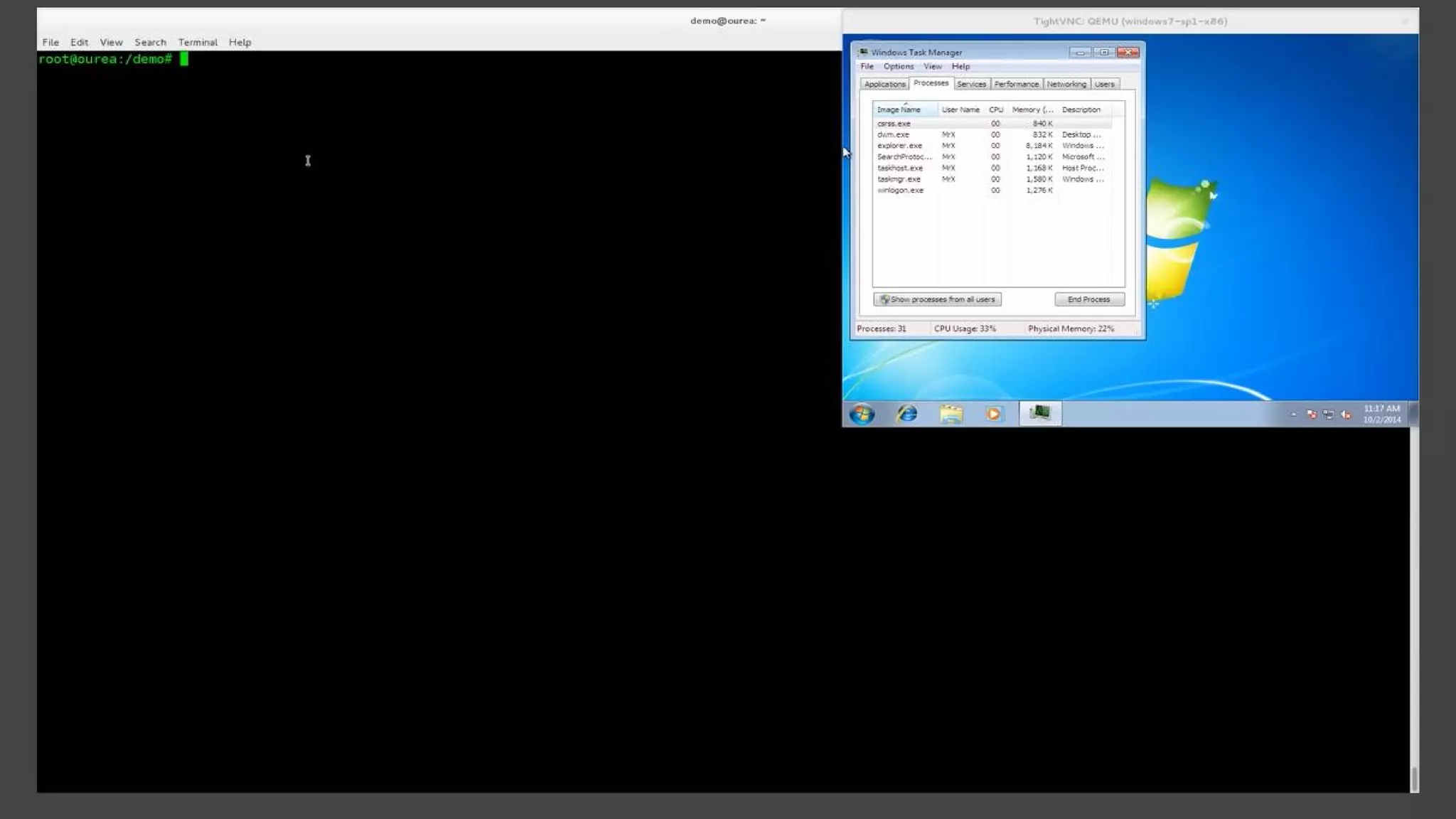
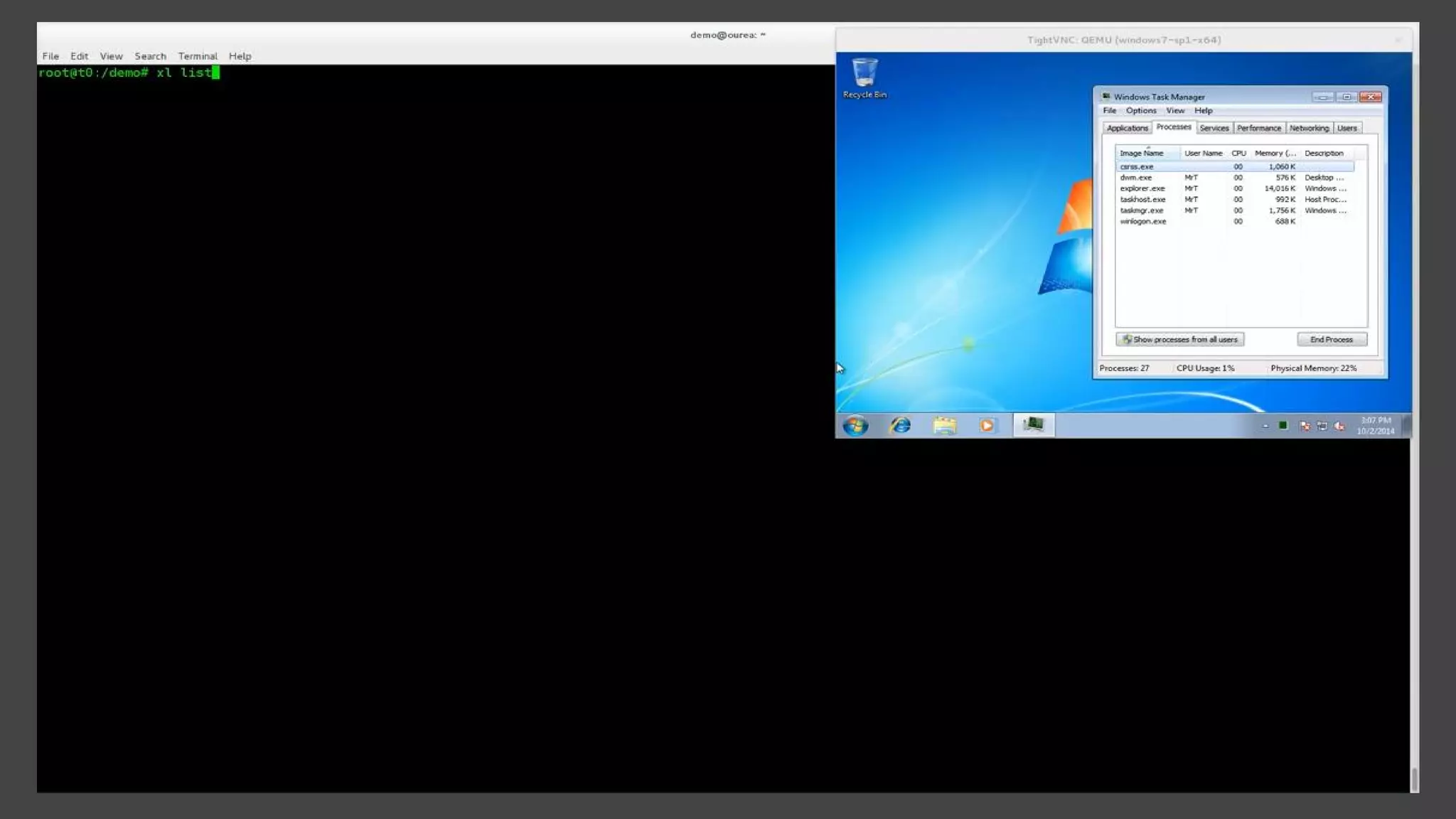
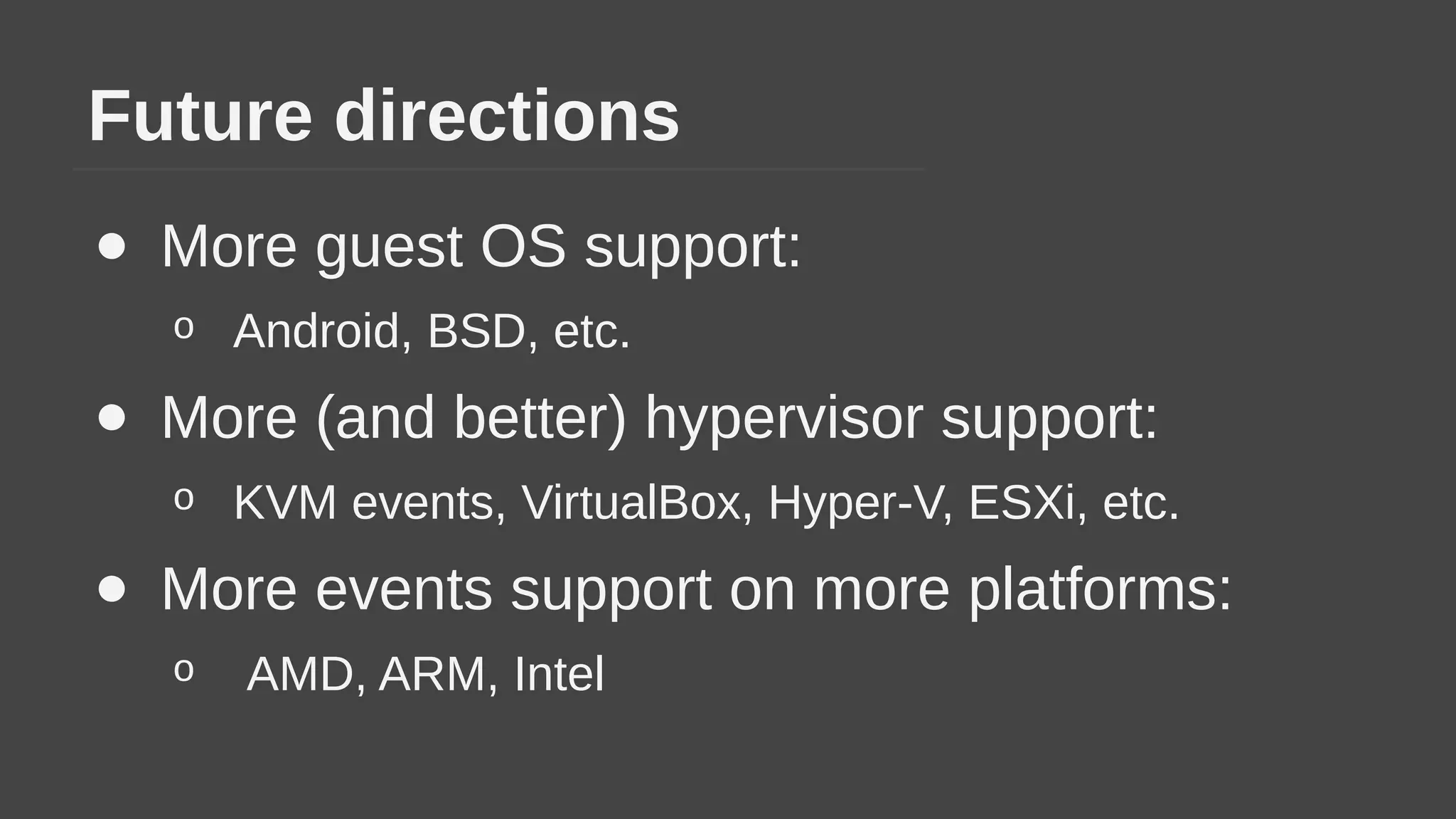
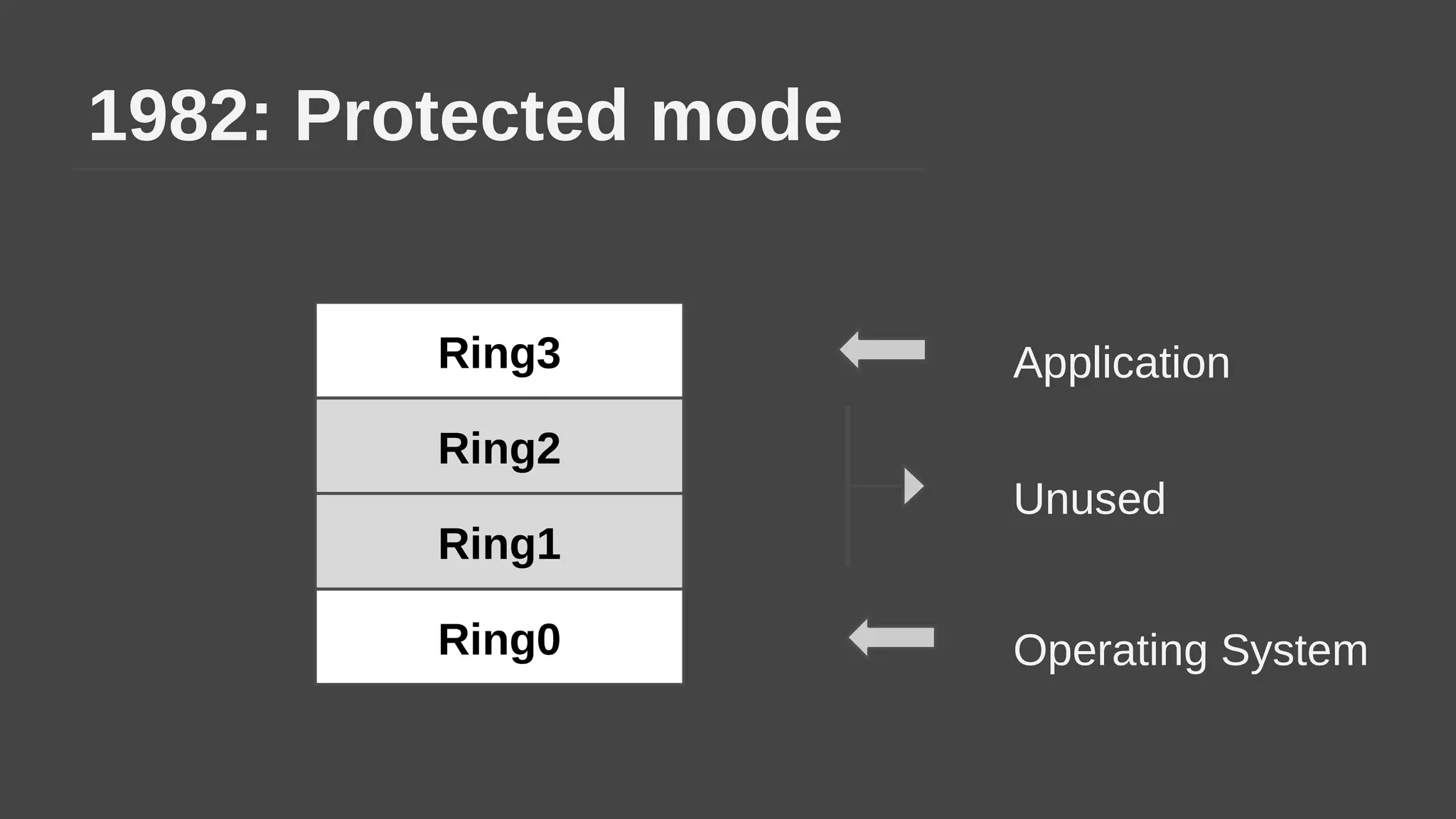
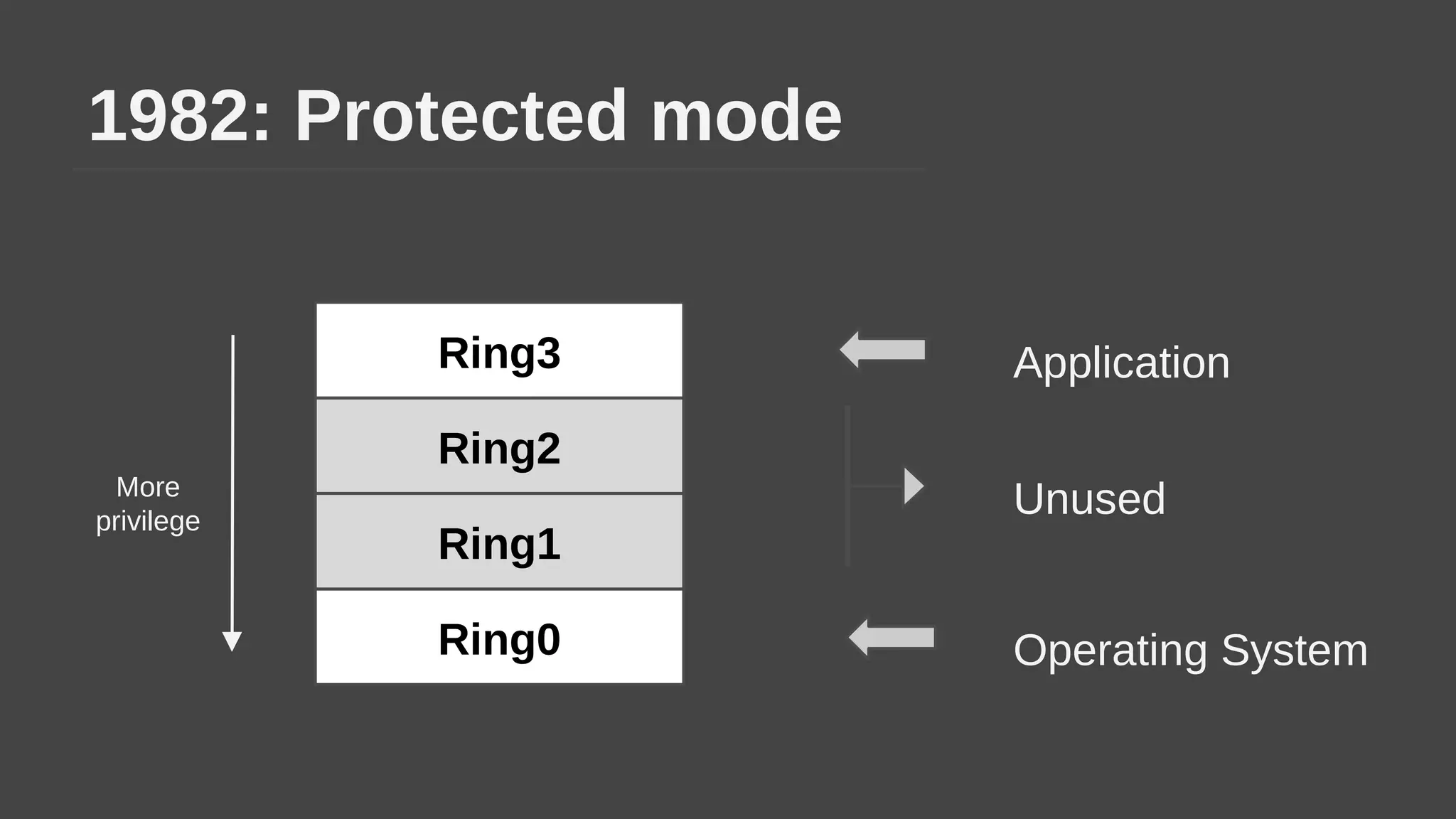
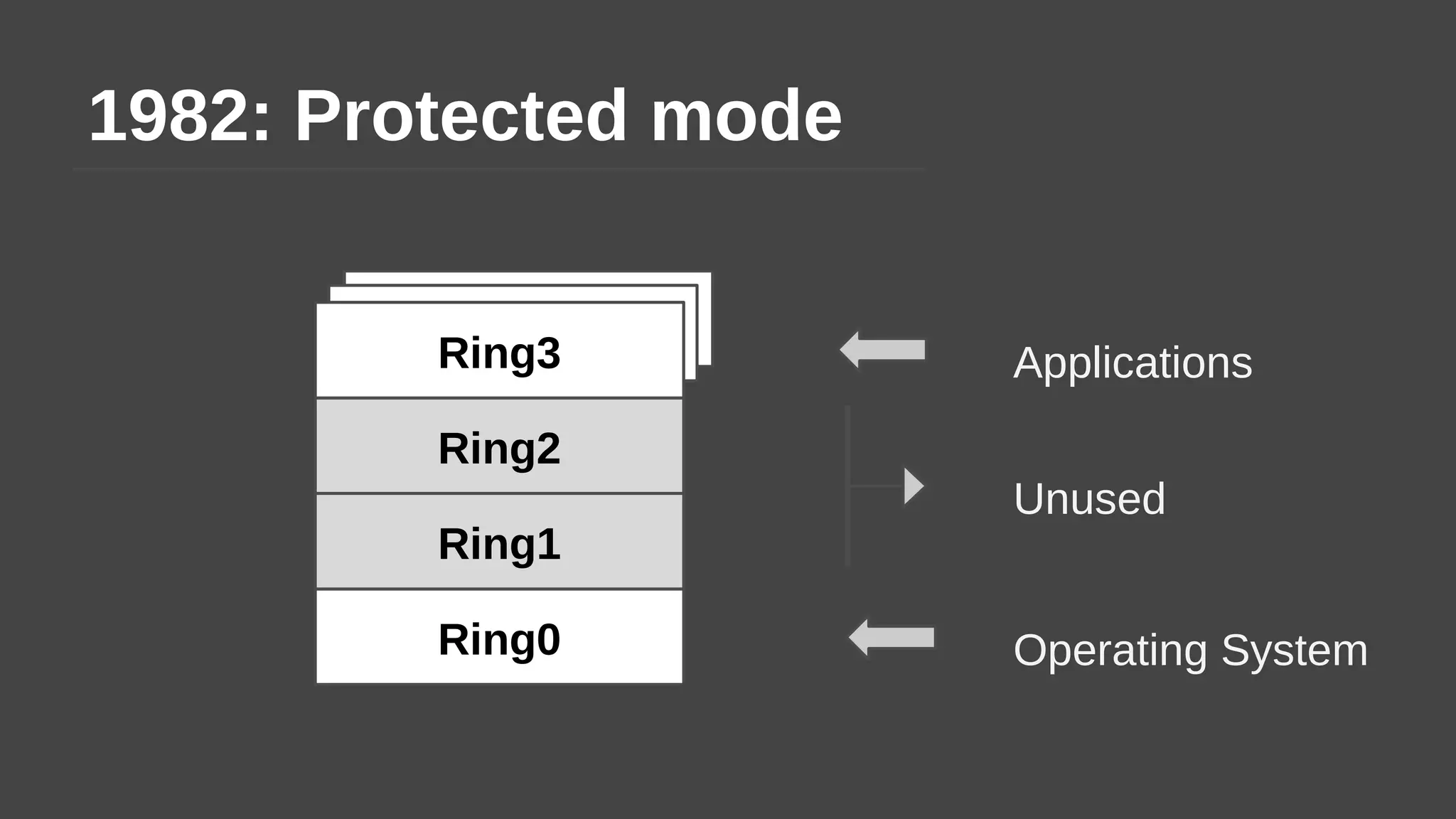
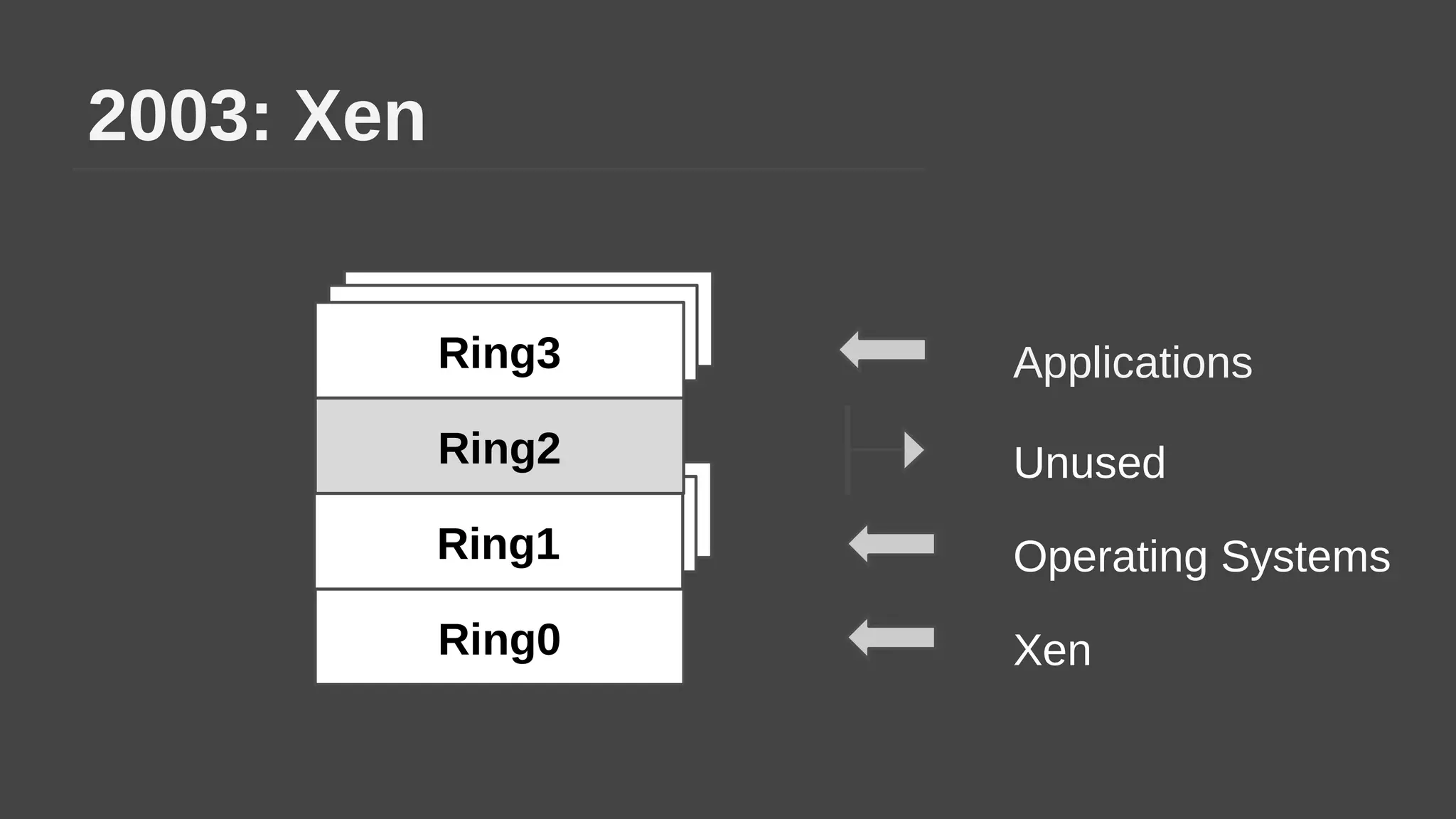
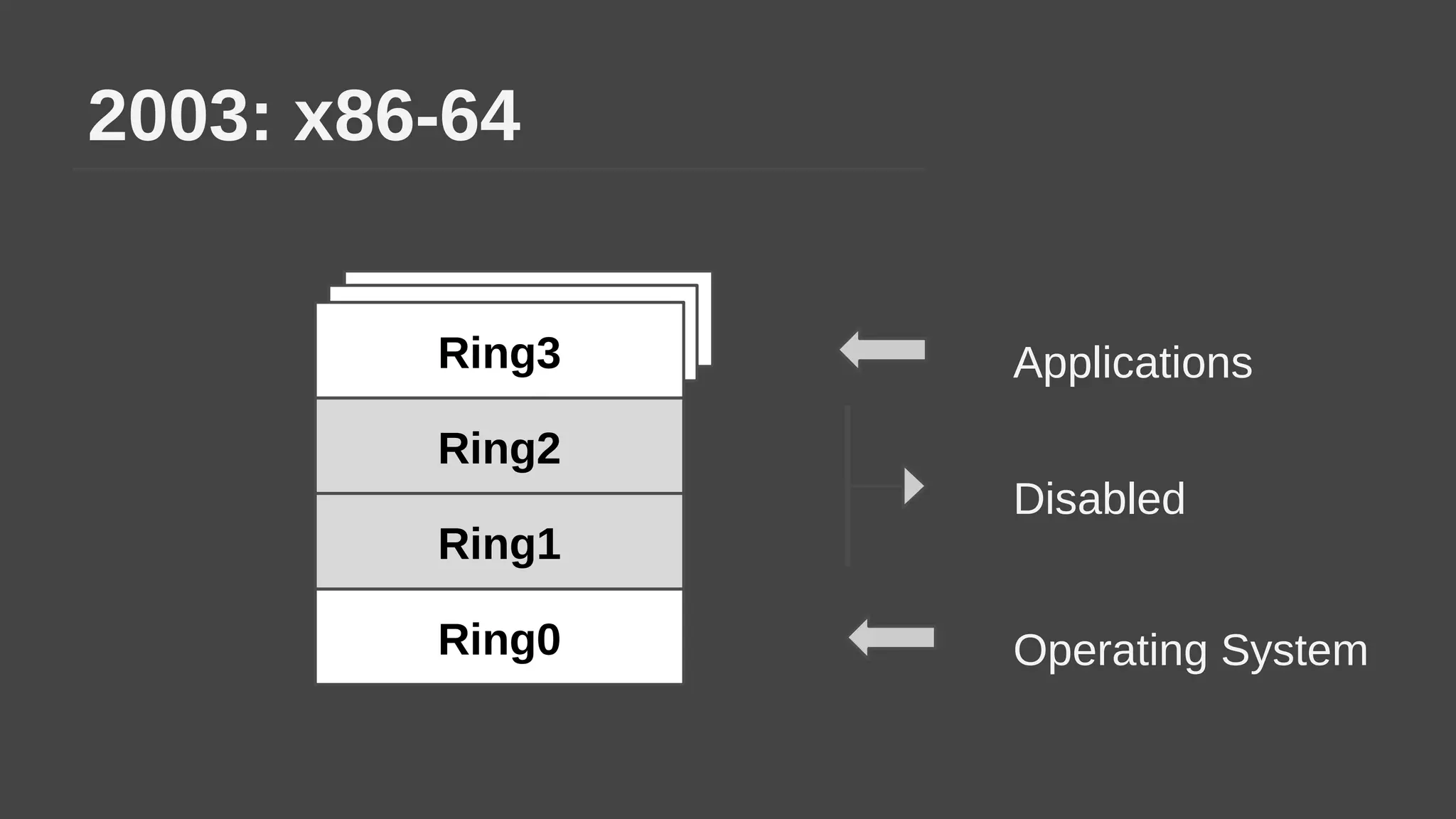
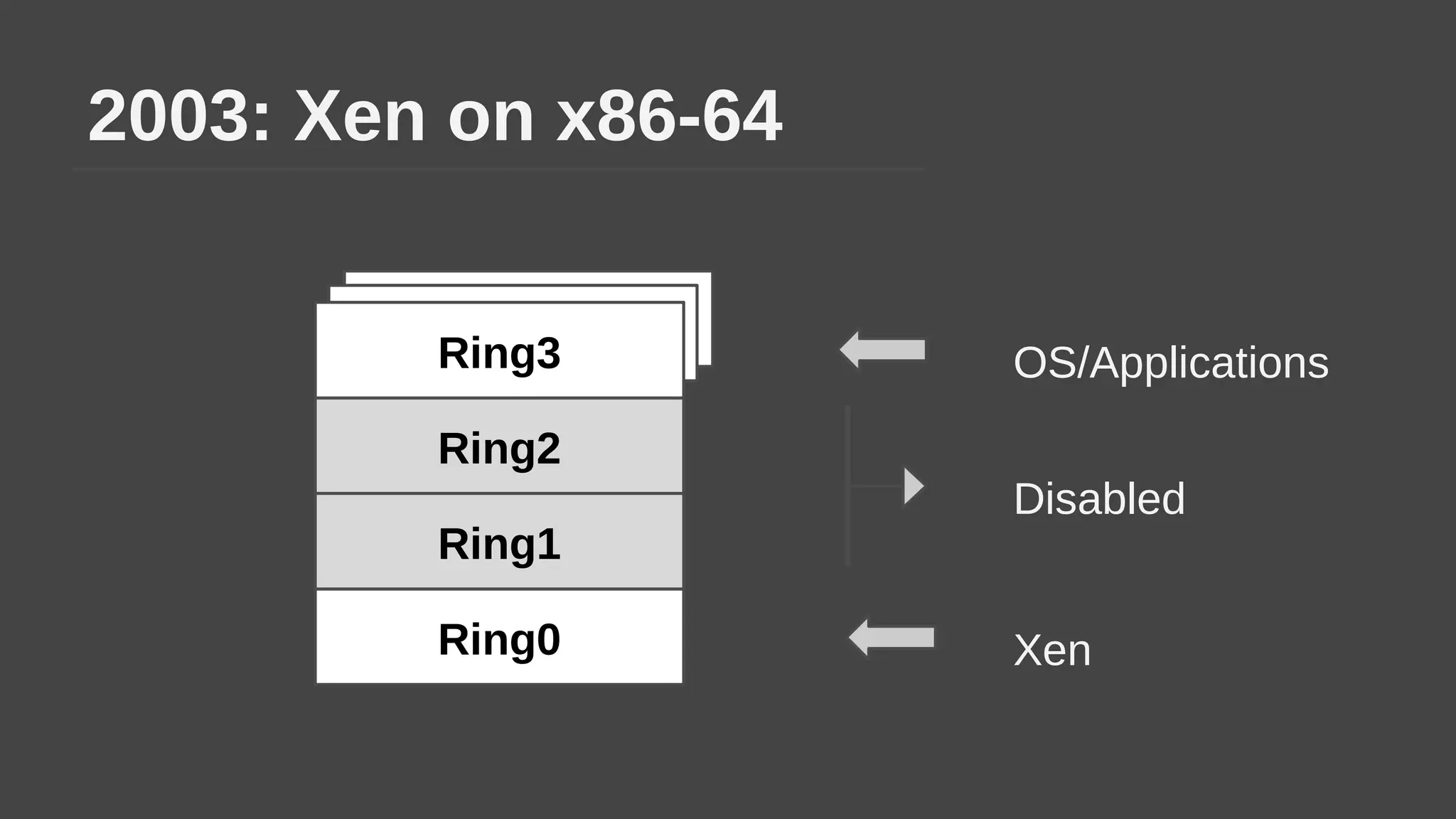
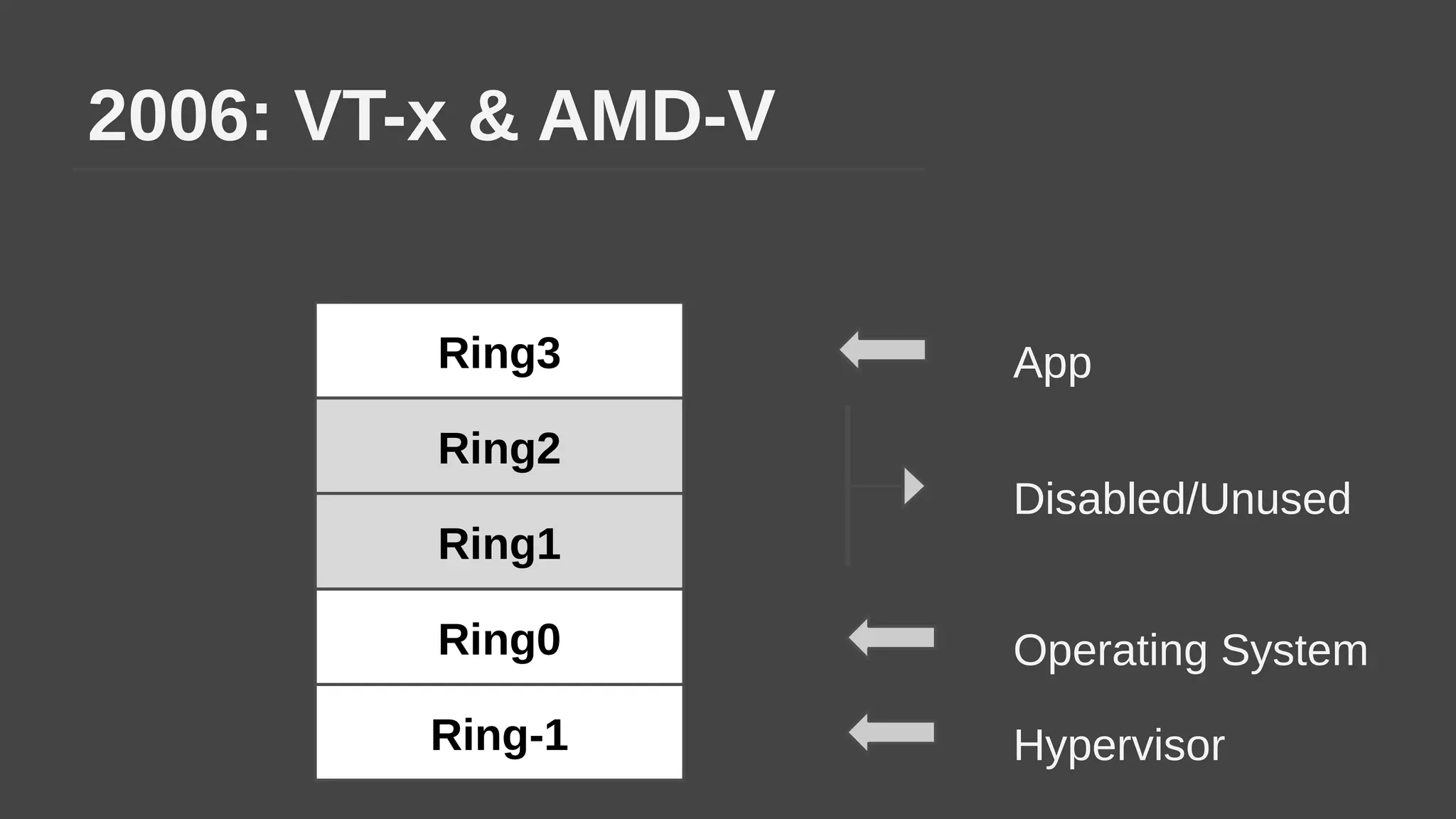
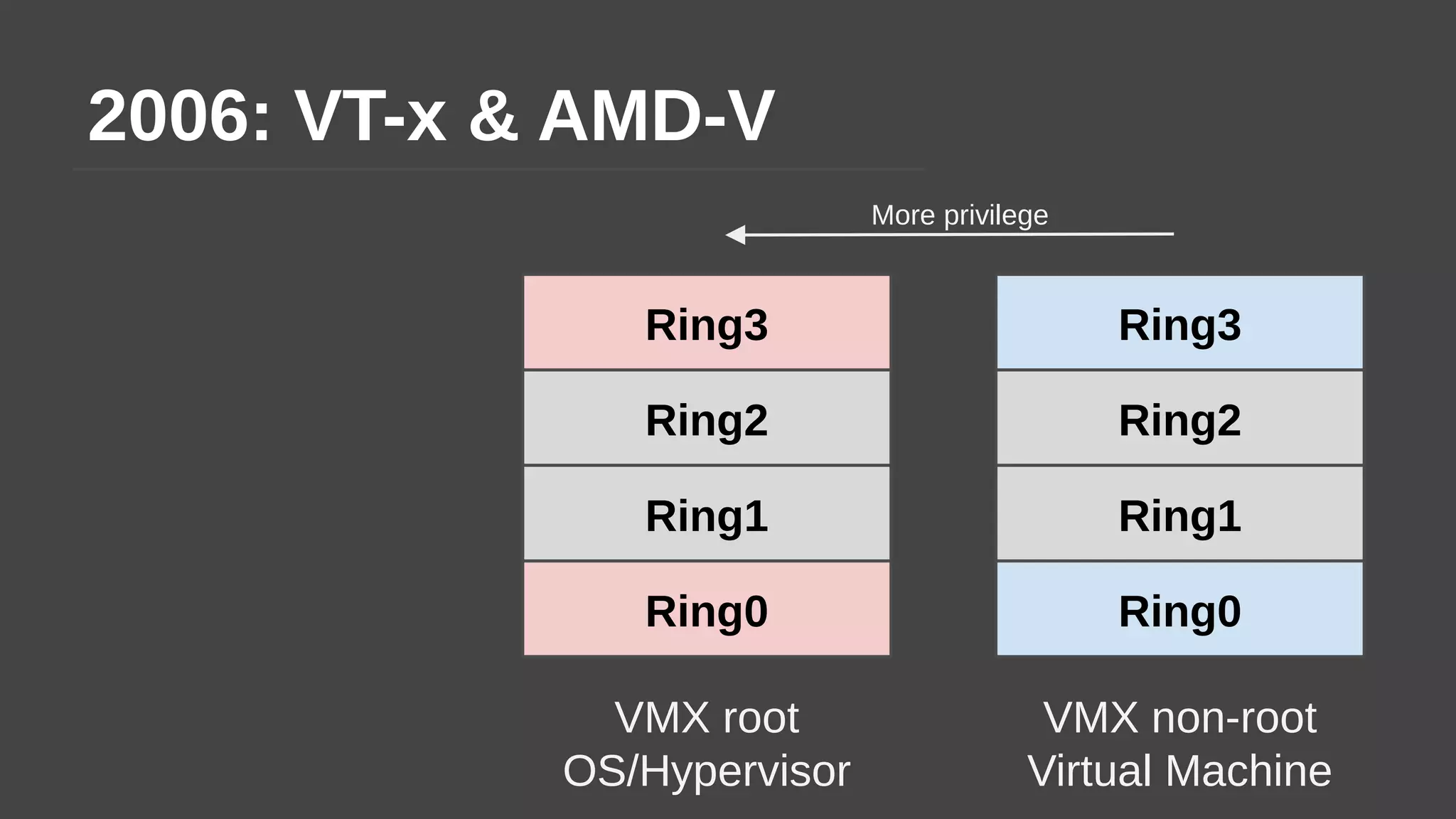
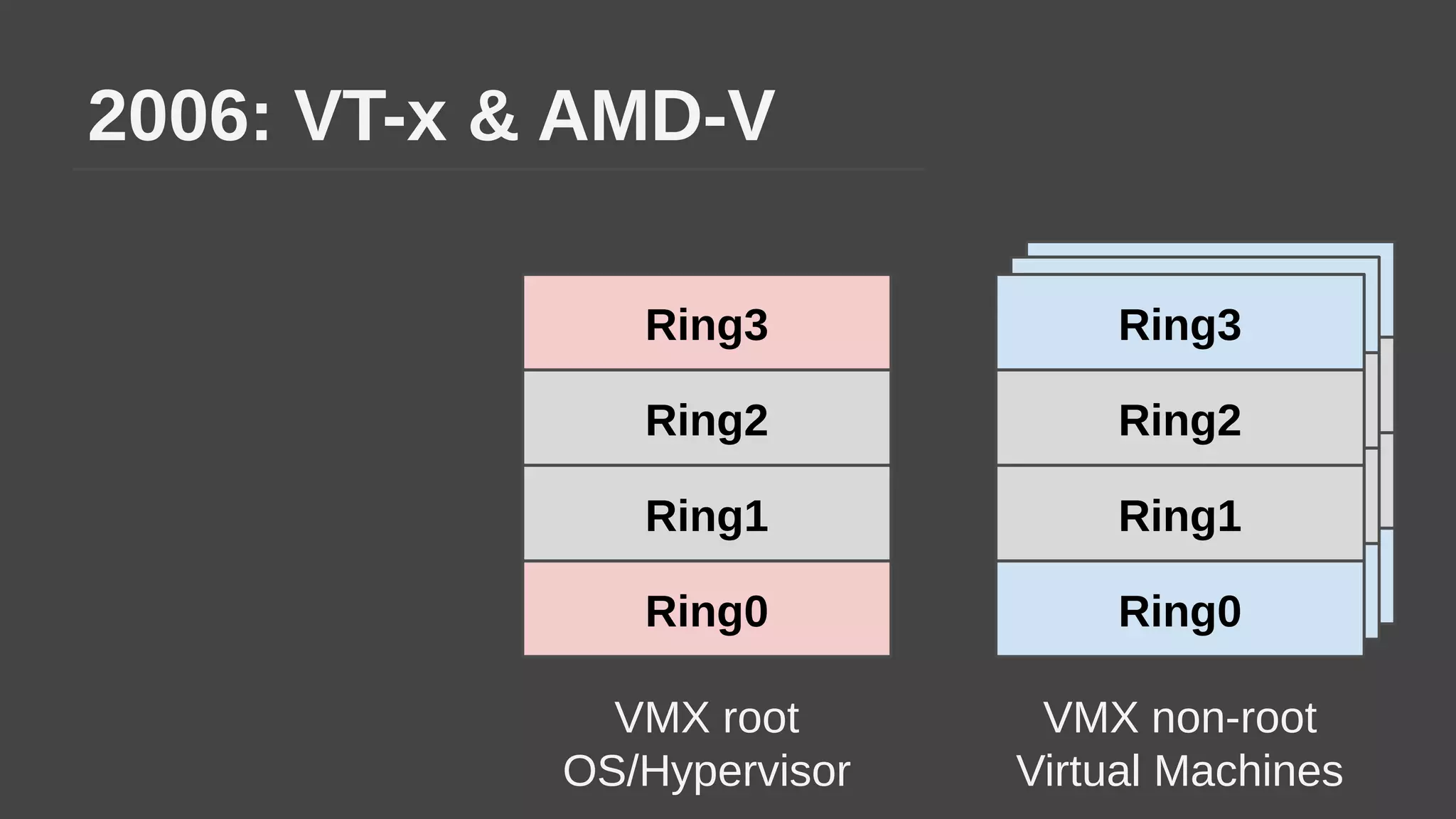
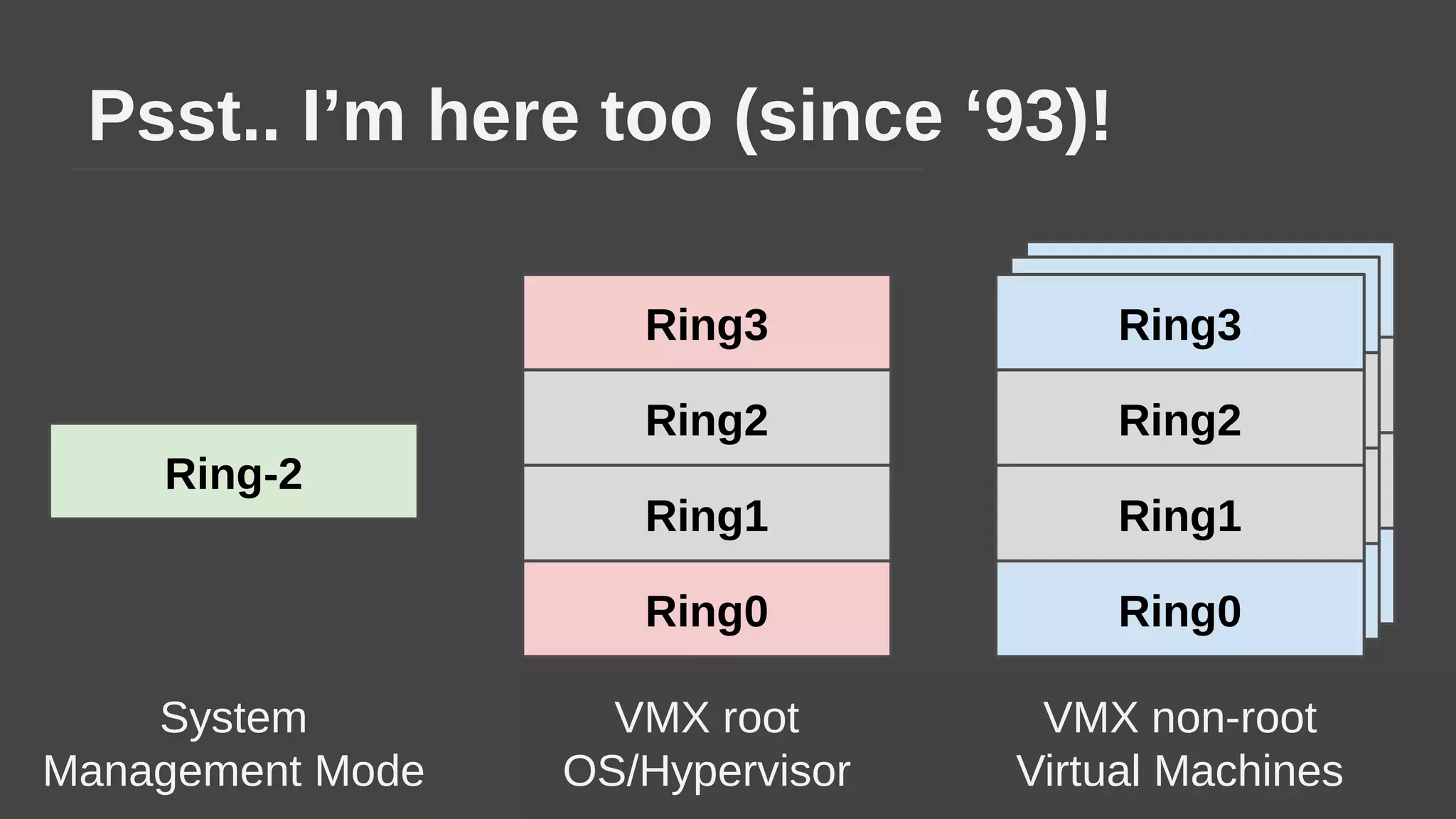
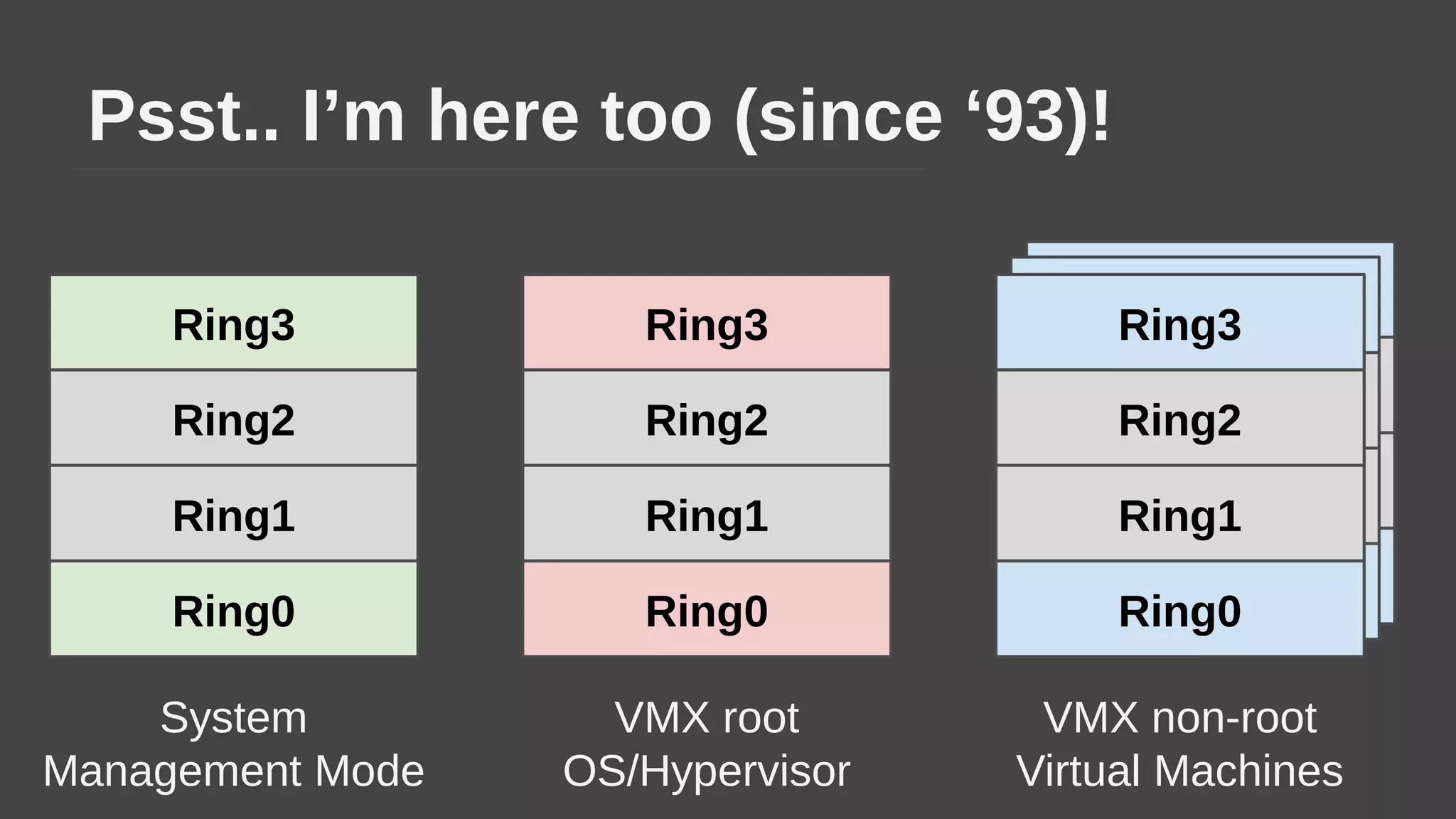
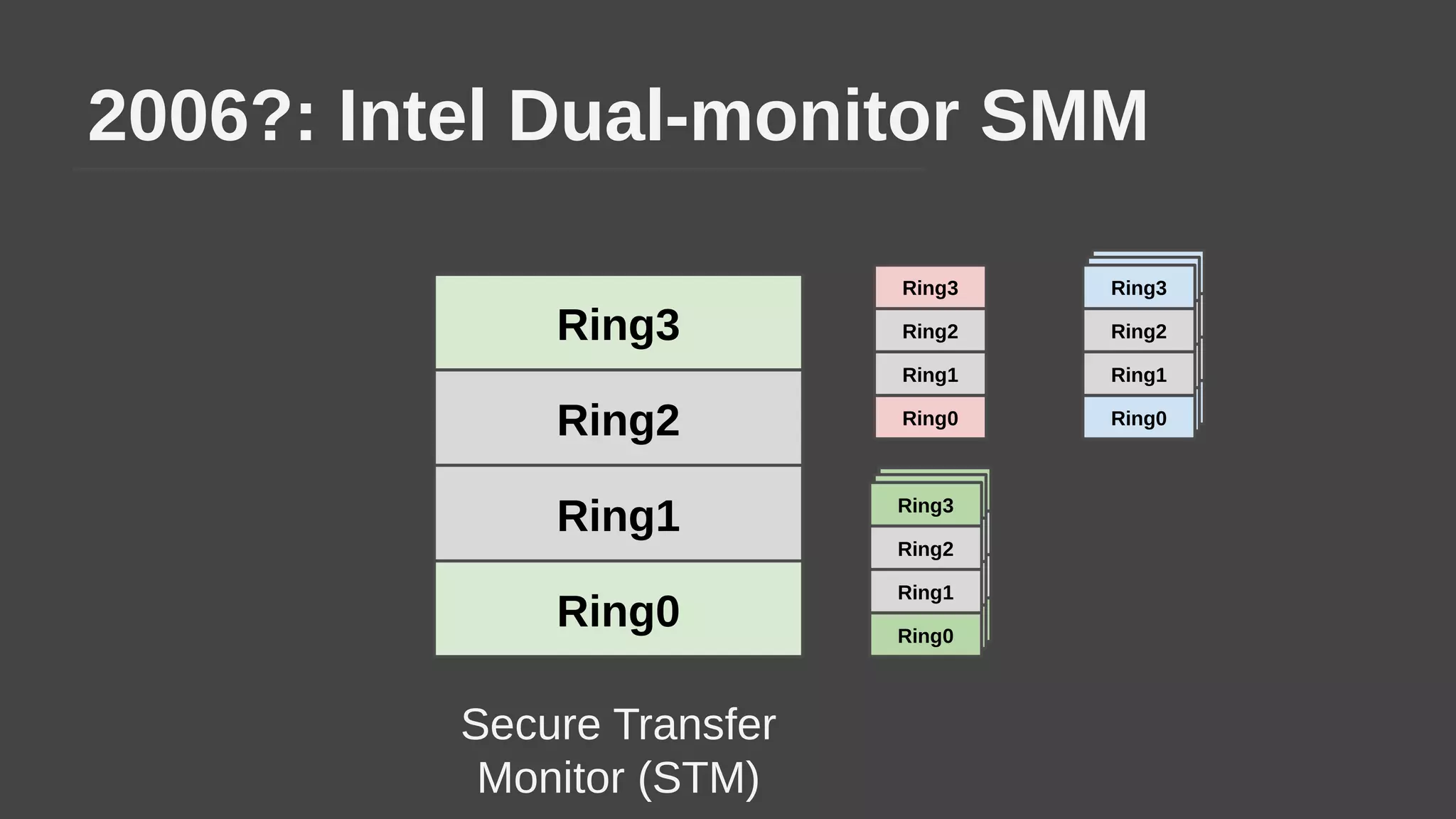
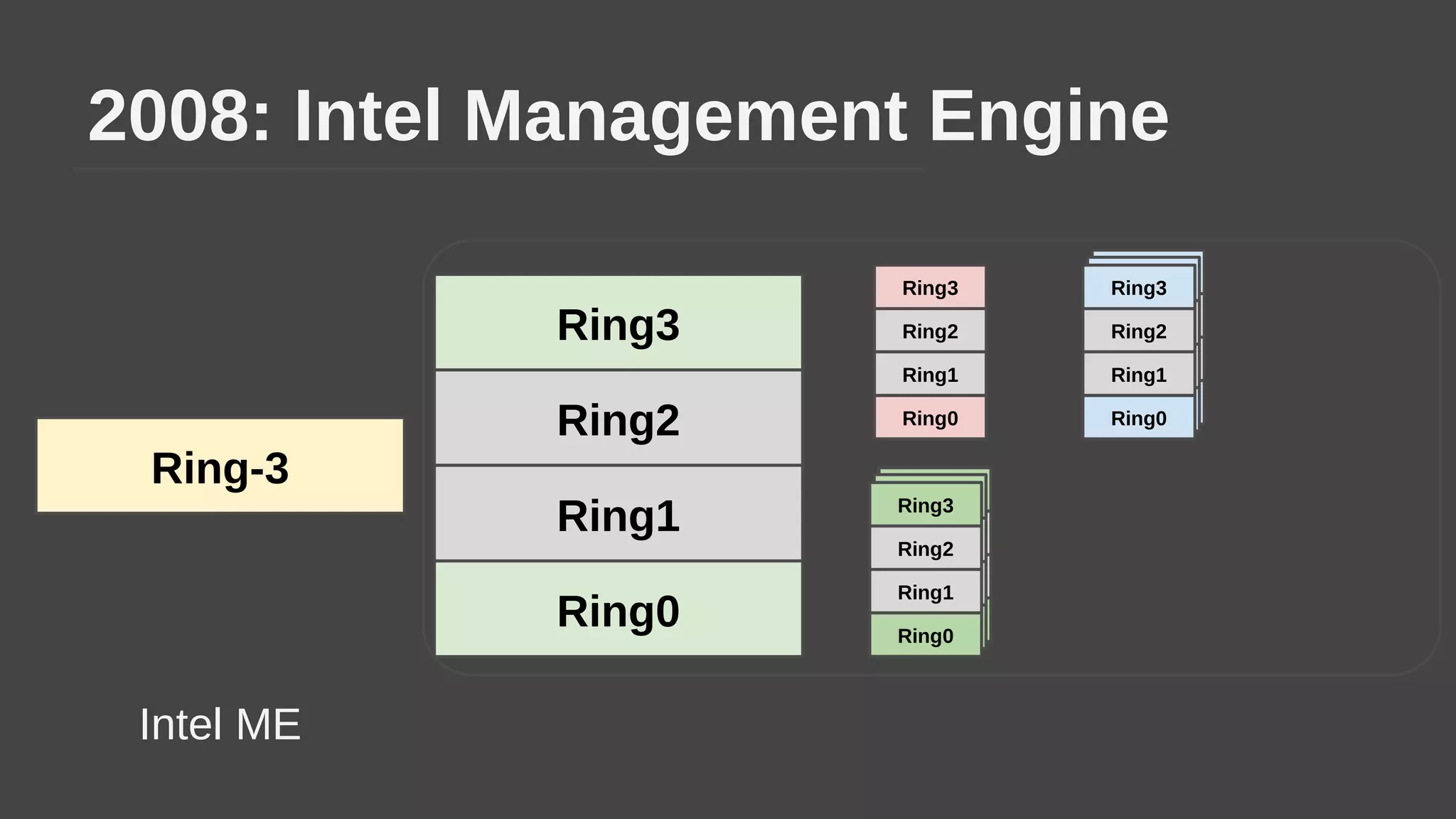
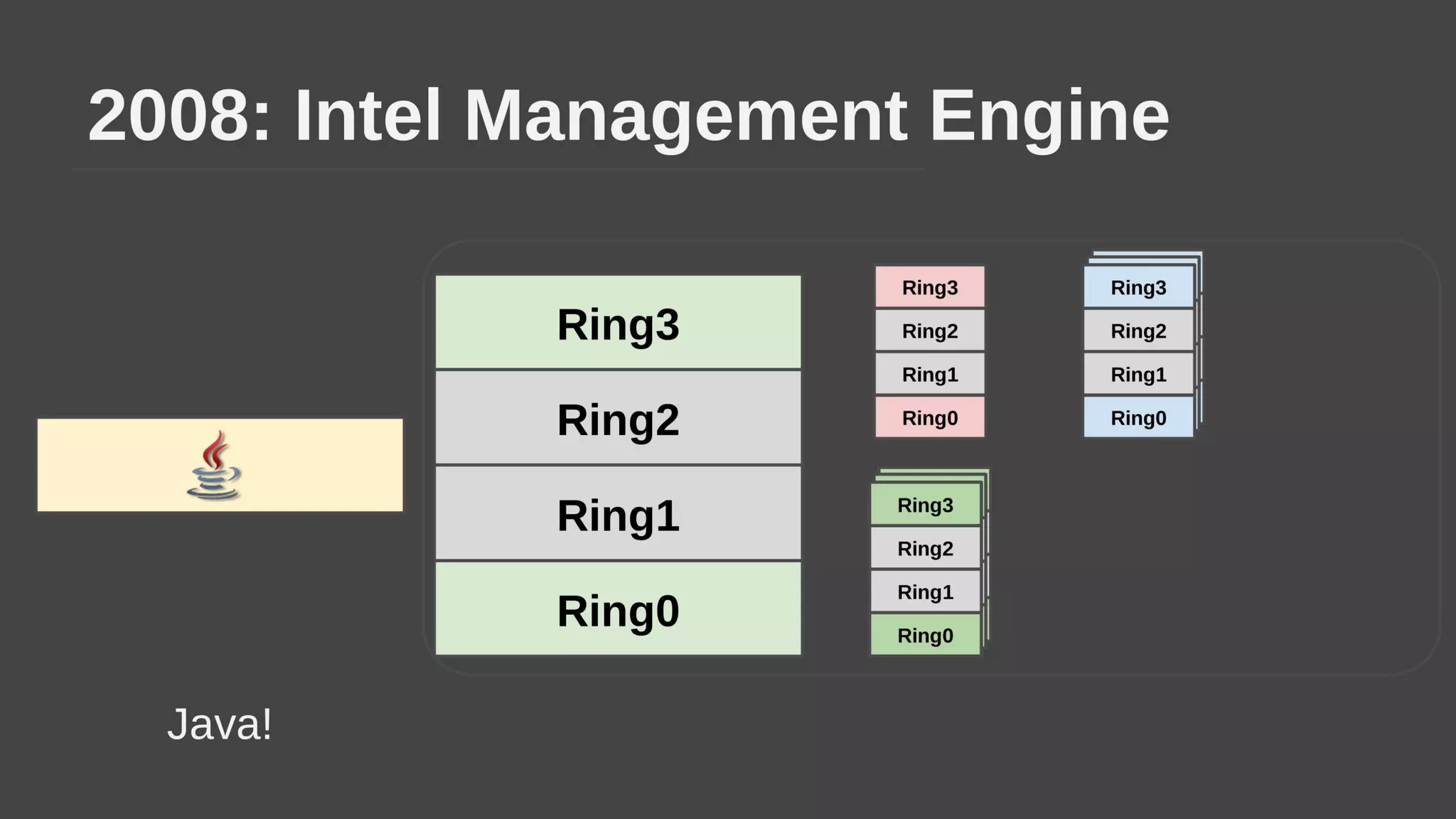
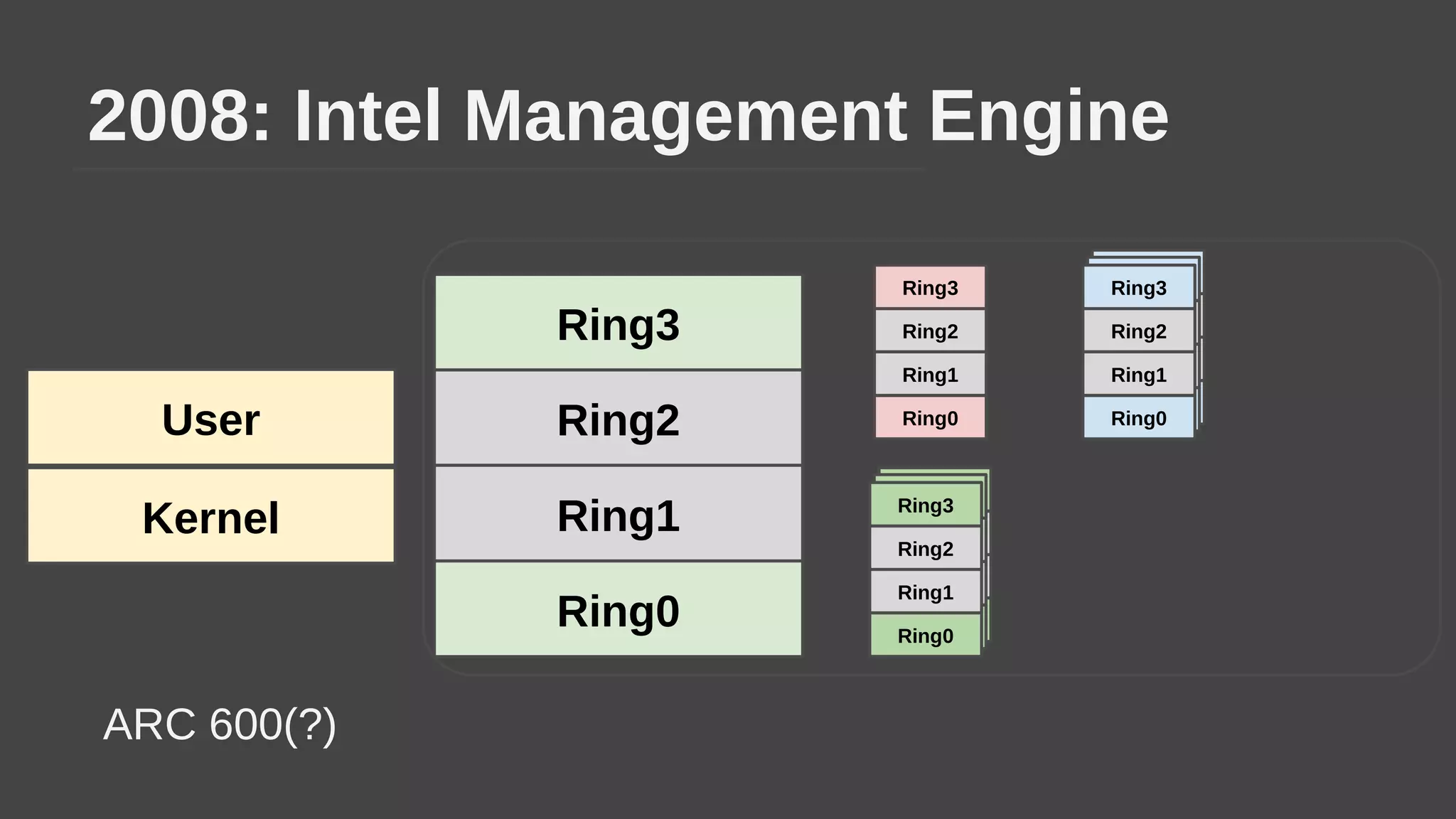
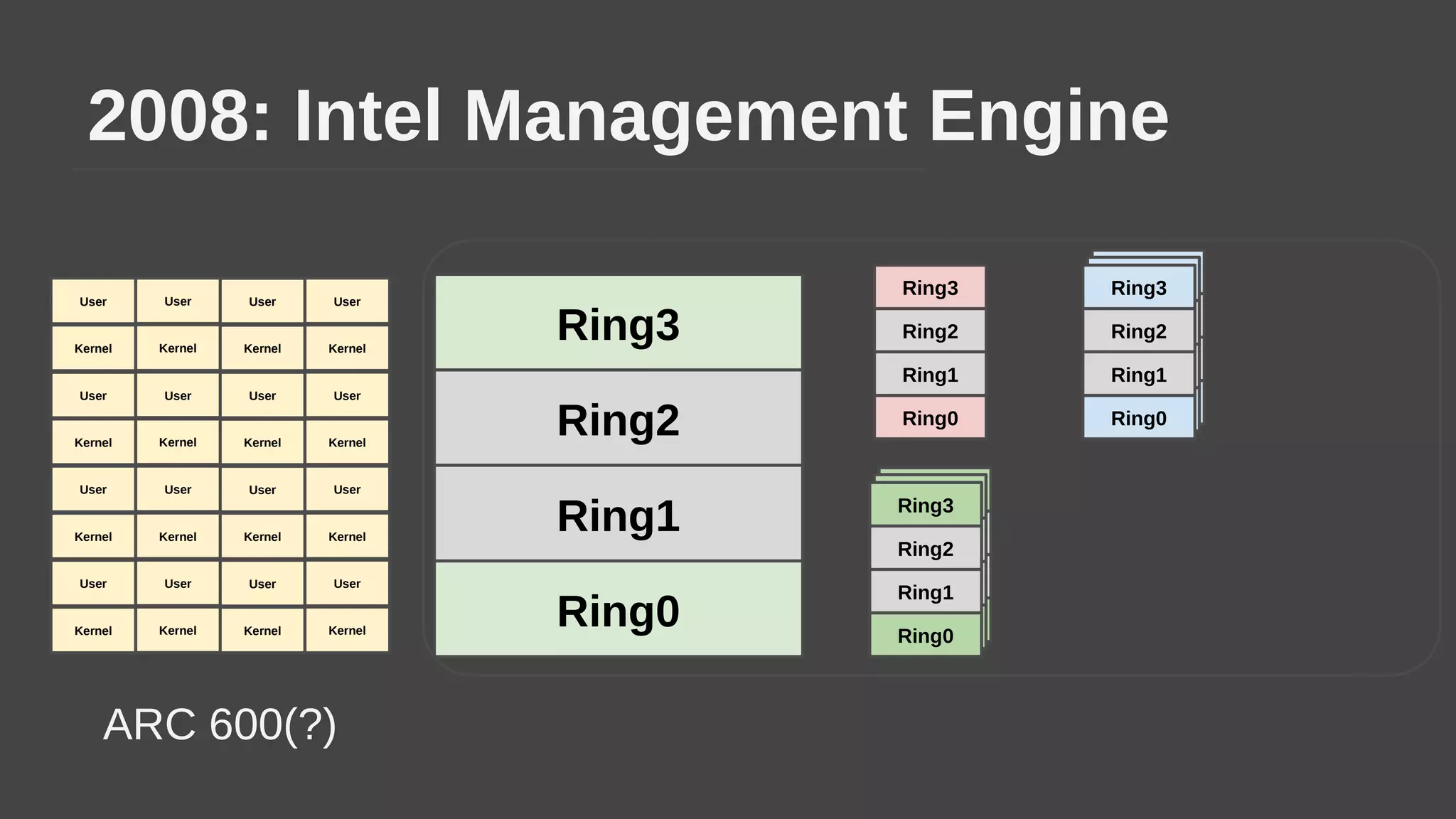
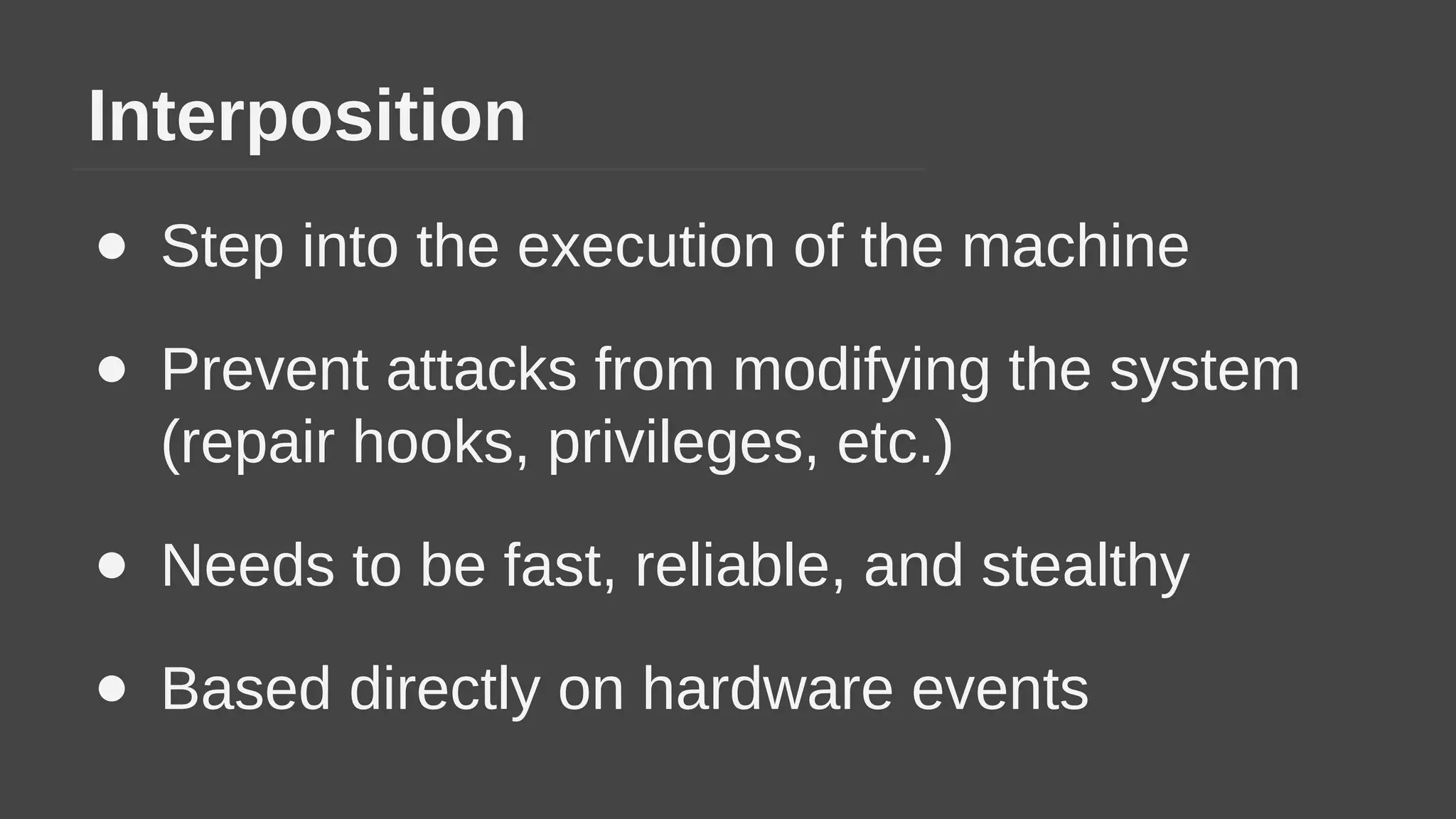
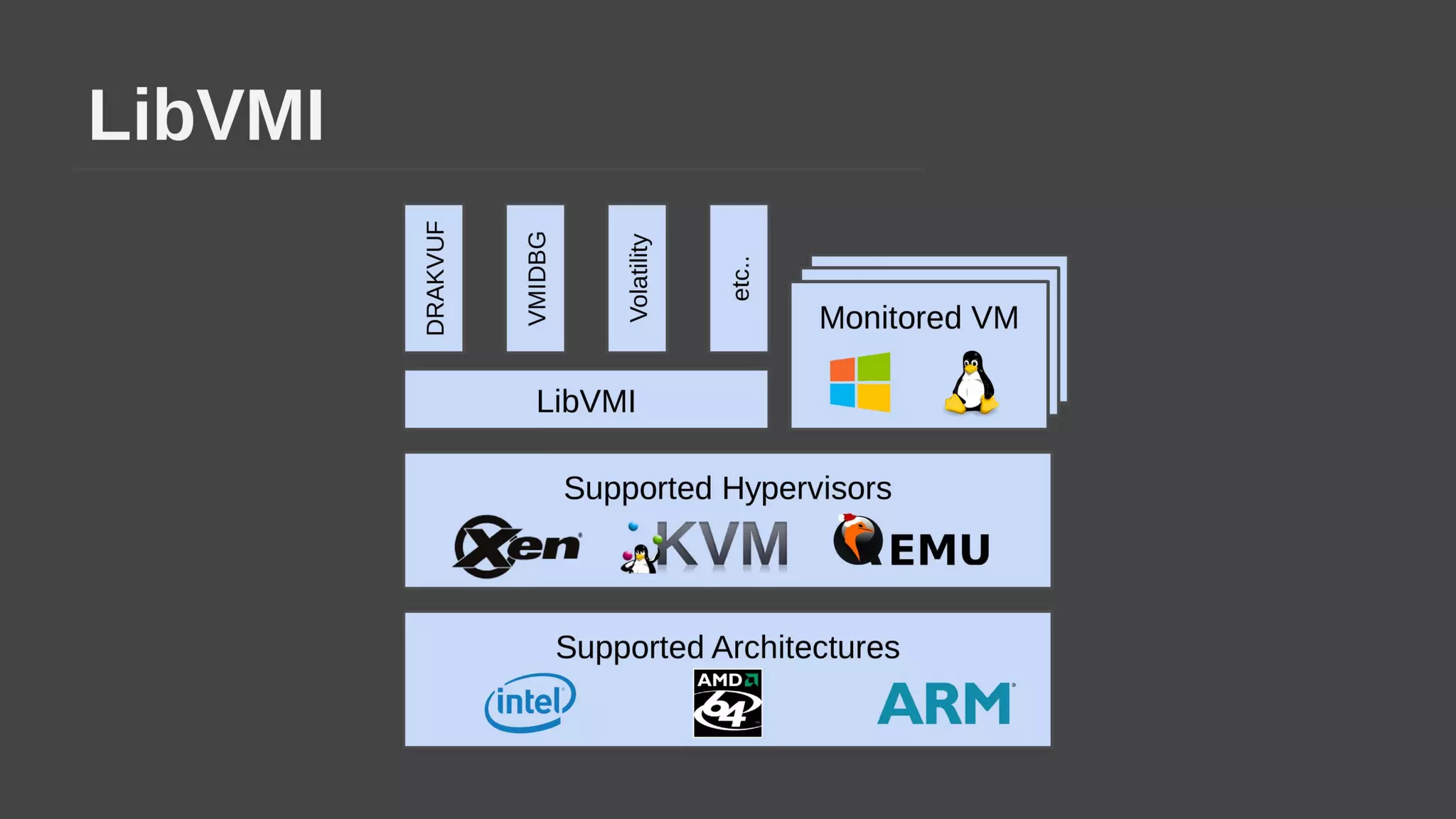
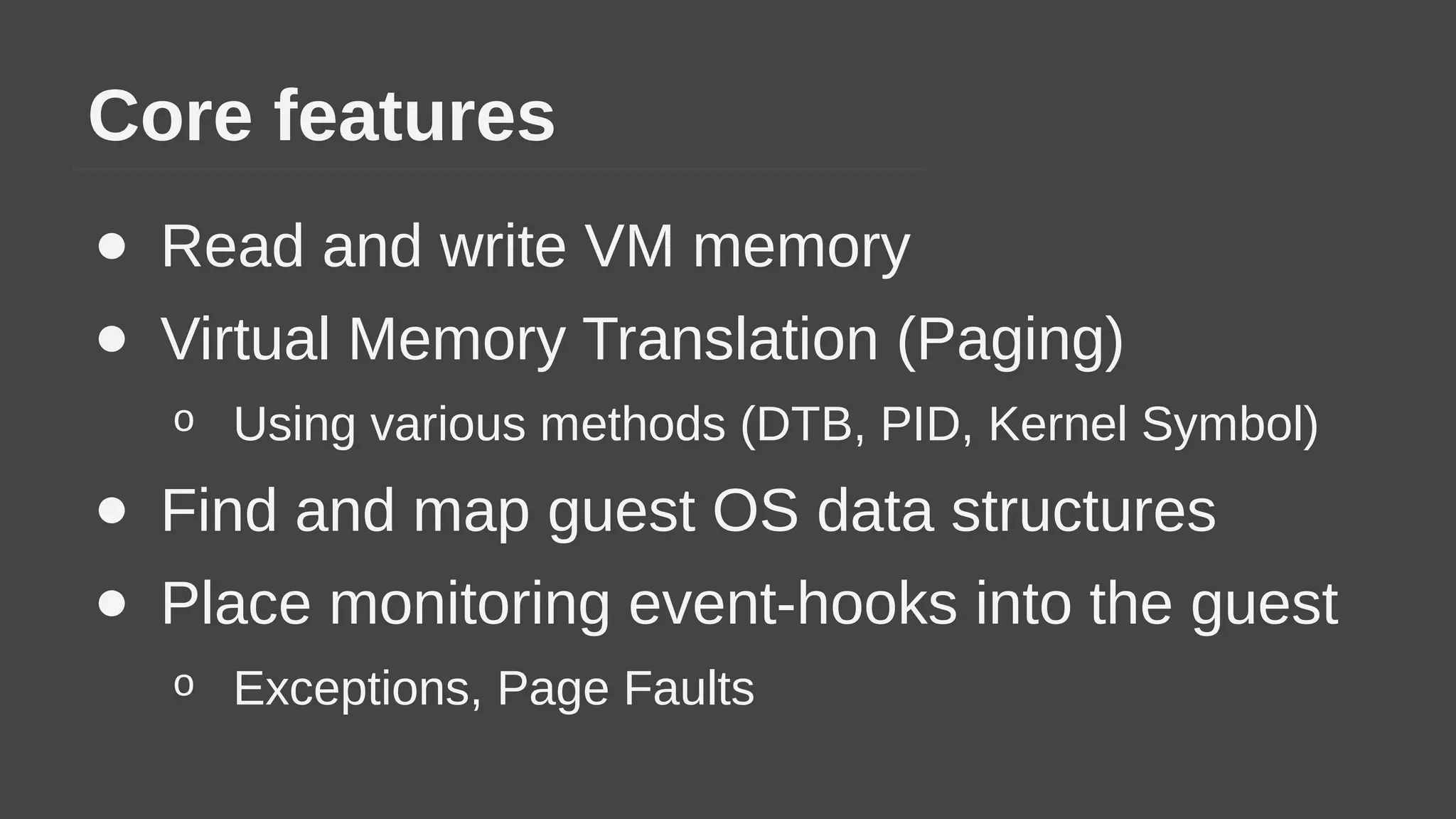
The document provides a brief history of hardware security from 1982 to present day, focusing on developments like protected mode, virtualization with Xen and VT-x/AMD-V, the Intel Management Engine, SGX, and virtual machine introspection (VMI). It discusses the core concepts behind VMI including isolation, interpretation, and interposition. LibVMI is introduced as a tool for VMI that allows monitoring VM memory, translating guest virtual addresses, and placing hooks in the guest. Future directions include more guest OS and hypervisor support as well as new event types.













![Events on Xen with Intel CPUs
● Intel Extended Page Tables (EPT)
● Register write events ([X]CR0/3/4, MSRs)
● Software breakpoint interrupts (INT3)
● Single-stepping (MTF)](https://image.slidesharecdn.com/bigtechdayfinal-150812192925-lva1-app6891/75/Cloud-Security-with-LibVMI-45-2048.jpg)