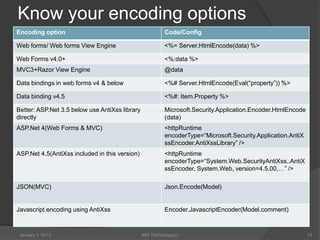
The document discusses cross-site scripting (XSS) vulnerabilities from a developer’s perspective, detailing methods of exploitation, including reflected, persistent, and DOM-based attacks. It emphasizes preventive strategies such as HTML encoding, auditing code for user input, and maintaining strict data sanitization practices. The document also highlights the importance of keeping up with evolving XSS threat patterns and utilizing various tools for detection and prevention.









![How do you prevent it?(Last but not
least)
Audit every location data is assigned, output, and used since lots of
data can be affected by user
Ensure its not used in JavaScript, or Highly sanitized
ASP.NET Textbox HtmlEncodes(), Label does not
○ KNOW YOUR CONTROL’s BEHAVIOUR!!! EVERY ONE!
Test by injecting script, special characters (ex <) into app – use Fiddler if you
must, to change incoming data
Be Concerned with any place that DOM elements are
created/modified
Use functions such as setAttribute and var y = document.createElement(“div”);
rather than document.writeln, $(x).html(), element.innerHTML, eval
Deprecate IE6 (and all older browsers)
Use Request.Browser, ie6update.com, etc…
Don’t turn off EnableRequestValidation or ValidateRequest!
MVC apps use [AllowHtml], Web forms more difficult (Until 4.5!!)
January 1, 2013 99X Technology(c) 12](https://image.slidesharecdn.com/crosssitescripting-130101023442-phpapp01/85/Cross-site-scripting-12-320.jpg)