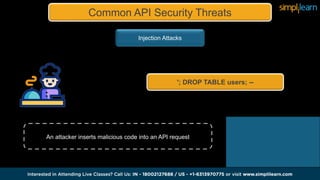
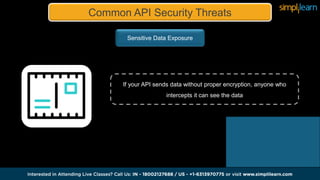
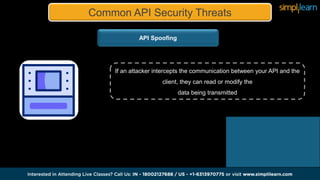
The document discusses APIs and their importance, particularly focusing on API security threats such as injection attacks, broken authentication, and sensitive data exposure. It outlines best practices for securing APIs, including authentication methods like OAuth 2.0, using encryption, input validation, rate limiting, and monitoring through logging. Additionally, it mentions tools and technologies for API management and highlights specific vulnerabilities, including Bluetooth vulnerabilities like Blueborne.