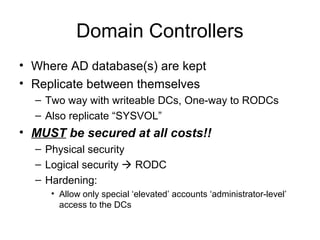
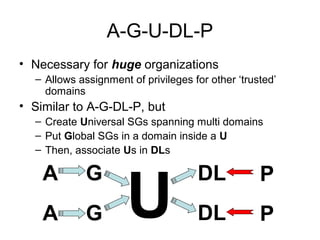
The document provides an overview of Active Directory including key elements such as domain controllers, the schema, security groups, SYSVOL, group policy objects, sites and subnets. It discusses features of Active Directory such as authentication, privileges, policies, auditing, replication, and trust relationships. It also describes important Active Directory elements in more detail including the roles of domain controllers, importance of the schema, best practices for assigning security groups and permissions, and functions of SYSVOL and group policy objects.