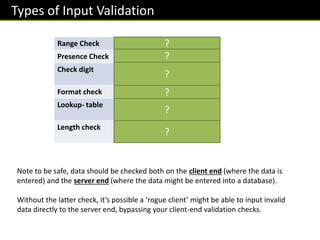
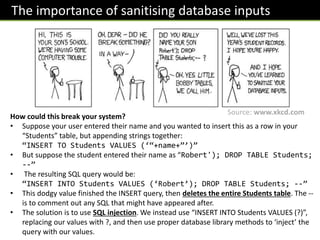
Defensive programming techniques aim to avoid problems in code development and during runtime. Issues that can occur include dodgy user input data, poorly structured code that is hard to maintain, and runtime errors. Defensive design focuses on preventing unintended exploitation of systems, keeping code well-organized, and minimizing bugs. Input validation and sanitization are important techniques to check user data meets criteria and remove unwanted characters. Database inputs especially need to be sanitized to prevent SQL injection attacks.



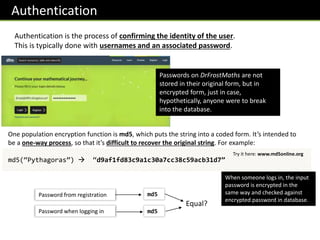
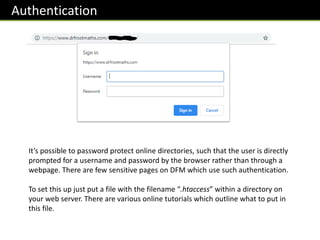
![Input Validation in JavaScript
How might we do each of the following checks in JavaScript, on an input x?
var x = prompt(“Enter a value”);
if(!x)alert(“No input entered”);
if([“bob”,”mike”,”dave”].indexOf(x)==-1)alert(“…”);
var n = Number(x);
if(n<100 || n>200)alert(“Number not in range 100-200”);
if(x.length > 10)alert(“Value too long”);
Was a value entered?
Note that empty strings (“”), when cast
to a Boolean, give a value of false.
Was “bob”, “mike” or
“dave” entered?
Was number in range 100 to 200?
Was length of the input at
most 10 characters?
?
?
?
?](https://image.slidesharecdn.com/gcsecs-defensivedesign-230301152706-2c5e6597/85/GCSECS-DefensiveDesign-pptx-8-320.jpg)
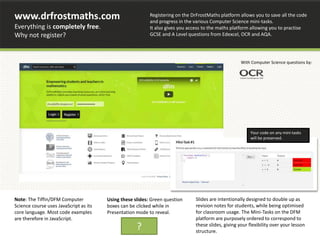
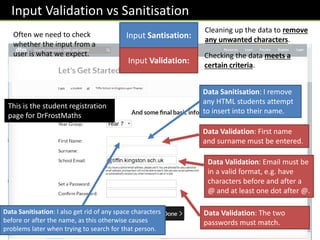
![Harder Ones :: Input Validation in JavaScript
Here’s some further ones you would not be expected to reproduce in an exam!
var x = prompt(“Enter a value”);
if(!/dd/dd/dddd/.test(x))alert(“Invalid date format”);
var re =
/^(([^<>()[].,;:s@"]+(.[^<>()[].,;:s@"]+)*)|(".+
"))@(([[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}.[0-
9]{1,3}])|(([a-zA-Z-0-9]+.)+[a-zA-Z]{2,}))$/;
if(!re.test(x))alert(“Invalid email”);
Was value a valid date format?
Regular expressions are an advanced way of matching strings which fit a specified pattern. In
Javascript we put these between forward slashes: / … /
d means ‘any single digit’. We want dd/dd/dddd. But because “/” denotes the end of the regular
expression, we need to ‘escape’ the /s by adding a backslash on front of them. This tells the code that
the character immediately after is a symbol we want to use rather than a special character. The test
function sees whether x matches the regular expression.
Valid email address format?
This is a much more complicated regular expression. It is a
standard pattern that can be easily found on the internet.
?
?](https://image.slidesharecdn.com/gcsecs-defensivedesign-230301152706-2c5e6597/85/GCSECS-DefensiveDesign-pptx-9-320.jpg)