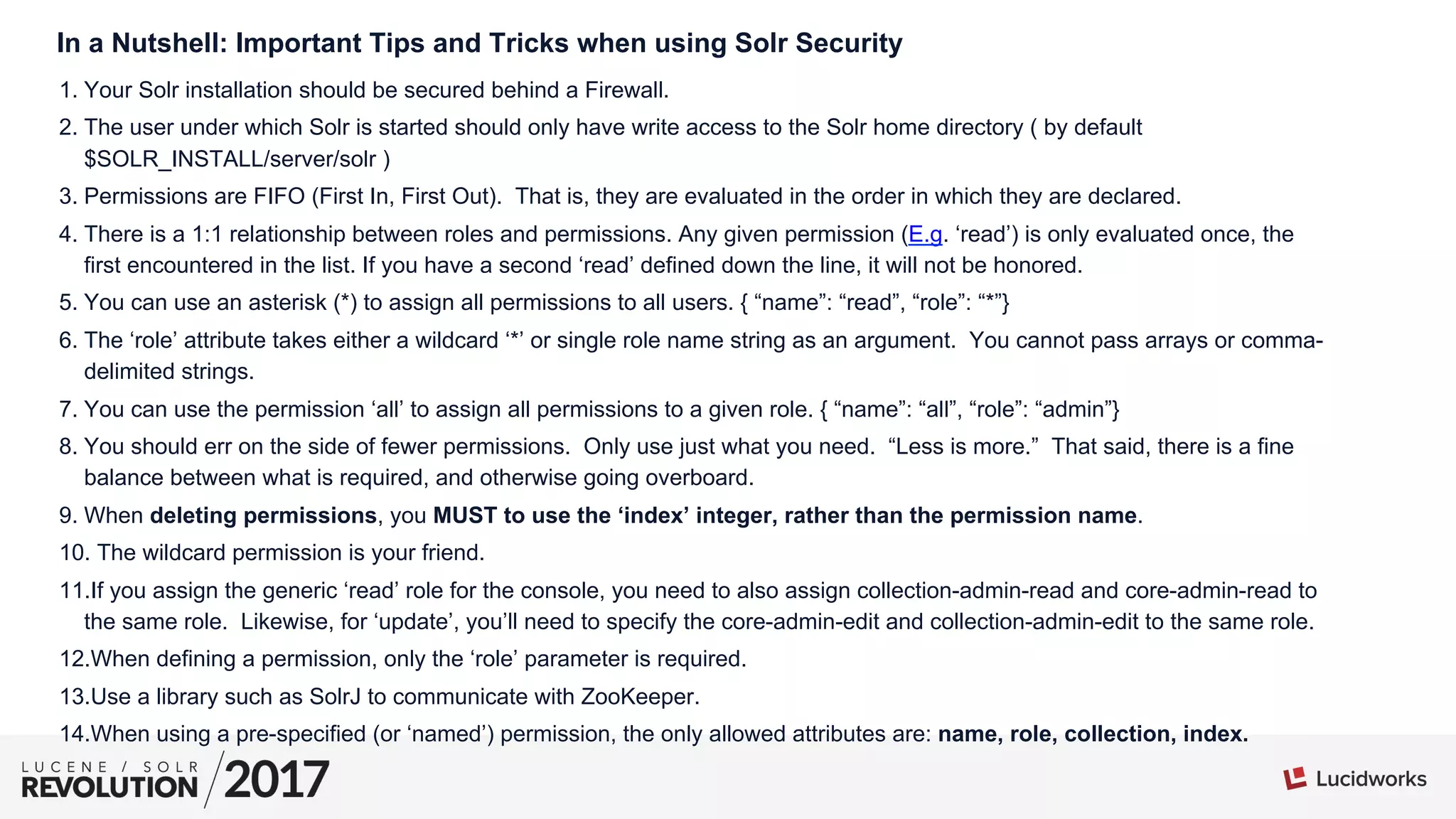
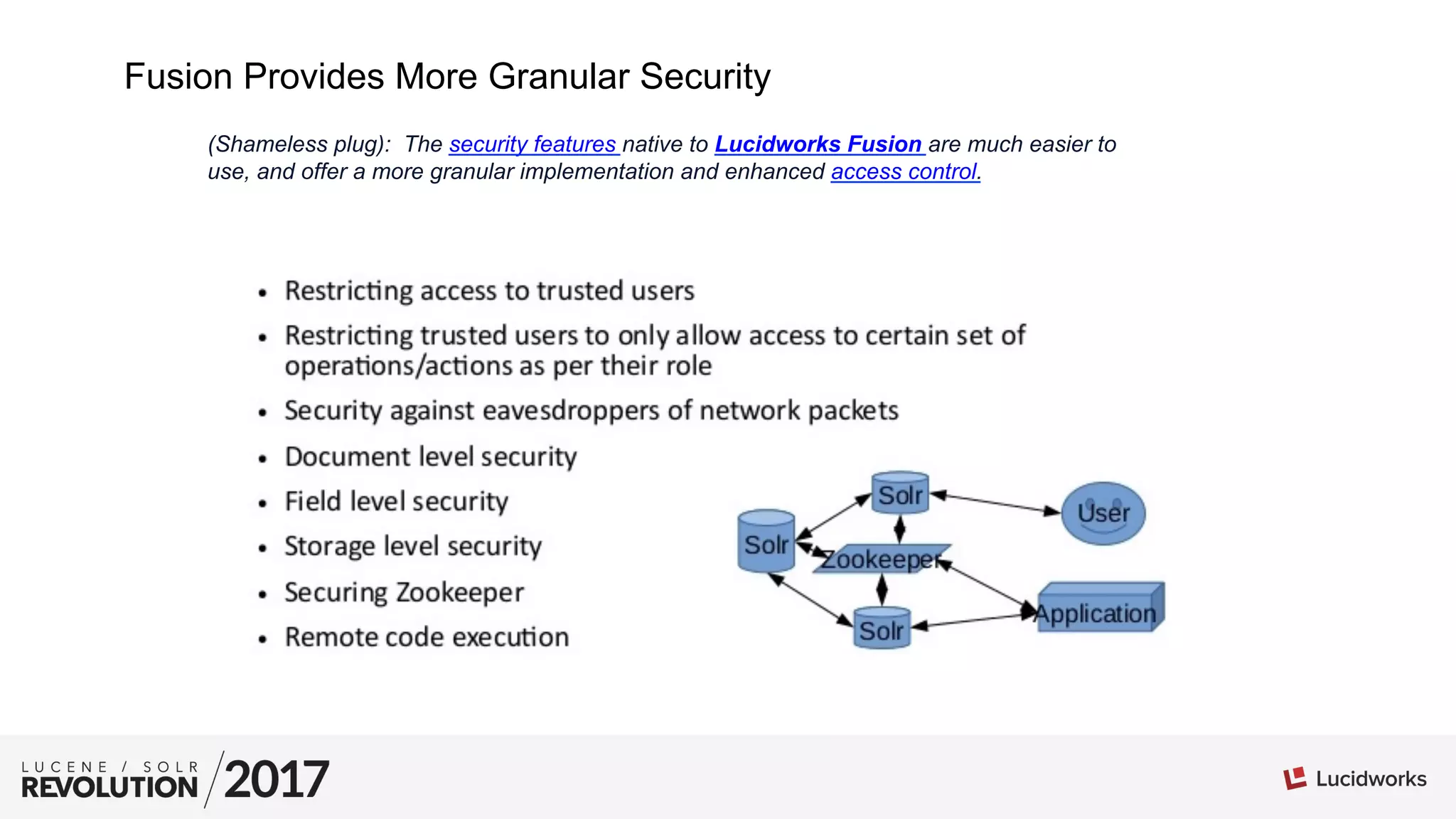
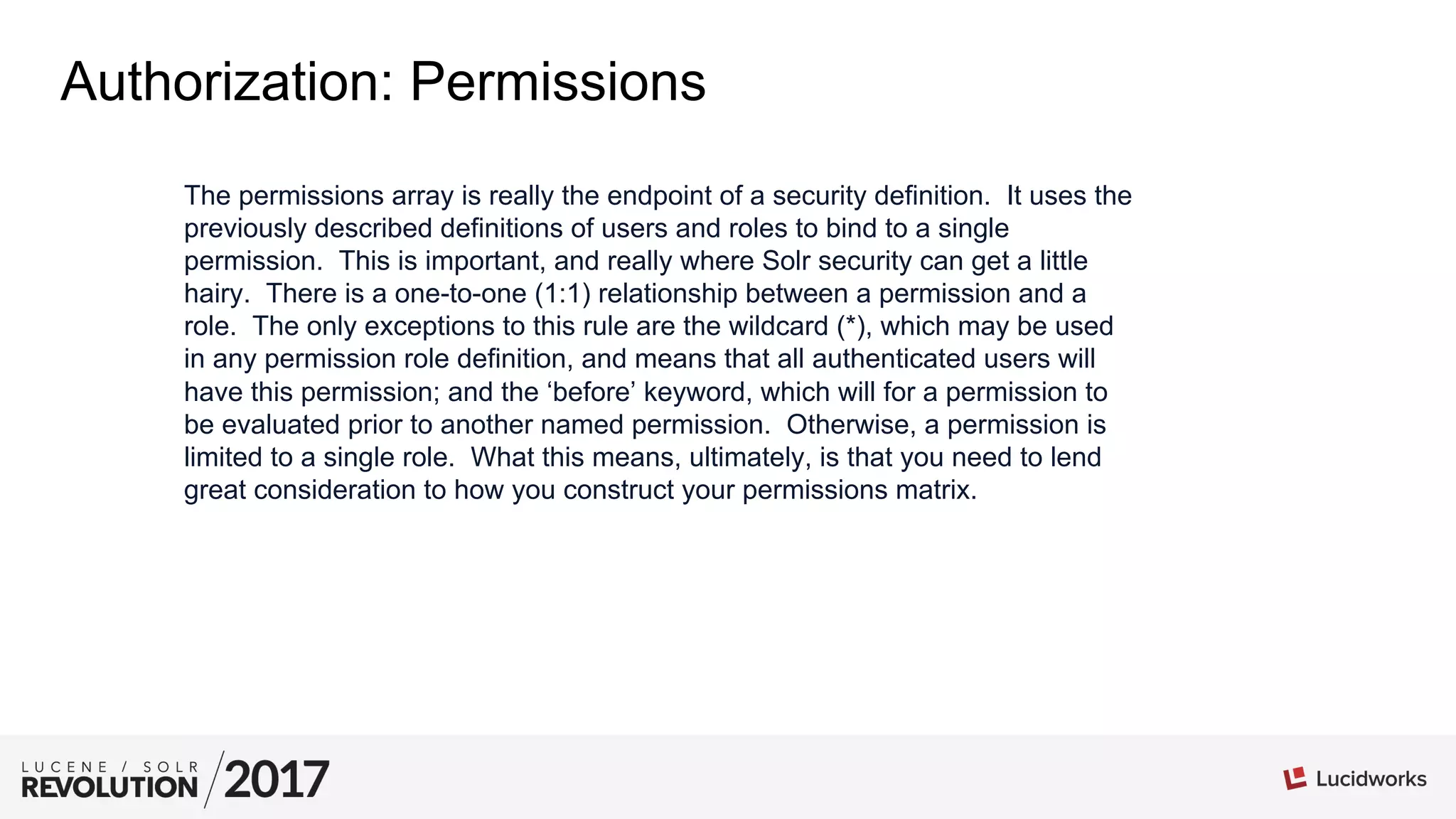
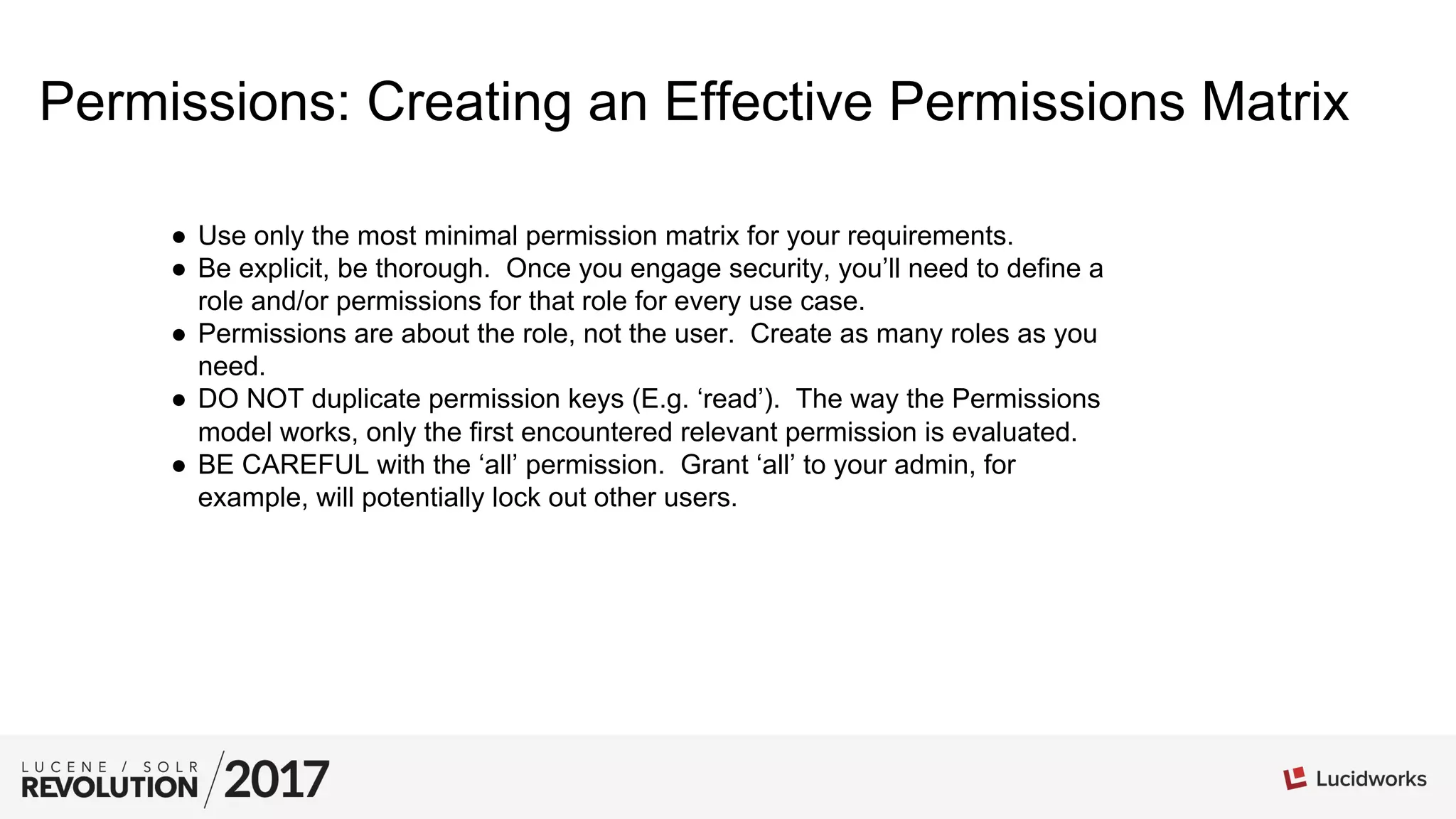
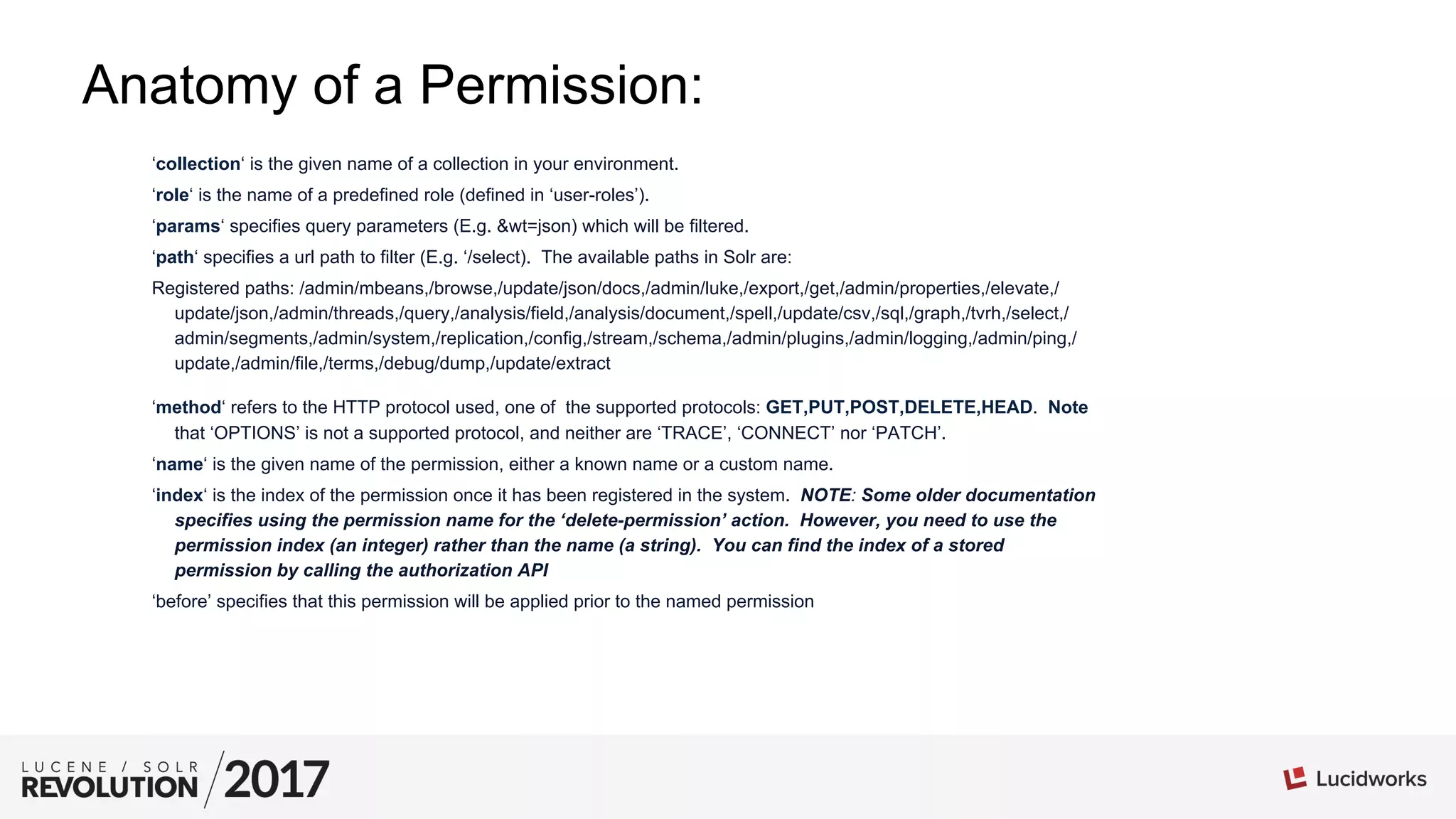
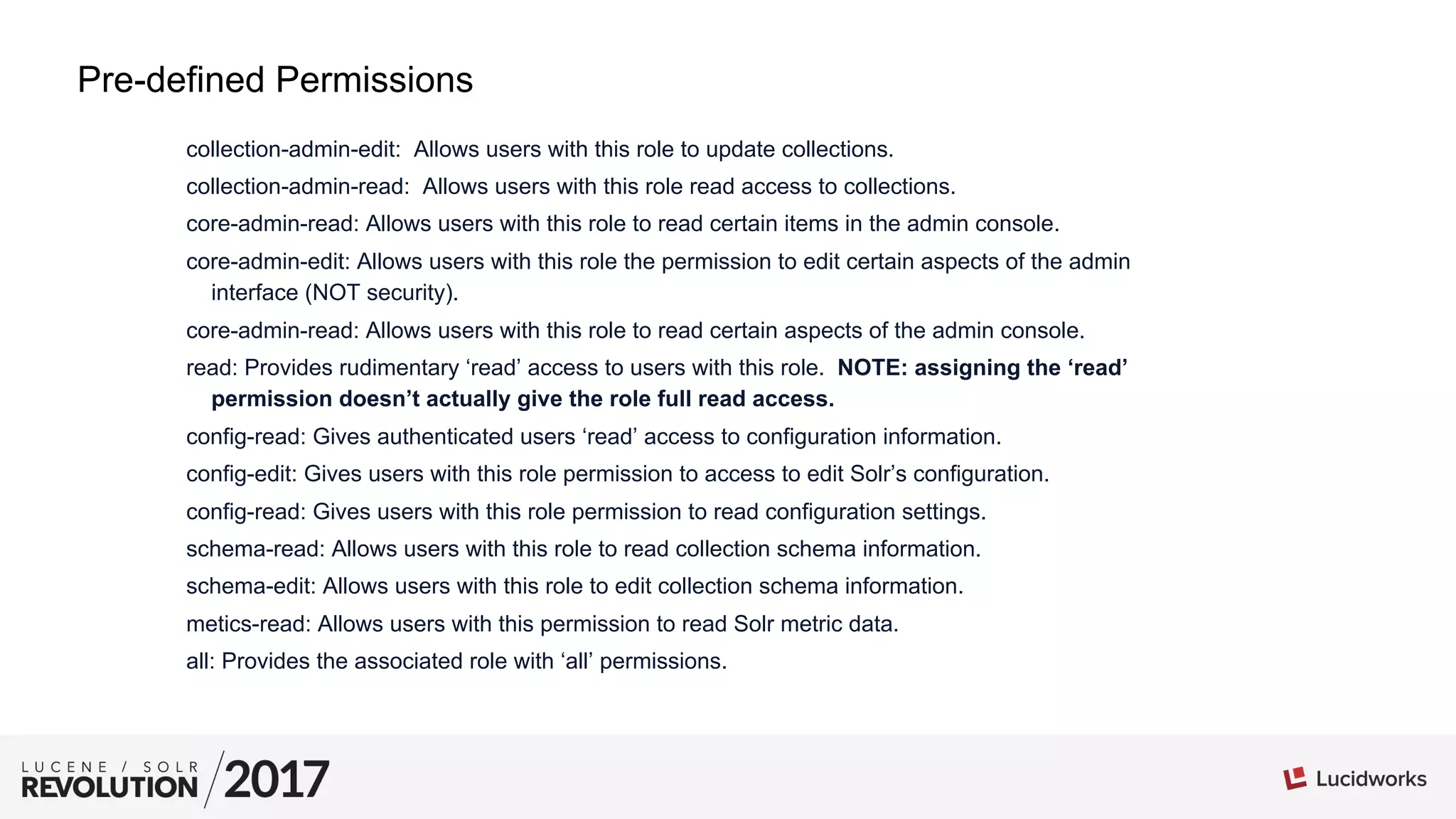
The document provides tips and best practices for securing Apache Solr installations. It discusses authentication using BasicAuthPlugin and authorization using RuleBasedAuthorizationPlugin. Key points include: defining roles and permissions in the security.json file; the relationship between roles, permissions, and users; creating an effective permission matrix; and troubleshooting permission issues. The document emphasizes maintaining the security.json file, using minimal necessary permissions, and considering the order that permissions are evaluated.



![A Sample Security JSON File:
{
"authorization": {
"class": "solr.RuleBasedAuthorizationPlugin",
"permissions": [{
"role": "*",
"name": "collection-admin-read",
"index": 1
}, {
"path": "/select",
"role": "admin",
"before": "collection-admin-read",
"name": "secure-collection1-permission",
"index": 2,
"collection": "securecollection"
}, {
"role": "*",
"name": "read",
"index": 3
}, {
"role": "admin",
"name": "collection-admin-edit",
"index": 4
}],
"user-role": {
"foobar": "[dev, foobrole]",
"solr": "admin",
"devuser": "dev"
}
},
"authentication": {
"class": "solr.BasicAuthPlugin",
"credentials": {
"solr": "IV0EHq1OnNrj6gvRCwvFwTrZ1+z1oBbnQdiVC3otuq0= Ndd7LKvVBAaZIF0QAVi1ekCfAJXr1GGfLtRUXhgrF8c=",
"testuser": "7oBNYcOwAY1WHlUHqrXtHPxxNKxk2FHy+dBZQiK09Lc= 81G4YPKSOQcHXdM65rh+as41qWSqiYd9Xh+Xe5eNJ1s=",
"devuser": "IV0EHq1OnNrj6gvRCwvFwTrZ1+z1oBbnQdiVC3otuq0= Ndd7LKvVBAaZIF0QAVi1ekCfAJXr1GGfLtRUXhgrF8c="
}
}
}](https://image.slidesharecdn.com/kevincowansteveharrisrev-2017-171004173608/75/Solr-Security-Tips-and-Tricks-and-Things-You-Really-Ought-to-Know-Kevin-Cowan-Steve-Harris-Lucidworks-6-2048.jpg)

![Custom Authentication: Rolling Your Own
It is also possible to specify your own Authorization class in your security.json config:
"authorization":{
"class":"package.to.class.that.implements.plugin",
"permissions":[{"name":"security-edit",
"role":"admin"}]
"user-role":{"solr":"admin"}
}
You’ll want to implement the class using the following interfaces:
implements AuthorizationPlugin,ConfigEditablePlugin,SpecProvider](https://image.slidesharecdn.com/kevincowansteveharrisrev-2017-171004173608/75/Solr-Security-Tips-and-Tricks-and-Things-You-Really-Ought-to-Know-Kevin-Cowan-Steve-Harris-Lucidworks-11-2048.jpg)

![Troubleshooting Permissions
Security implementations are, more often than not, very difficult to troubleshoot. Often these
implementations don’t provide cogent error messages, or worse, no message at all. Such is not
the case with Solr. Solr returns a 403 ‘Unauthroized’ error in general. However, if you upload a
security.json that doesn’t behave the way you would expect, go to your solr.log file, and look for
error messages. They will be your best friends in debugging a Solr permission matrix. Here are
some common errors:
No Authorized User:
2017-03-08 15:47:55.876 INFO (qtp1348949648-16) [ ] o.a.s.s.HttpSolrCall USER_REQUIRED
auth header null context : [FAILED toString()]
Invalid Role:
“role”:”admin”}, The principal [principal: devuser] does not have the right role
This will be your most common exception when dealing with user permissions!](https://image.slidesharecdn.com/kevincowansteveharrisrev-2017-171004173608/75/Solr-Security-Tips-and-Tricks-and-Things-You-Really-Ought-to-Know-Kevin-Cowan-Steve-Harris-Lucidworks-17-2048.jpg)