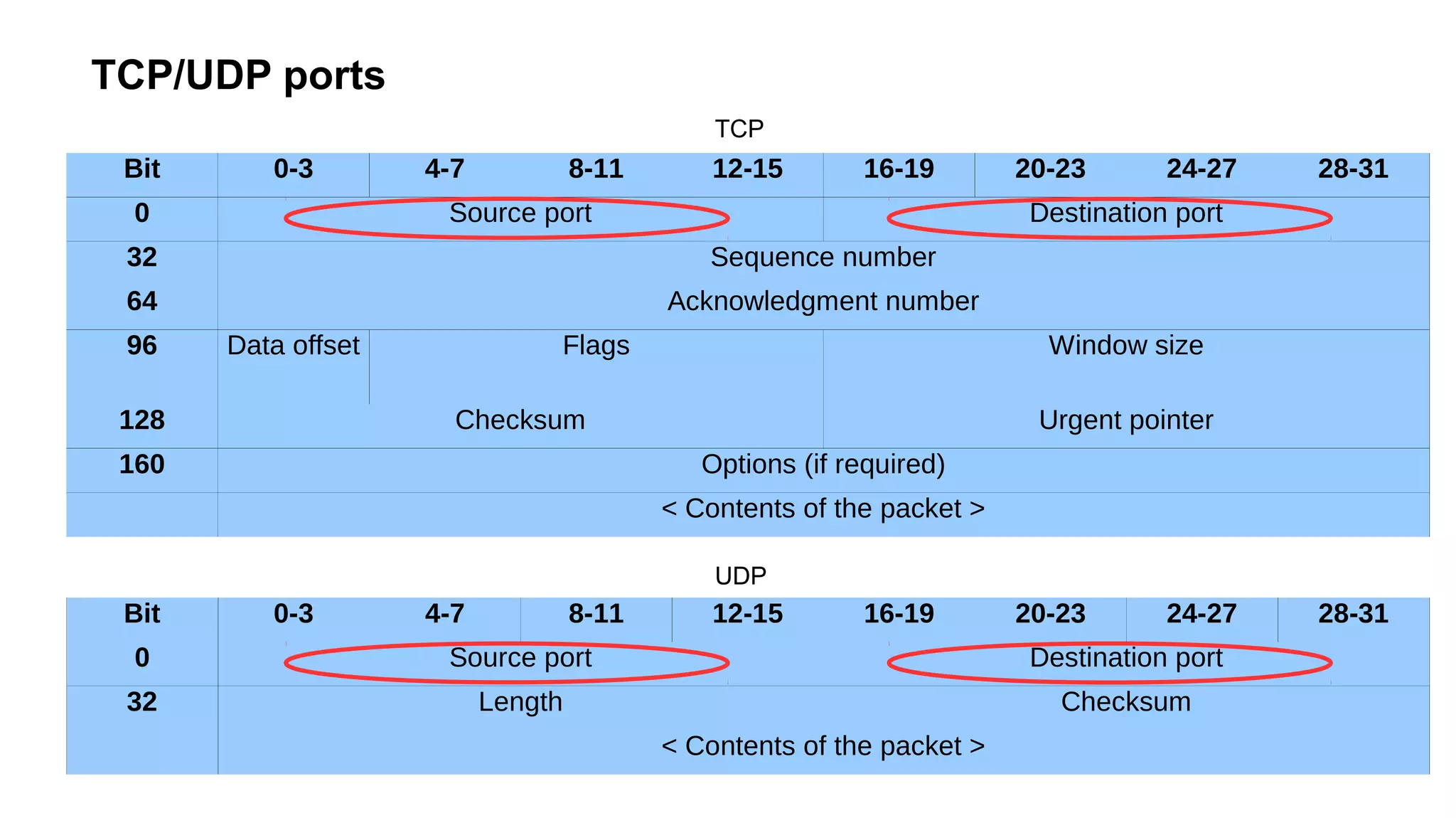
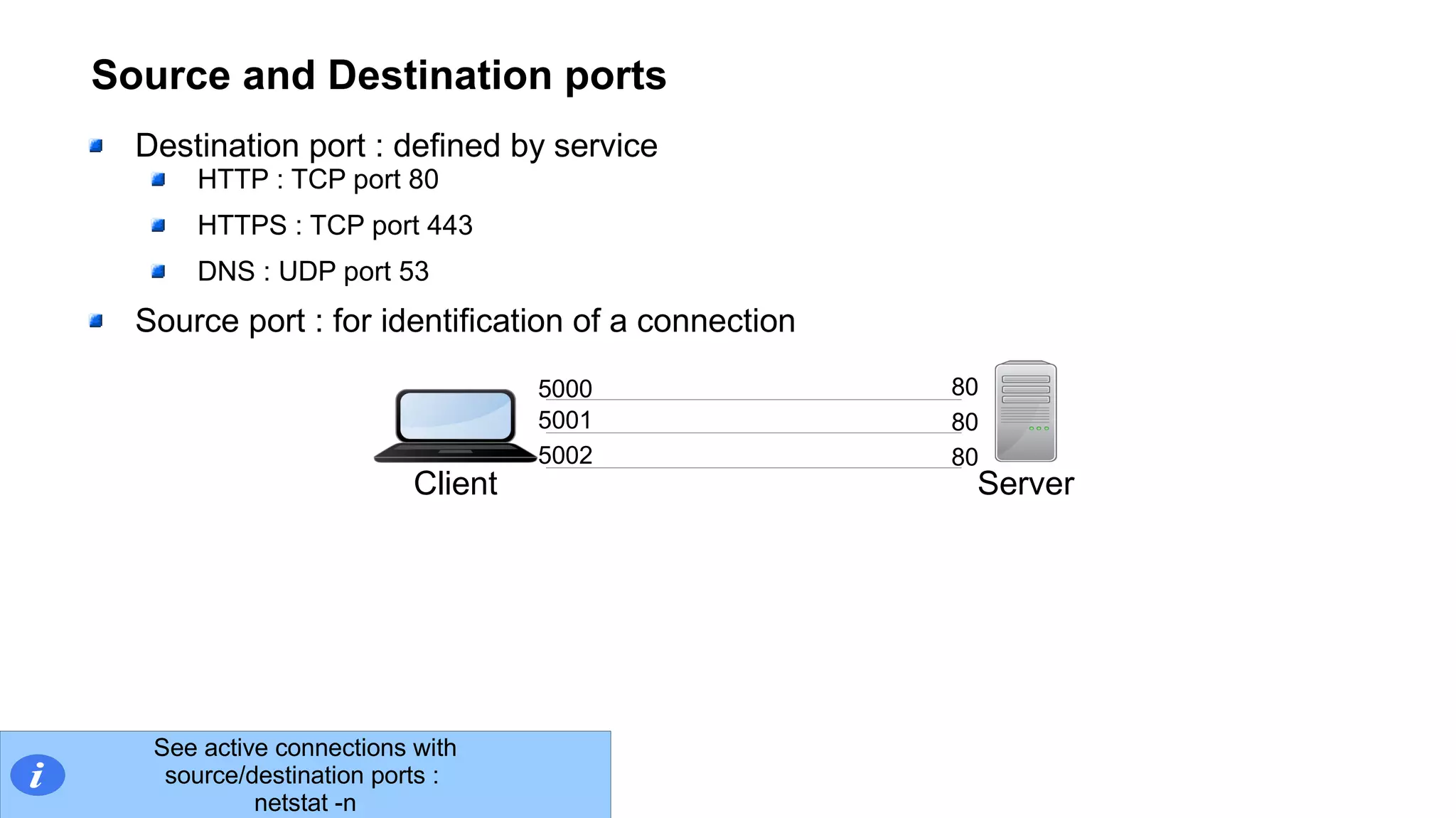
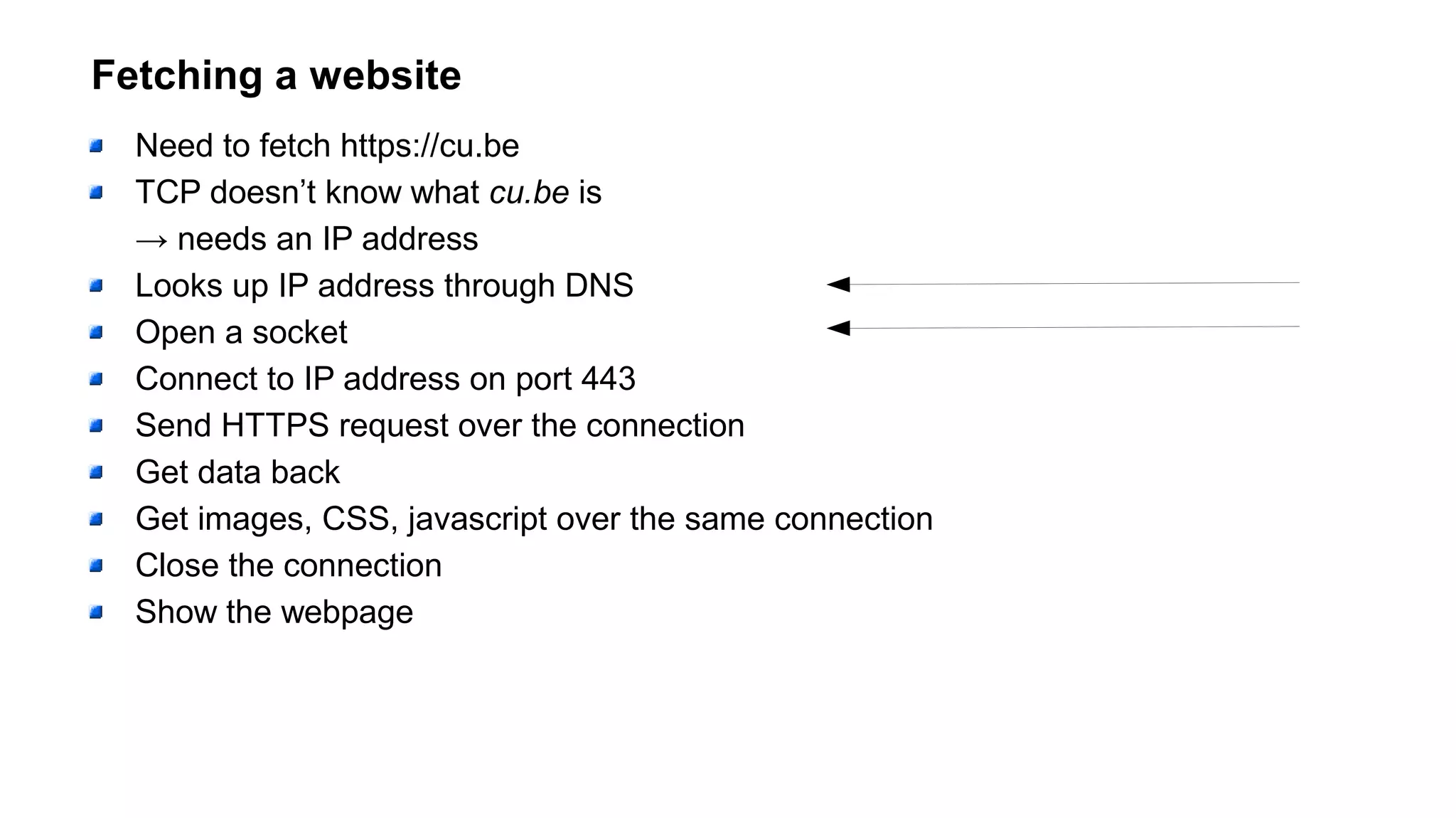
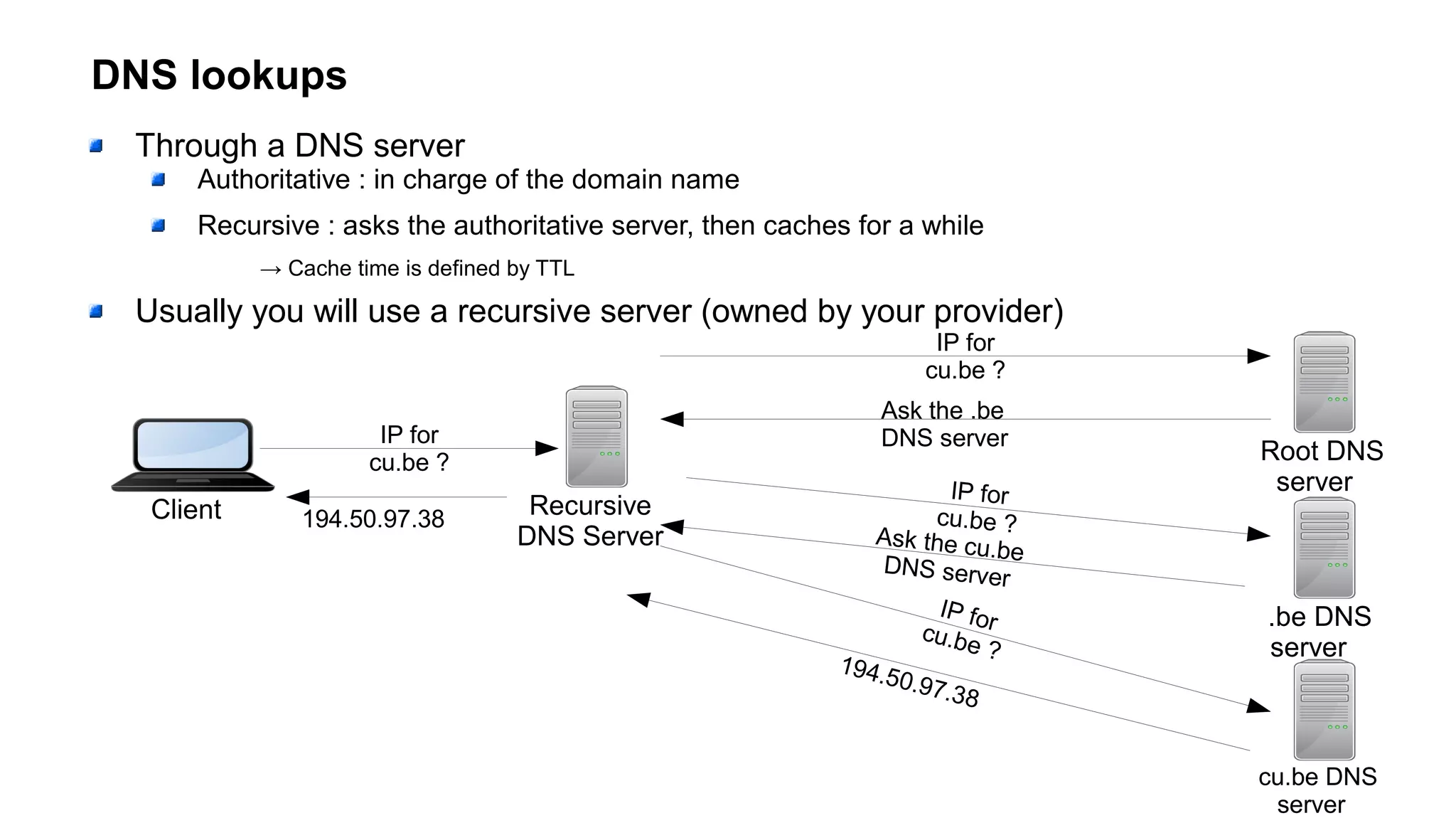
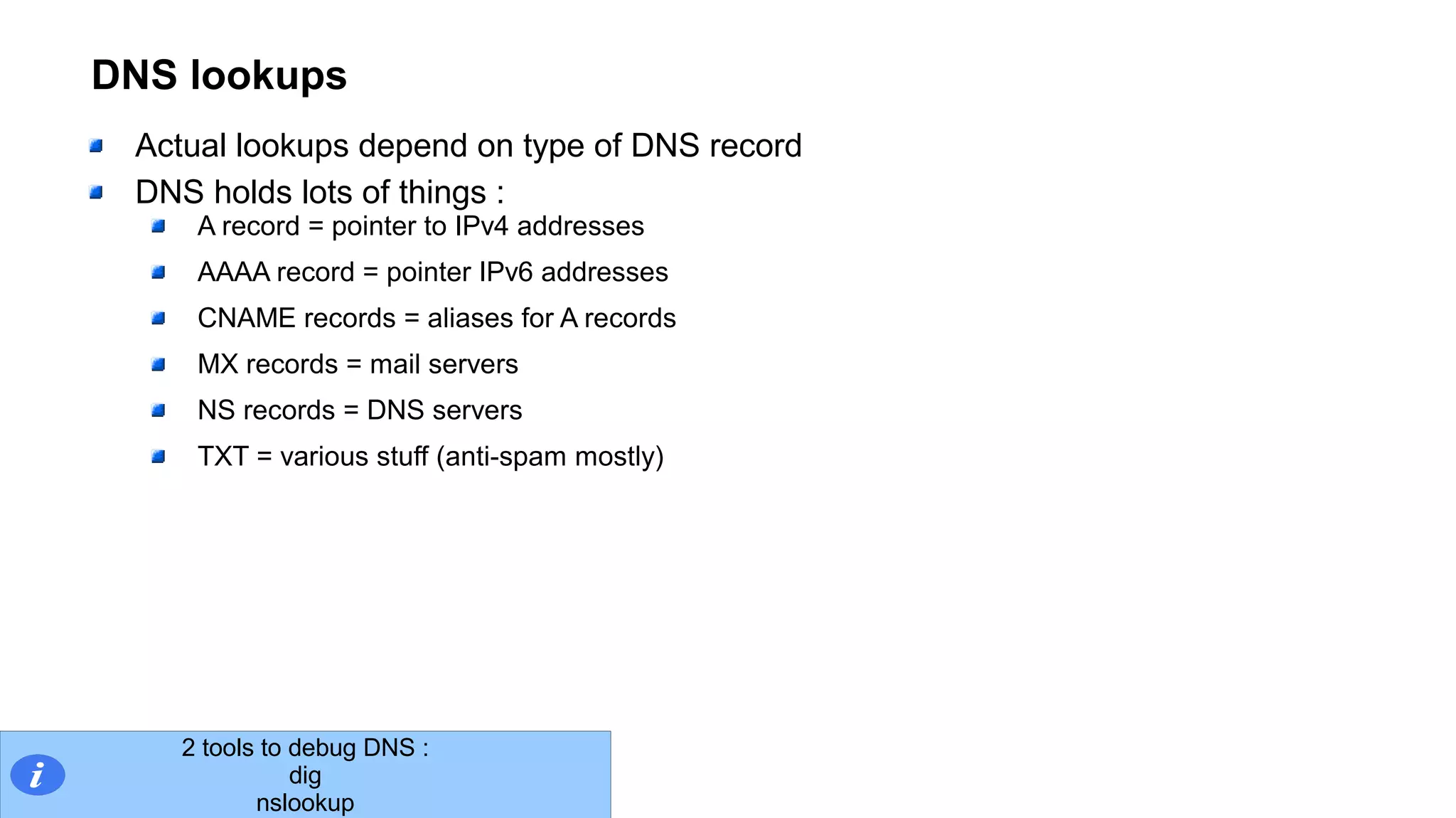
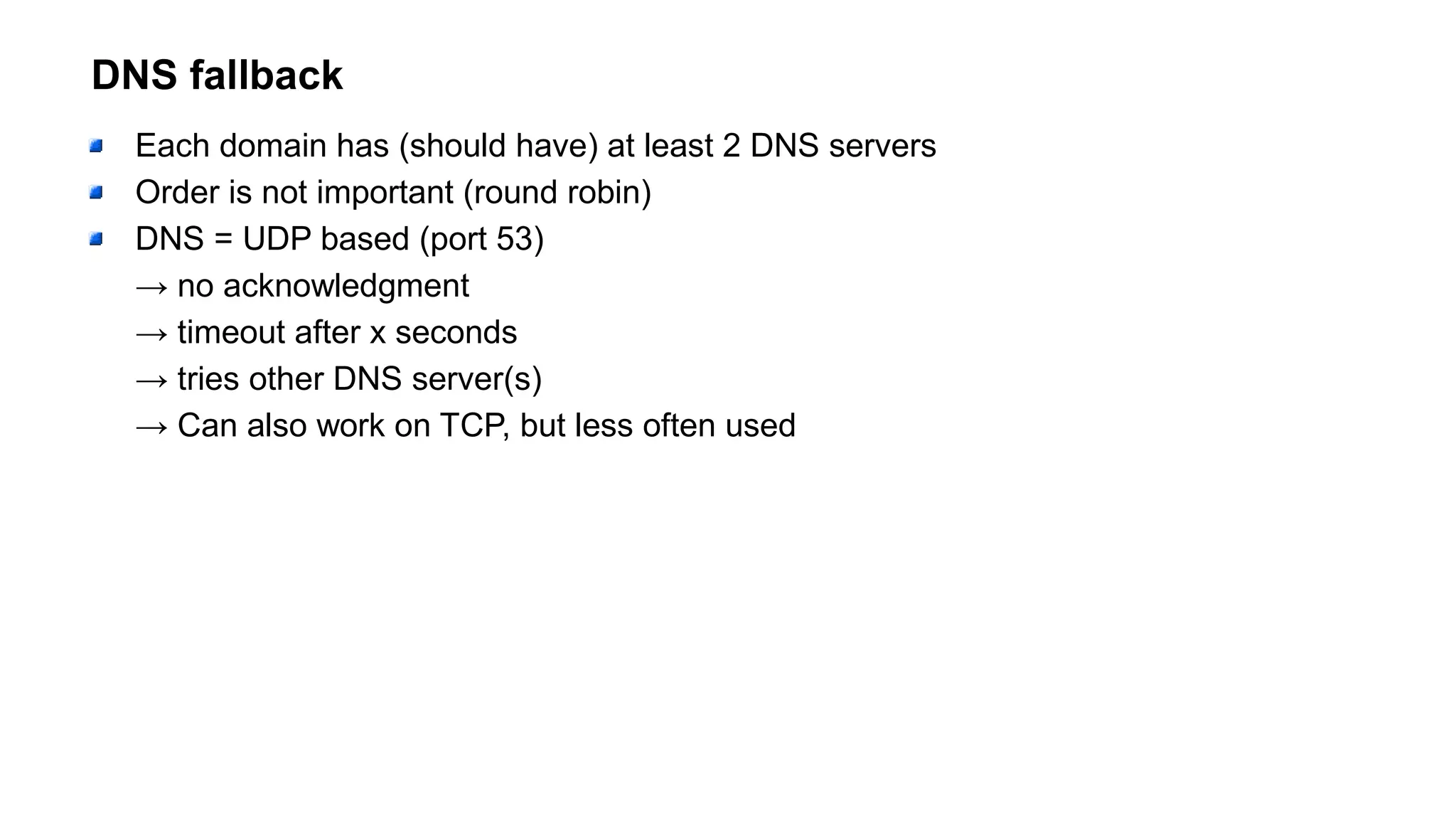
The document outlines foundational concepts of networking, including the roles of TCP/IP, packet structures, IP addressing (both IPv4 and IPv6), and routing mechanisms. It emphasizes the importance of understanding how data is transmitted over networks, with practical considerations for developers and system engineers. Technical details include packet headers, subnetting, and brief overviews of protocols such as DNS, TCP, and UDP.














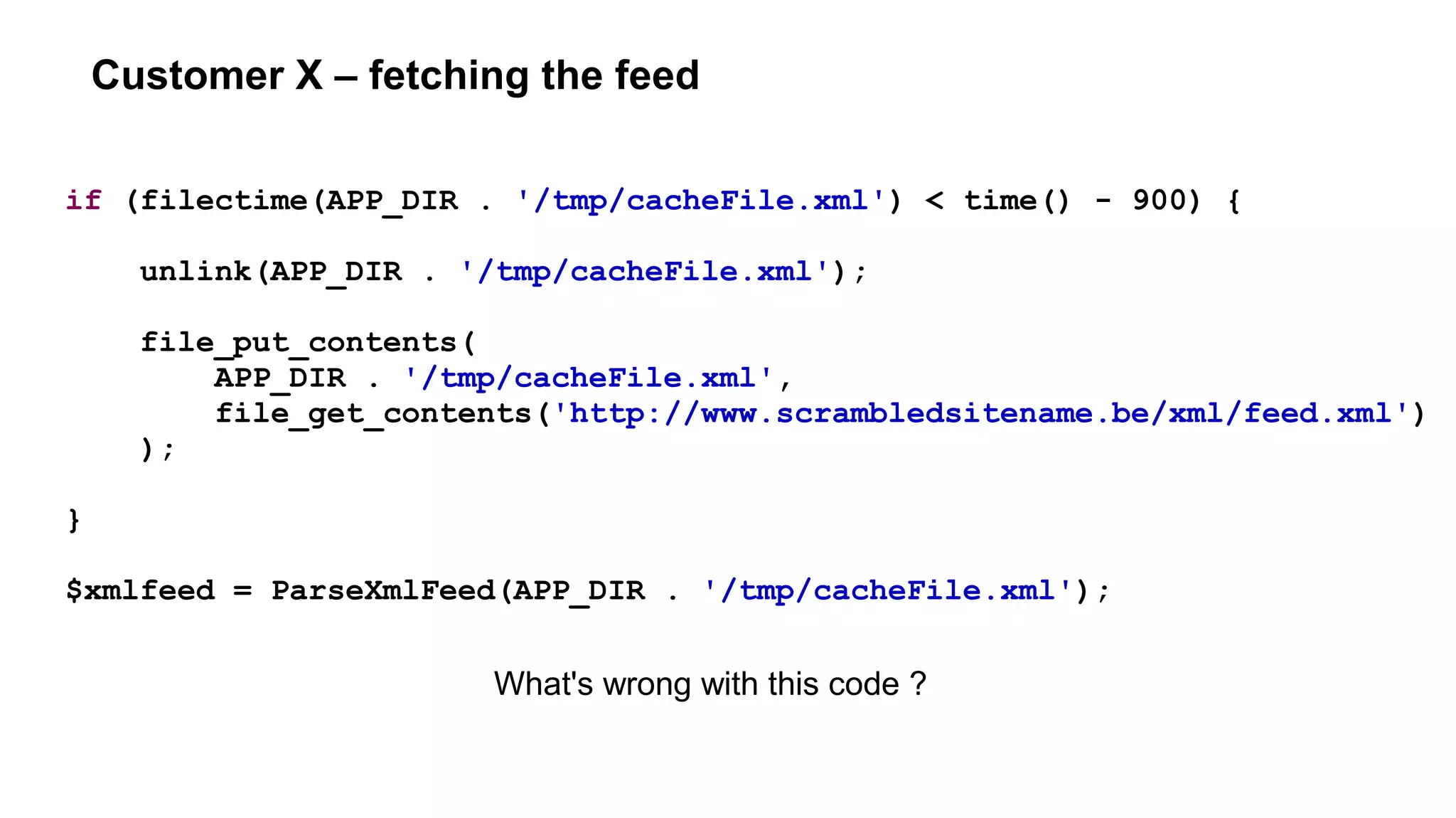
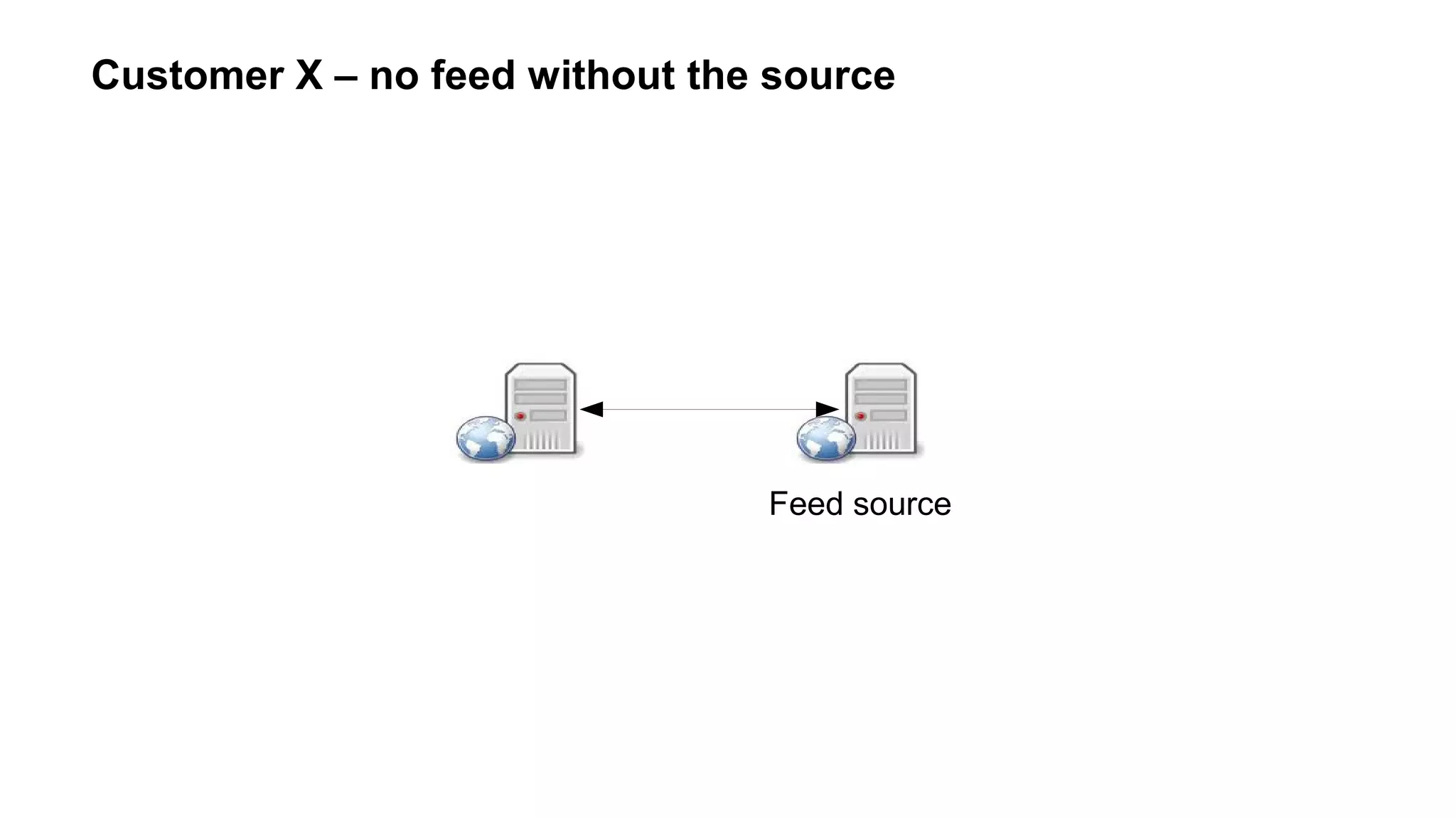
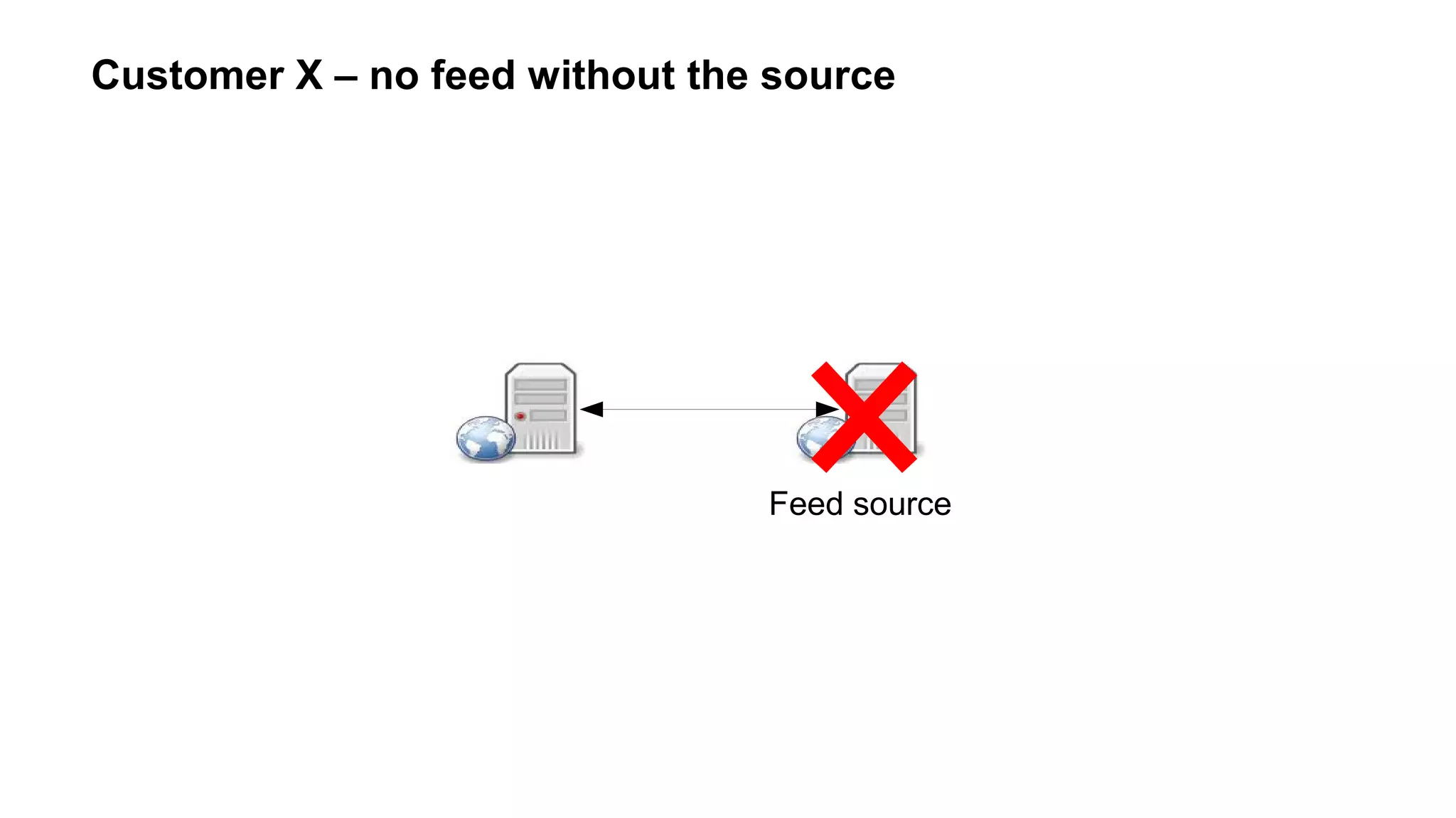
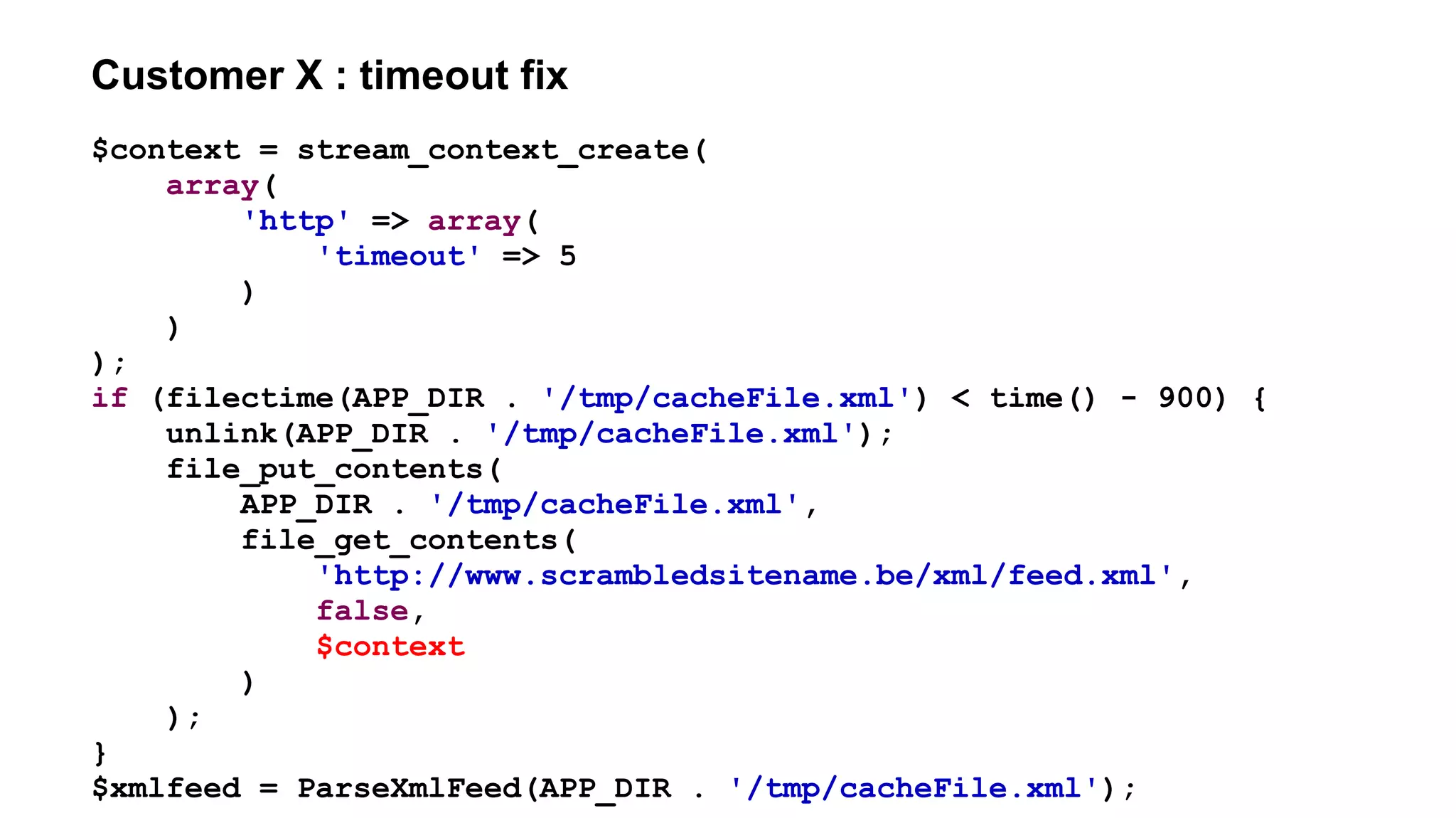
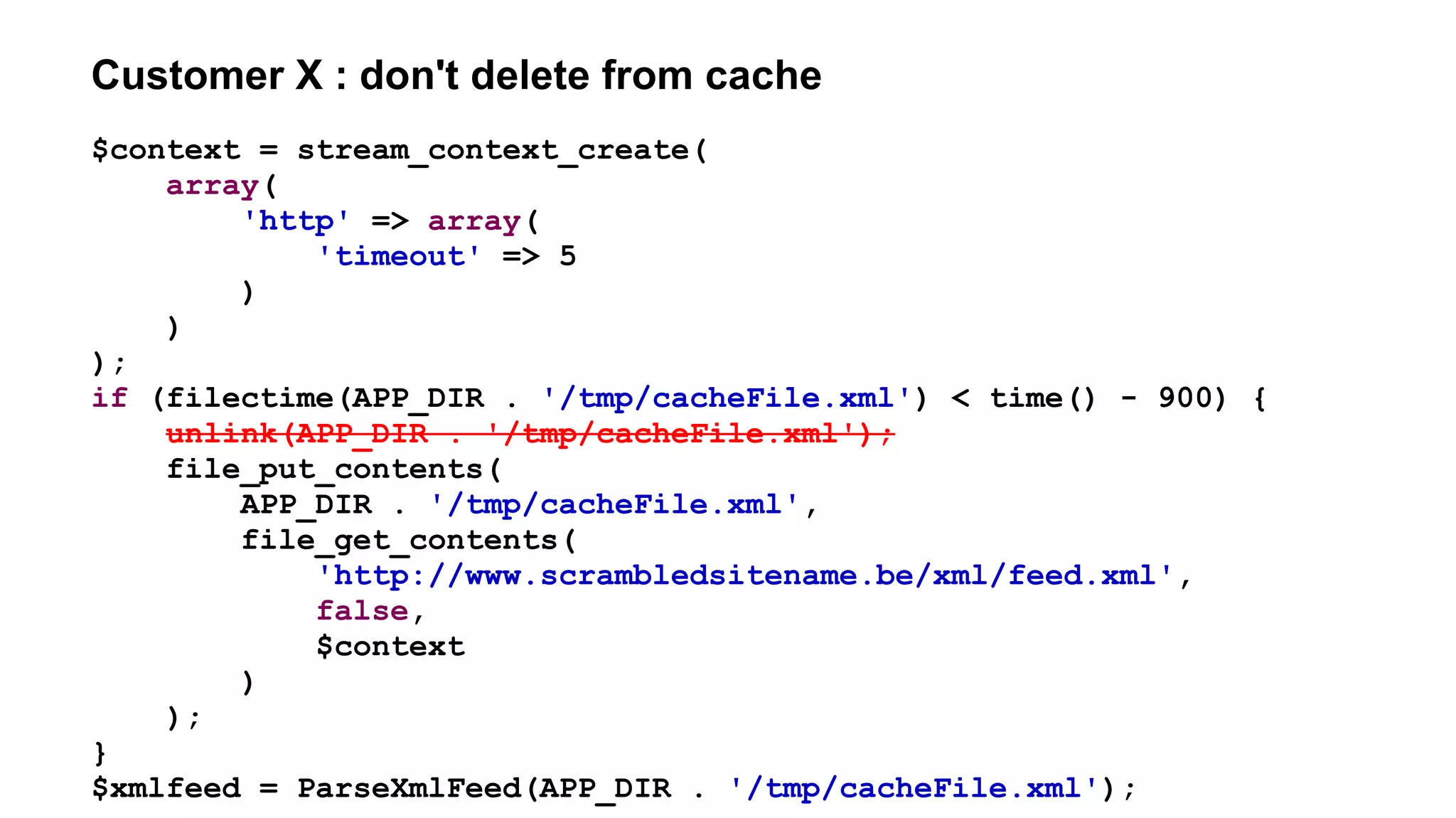
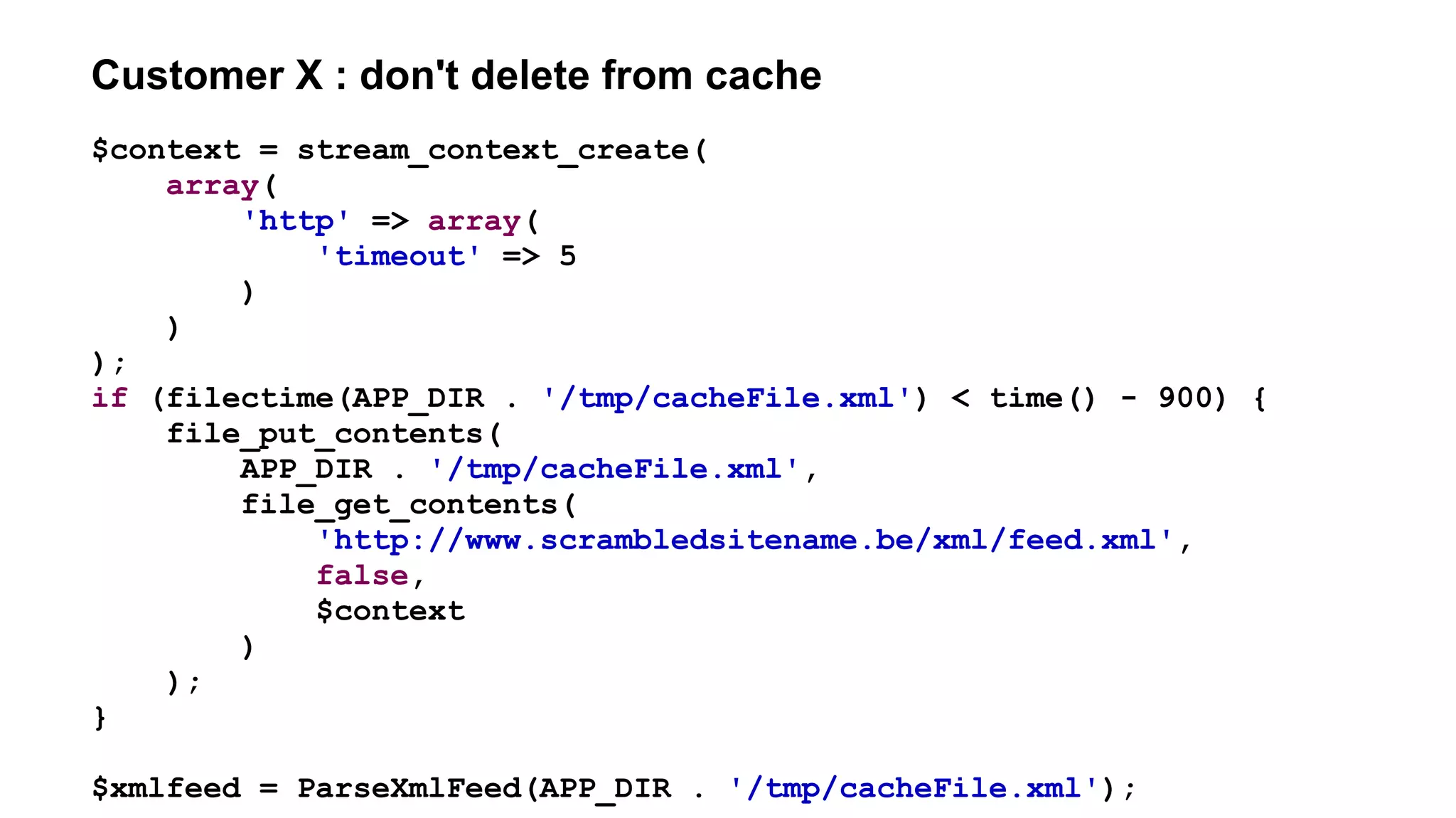
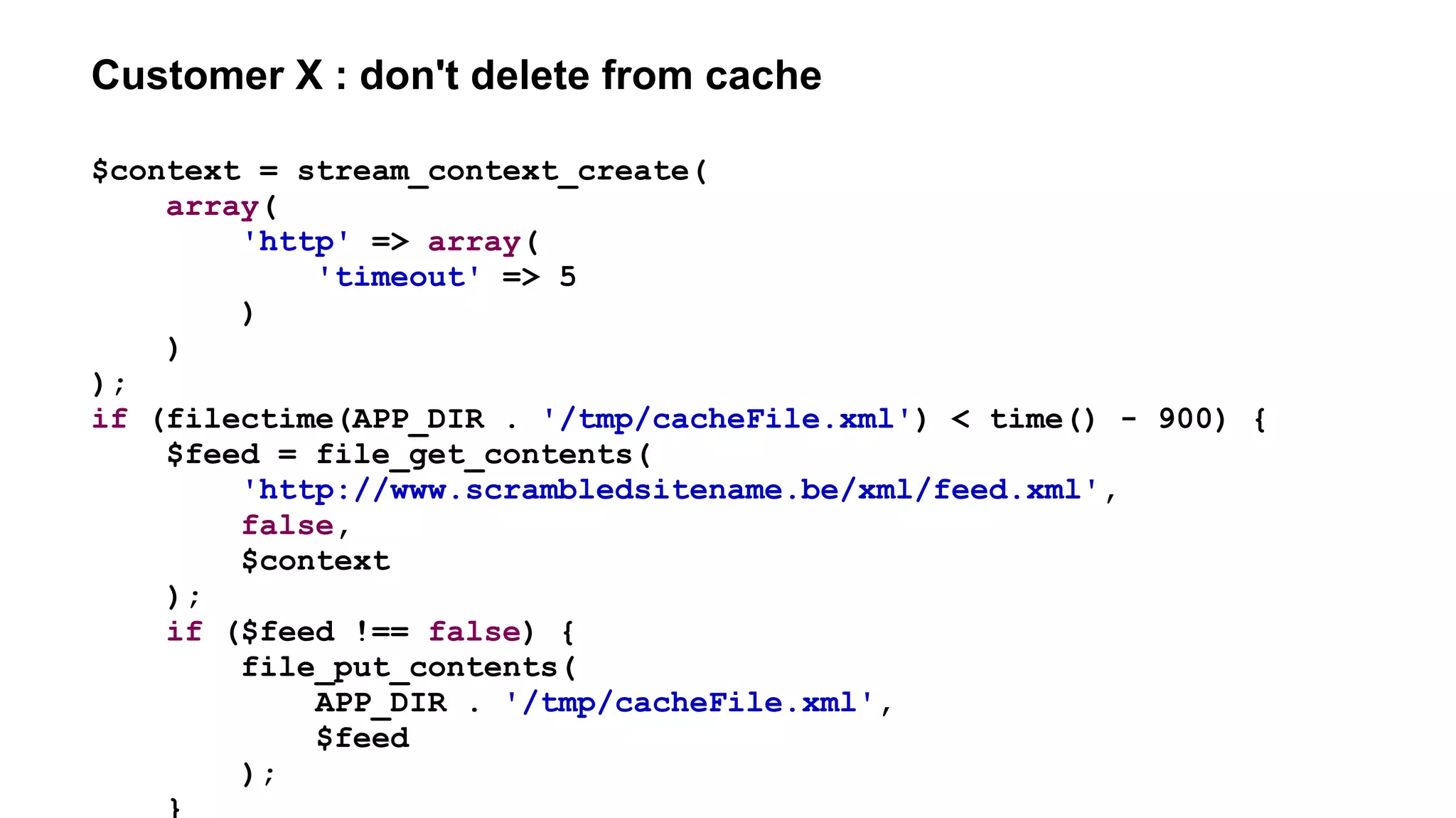
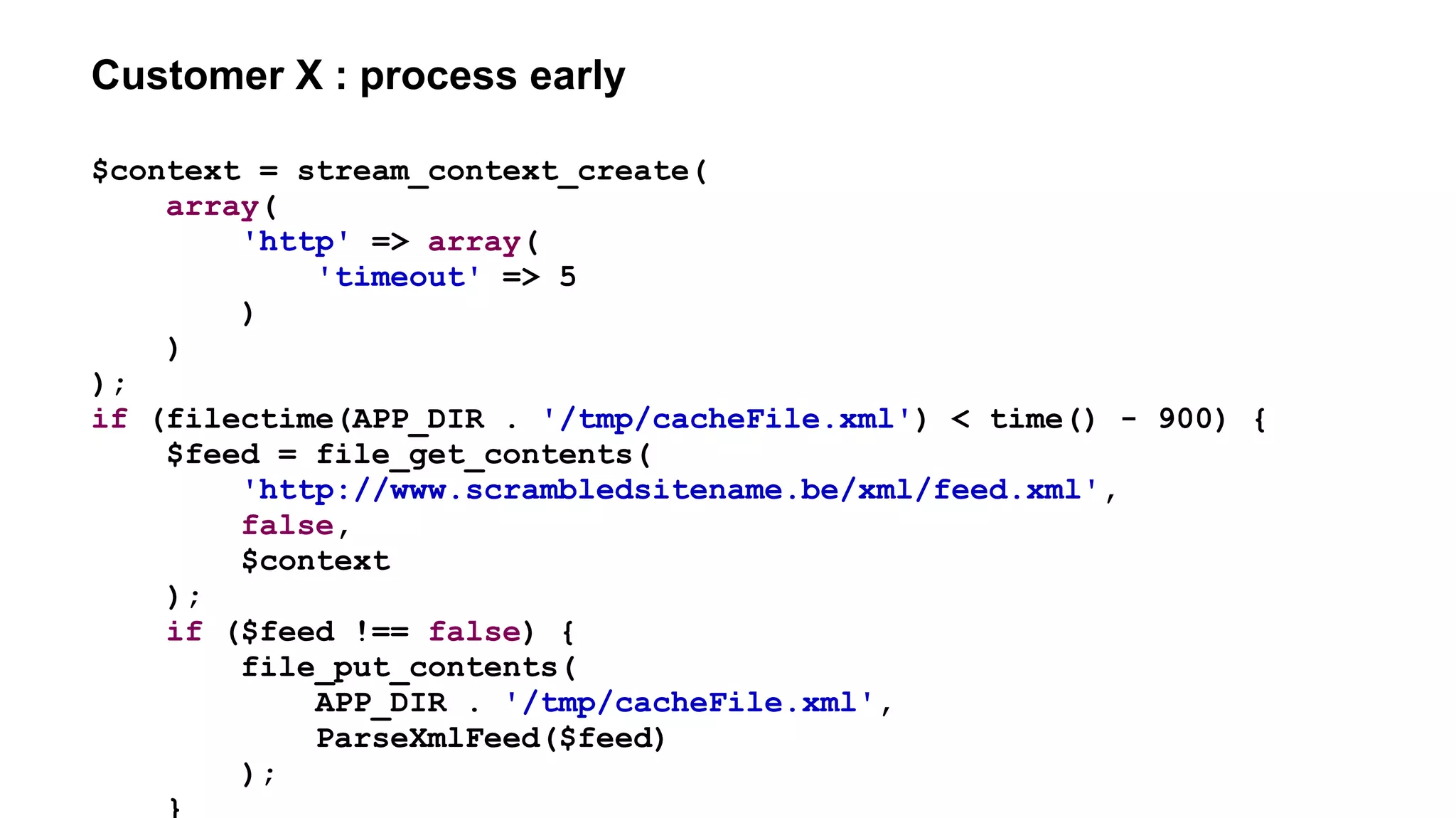
![Customer X : file_[get|put]_contents atomicity
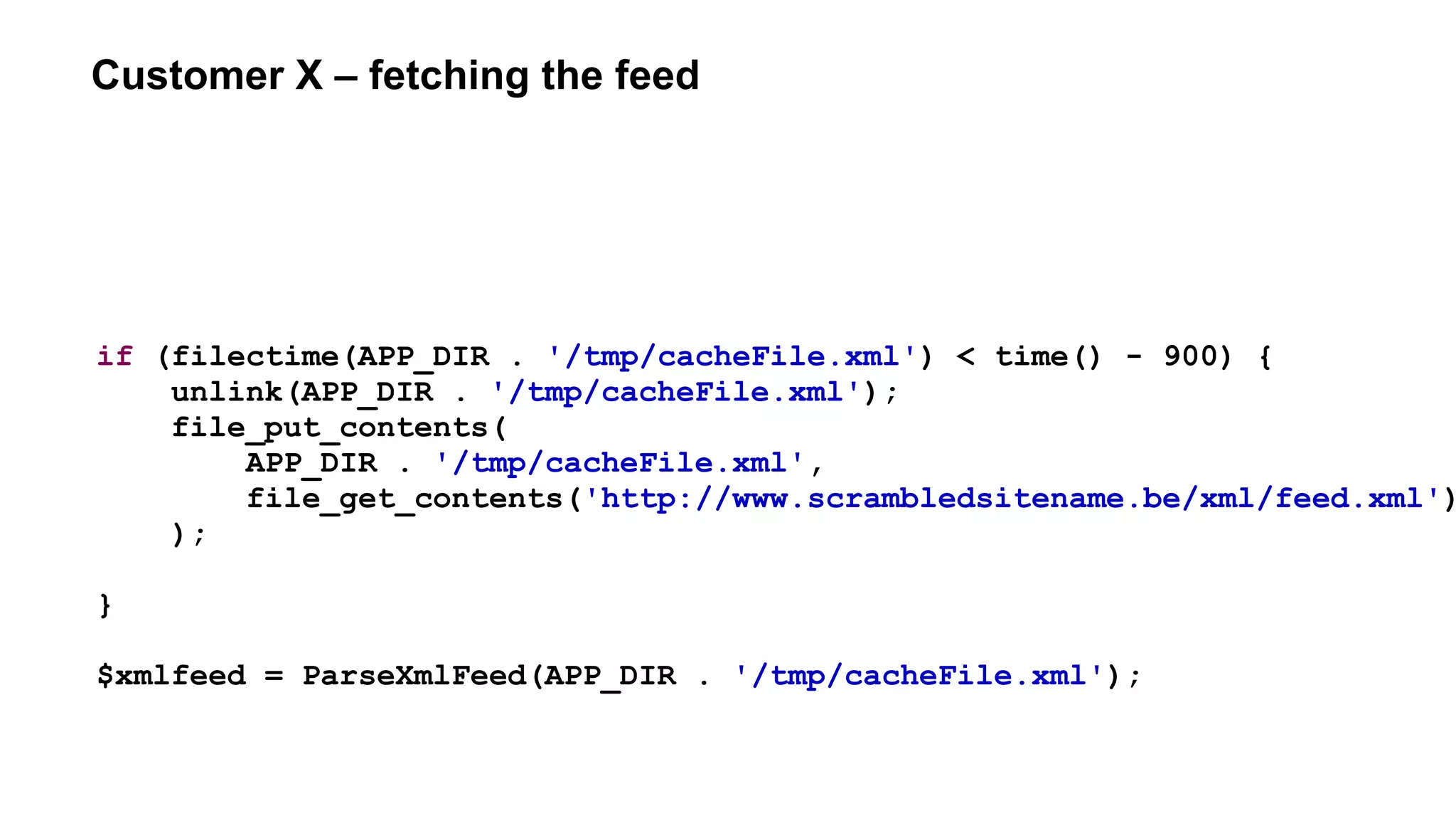
if (filectime(APP_DIR . '/tmp/cacheFile.xml') < time() - 900) {
$feed = file_get_contents(
'http://www.scrambledsitename.be/xml/feed.xml',
false,
$context
);
if ($feed !== false) {
file_put_contents(
APP_DIR . '/tmp/cacheFile.xml',
ParseXmlFeed($feed)
);
}
}
Relying on user → concurrent requests → possible data corruption
Better : run every 15min through cronjob](https://image.slidesharecdn.com/networking-short-wde-190221152226/75/Your-app-lives-on-the-network-networking-for-web-developers-73-2048.jpg)