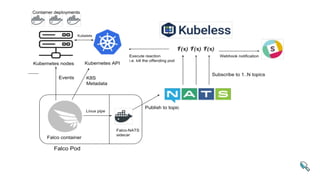
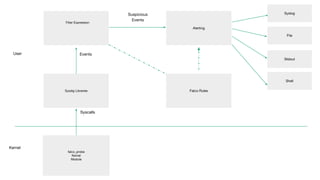
Néstor Salceda, an integrations engineer at Sysdig, discussed implementing active security with Sysdig Falco during a meetup in Barcelona on September 27, 2018. The presentation covered the layers of container security, including vulnerability management, anomaly detection, and behavioral activity monitoring using configurable rules. Salceda emphasized the importance of proactive security measures in the ephemeral container environment and invited contributions to the open-source project.











![Rules
- macro: bin_dir
condition: fd.directory in (/bin, /sbin, /usr/bin, /usr/sbin)
- list: shell_binaries
items: [bash, csh, ksh, sh, tcsh, zsh, dash]
- rule: write_binary_dir
desc: an attempt to write to any file below a set of binary directories
condition: bin_dir and evt.dir = < and open_write and not package_mgmt_procs
output: "File below a known binary directory opened for writing (user=%user.name
command=%proc.cmdline file=%fd.name)"
priority: WARNING](https://image.slidesharecdn.com/implementingactivesecuritywithsysdigfalco-181001161011/85/Implementing-Active-Security-with-Sysdig-Falco-Docker-Meetup-Barcelona-13-320.jpg)