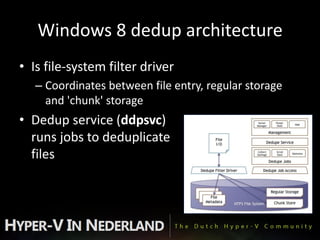
This document discusses disk deduplication, a new feature in Windows 8. Disk deduplication saves storage space by ensuring only one copy of identical data blocks are stored, even if they appear in multiple files. It works post-process in the background to deduplicate files. Reported savings can be 30-50% for documents, 70-80% for application libraries, and up to 95% for virtual hard disk libraries. Performance impacts are minimal at around 3% slower read speeds when data is not cached.