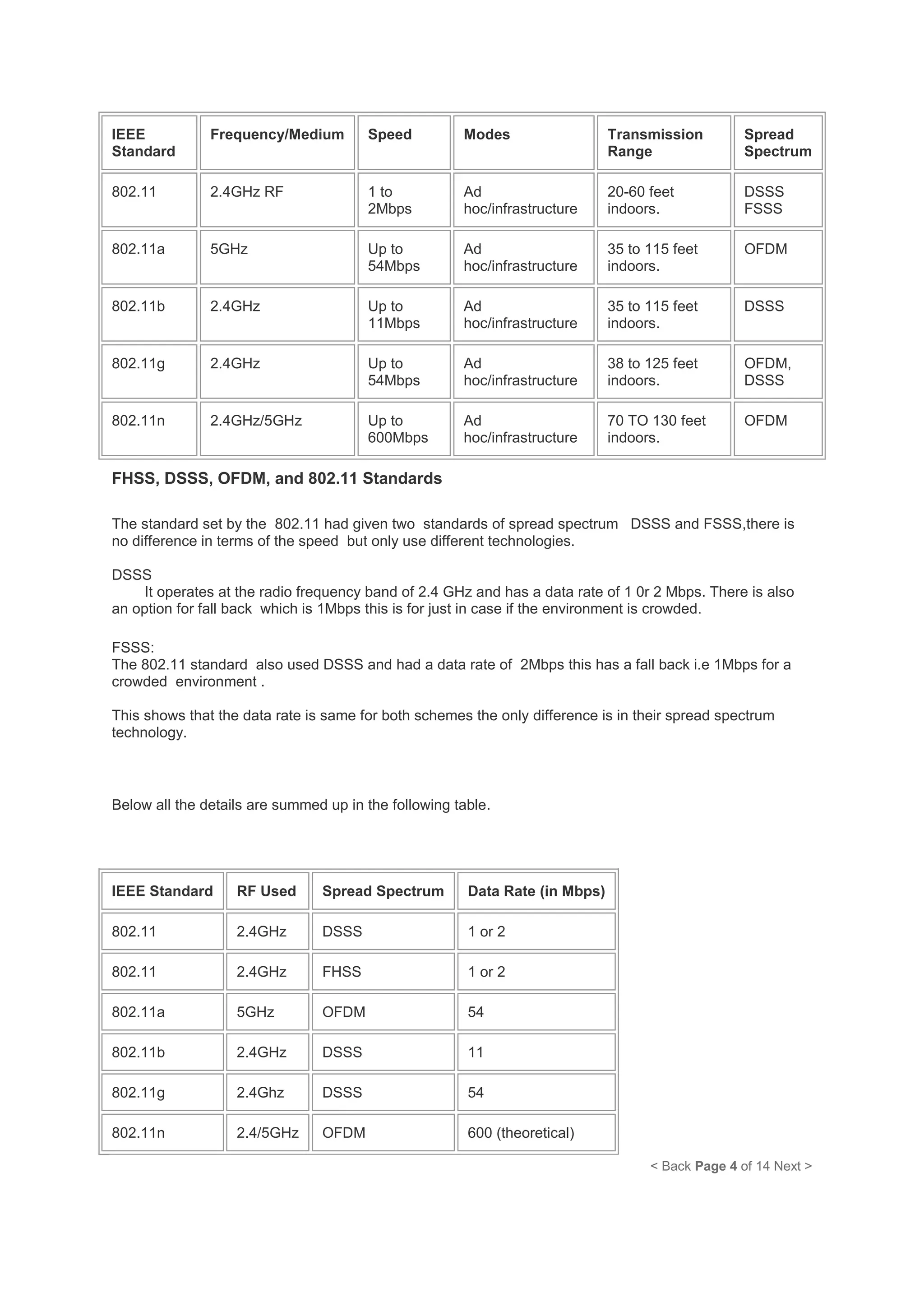
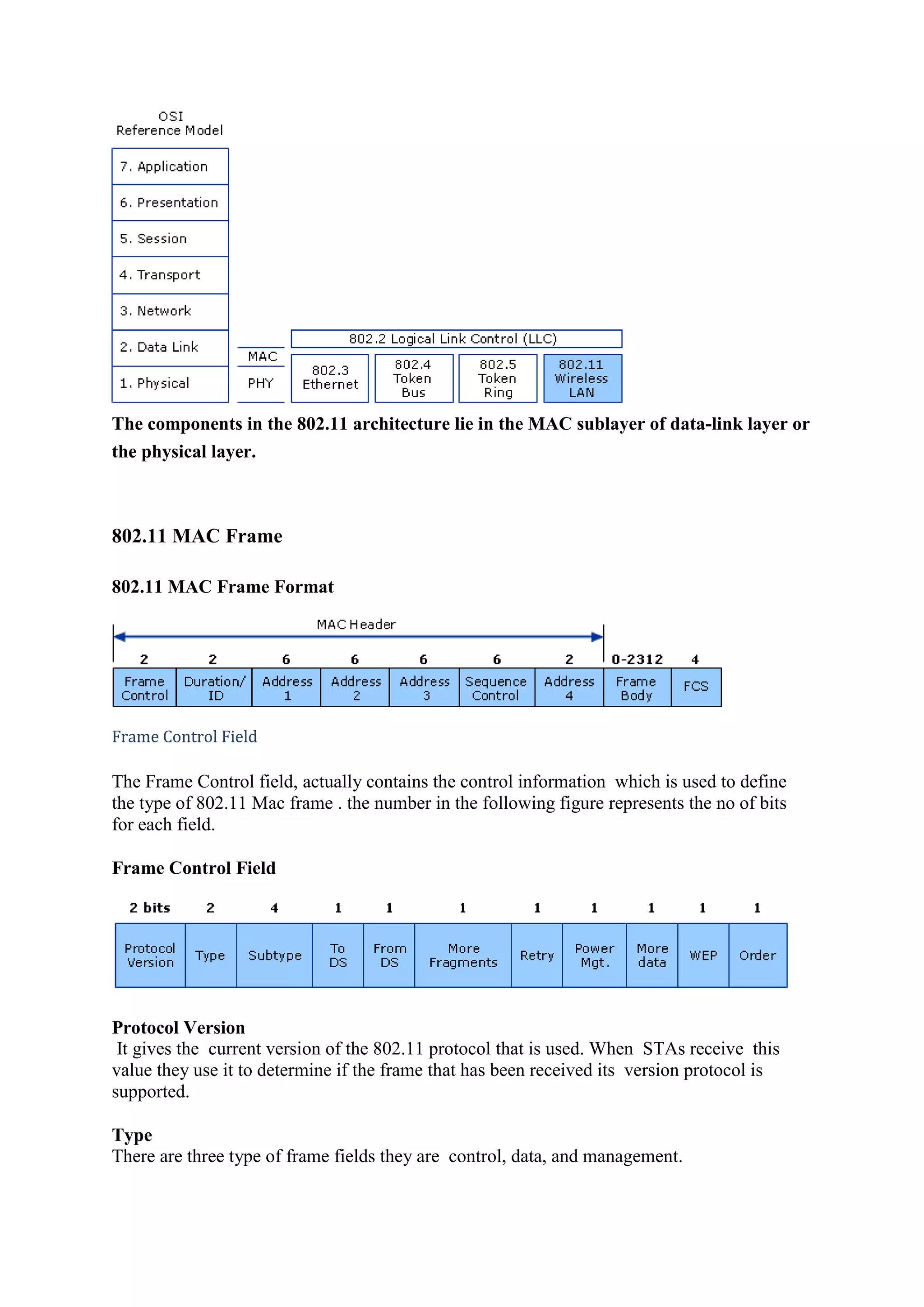
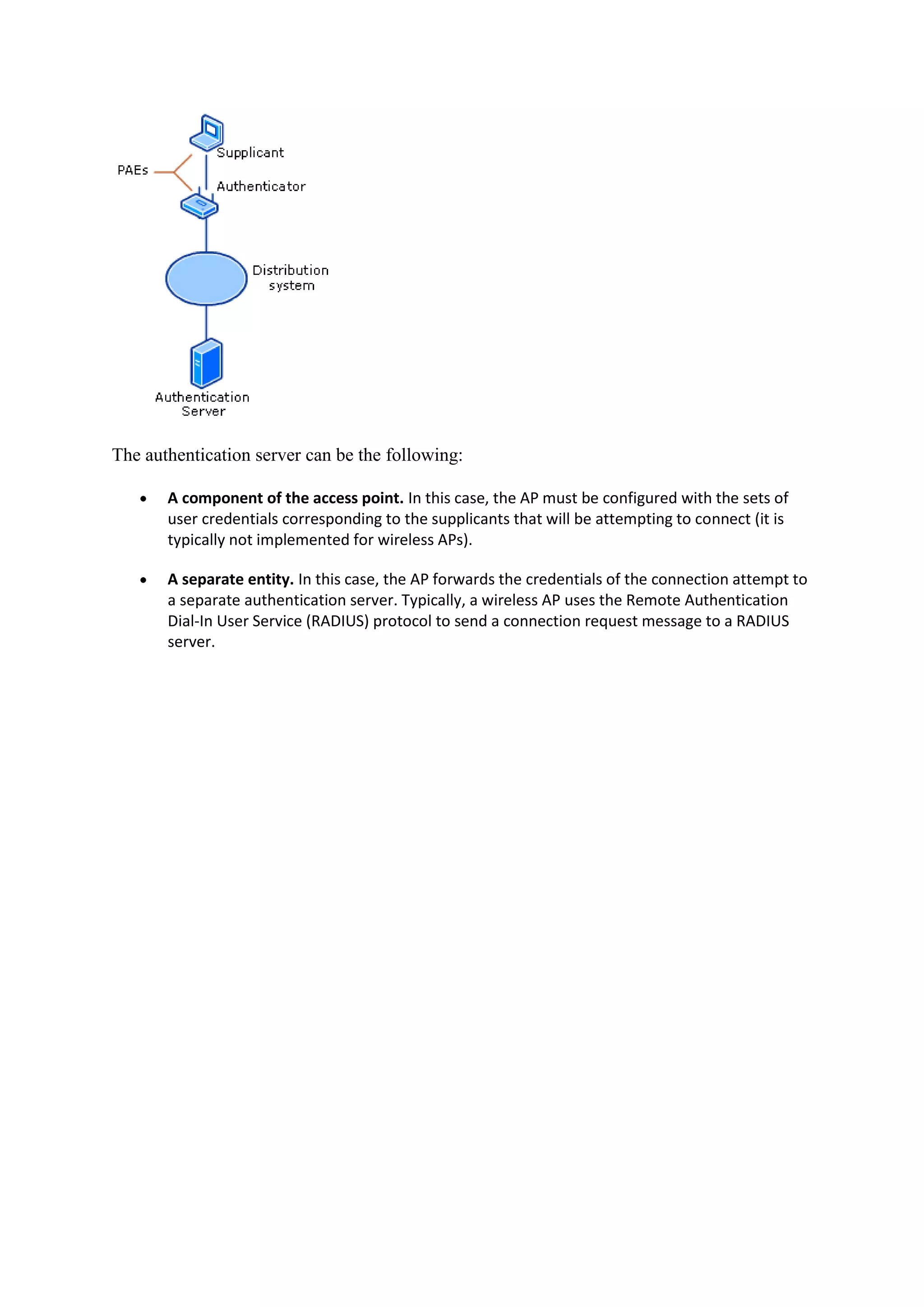
A home wireless network allows multiple digital devices in a home, like computers, laptops, tablets, phones, and printers, to connect and communicate with each other over Wi-Fi. A wireless router broadcasts the Wi-Fi signal, which devices can detect and connect to wirelessly using built-in Wi-Fi adapters or external USB adapters. Common wireless network standards are 802.11b providing speeds up to 11 Mbps and 802.11g providing speeds up to 54 Mbps. The router's firewall, network address translation, and ability to share a single internet connection allow multiple devices on the home network to securely access the internet simultaneously.