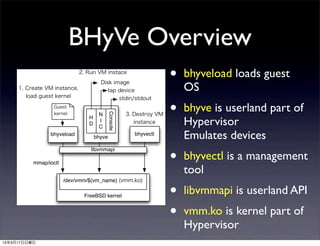
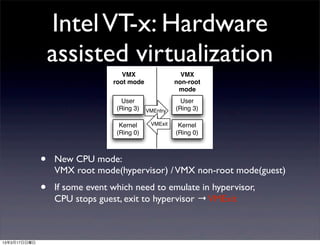
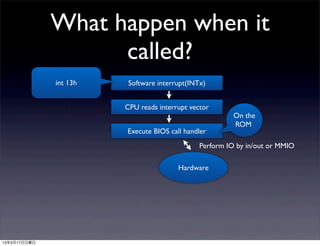
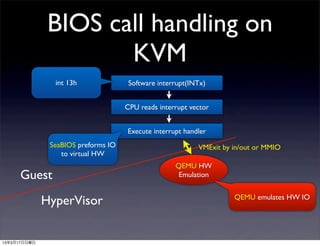
This document discusses implementing BIOS emulation support for BHyVe, the hypervisor component of FreeBSD. It provides an overview of BHyVe's internal structure, including how it uses Intel VT-x hardware-assisted virtualization to run guest virtual machines. It then outlines a project to add BIOS emulation capabilities to BHyVe in order to support booting legacy systems within BHyVe virtual machines, as is done in other hypervisors like KVM through the use of emulated BIOS code. Alternatives and challenges to implementing BIOS emulation for BHyVe are also discussed.






















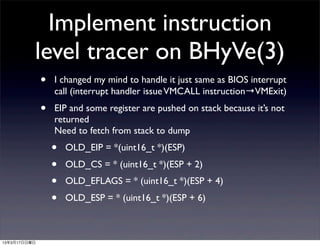
![Instruction level tracer
output
[trace] 16bit ip:7c3e cs:0 flags:102 ss:0 sp:7ffe ds:0 cr0:30 eax:0 ebx:0 ecx:0 edx:80 insn:cld
[trace] 16bit ip:7c3f cs:0 flags:102 ss:0 sp:7ffe ds:0 cr0:30 eax:0 ebx:0 ecx:0 edx:80 insn:xor %cx, %cx
[trace] 16bit ip:7c41 cs:0 flags:146 ss:0 sp:7ffe ds:0 cr0:30 eax:0 ebx:0 ecx:0 edx:80 insn:mov %cx, %es
[trace] 16bit ip:7c43 cs:0 flags:146 ss:0 sp:7ffe ds:0 cr0:30 eax:0 ebx:0 ecx:0 edx:80 insn:mov %cx, %ds
[trace] 16bit ip:7c45 cs:0 flags:146 ss:0 sp:7ffe ds:0 cr0:30 eax:0 ebx:0 ecx:0 edx:80 insn:mov %cx, %ss
[trace] 16bit ip:7c4a cs:0 flags:146 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:0 edx:80 insn:mov %sp, %si
[trace] 16bit ip:7c4c cs:0 flags:146 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:0 edx:80 insn:mov $0x700, %di
[trace] 16bit ip:7c4f cs:0 flags:146 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:0 edx:80 insn:incb %ch
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:100 edx:80 insn:rep movsw
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:ff edx:80 insn:rep movsw
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:fe edx:80 insn:rep movsw
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:fd edx:80 insn:rep movsw
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:fc edx:80 insn:rep movsw
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:fb edx:80 insn:rep movsw
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:fa edx:80 insn:rep movsw
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:f9 edx:80 insn:rep movsw
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:f8 edx:80 insn:rep movsw
[trace] 16bit ip:7c51 cs:0 flags:102 ss:0 sp:7c00 ds:0 cr0:30 eax:0 ebx:0 ecx:f7 edx:80 insn:rep movsw
13年3月17日日曜日](https://image.slidesharecdn.com/implementsbiosemulationsupportforbhyve-130316223518-phpapp01/85/Implements-BIOS-emulation-support-for-BHyVe-32-320.jpg)




![BTX interrupt call
causes exception
[trace] 32bit-kern eip:9332 cs:18 eflags:106 ss:10 esp:17b8 ds:10 cr0:31 eax:31
ebx:9357 ecx:0 edx:70000 insn:decb %al
[trace] 32bit-kern eip:9334 cs:18 eflags:106 ss:10 esp:17b8 ds:10 cr0:31 eax:30
ebx:9357 ecx:0 edx:70000 insn:mov %eax, %cr0
[trace] 32bit-kern eip:9097 cs:8 eflags:146 ss:0 esp:1800 ds:0 cr0:31 eax:102
ebx:2820 ecx:0 edx:708ee insn:mov $0x10, %cl
[trace] 32bit-kern eip:9099 cs:8 eflags:146 ss:0 esp:1800 ds:0 cr0:31 eax:102
ebx:2820 ecx:10 edx:708ee insn:mov %ecx, %ss
[trace] 32bit-kern eip:909d cs:8 eflags:146 ss:10 esp:1800 ds:0 cr0:31 eax:102
ebx:2820 ecx:38 edx:708ee insn:ltr %cx
[except] 32bit-kern exception:13 error_code:38 eip:909d cs:8 eflags:10146 ss:
10 esp:1800 insn:ltr %cx ds:0 cr0:31 eax:102 ebx:2820 ecx:38 edx:708ee
• INT 0x31 (BIOS call from BTX app) causes an exception at LTR instruction
• I Have no idea... → Tried to skips all BIOS call on boot2 & loader, use in/out
13年3月17日日曜日](https://image.slidesharecdn.com/implementsbiosemulationsupportforbhyve-130316223518-phpapp01/85/Implements-BIOS-emulation-support-for-BHyVe-37-320.jpg)
![rep causes exception in
loader
[trace] 32bit-kern eip:2000c4 cs:8 eflags:10106 ss:10 esp:ffc ds:10 cr0:31
eax:a0200 ebx:201000 ecx:52f edx:50000a insn:rep movsb
[trace] 32bit-kern eip:2000c4 cs:8 eflags:10106 ss:10 esp:ffc ds:10 cr0:31
eax:a0200 ebx:201000 ecx:52e edx:50000a insn:rep movsb
[trace] 32bit-kern eip:2000c4 cs:8 eflags:10106 ss:10 esp:ffc ds:10 cr0:31
eax:a0200 ebx:201000 ecx:52d edx:50000a insn:rep movsb
[trace] 32bit-kern eip:2000c4 cs:8 eflags:10106 ss:10 esp:ffc ds:10 cr0:31
eax:a0200 ebx:201000 ecx:52c edx:50000a insn:rep movsb
[trace] 32bit-kern eip:2000c4 cs:8 eflags:10106 ss:10 esp:ffc ds:10 cr0:31
eax:a0290 ebx:201000 ecx:52b edx:50000a insn:rep movsb
[trace] 32bit-kern eip:2000c4 cs:8 eflags:10106 ss:10 esp:ffc ds:10 cr0:31
eax:a027b ebx:201000 ecx:52a edx:50000a insn:rep movsb
[except] 32bit-kern exception:3 error_code:0 eip:2000c4 cs:8 eflags:10106 ss:10
esp:ffc insn:rep movsb ds:10 cr0:31 eax:a0236 ebx:201000 ecx:529 edx:50000a
• Really haven’t good idea...
13年3月17日日曜日](https://image.slidesharecdn.com/implementsbiosemulationsupportforbhyve-130316223518-phpapp01/85/Implements-BIOS-emulation-support-for-BHyVe-38-320.jpg)

