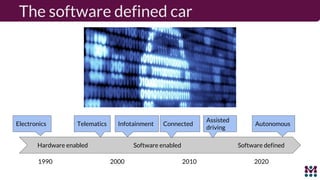
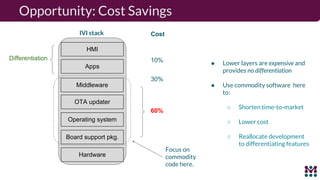
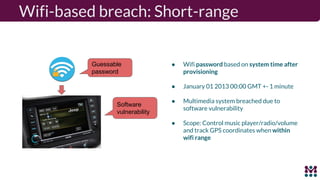
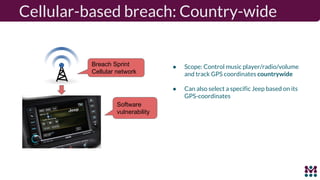
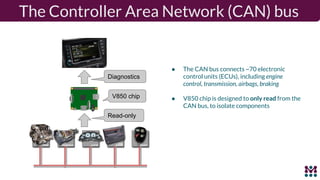
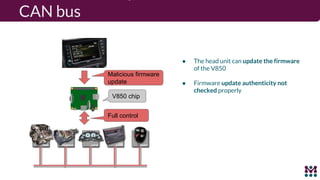
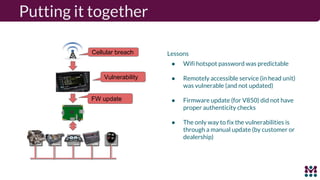
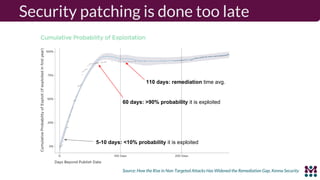
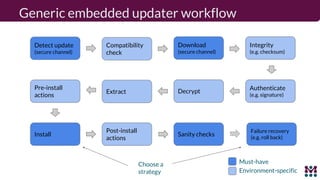
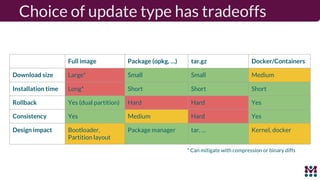
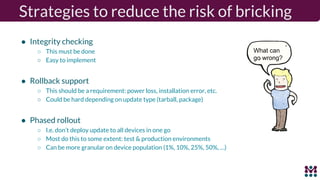
Drew Moseley discussed opportunities and challenges with software-defined connected cars. The connected car brings new revenue opportunities from services but also a larger attack surface. An attack on Jeep Cherokees in 2015 demonstrated safety risks when vehicles cannot be updated remotely. Securing software-defined cars requires over-the-air updates to fix issues, but patching is currently done too late. Moseley's company Mender provides an open source over-the-air updater to help automakers securely manage remote software updates.











![The best way to respond to hacking?
Fiat Chrysler said exploiting the flaw "required
unique and extensive technical knowledge,
prolonged physical access to a subject vehicle and
extended periods of time to write code" and added
manipulating its software "constitutes criminal
action".
Sources: BBC News, Wired
Straubel [Tesla CTO] credits KeenLabs’
researchers [...] says Tesla will pay
KeenLabs’ team a monetary reward for its
work [...] “They did good work,” Straubel says.
“They helped us find something that’s a
problem we needed to fix. And that’s what we
did.”](https://image.slidesharecdn.com/securingtheconnectedcar-scale2018-180309232932/85/Securing-the-Connected-Car-SCaLE-2018-23-320.jpg)