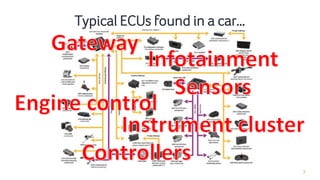
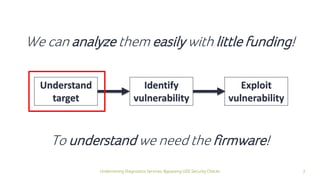
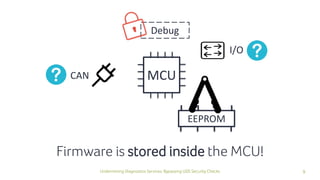
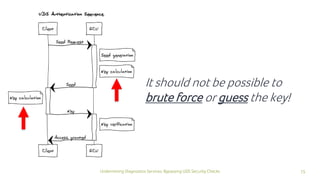
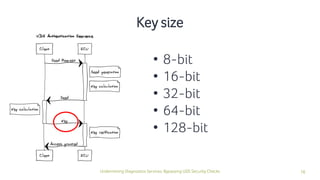
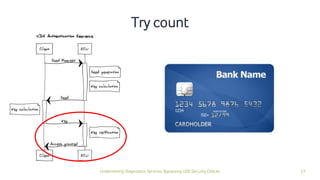
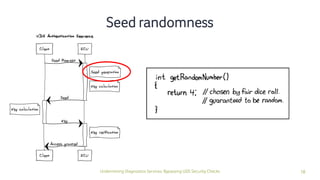
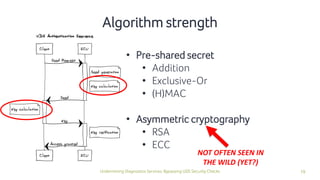
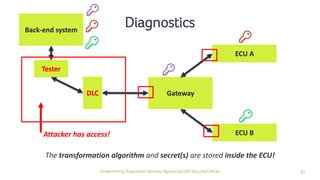
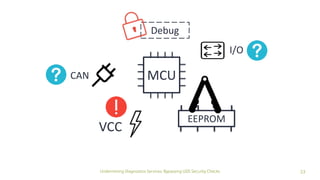
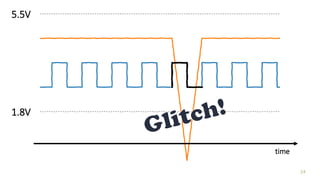
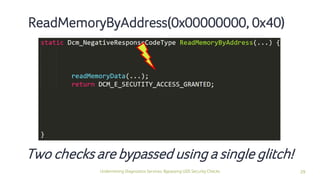
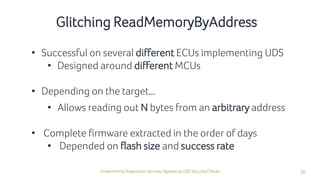
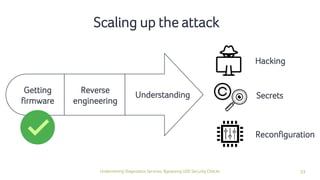
The document discusses how security checks for diagnostics services in vehicles can be bypassed. It describes how fault injection techniques can be used to extract firmware from electronic control units (ECUs), allowing attackers to obtain secrets and reconfigure ECUs. Recommendations are provided for hardening ECUs, such as using secure hardware and asymmetric cryptography instead of pre-shared secrets. The key takeaway is that hardware attacks are scalable and will expose firmware, compromising any pre-shared secrets.