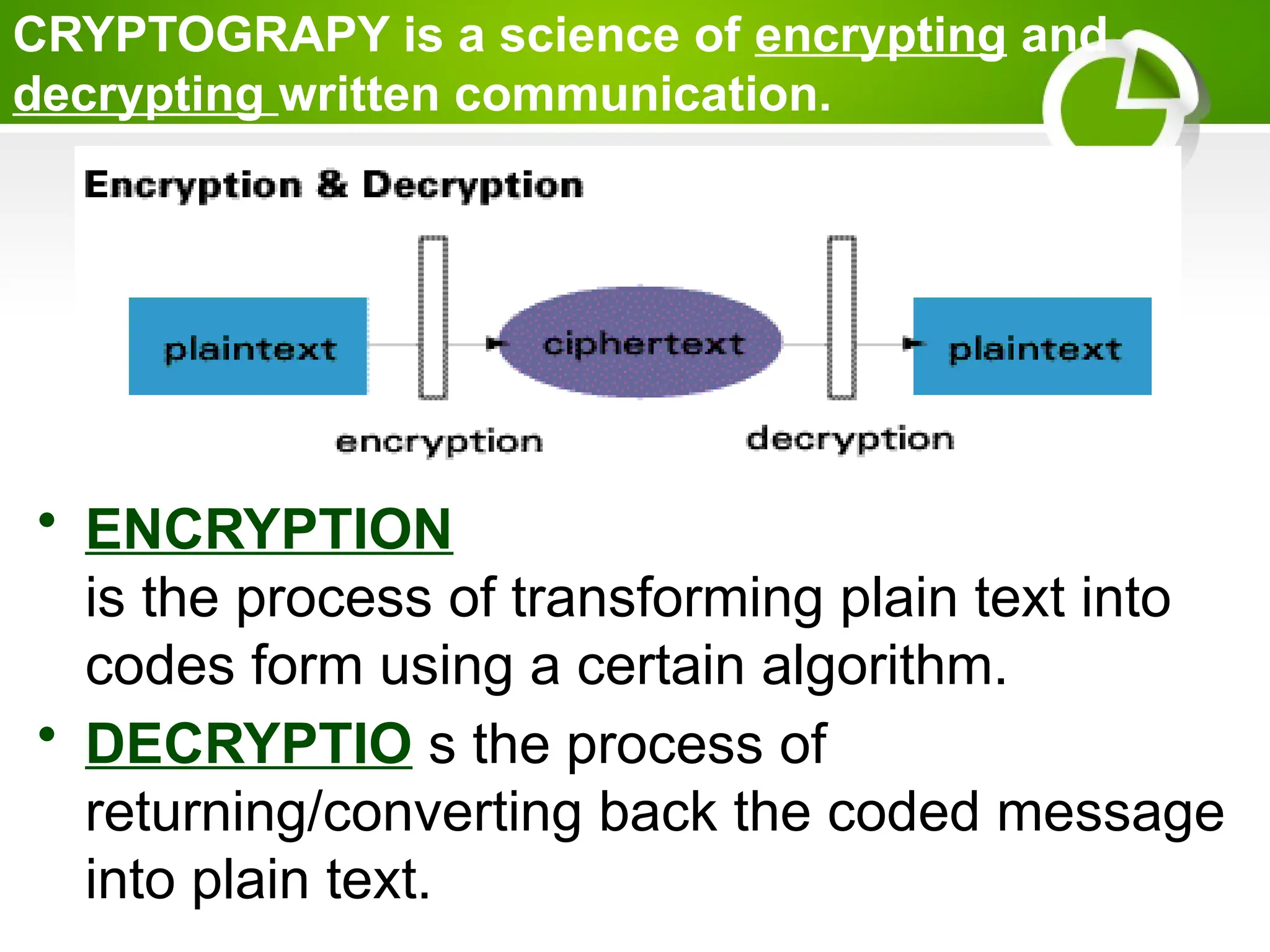
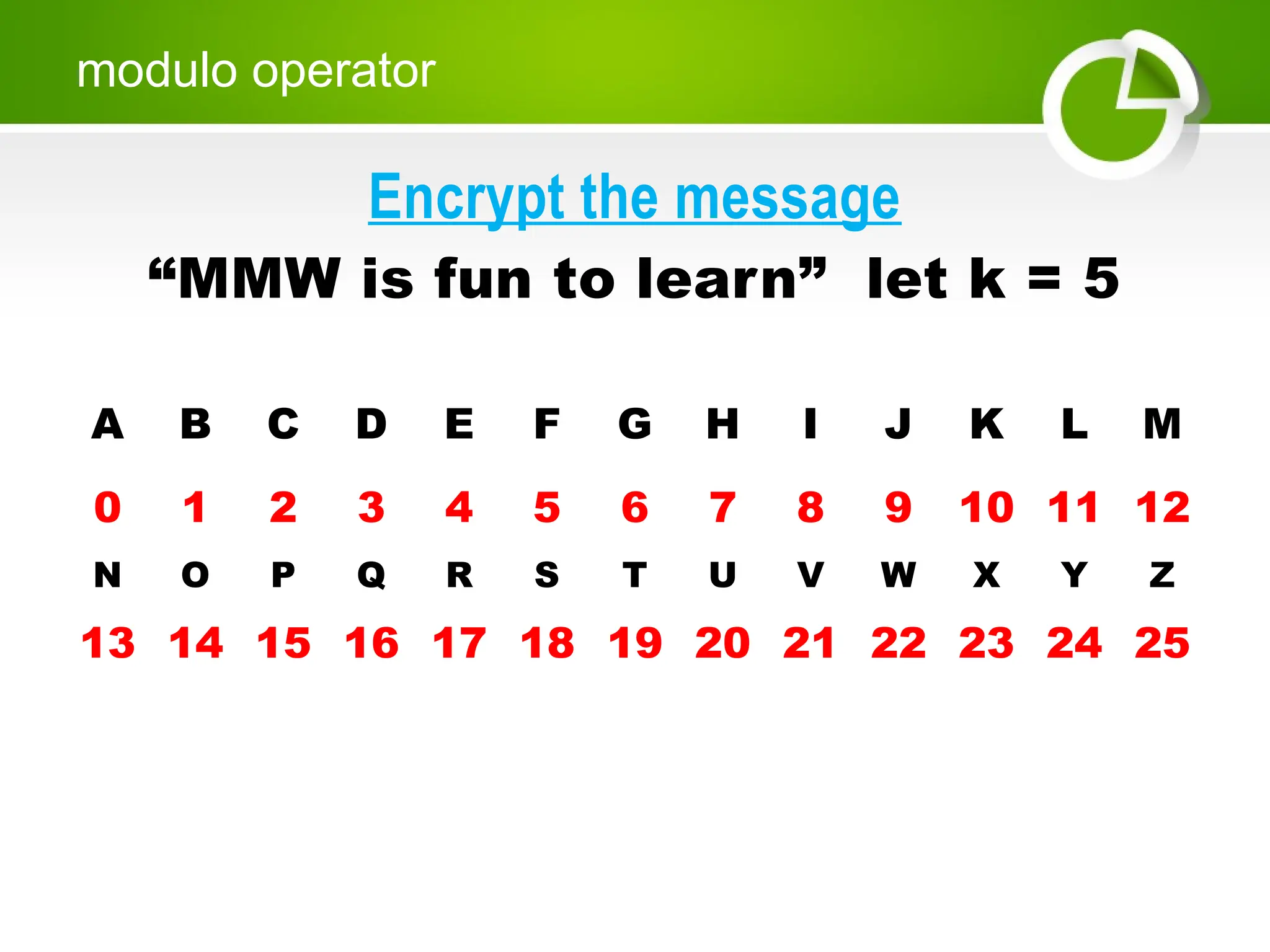
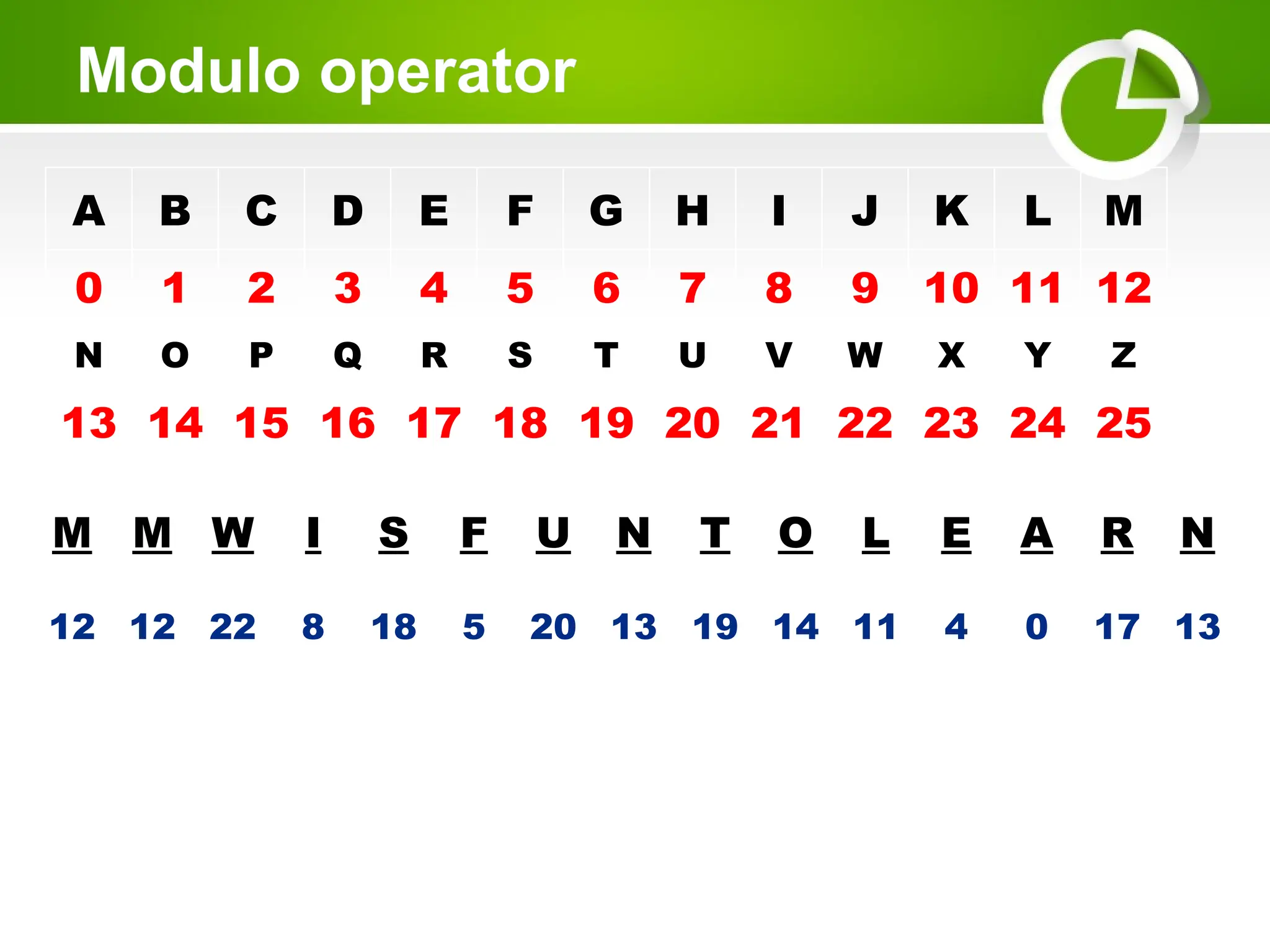
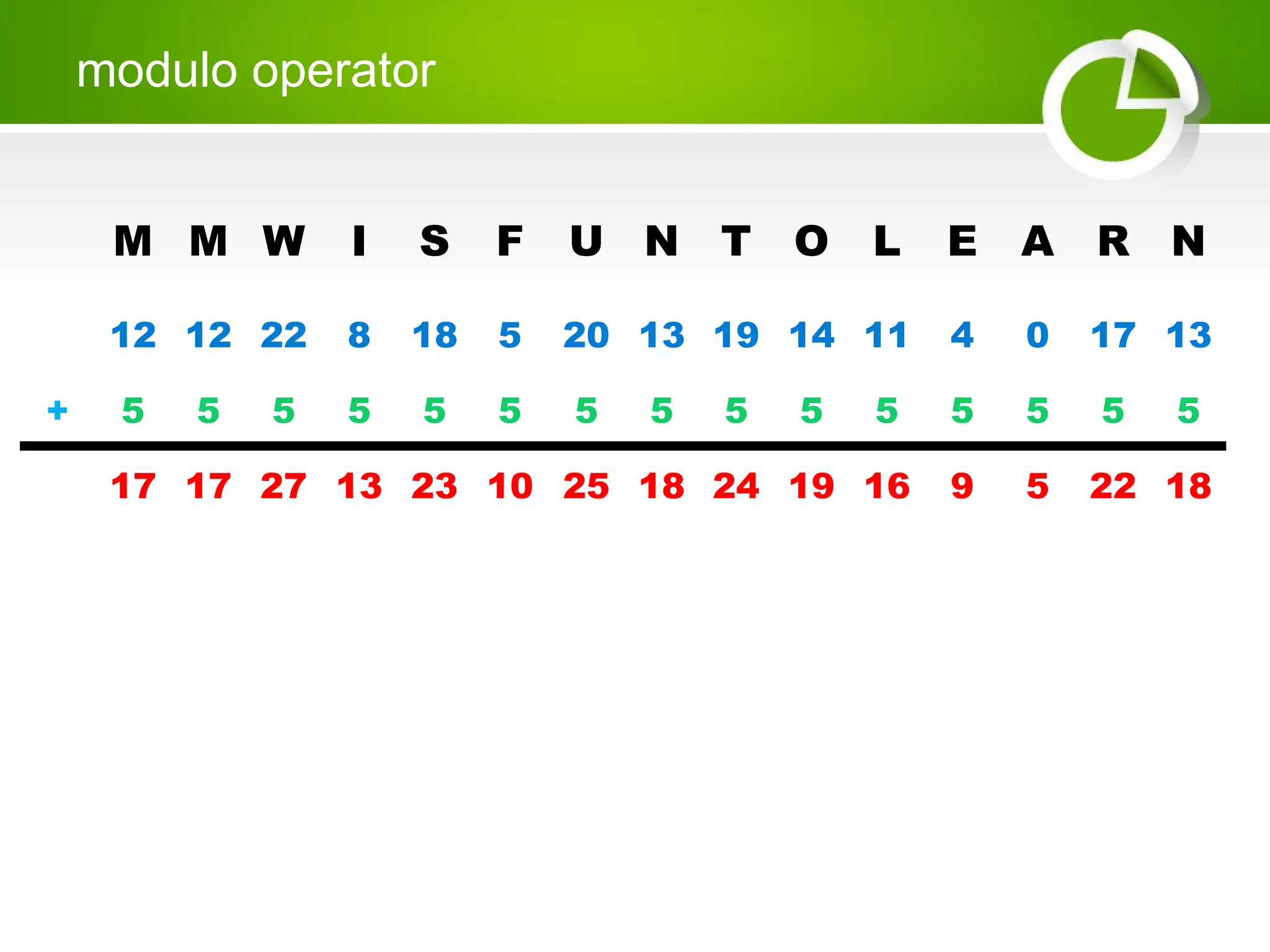
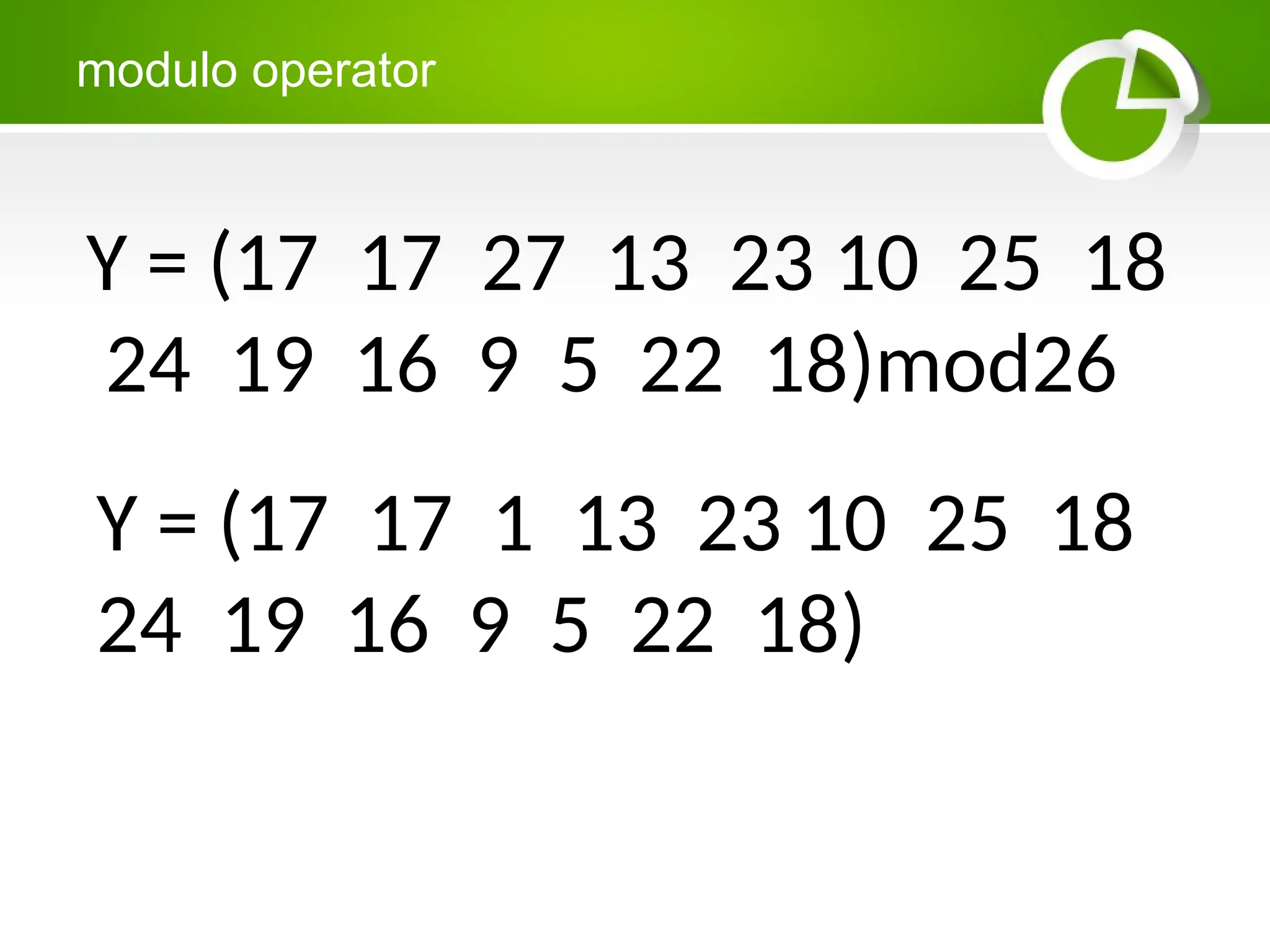
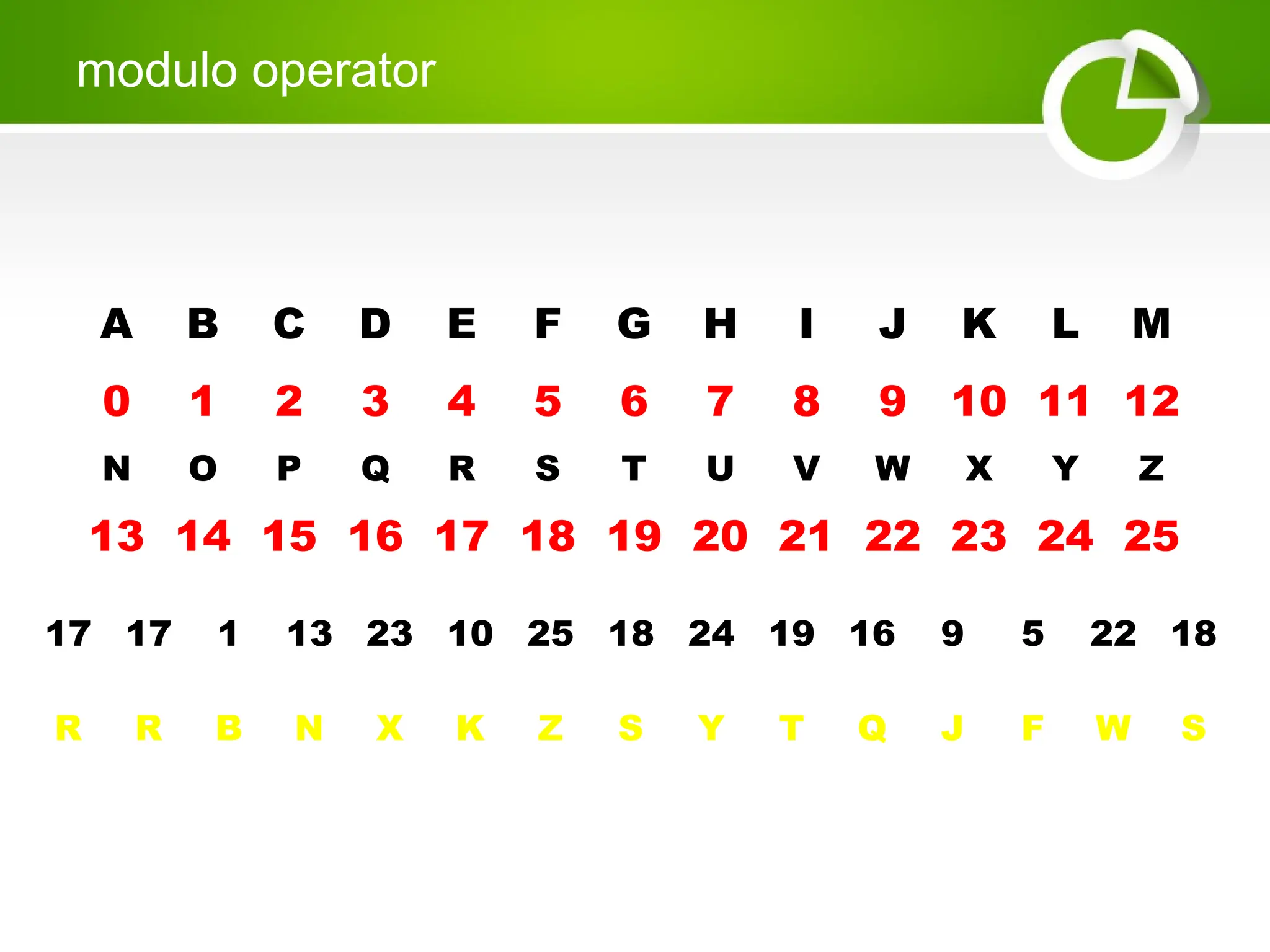
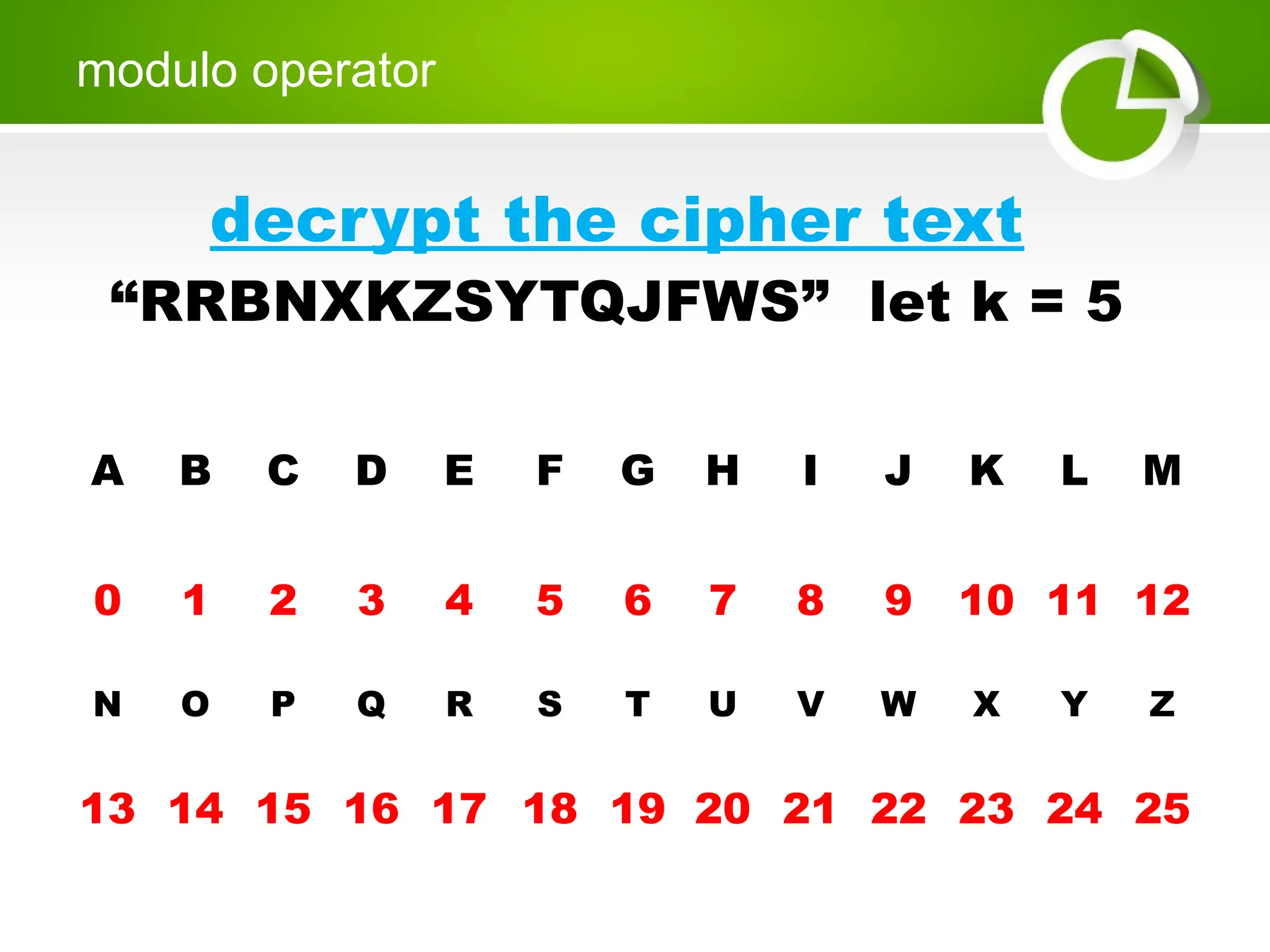
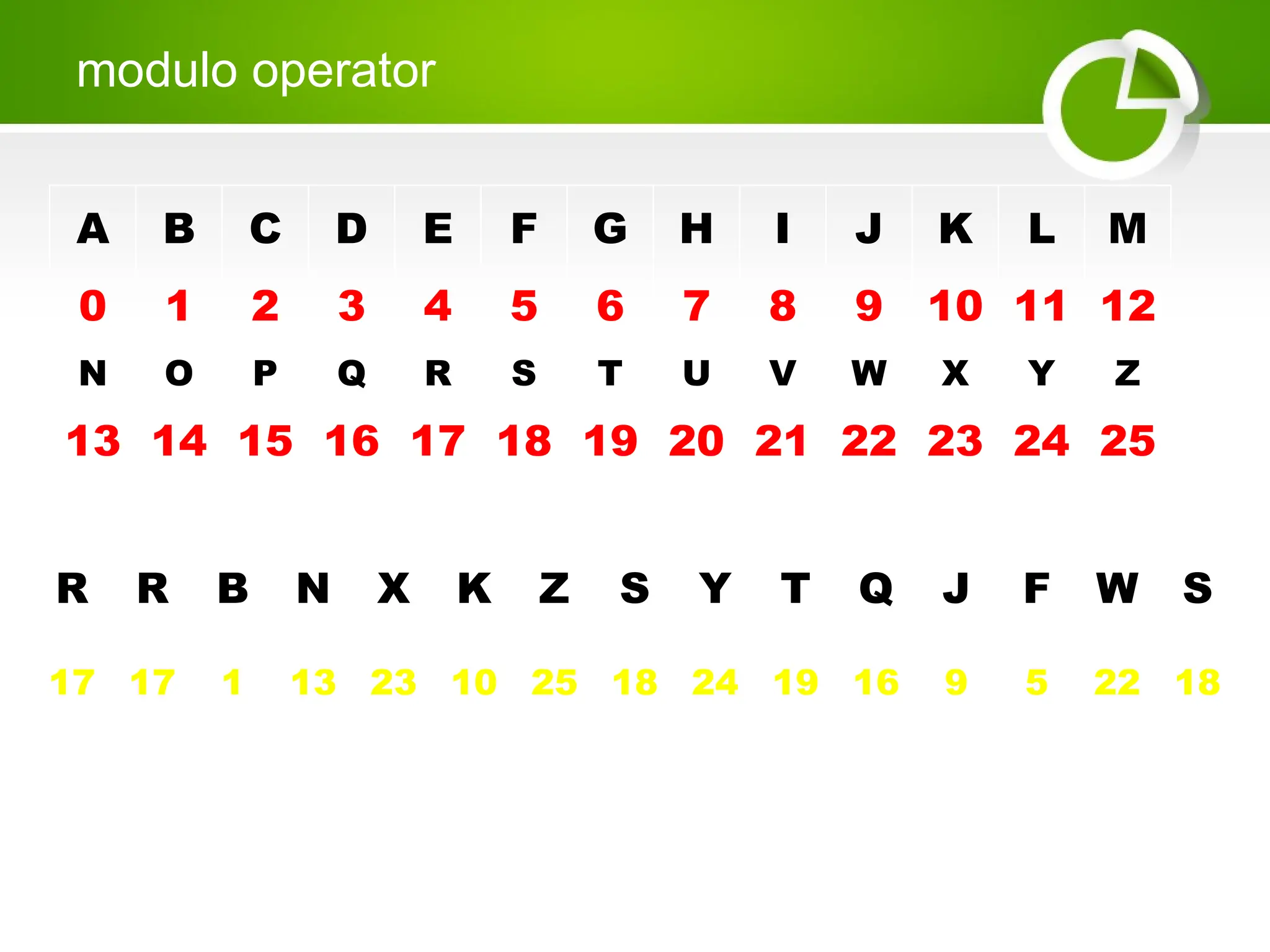
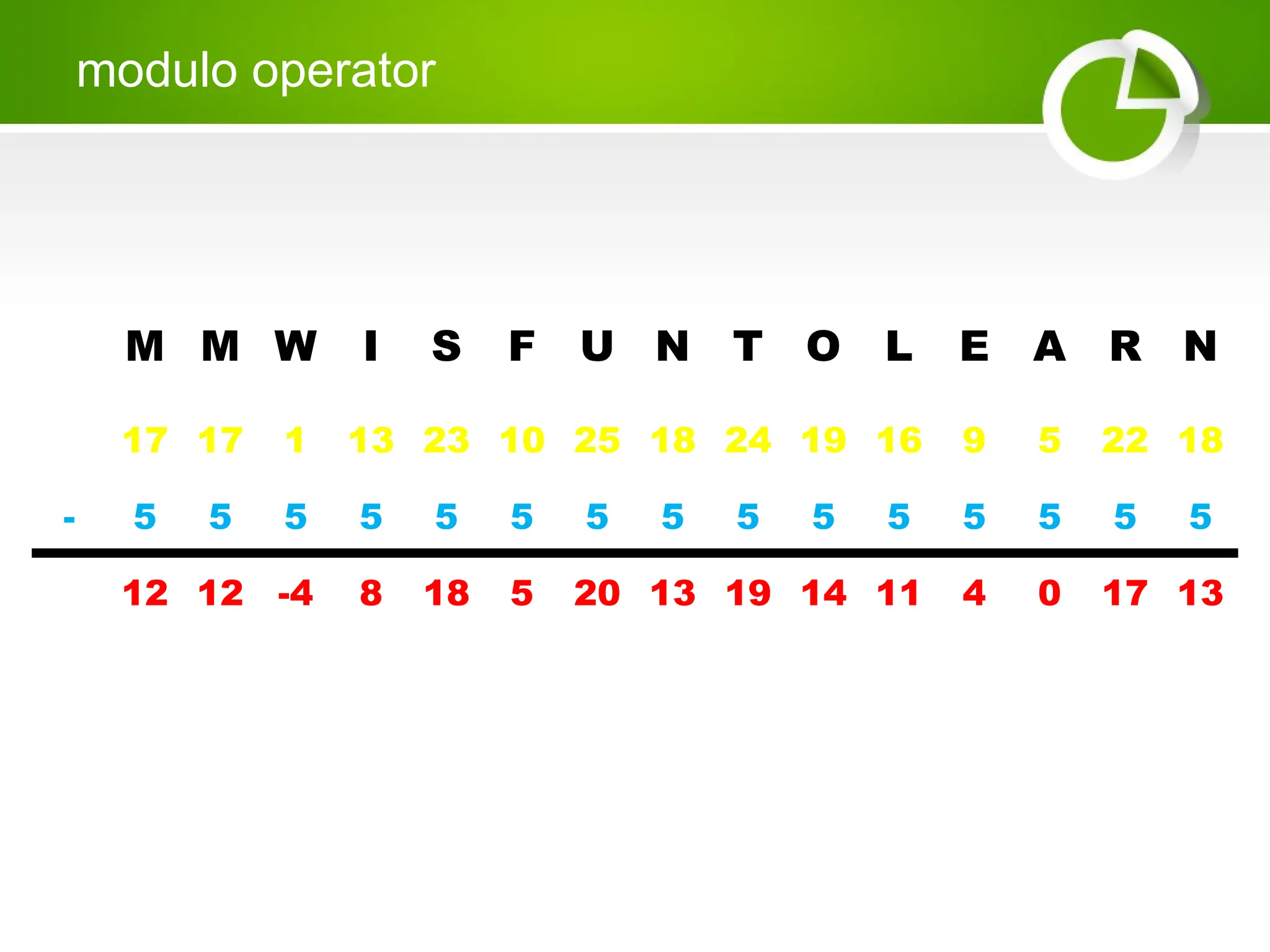
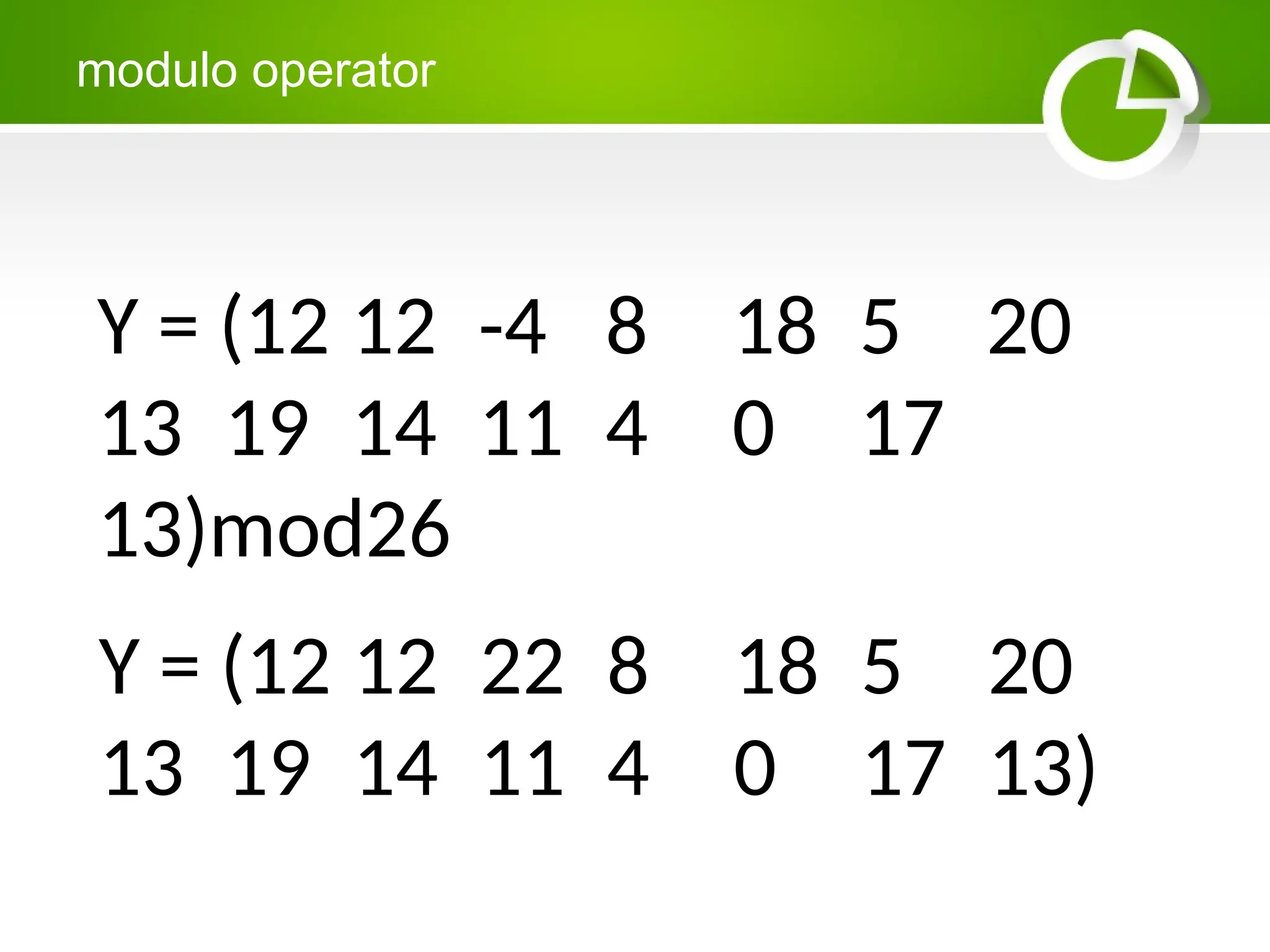
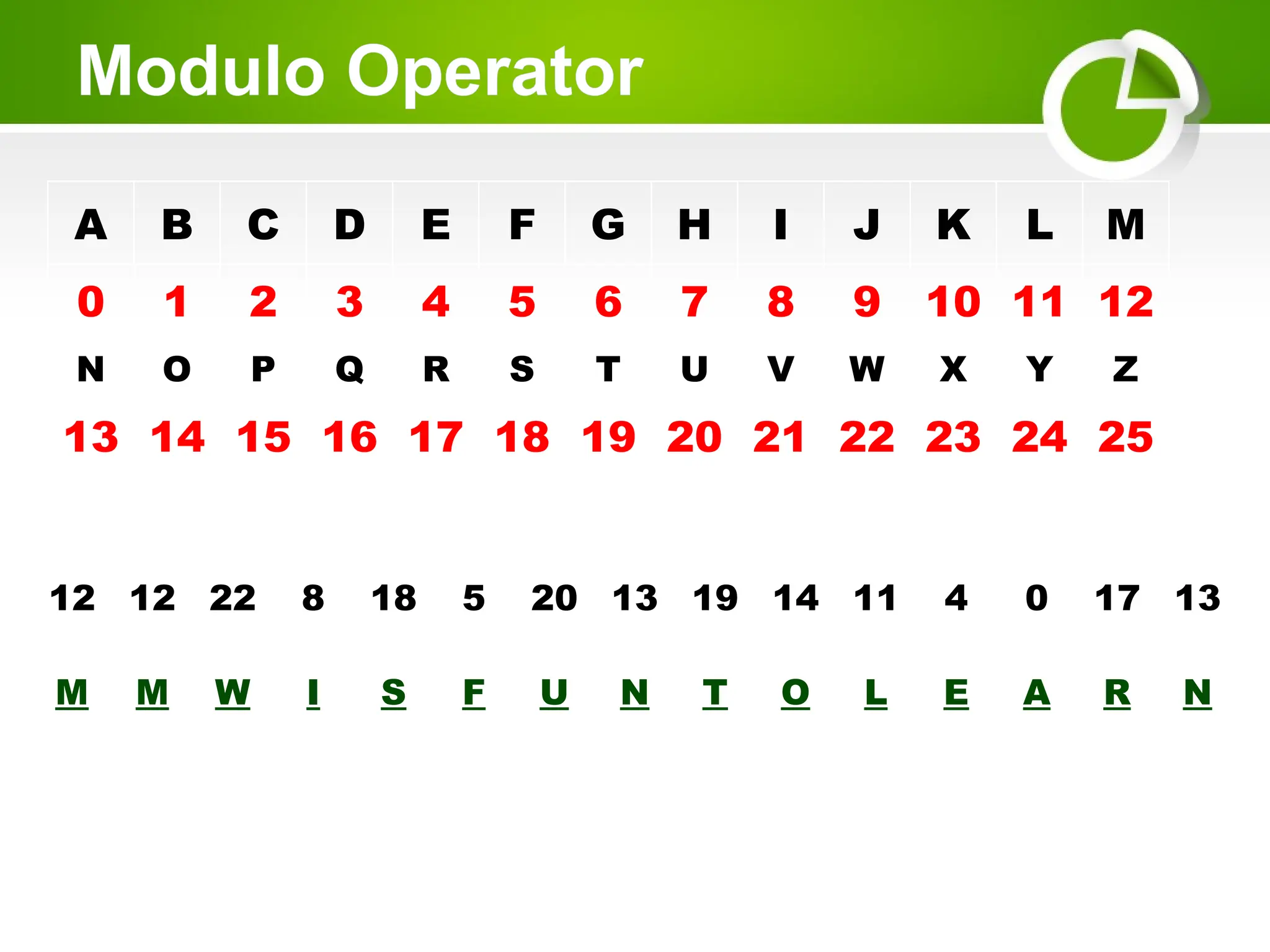
Cryptography is the science of protecting information through encoding, derived from Greek meanings of 'hidden' and 'writing'. It involves the processes of encryption and decryption, turning readable text into coded messages and back again, using various methods such as shift ciphers and modulo operations. The document provides examples and methods for encrypting and decrypting messages using these techniques.