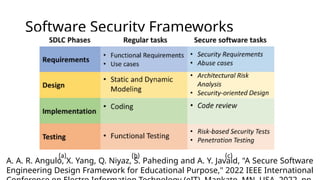
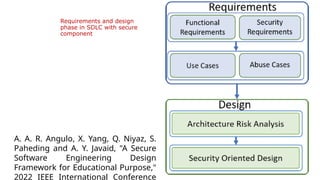
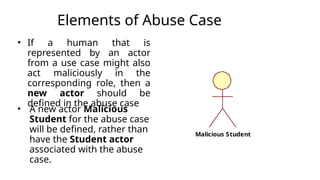
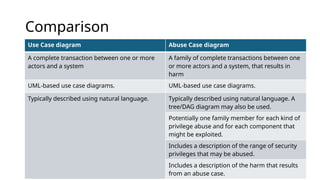
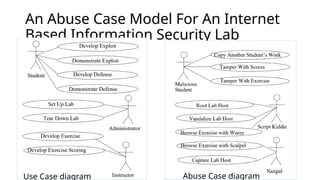
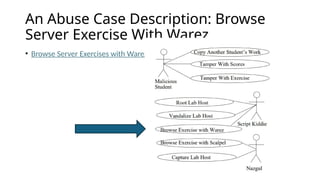
This document details the development and application of abuse cases within the secure software development life cycle (SDLC), outlining their role in identifying potential harmful interactions between actors and systems. It describes the steps for developing abuse cases, such as identifying actors, defining abuse cases, and checking for completeness, while differentiating between use case and abuse case diagrams. Additionally, the document highlights how abuse cases enhance understanding of security requirements during the requirements and design phases of software development.