Embed presentation
Downloaded 16 times


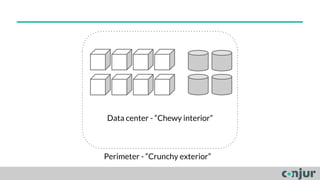
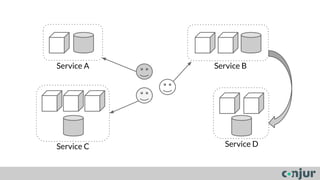
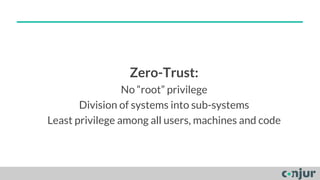




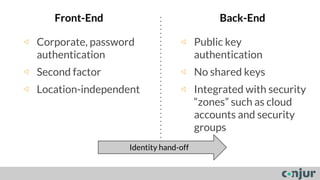
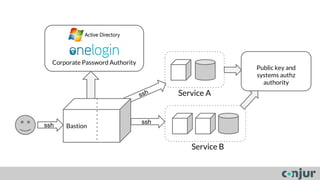




The document discusses zero-trust server management as an alternative to traditional server access management using Active Directory and VPN. Zero-trust involves dividing systems into sub-systems with least privilege access for all users, machines, and code. It also recommends using public key authentication and bastion hosts to create security zones for access to servers rather than relying on Active Directory in cloud environments.















