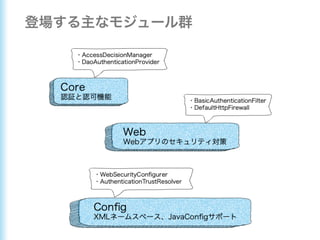
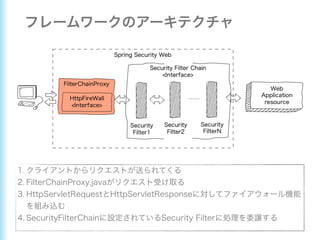
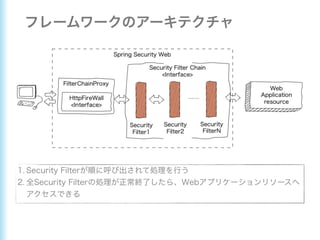
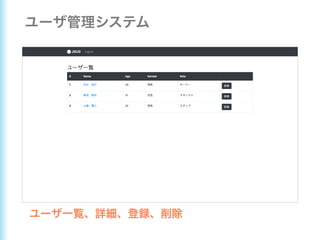
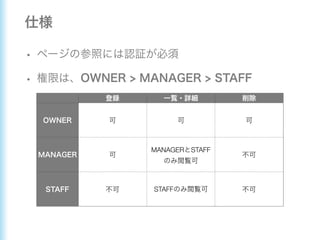
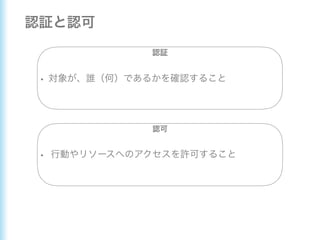
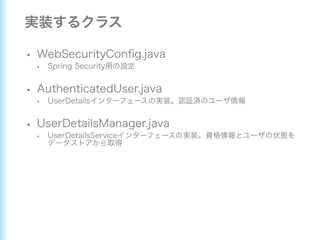
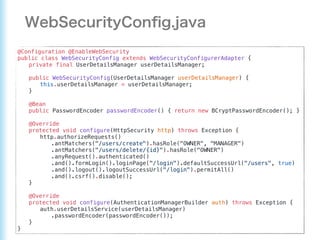
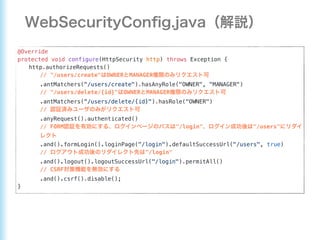
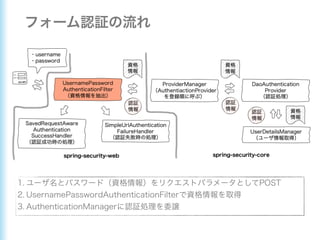
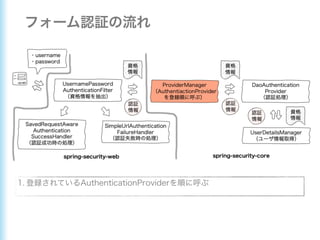
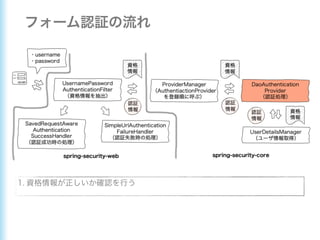
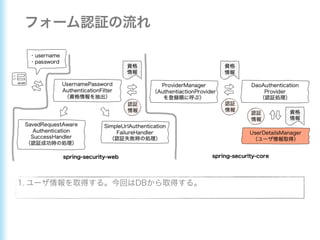
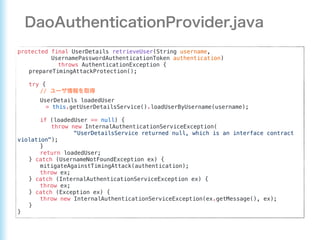
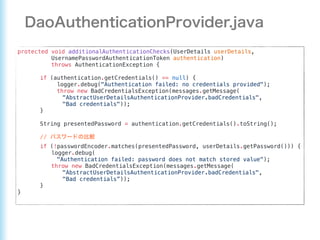
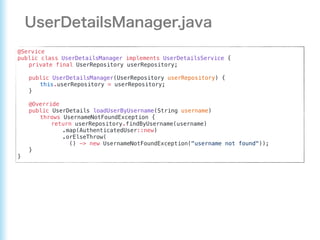
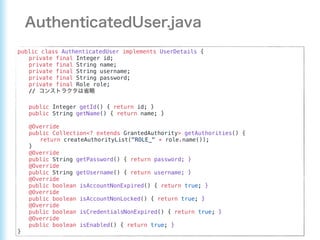
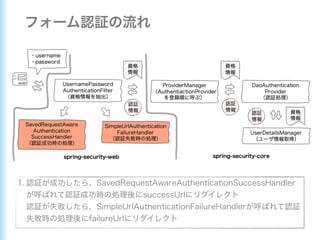
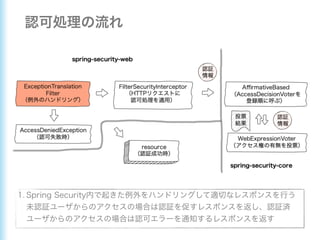
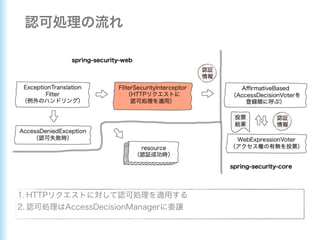
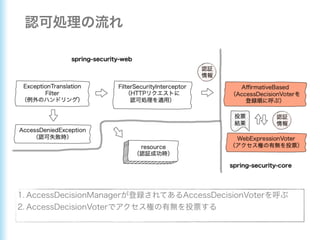
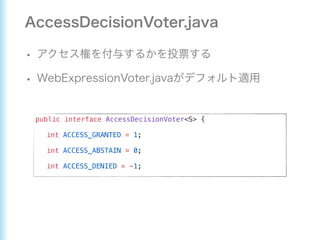
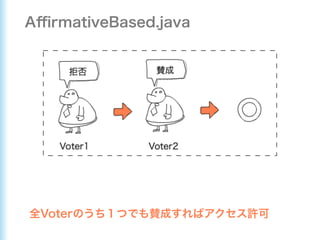
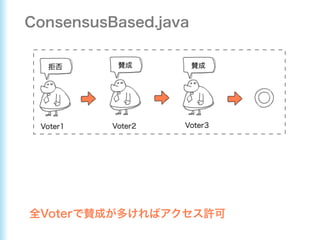
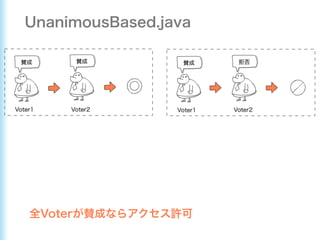
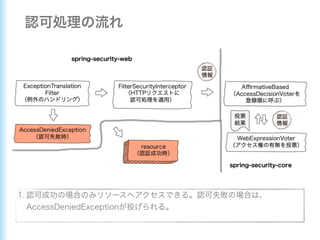
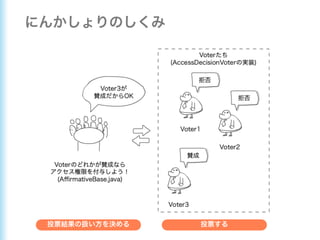
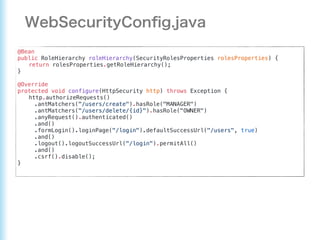
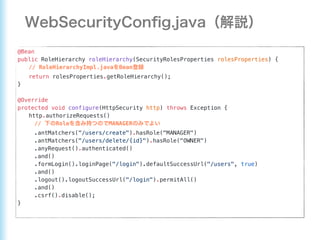
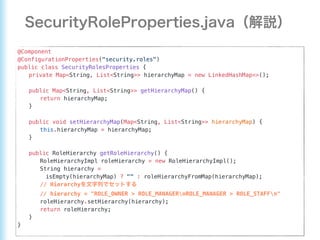
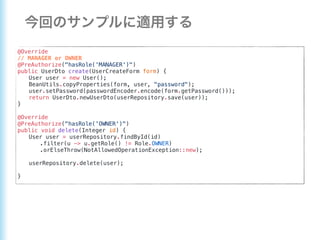
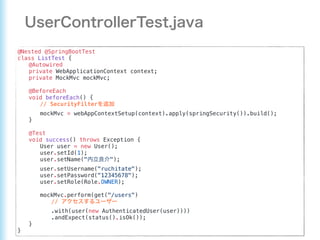
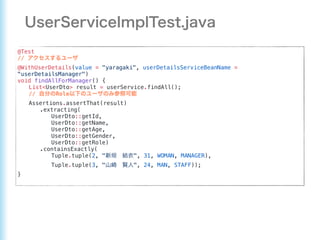
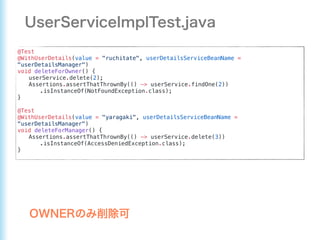
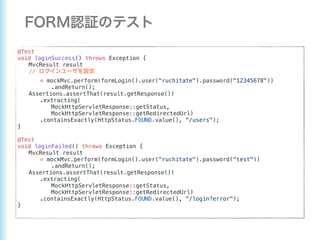
This document describes how to configure Spring Security for authentication and authorization in a web application. It defines a WebSecurityConfig class that configures HTTP security with roles like OWNER and MANAGER for access control. It also defines a UserDetailsManager service for loading users and a User entity class implementing UserDetails. Tests are shown for security configuration, login, access control and more using Spring Security's test utilities.