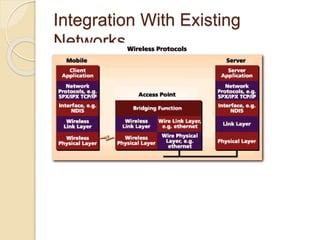
The document discusses wireless networks and wireless local area networks (WLANs). It provides an overview of wireless technology, IEEE 802.11 WLAN standards including 802.11a, 802.11b, security considerations, and migrating to wireless networks. The key topics covered include how wireless LANs work and differ from wired LANs, common network topologies, hardware requirements, and performance comparisons between the different 802.11 standards.