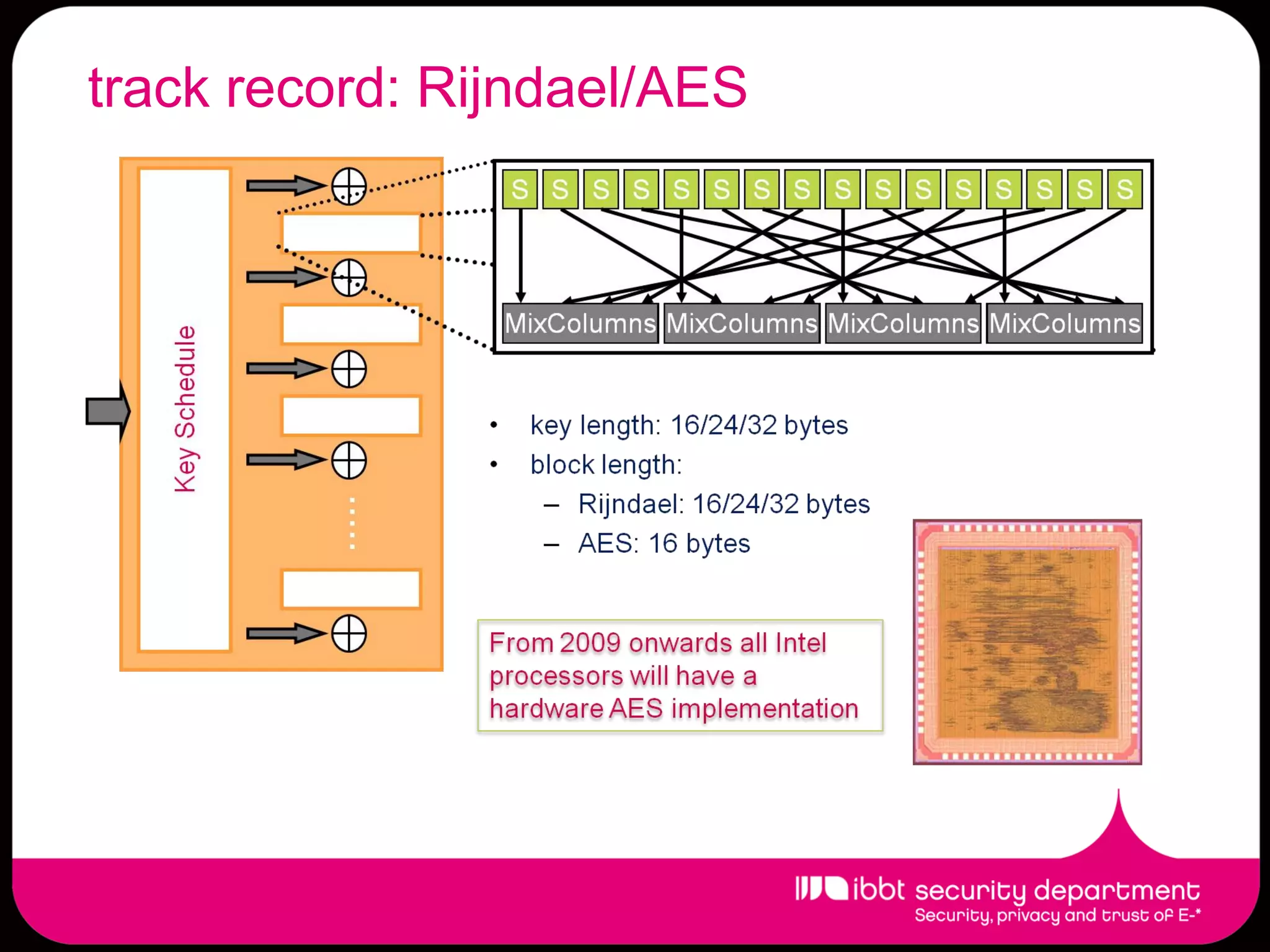
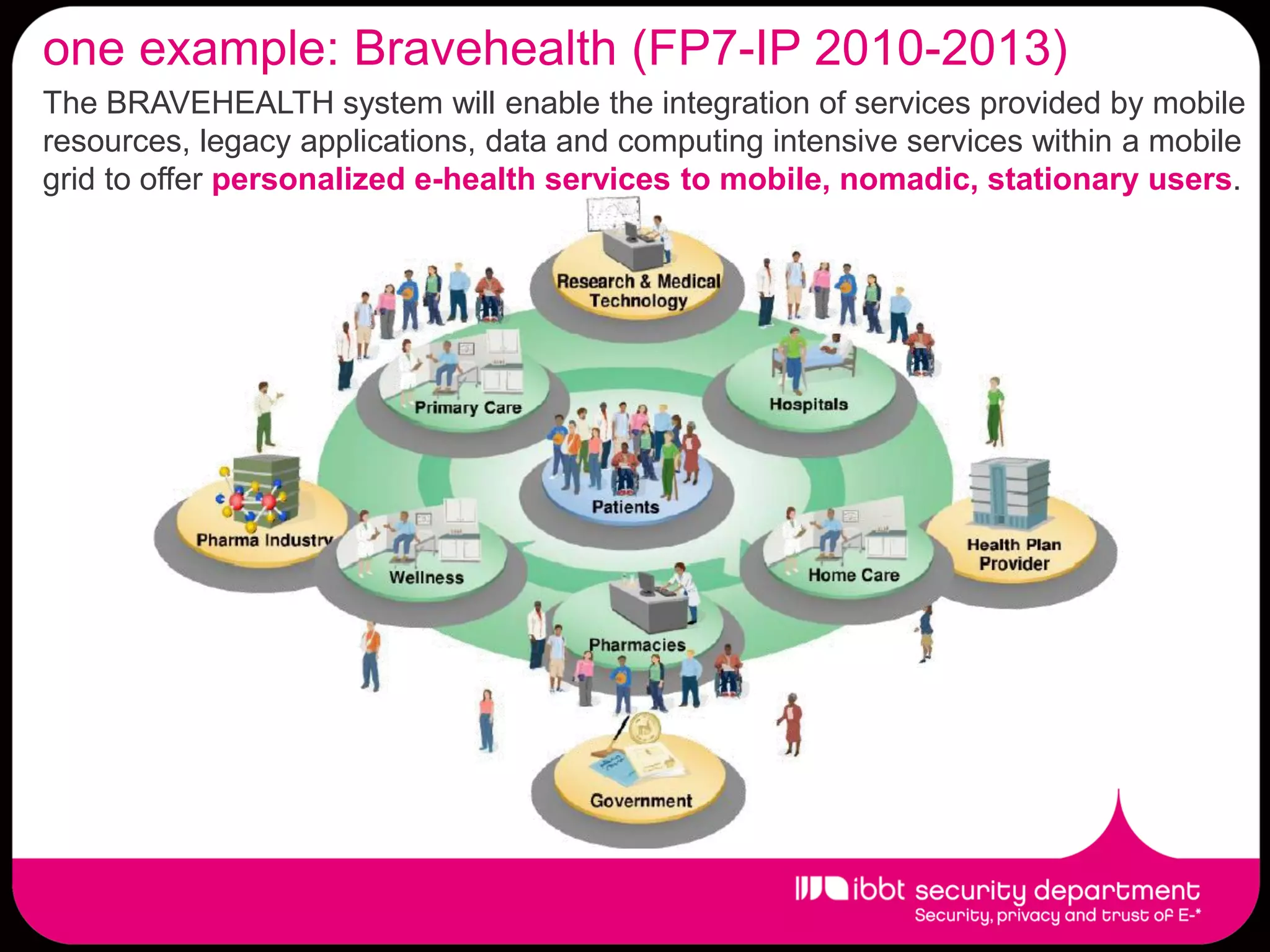
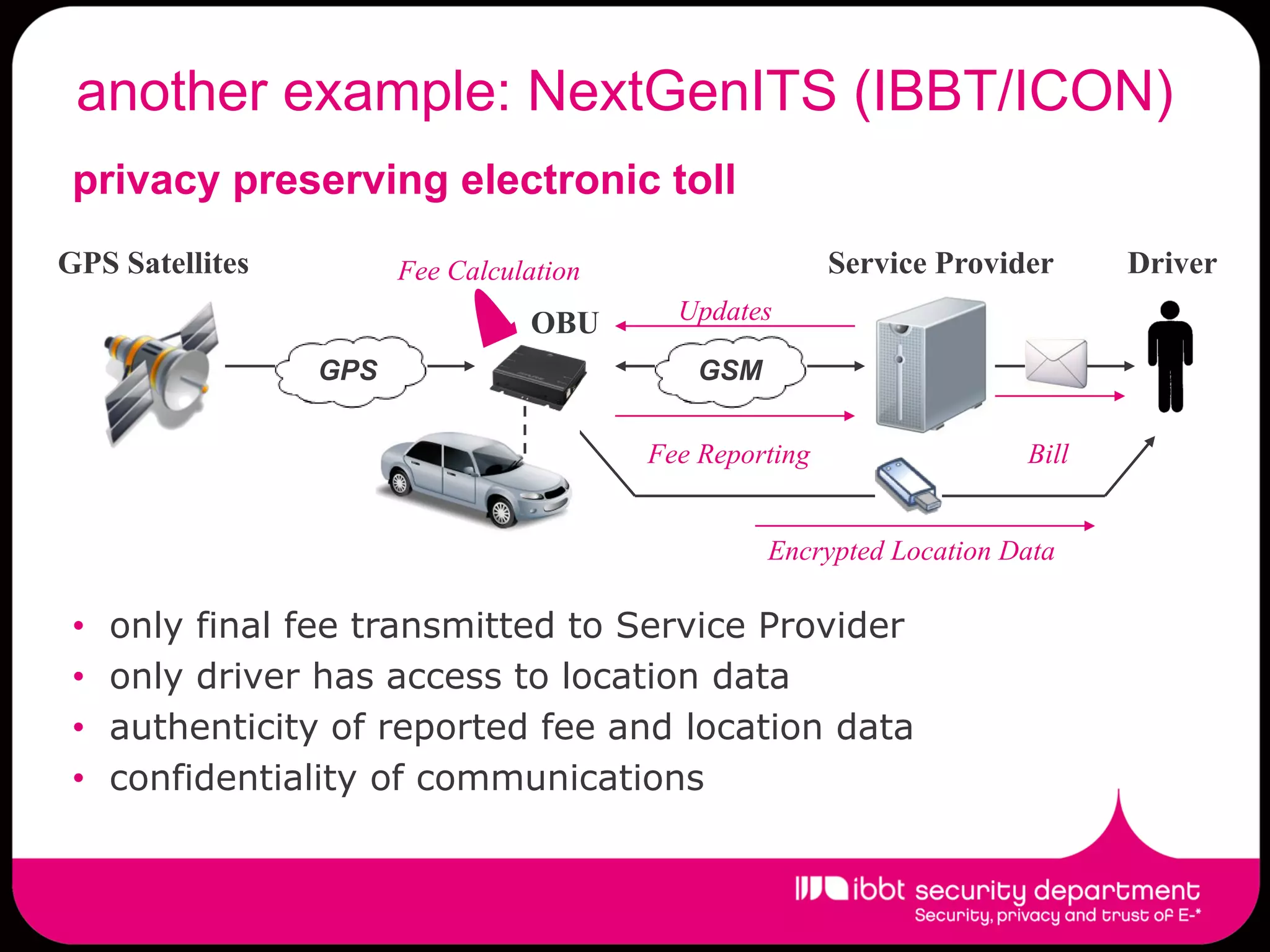
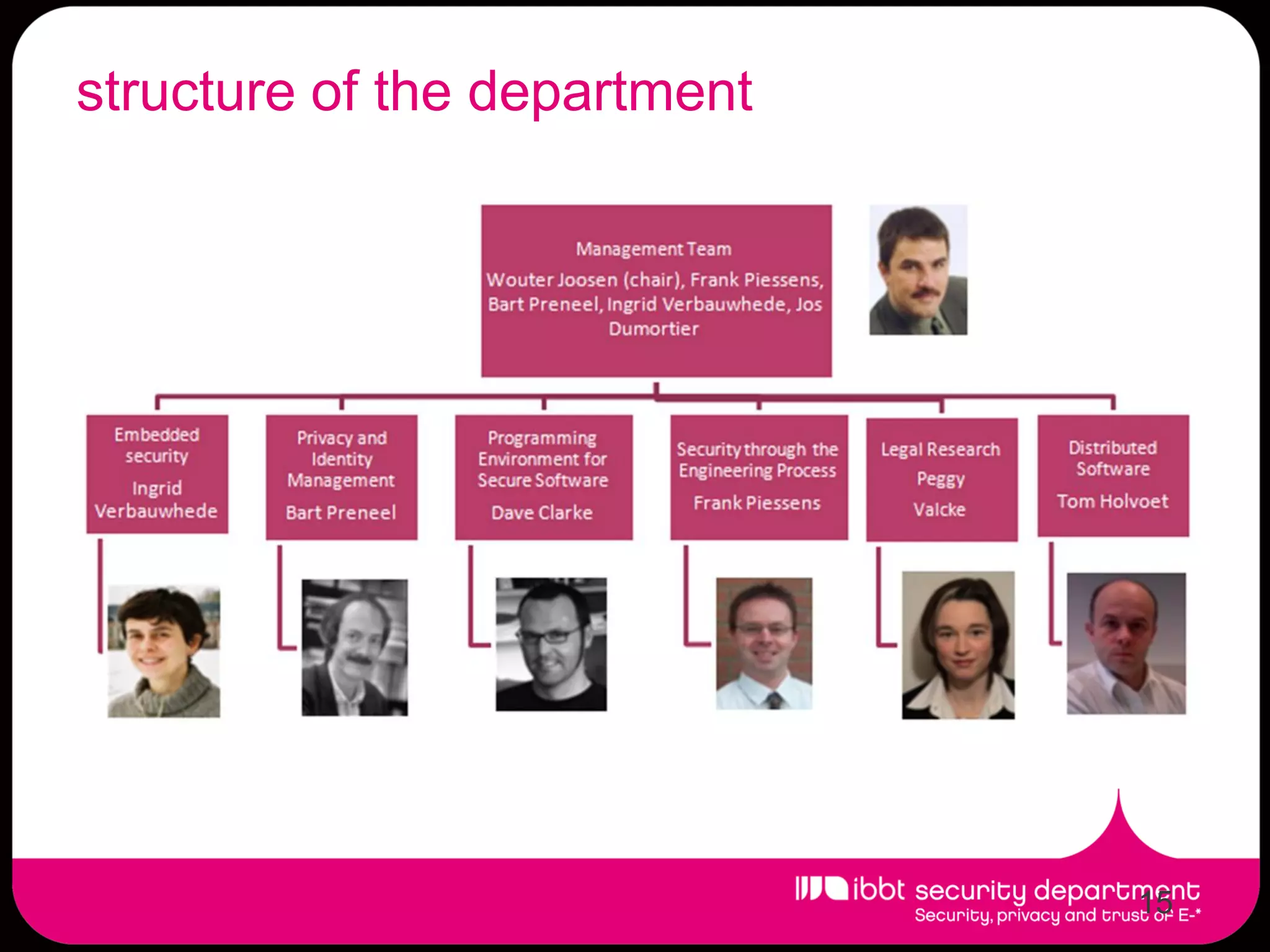
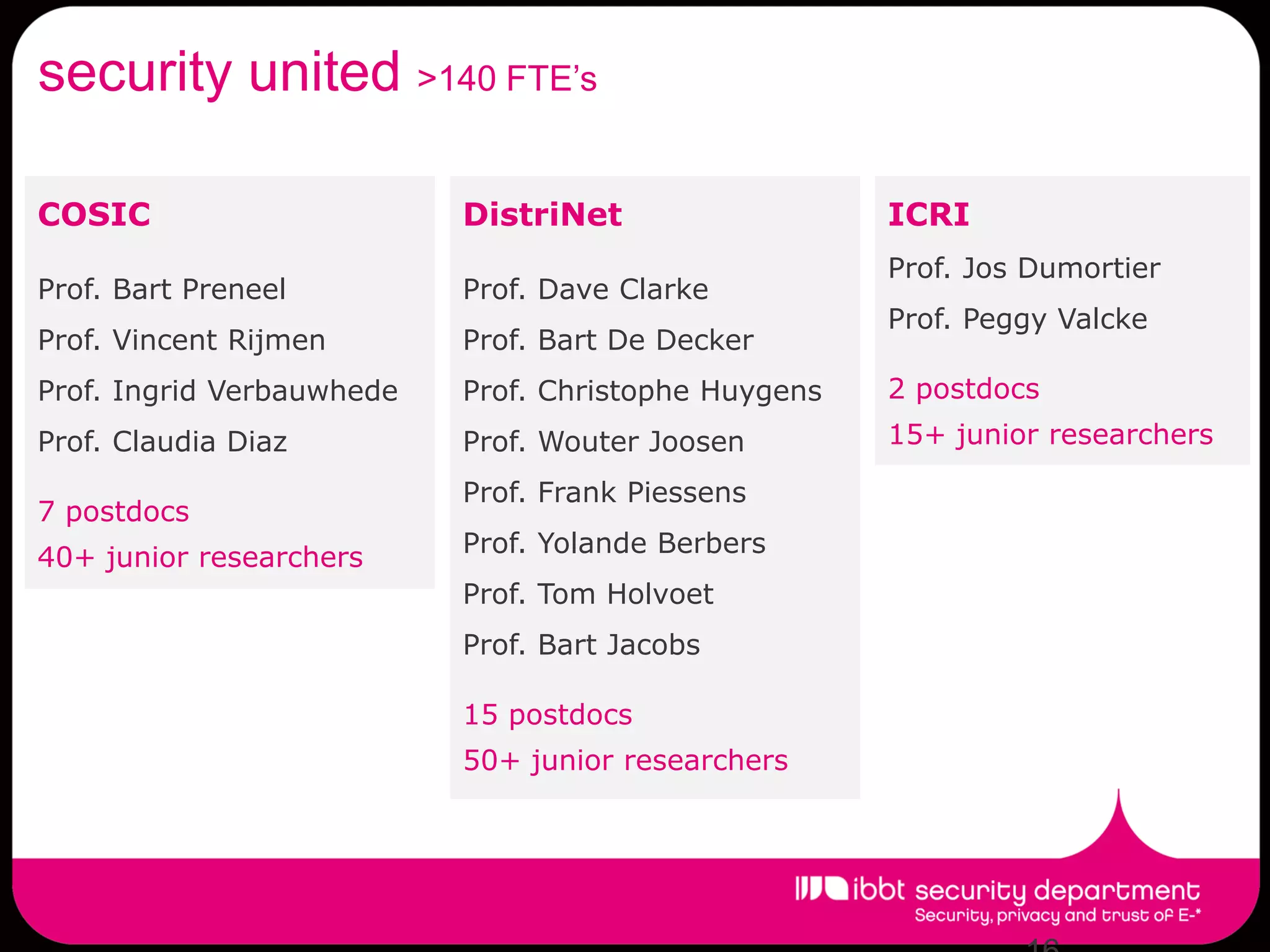
The document summarizes the IBBT security department, which enhances ICT security research in Flanders through first-class basic and applied research, knowledge transfer to industry, lowering regulatory compliance costs, and training students. The department has expertise across many security areas and collaborates between its COSIC, DistriNet, and ICRI groups. It has a strong track record of FP6/FP7 projects and commercial spin-offs. Research focuses include assurance for future internet services, privacy, identity management, and cybercrime.