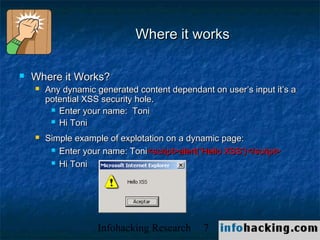
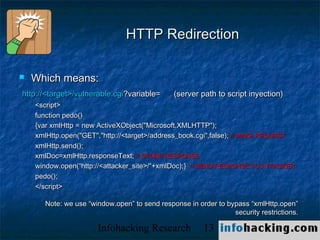
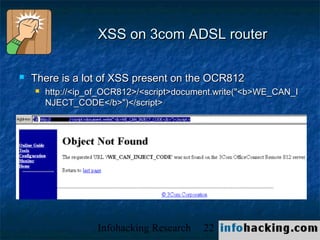
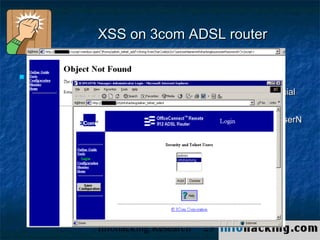
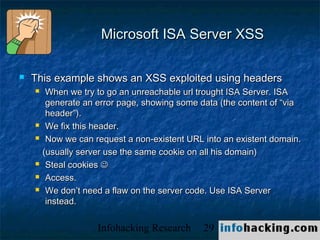
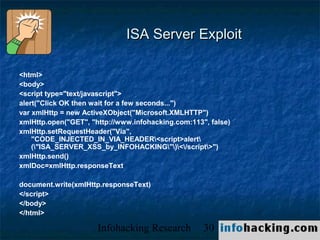
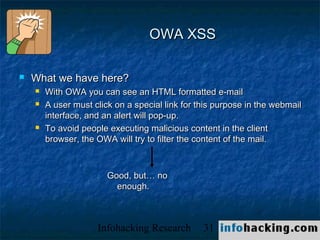
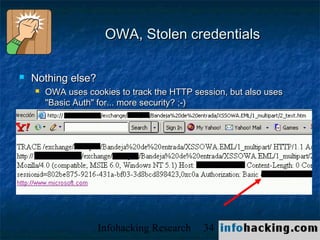
The document summarizes a presentation on cross-site scripting (XSS) attacks. It discusses how XSS works, where it can be exploited, and examples of XSS vulnerabilities. Specific examples covered include XSS in 3Com routers, Inktomi Traffic Servers, Iplanet messaging servers, Microsoft ISA servers, and Outlook Web Access. The presentation also discusses how XSS could be used in worms and trojans to spread malware or steal user information.