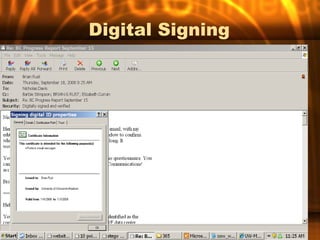
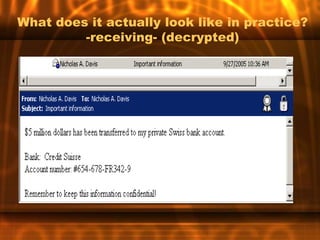
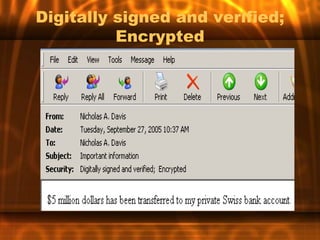
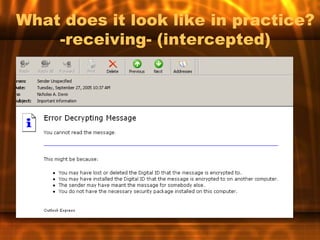
This document outlines the key topics and objectives covered in an introduction to e-commerce course. It discusses the system development lifecycle, software and platform selection, e-commerce tools, security threats and payment systems. Assignments include analyzing case studies, websites, internet service providers and developing an action plan for an e-commerce paper. The instructor discusses best practices for analysis, design, testing, implementation and payment systems in e-commerce.